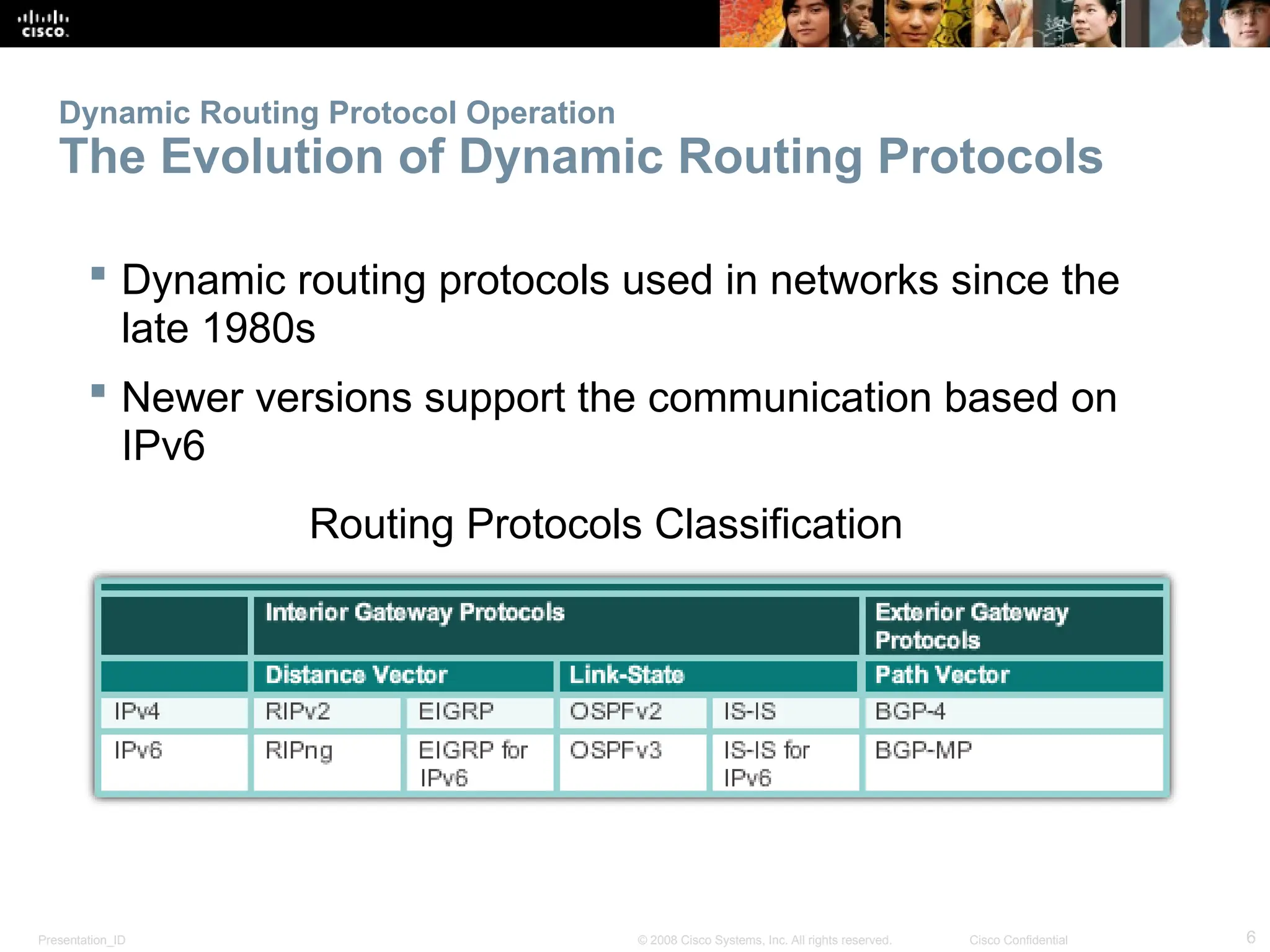
