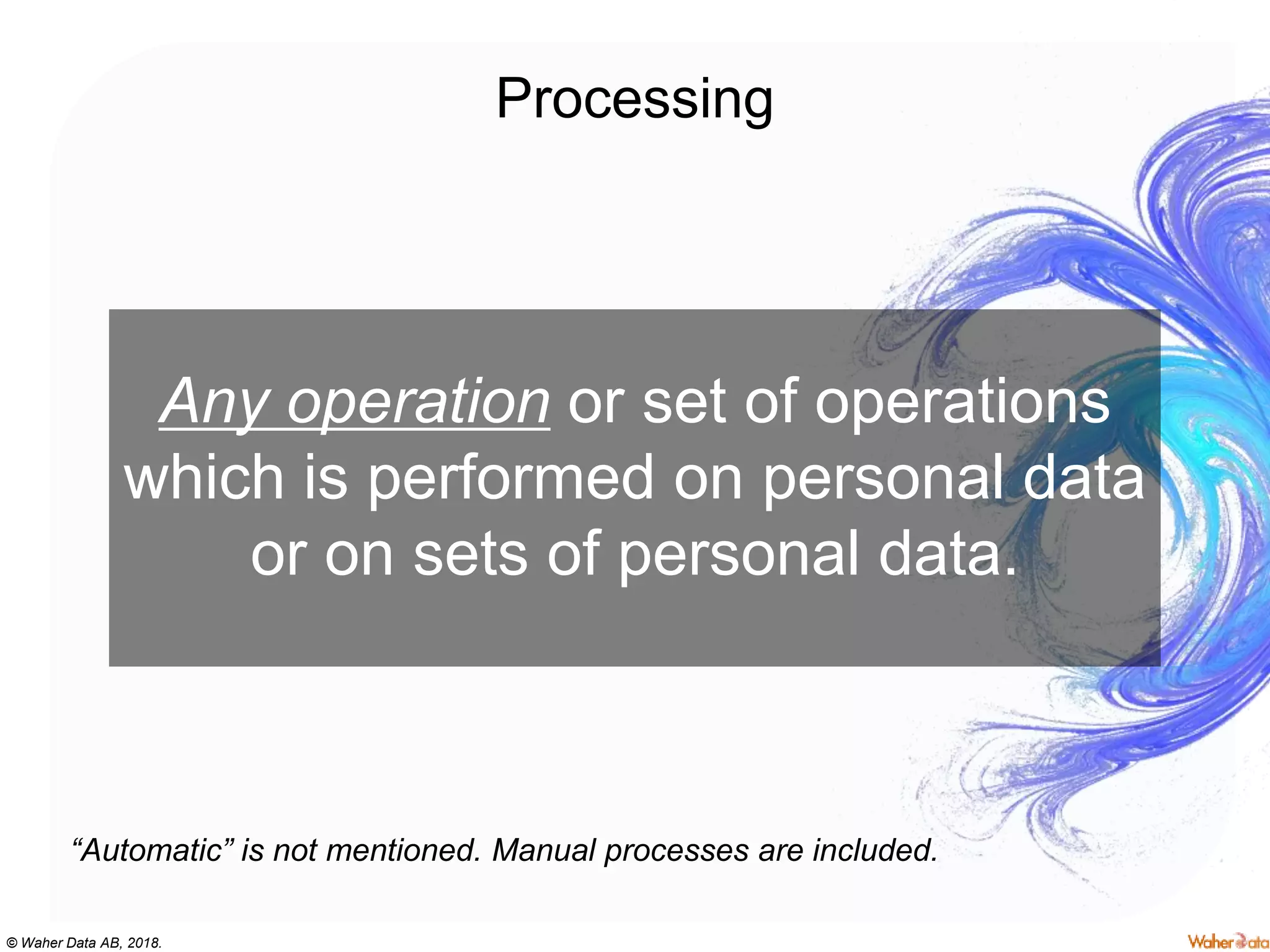
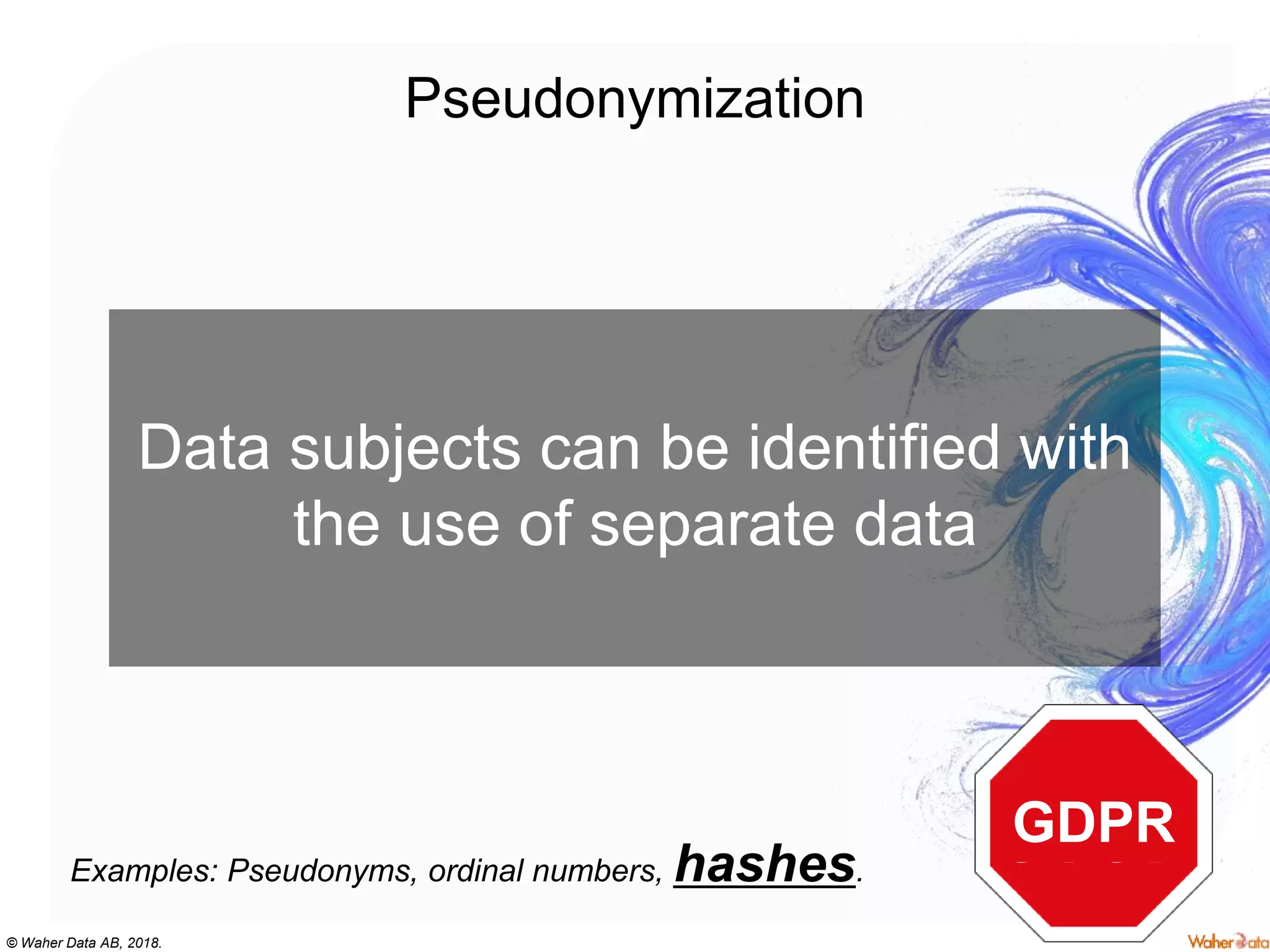
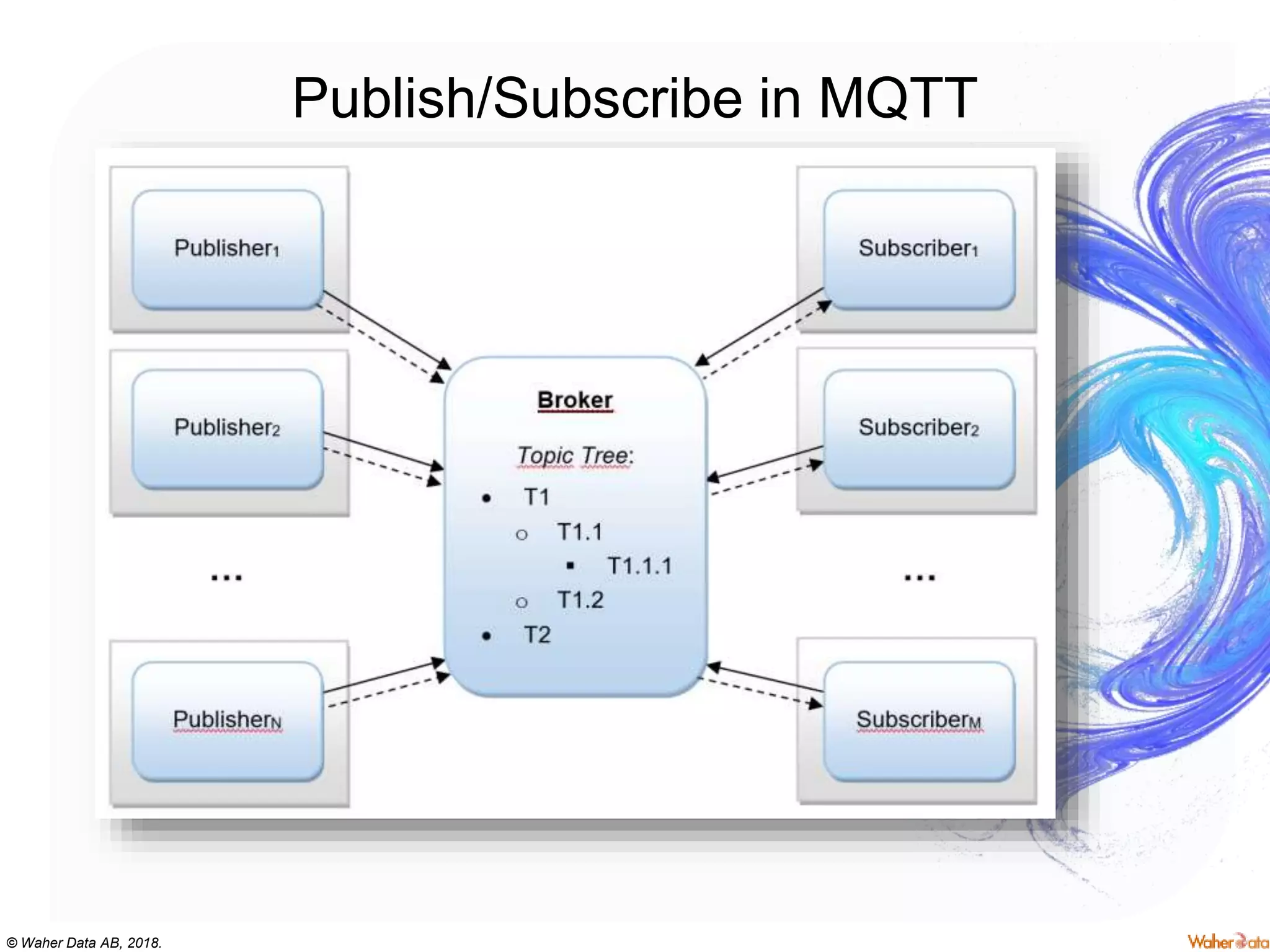
