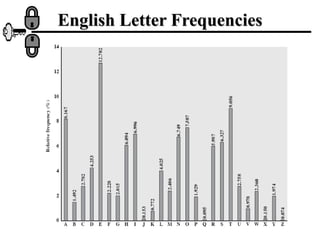
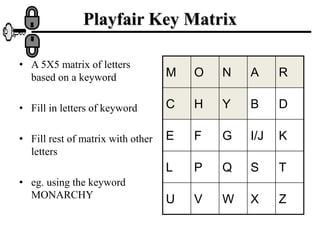
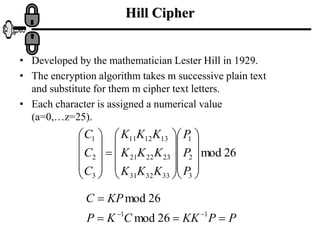
The document discusses various ciphers and their security, including monoalphabetic substitution ciphers, the Playfair cipher, and the Hill cipher. It explains that while monoalphabetic ciphers have many possible keys, the regularities of language allow them to be broken through frequency analysis of letters in the ciphertext. The Playfair cipher improves security by encrypting digrams rather than single letters, but plaintext patterns remain. The Hill cipher encrypts multiple letters together using matrix multiplication, further obscuring the original message.