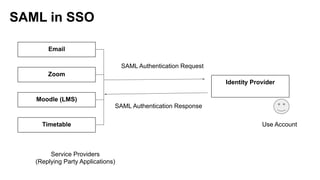
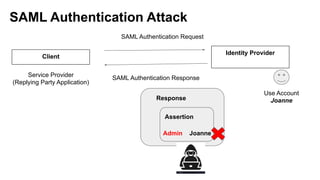
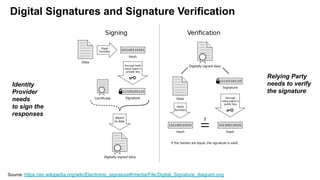
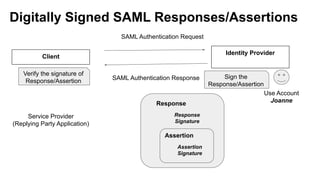
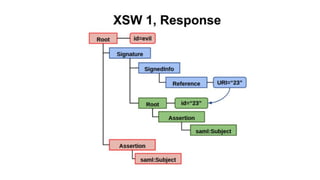
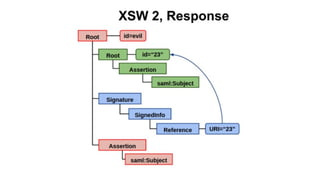
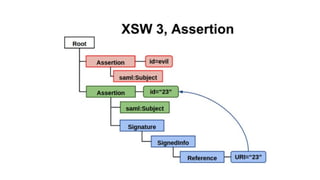
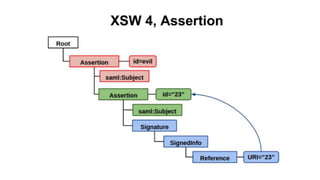
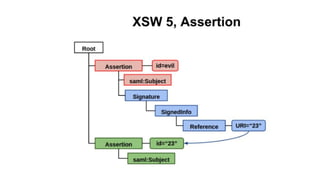
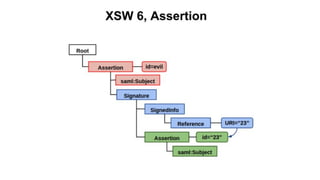
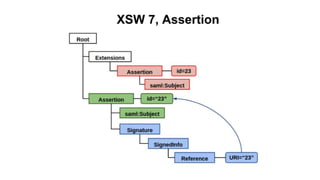
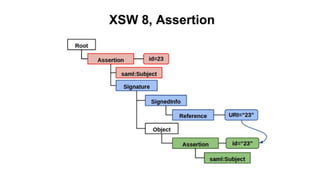
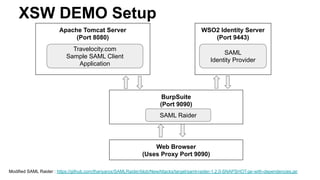
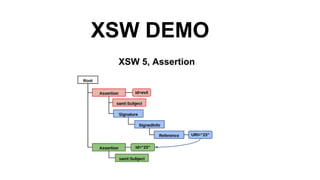
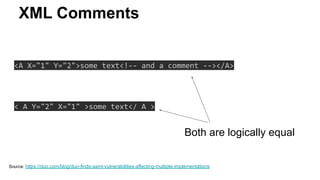
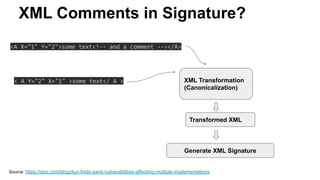
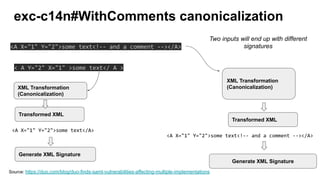
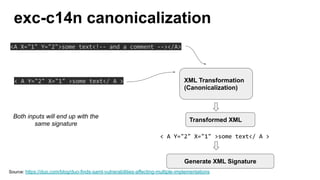
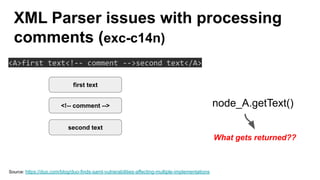
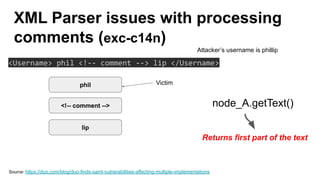
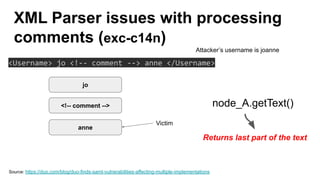
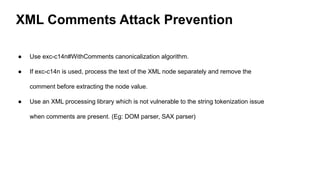
The document discusses security measures for Single Sign-On (SSO) using SAML, addressing vulnerabilities like XML Signature Wrapping (XSW) attacks and the importance of digital signatures. It emphasizes the need for penetration testing and implementations that prevent XSW, including using third-party libraries that support these features. The document also mentions potential XML parser issues with comments in signatures and recommends best practices for preventing associated attacks.