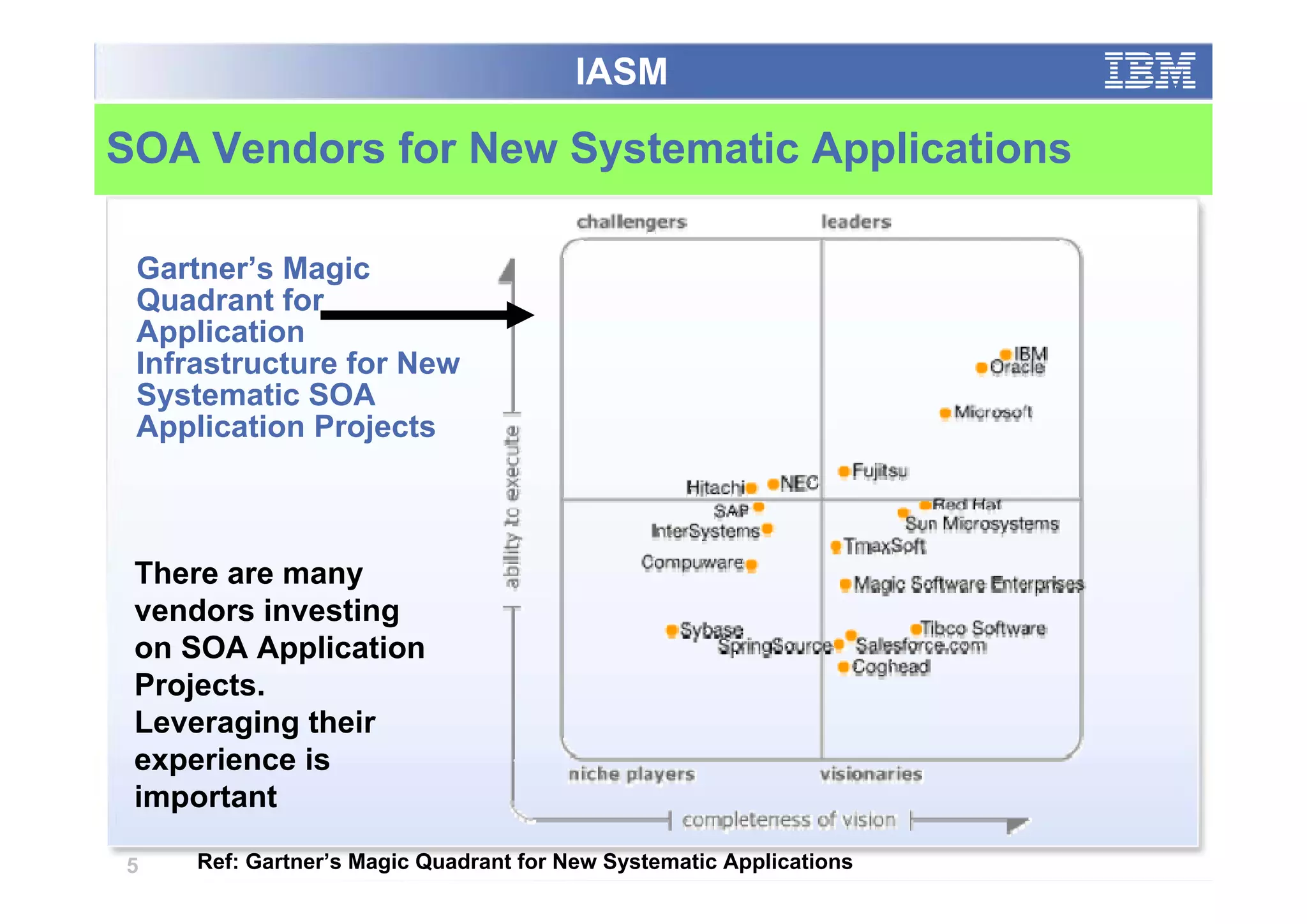
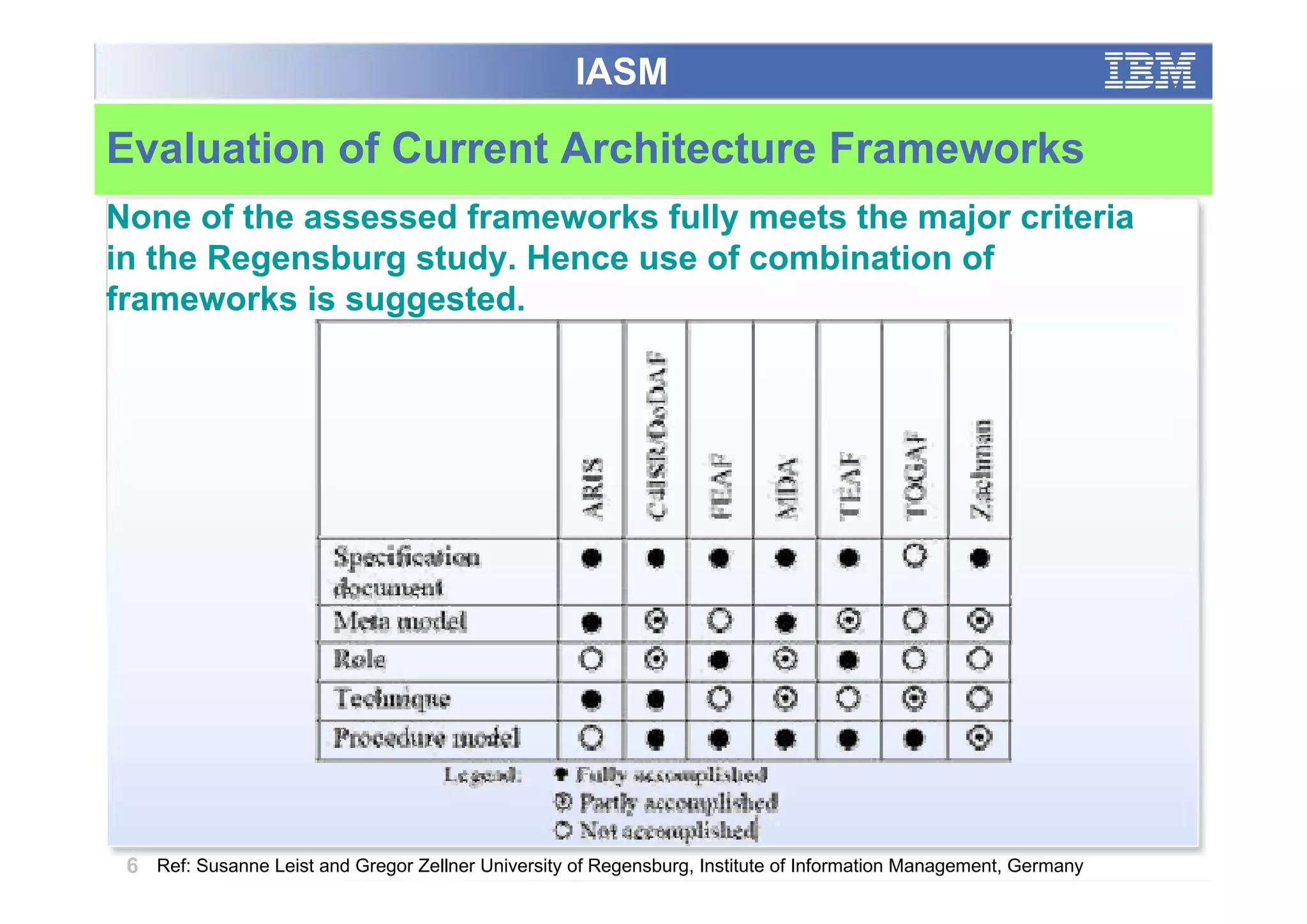
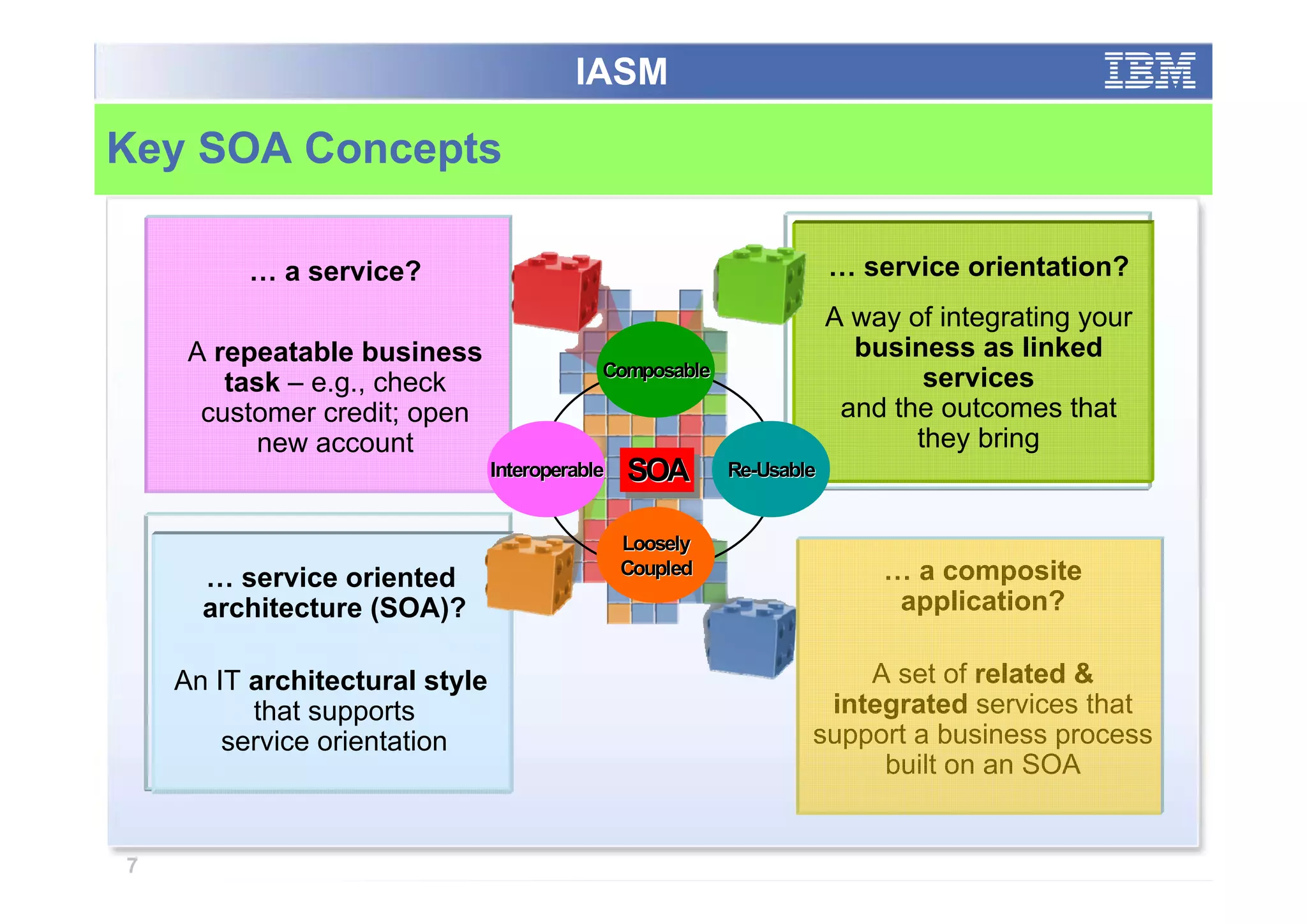
