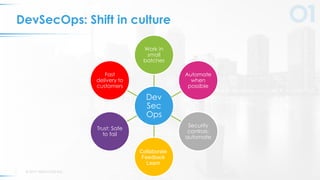
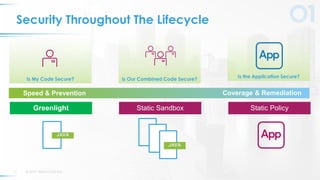
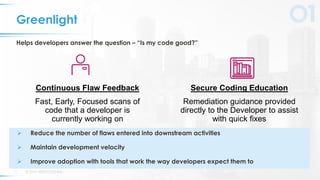
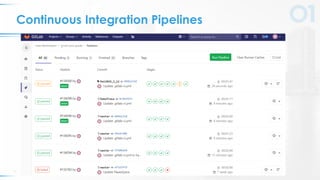
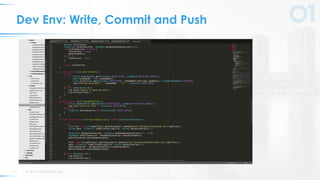
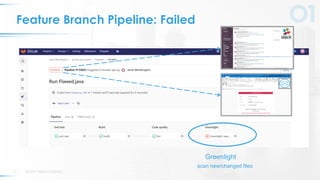
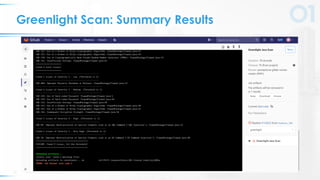
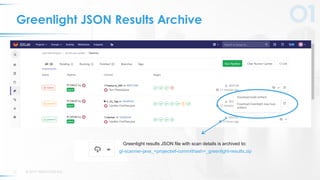
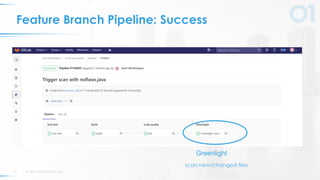
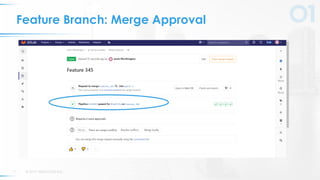
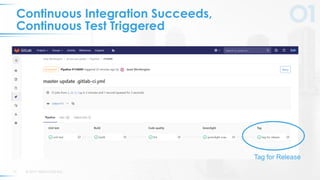
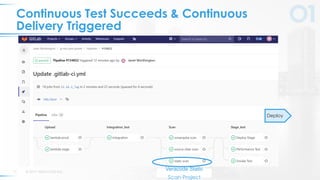
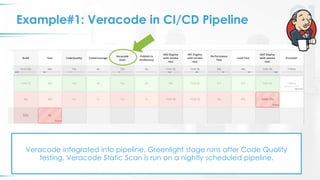
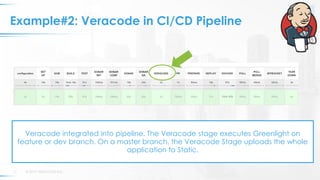
The document presents a comprehensive overview of DevSecOps, emphasizing the integration of security into the development and operations lifecycle. It discusses the benefits of continuous integration and deployment pipelines, highlighting best practices for developers to ensure code security while maintaining development speed. The presentation includes tools like Veracode's Greenlight for real-time flaw feedback and emphasizes collaboration among cross-functional teams.