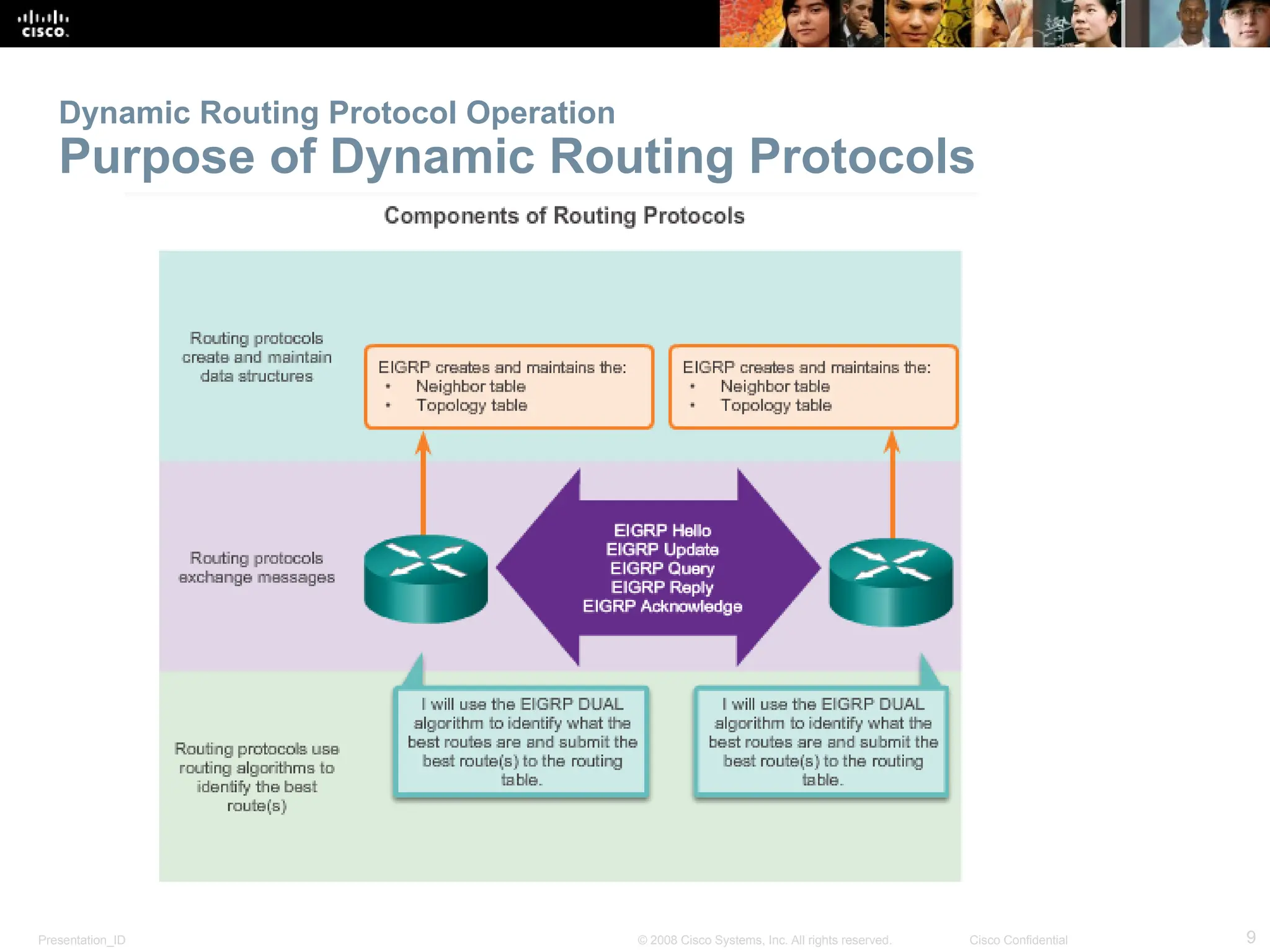
