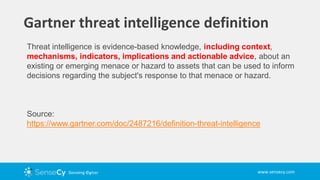
This presentation discusses the difference between cyber threat information and cyber threat intelligence. Cyber threat information provides a large amount of data like IP addresses and malware signatures but does not provide context or actionable advice. Cyber threat intelligence involves analyzed and refined information that is specific and useful for making security decisions, such as indicators that directly pertain to a company's assets and potential hacktivist attacks planned against the organization. The type of intelligence received is often dictated by the cybersecurity tools used.