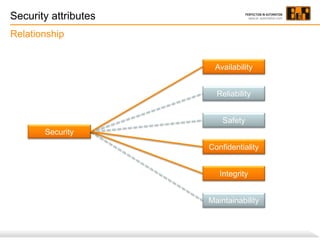
Safety refers to freedom from risk of physical injury or damage to health or property. It is an aspect of dependability, which is the ability of a system to operate as intended. Security refers to preventing illegal or unwanted access or interference with systems. It involves availability, confidentiality, and integrity. Dependability and security are related concepts, with dependability concerning proper operation and security concerning preventing improper access or changes. Functional safety specifically refers to a system operating correctly in response to inputs to manage errors, failures, and environmental changes.









![References
[1] http://en.wikipedia.org/wiki/Dependability
[2] http://www.iec.ch/functionalsafety
[3] IEC/TS 62443-1-1 Industrial communication networks – Network
and system security – Part 1-1: Terminology, concepts and models
[4] A. Avizienis, J.-C. Laprie and B. Randell: Fundamental Concepts
of Dependability. Research Report No 1145, LAAS-CNRS, April
2001
[5] http://www.open-safety.org](https://image.slidesharecdn.com/safetyvssecurity-131118103311-phpapp01/85/Safety-versus-security-12-320.jpg)
