Embed presentation
Downloaded 25 times

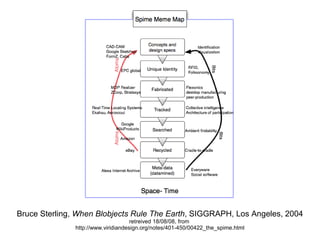

























Bruce Sterling's work discusses the implications of pervasive computing on privacy, highlighting concerns such as the complexity and limited application of systems designed to manage digital privacy. The virtual wall model aims to address these issues, although it raises fears reminiscent of surveillance by central authorities. Overall, while the system functions, it faces challenges that need careful consideration.


























