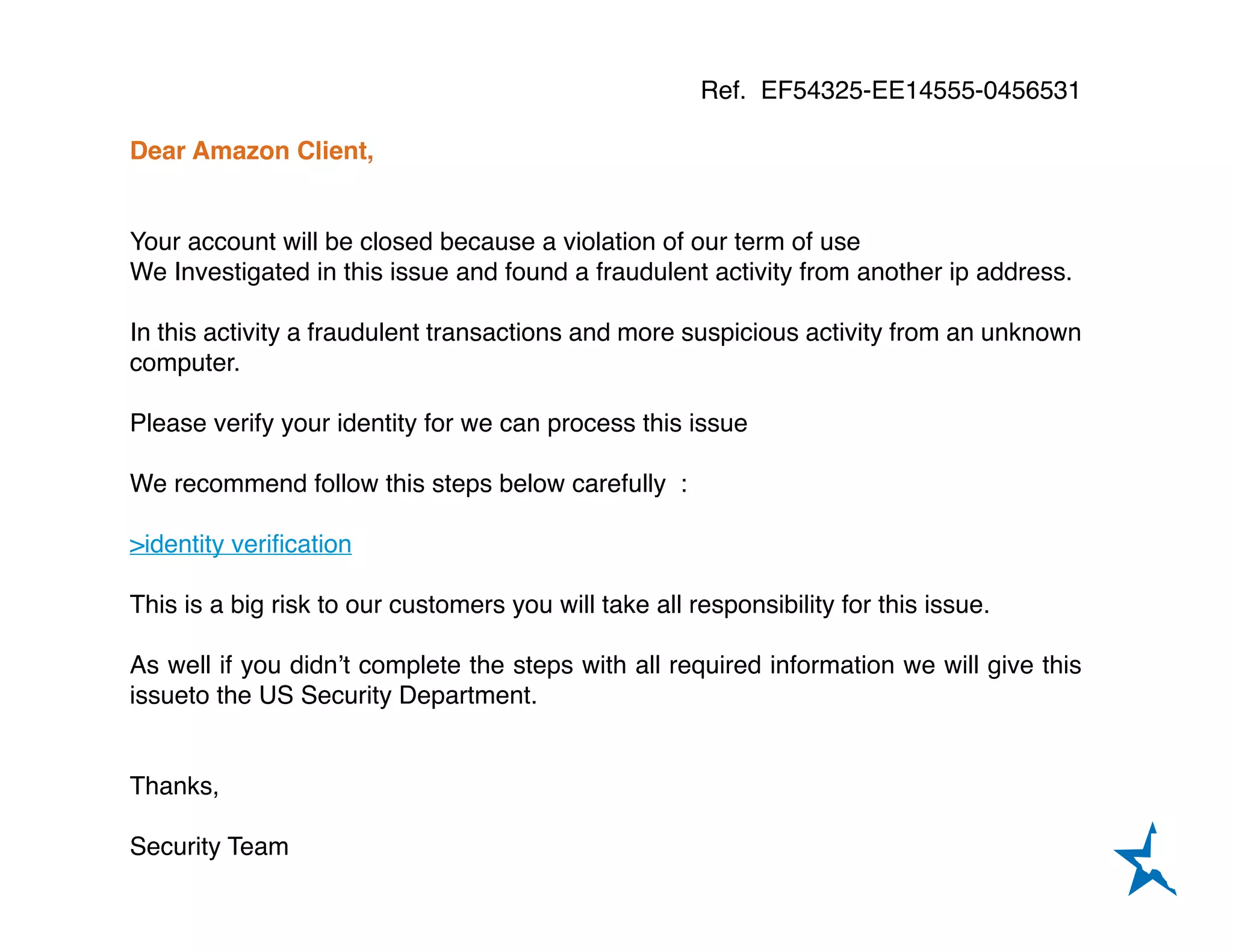
This document provides information about how to detect email fraud, also known as phishing. It outlines several signs that an email may be a phishing attempt, including spelling and grammar mistakes, threats or requests for urgent responses, suspicious links that do not match the website addressed in the email, and requests for personal or financial information. The document advises physicians not to provide any sensitive information or click on links in response to suspicious emails and to independently verify requests with the purported sender using verified contact information.