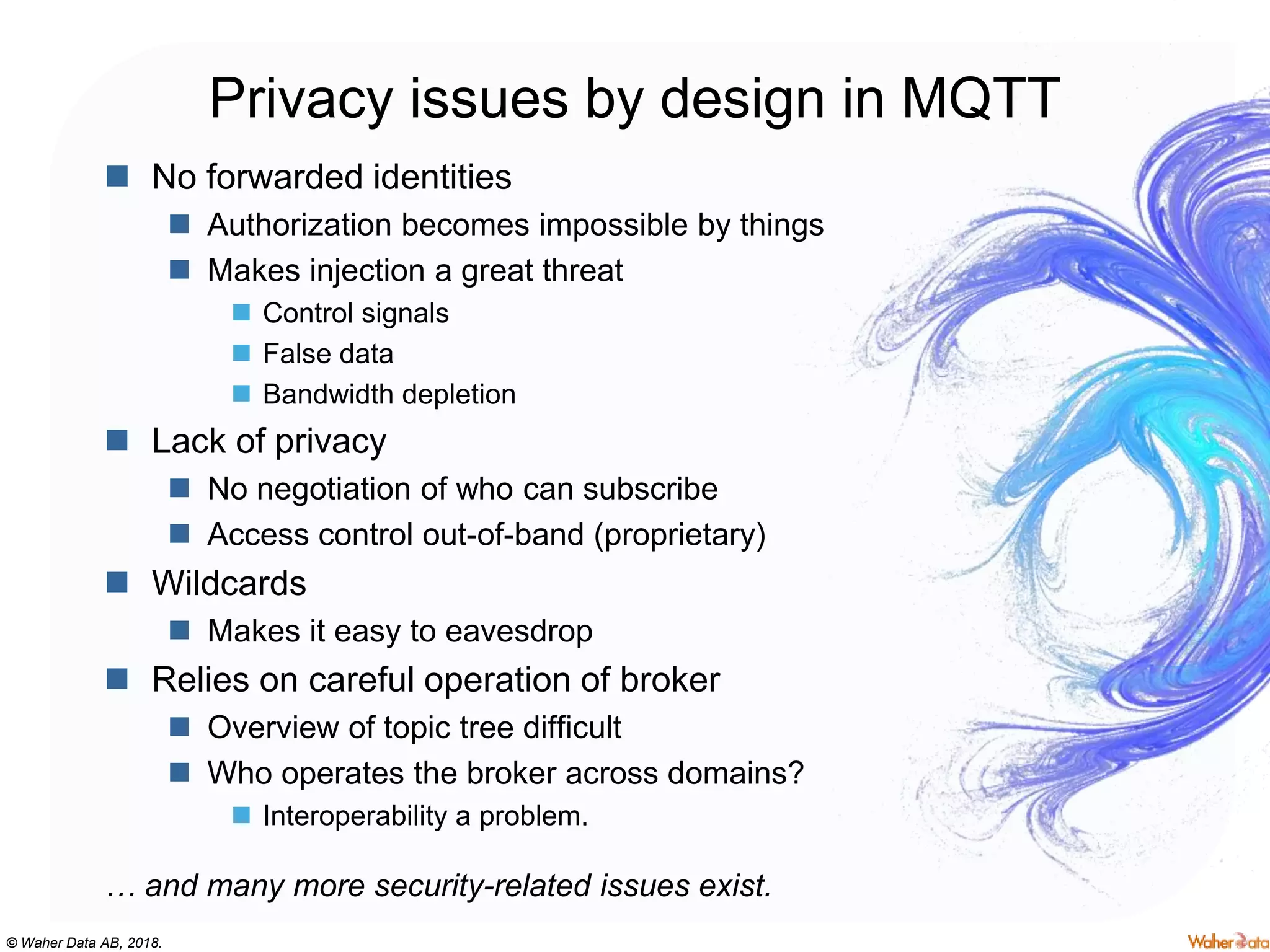
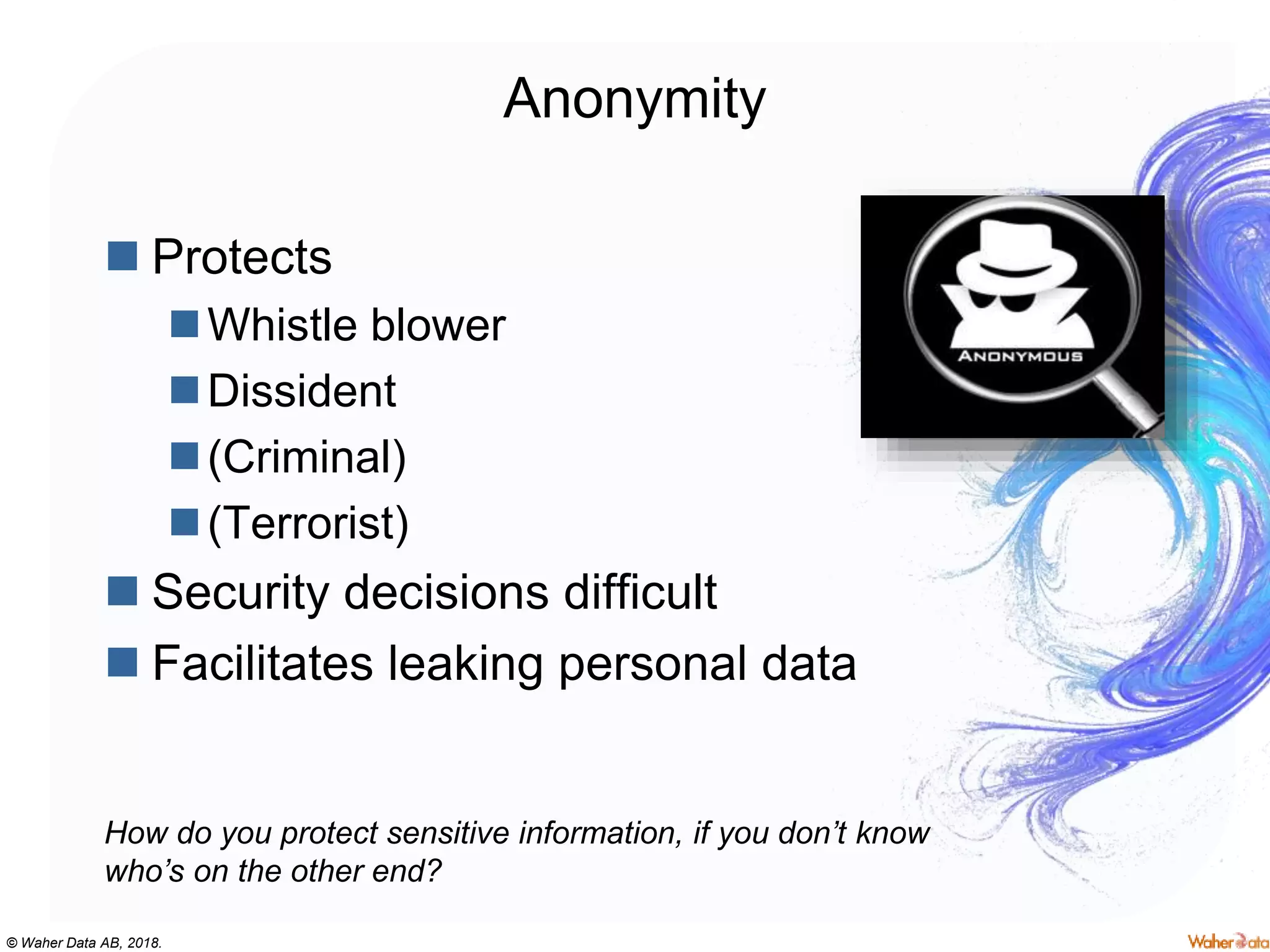
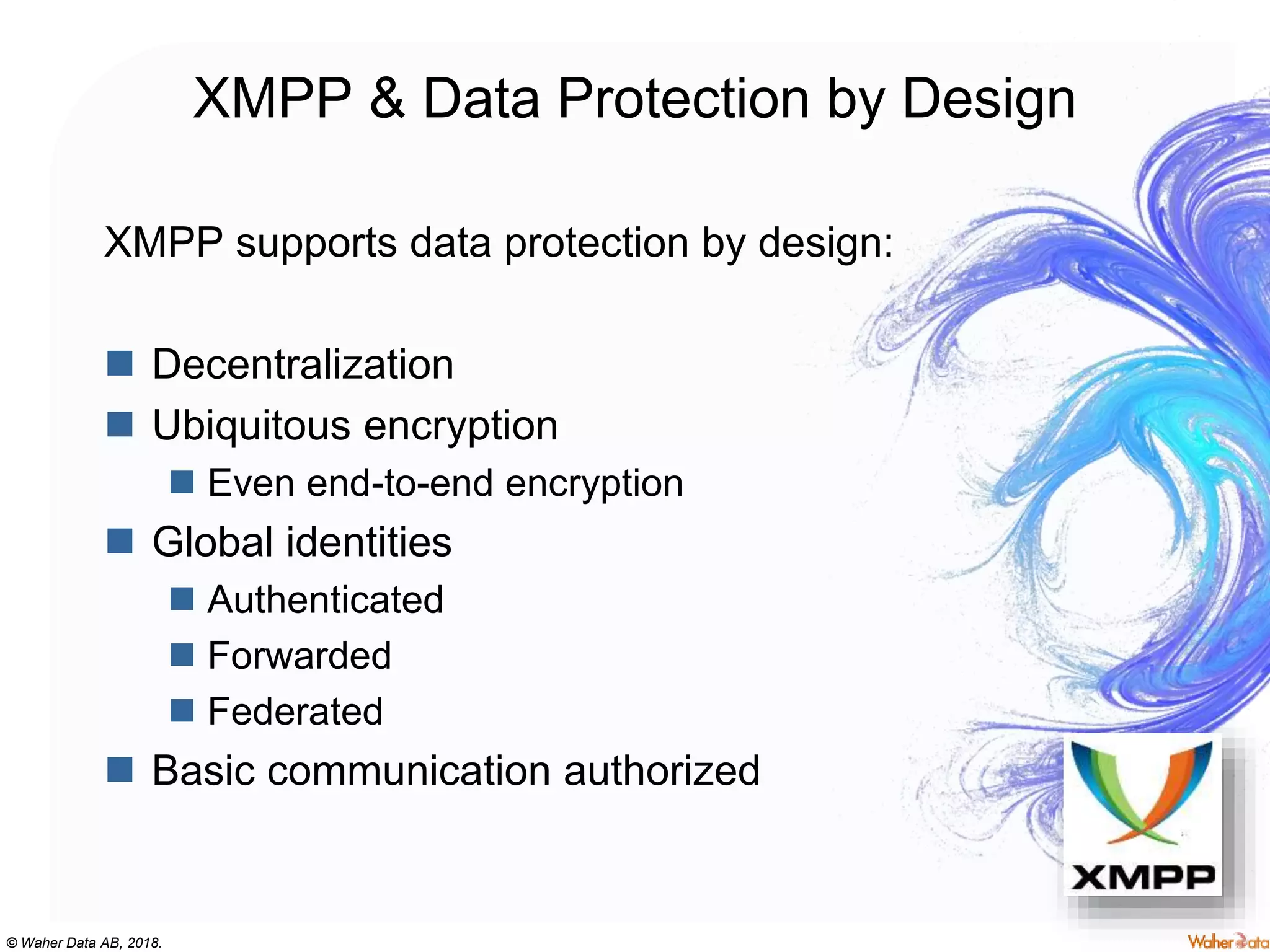
The document discusses privacy concerns within the context of smart cities, particularly highlighting the implications of surveillance systems like China's social credit system and the GDPR's role in protecting personal data. It emphasizes the need for privacy by design and ownership of data while critically examining technologies that either hinder or facilitate privacy protection. Furthermore, it explores various technologies and solutions to enhance privacy, such as decentralized processing and edge computing.