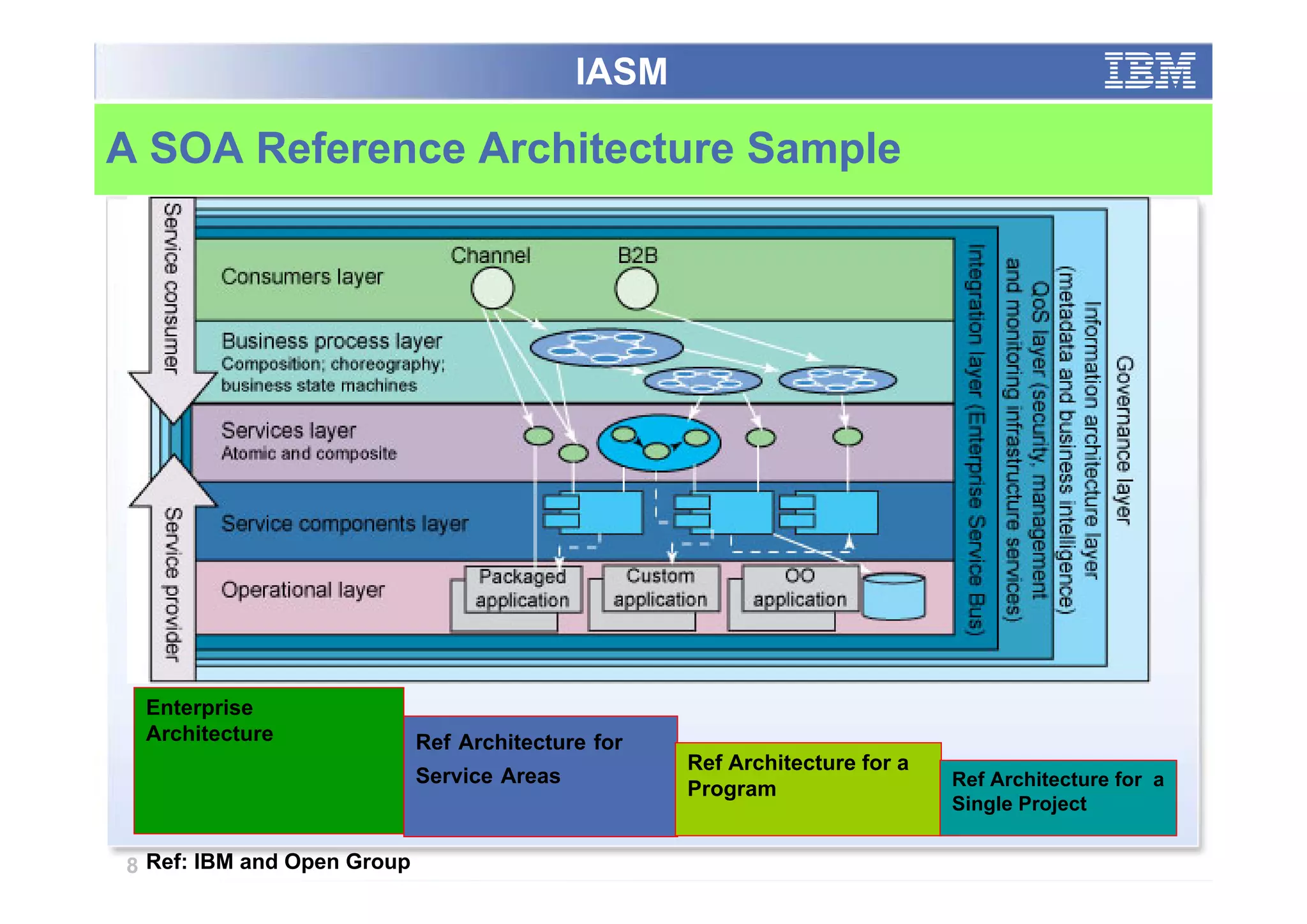
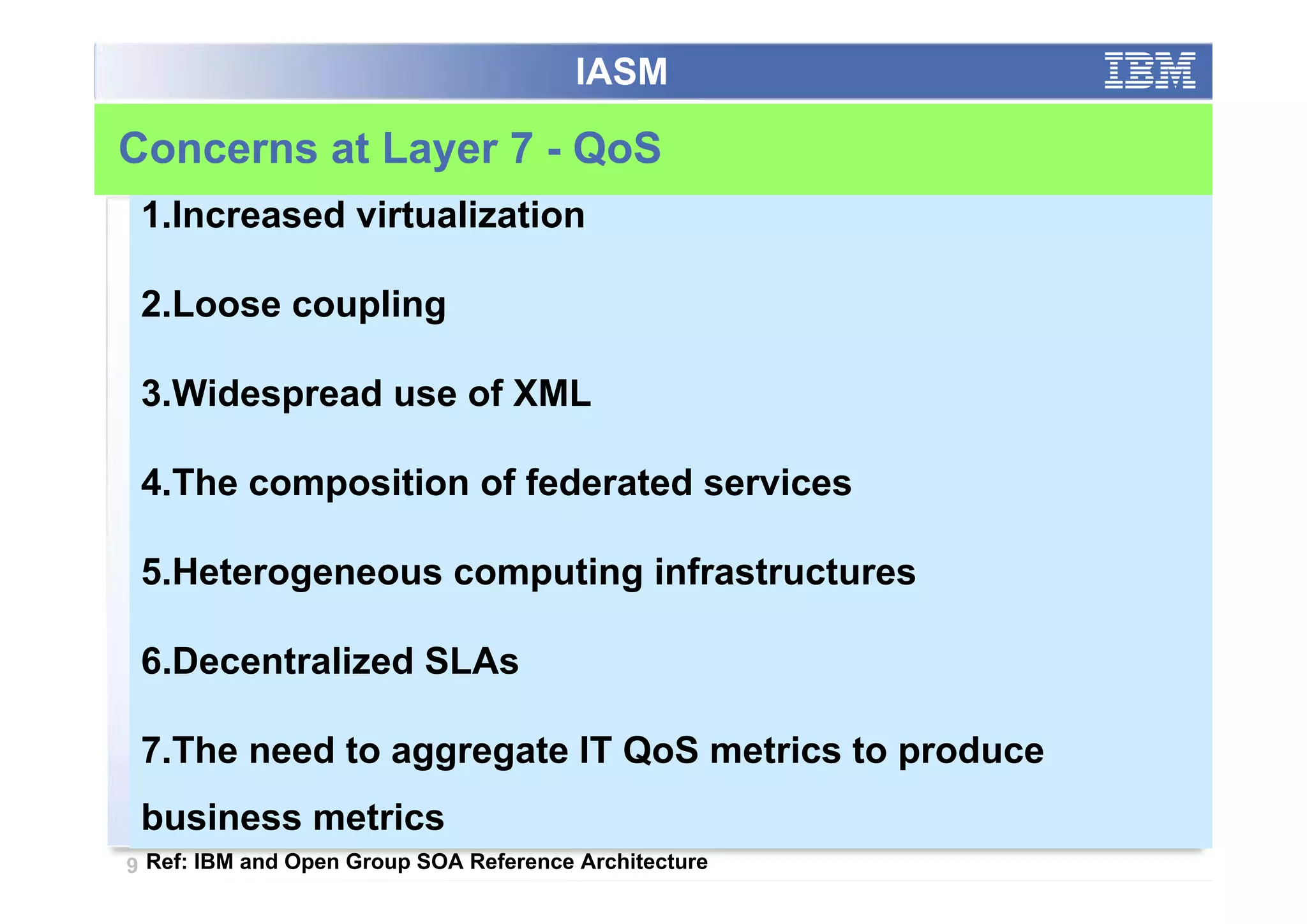
