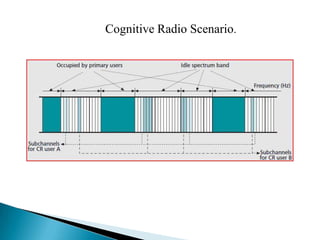
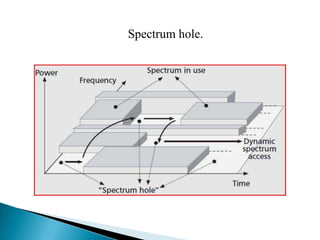
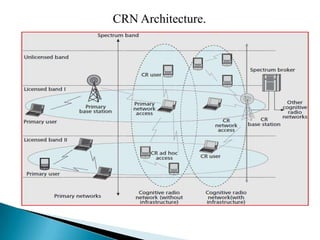
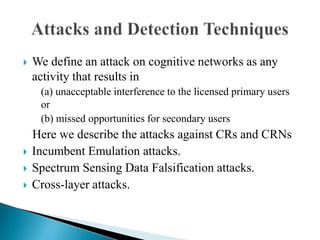
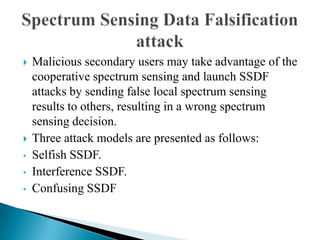
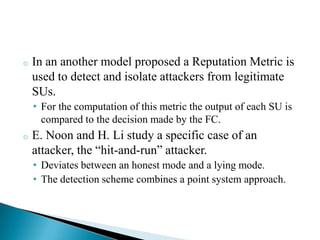
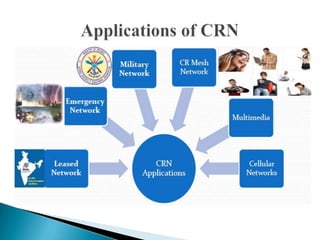
This document discusses cognitive radio networks and security issues within them. It begins with an introduction to cognitive radio and its ability to identify unused spectrum. It then describes two common attacks on cognitive radio networks: incumbent emulation attacks and spectrum sensing data falsification attacks. The document reviews several detection techniques for these attacks, including evaluating trust values and consistency, using reputation metrics, and analyzing statistics. Finally, it discusses some applications and advantages of cognitive radio networks, as well as topics for further research.