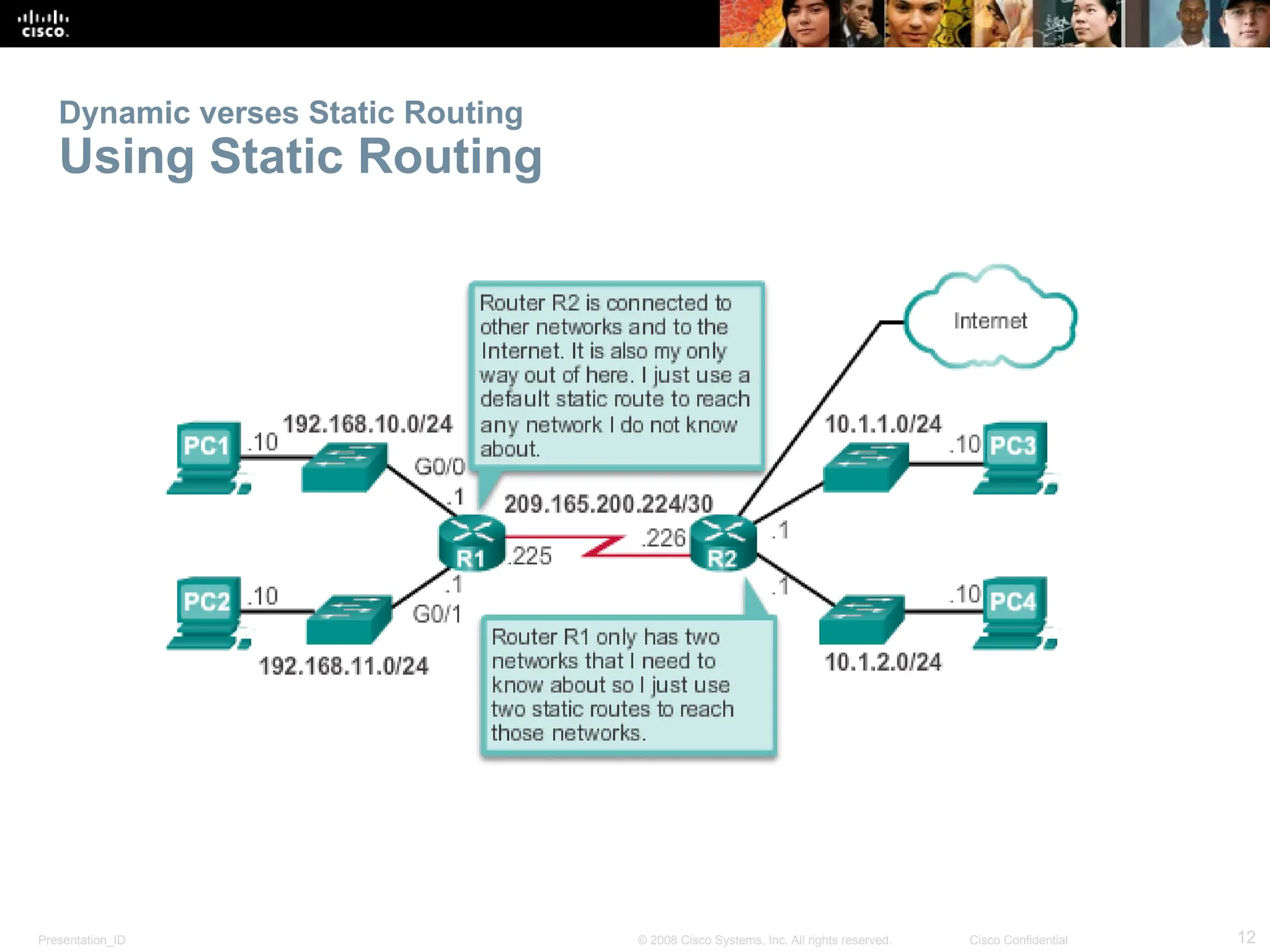