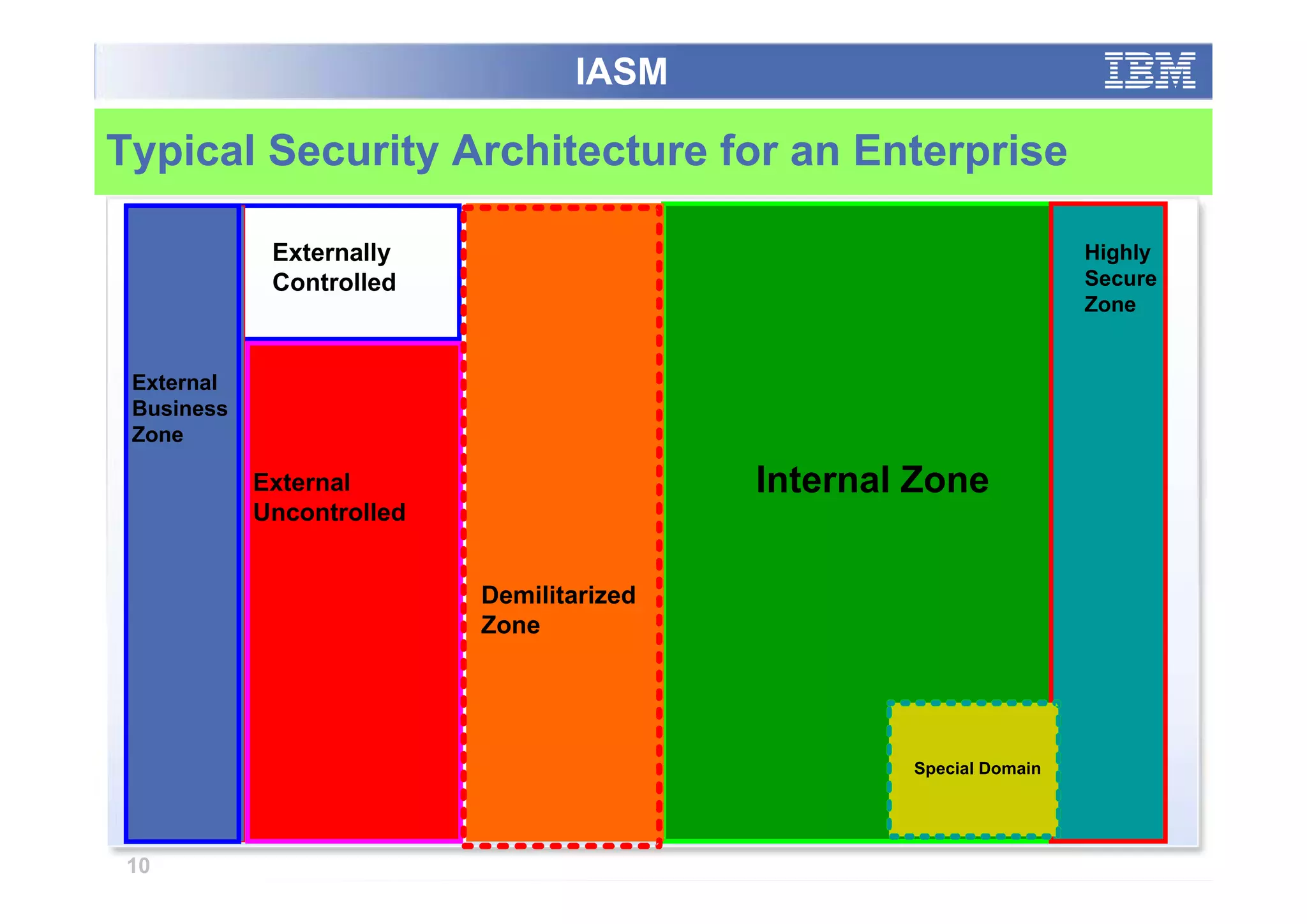
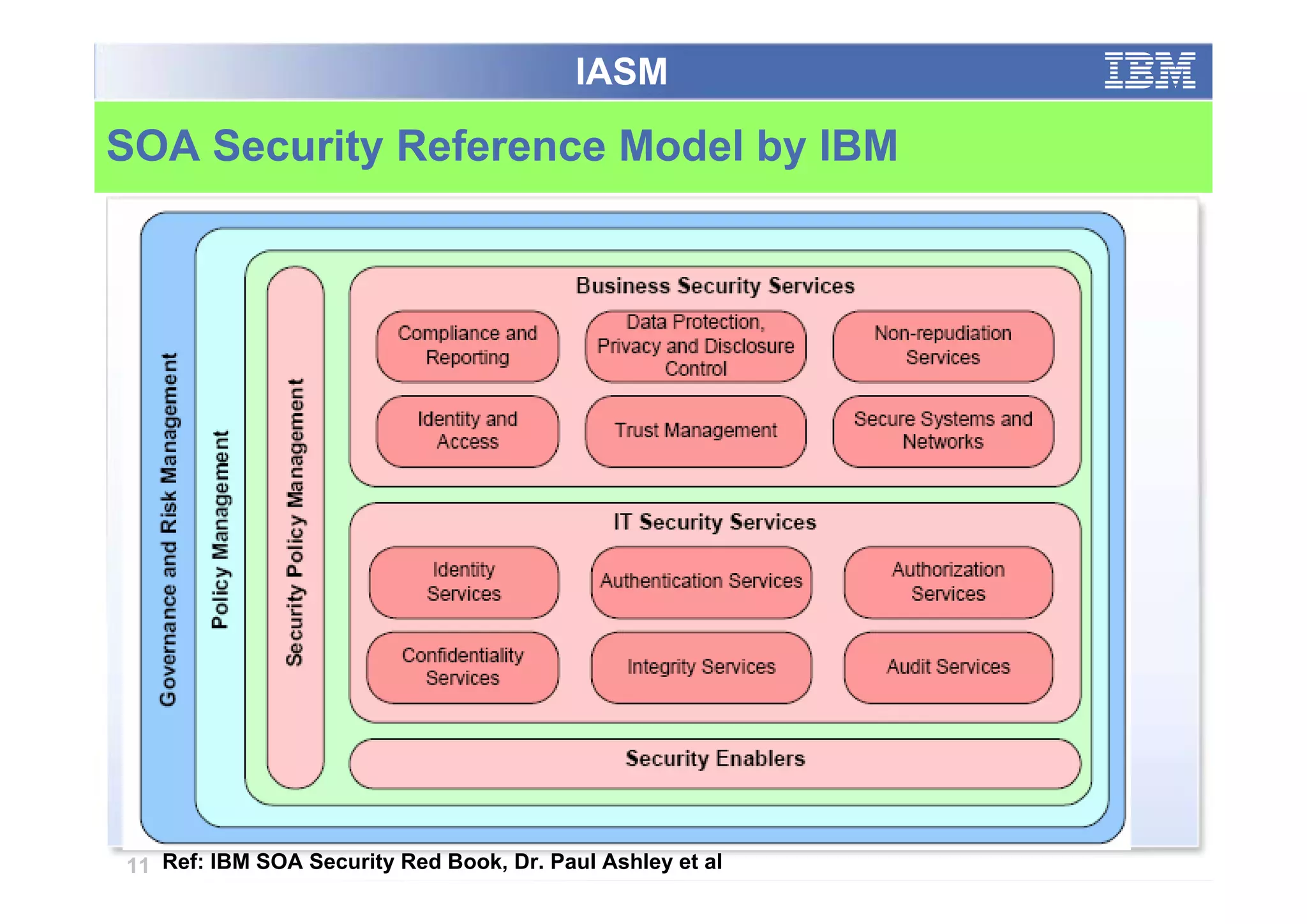
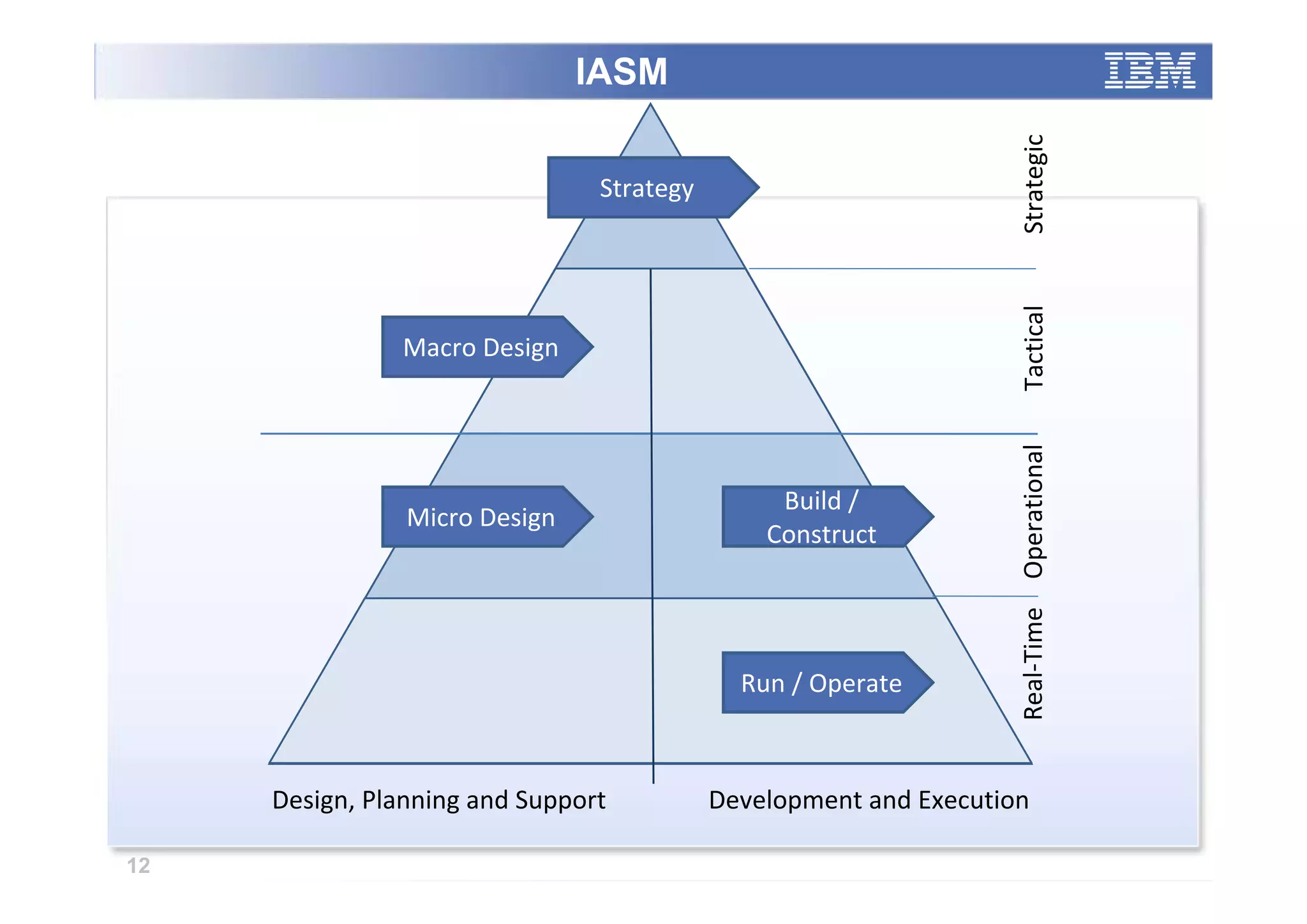
