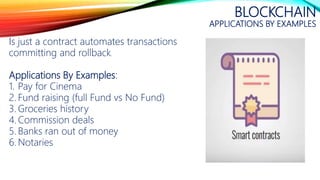
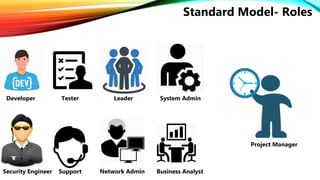
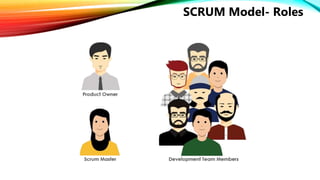
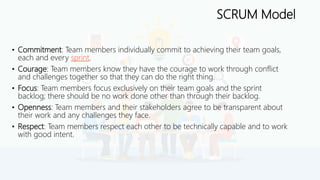
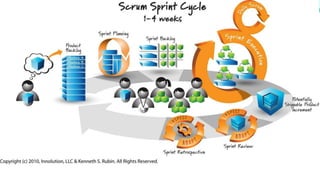
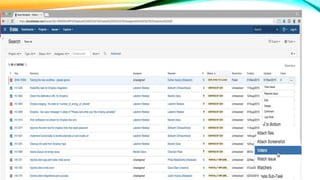
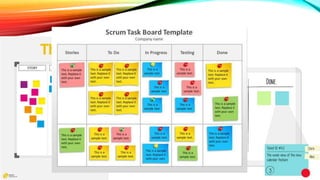
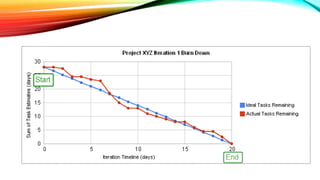
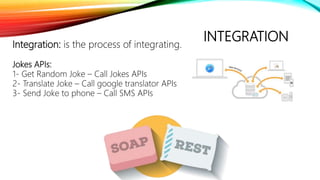
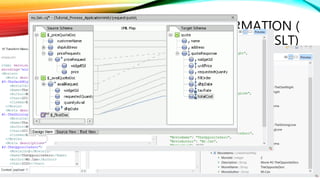
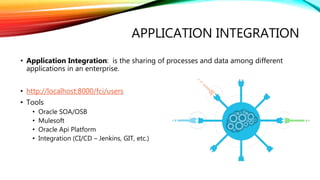
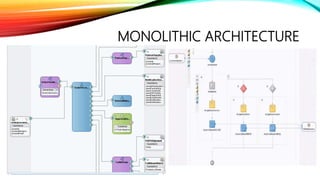
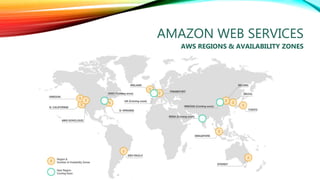
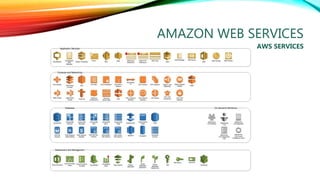
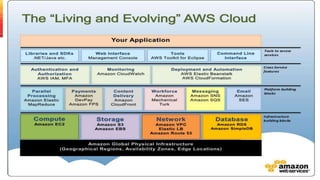
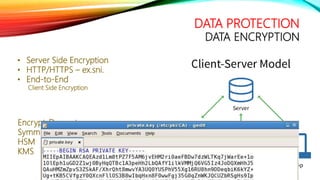
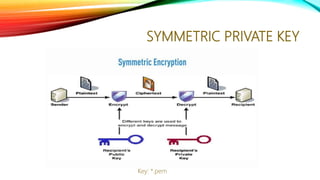
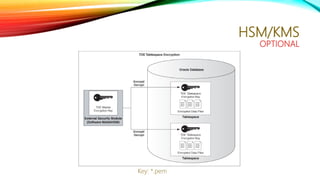
The document details a comprehensive overview of middleware and cloud technologies, highlighting the author's extensive experience and qualifications in the field. It covers software engineering processes like Agile and Scrum, emphasizing iterative development, integration and microservices, cloud computing essentials, and various security measures. Additionally, the document discusses concepts related to data protection, cryptocurrencies, and blockchain technology, illustrating the increasing importance of these areas in modern development practices.




















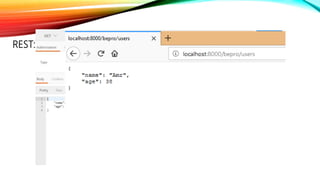

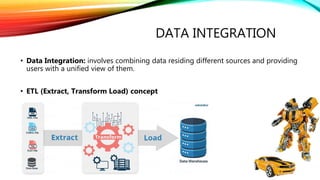
![RESTREST: Representational State Transfer
Client : {
Name: Client_1
Title: Mr.
Domain: Technology
Employees: [
Employee:{
EmpName: Emp_1
EmpTitle: SW Engineer
},
Employee: {
EmpName: Emp_2
EmpTitle: Security Engineer
}
]
}
http://fci/clients/100
http://fci/clients/100/employees
http://fci/clients/100/employees/102](https://image.slidesharecdn.com/session-180108011131/85/Session-33-320.jpg)











































