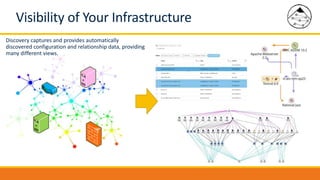
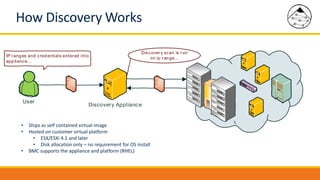
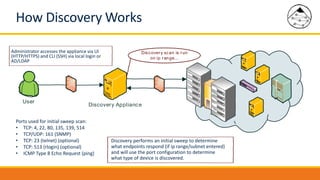
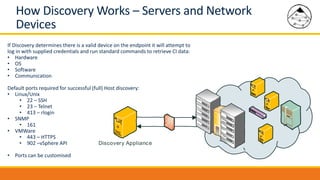
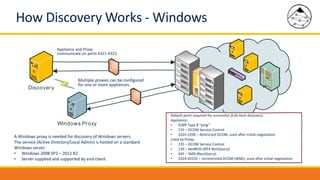
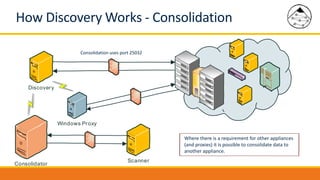
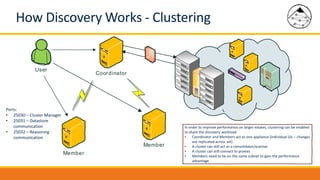
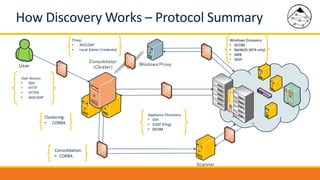
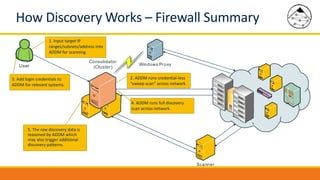
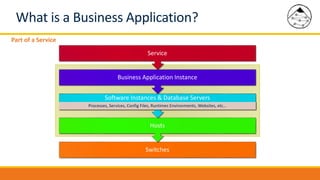
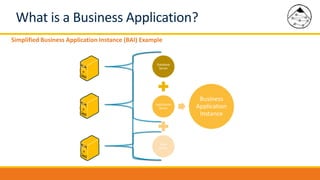
BMC Discovery is an agentless discovery and dependency mapping tool that automatically discovers configuration and relationship data across an IT infrastructure. It provides visibility into hardware, software, applications and their dependencies. BMC Discovery works by running scans from a virtual appliance using supplied credentials to retrieve configuration information. It analyzes the data to map relationships and can integrate with a CMDB. Security features include encrypted credential storage and secure communications. Prerequisites for deployment include virtual appliances, a Windows proxy server, and credentials for systems being discovered.