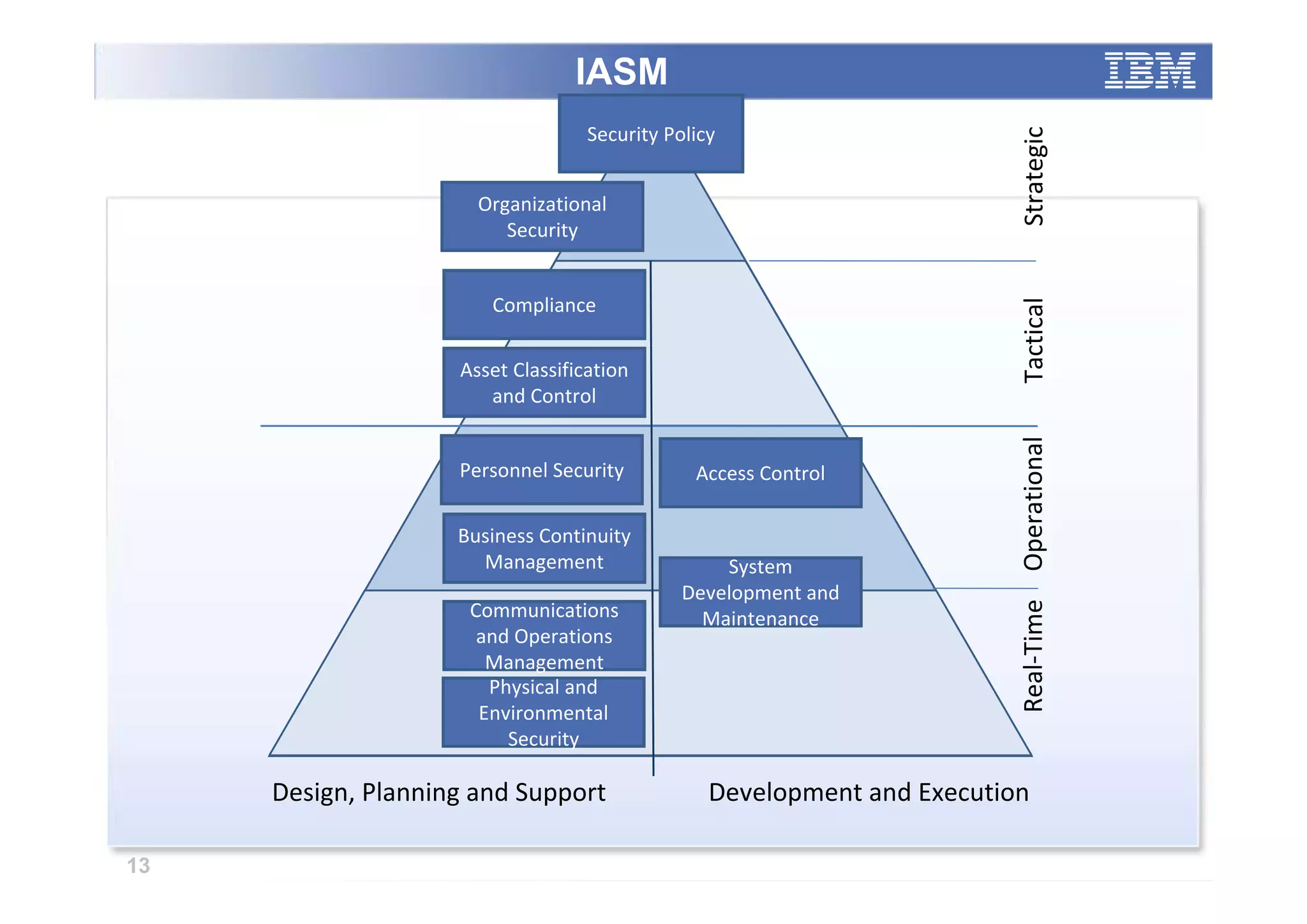
The paper analyzes governance roles in service-oriented architecture (SOA) security at a macro level, mapping elements to a governance structure across four organizational decision-making levels. It proposes a prescriptive model that integrates theoretical frameworks with practical industry experience, highlighting the importance of clear role definitions and standard practices like SOGP and ISO/IEC 17799. The study emphasizes an agile governance model to effectively manage security requirements in complex enterprise systems.