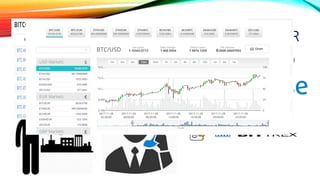
![CURRENCY
• Programmed using C++. – [Electronic]
• Set of transactions recorded into public database & Verified by Miners. –
[Decentralized]
• Ownership is verified by Keys. [Secure]
• Transactions are stored into Block. – [Blockchain, Public Ledger]
• Records are stored on User’s Side. – [P2P – Peer-to-Peer]
• Everyone can see other’s Bitcoins Masked by VK(PK)
• Bitcoin equals 17750 USD now.
• There are 700 Altcoins.](https://image.slidesharecdn.com/session-180108011131/85/Session-98-320.jpg)






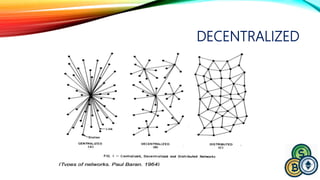
![CENTRALIZED DIGITAL CURRENCY
Double-spending is a potential flaw in a digital
cash scheme in which the same single digital token can
be spent more than once. This is possible because a
digital token consists of a digital file that can be duplicated
or falsified.[1]
Example:
You go to Starbucks and order a cappuccino worth $10.
You pay in cash. Now that $10 in cash is in the cash vault
of Starbucks. By all means, you simply cannot spend the
same $10 somewhere else to make another purchase.](https://image.slidesharecdn.com/session-180108011131/85/Session-107-320.jpg)
![CRUPTOCURRENCT
• Programmed using C++. – [Electronic]
• Set of transactions recorded into public database & Verified by Miners. –
[Decentralized]
• Ownership is verified by Keys. [Secure]
• Transactions are stored into Block. – [Blockchain, Public Ledger]
• Records are stored on User’s Side. – [P2P – Peer-to-Peer]
• Everyone can see other’s Bitcoins Masked by VK(PK)
• Bitcoin equals 17750 USD now.
• There are 700 Altcoins.](https://image.slidesharecdn.com/session-180108011131/85/Session-108-320.jpg)
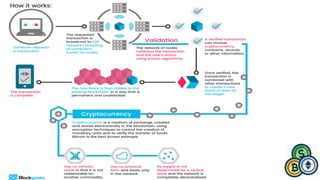
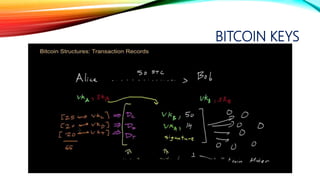

![DOUBLE SPEND CONFIRMATION
Double-spending is a potential flaw in a digital cash scheme in which the same single digital token can be spent
more than once. This is possible because a digital token consists of a digital file that can be duplicated or falsified.[1]
1- Alice Purchases a product from Bob
2- Alice will create two bitcoin transactions; one that include payments
for the product or service he seeks from Bob, the other pays the same
amount to himself/herself.
3- Alice will broadcast the “A to B” transaction and then
start secretly mining the block that includes the “A to A”
payment.
Once he/she successfully mines this block, further blocks will be added to it.
4- Bob will give the service or product to Alice,
on seeing the transaction on the public ledger, whether or not the
transaction was confirmed, if he/she doesn’t wait for the confirmation
to send the products.
5- Alice can be lucky and the attack succeeds ,](https://image.slidesharecdn.com/session-180108011131/85/Session-116-320.jpg)
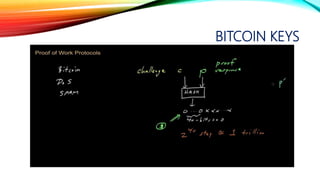
![6 CONFIRMATIONS
Double-spending is a potential flaw in a digital
cash scheme in which the same single digital token can
be spent more than once. This is possible because a
digital token consists of a digital file that can be duplicated
or falsified.[1]
Example:
You go to Starbucks and order a cappuccino worth $10.
You pay in cash. Now that $10 in cash is in the cash vault
of Starbucks. By all means, you simply cannot spend the
same $10 somewhere else to make another purchase.](https://image.slidesharecdn.com/session-180108011131/85/Session-117-320.jpg)


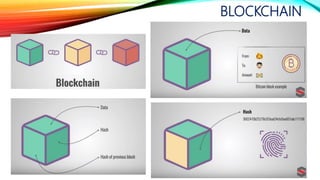
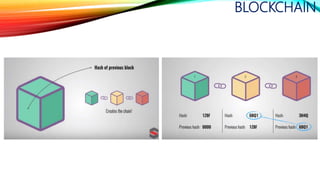
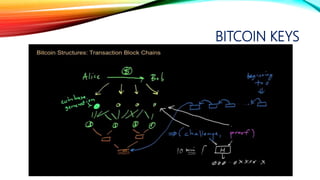
![BLOCKCHAIN
originally block chain,[4][5] is a continuously growing list
of records, called blocks, which are linked and secured
using cryptography.[1][6] Each block typically contains
a hash pointer as a link to a previous
block,[6] a timestamp and transaction data.[7] By design,
blockchains are inherently resistant to modification of
the data. Harvard Business Review defines it as "an
open, distributed ledger that can record transactions
between two parties efficiently and in a verifiable and
permanent way."[8] For use as a distributed ledger, a
blockchain is typically managed by a peer-to-
peer network collectively adhering to a protocol for
validating new blocks. Once recorded, the data in any
given block cannot be altered retroactively without the
alteration of all subsequent blocks, which requires
collusion of the network majority.](https://image.slidesharecdn.com/session-180108011131/85/Session-120-320.jpg)