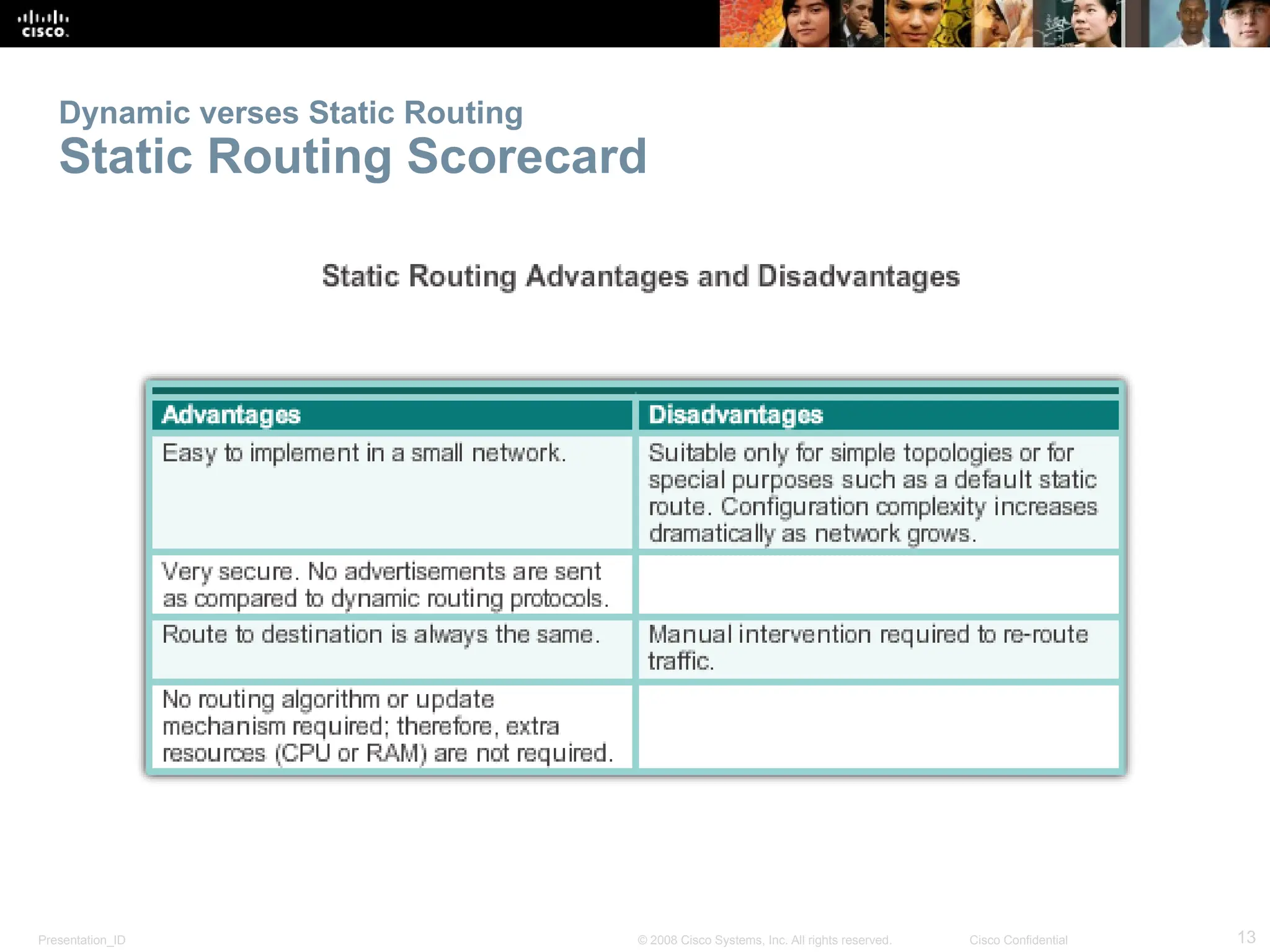
