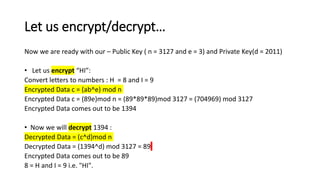
RSA is an asymmetric encryption algorithm that uses public and private key pairs for encryption and decryption. It involves key generation to create the public and private keys, and encryption and decryption functions that use the keys to scramble and unscramble data. Digital signatures generated using RSA can verify the authenticity of electronically sent messages.