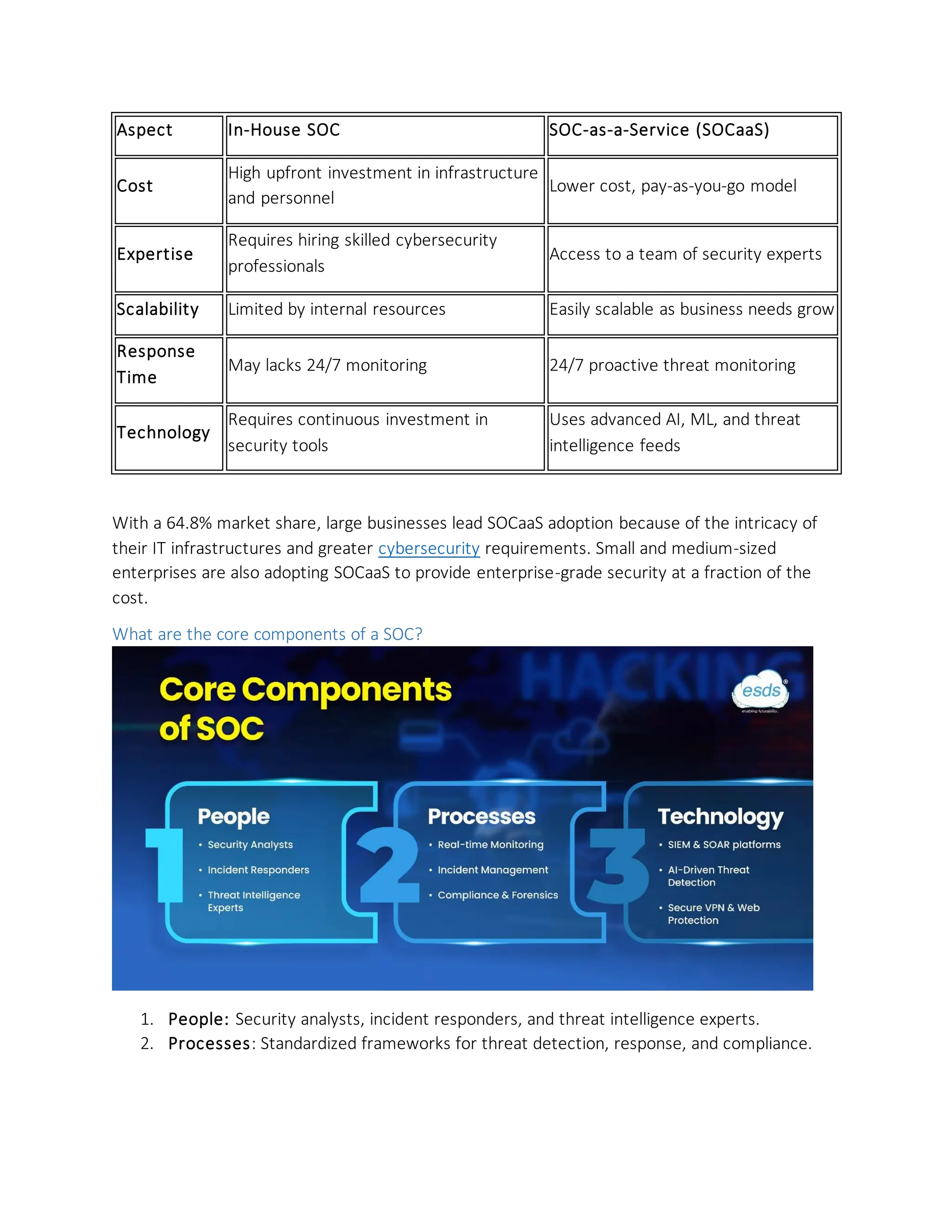
Using SOC-as-a-Service (SOCaaS), organizations, large businesses, or SMBs can have enterprise-level security without significant upfront investments. The SOCaaS market keeps growing, fueled by increasing cyber threats, cloud usage, and AI-based security innovations.