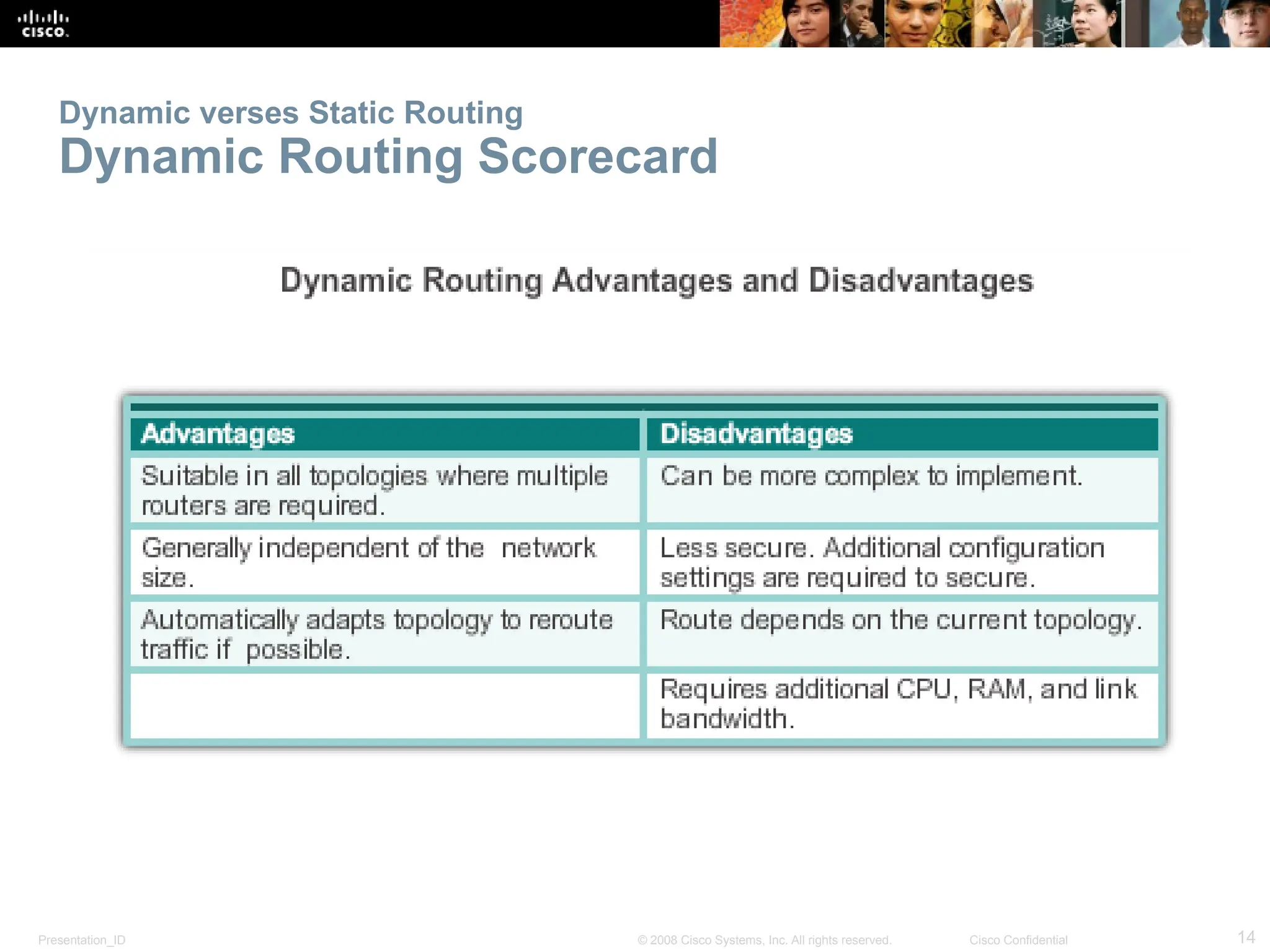
