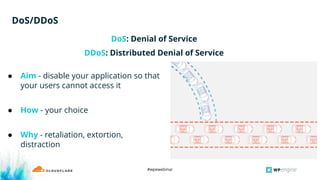
The webinar covers essential aspects of securing web infrastructure, highlighting common security threats like application vulnerabilities, account takeover, and denial of service (DoS) attacks. It emphasizes the importance of proactive measures such as SSL encryption, using managed web application firewalls, and maintaining updated software to mitigate risks. Participants will also have access to Q&A sessions and additional resources post-webinar.