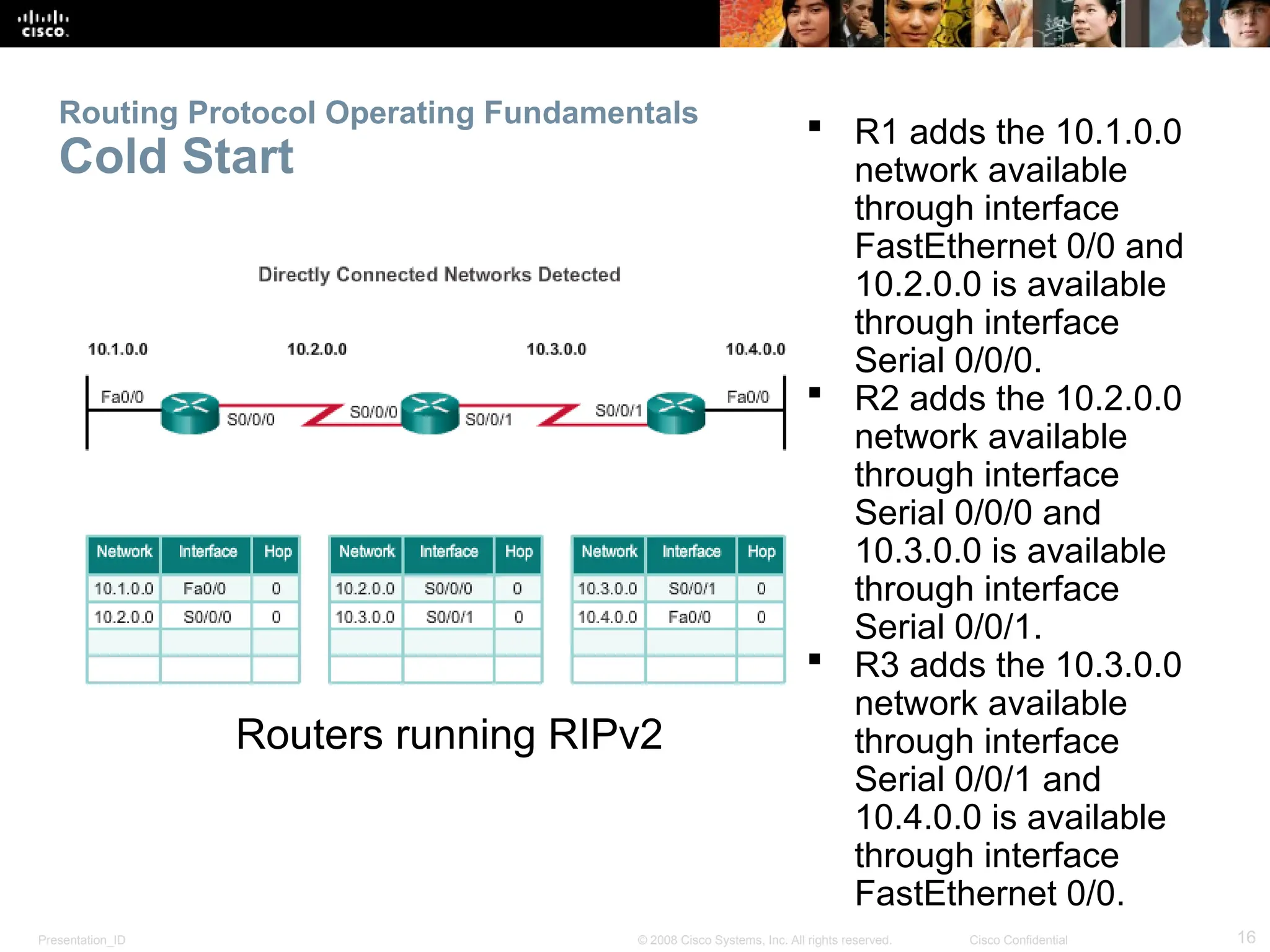
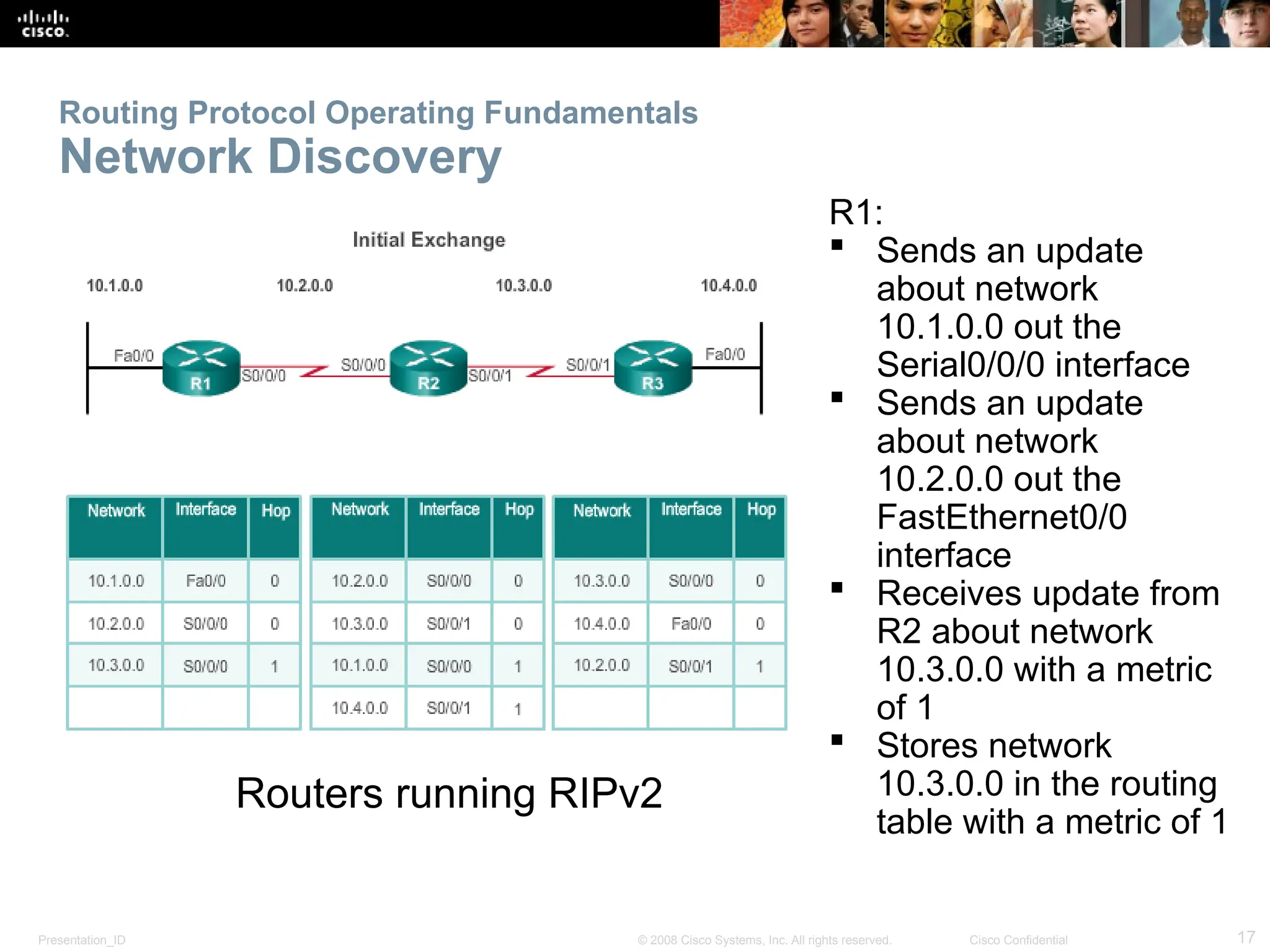
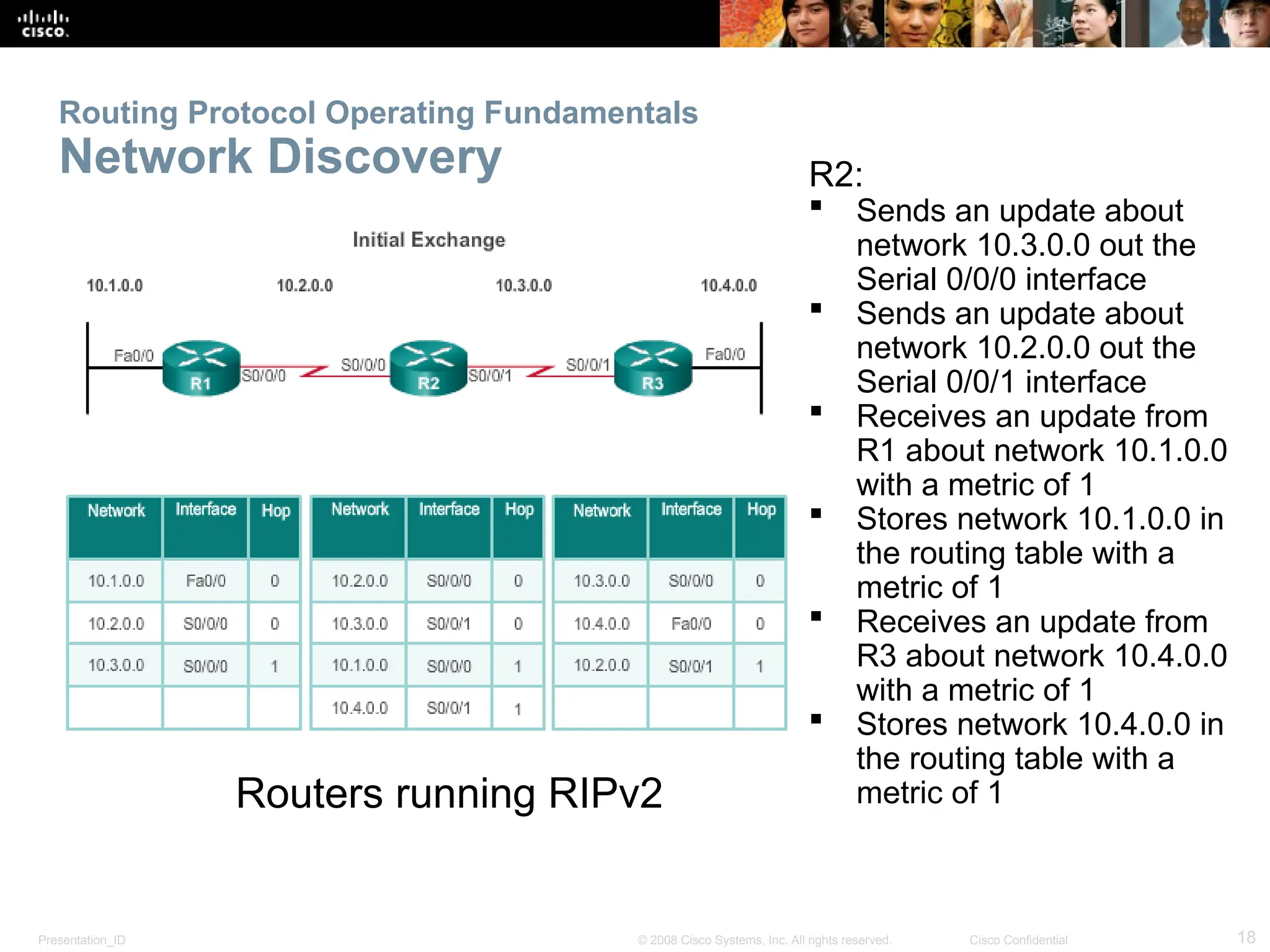
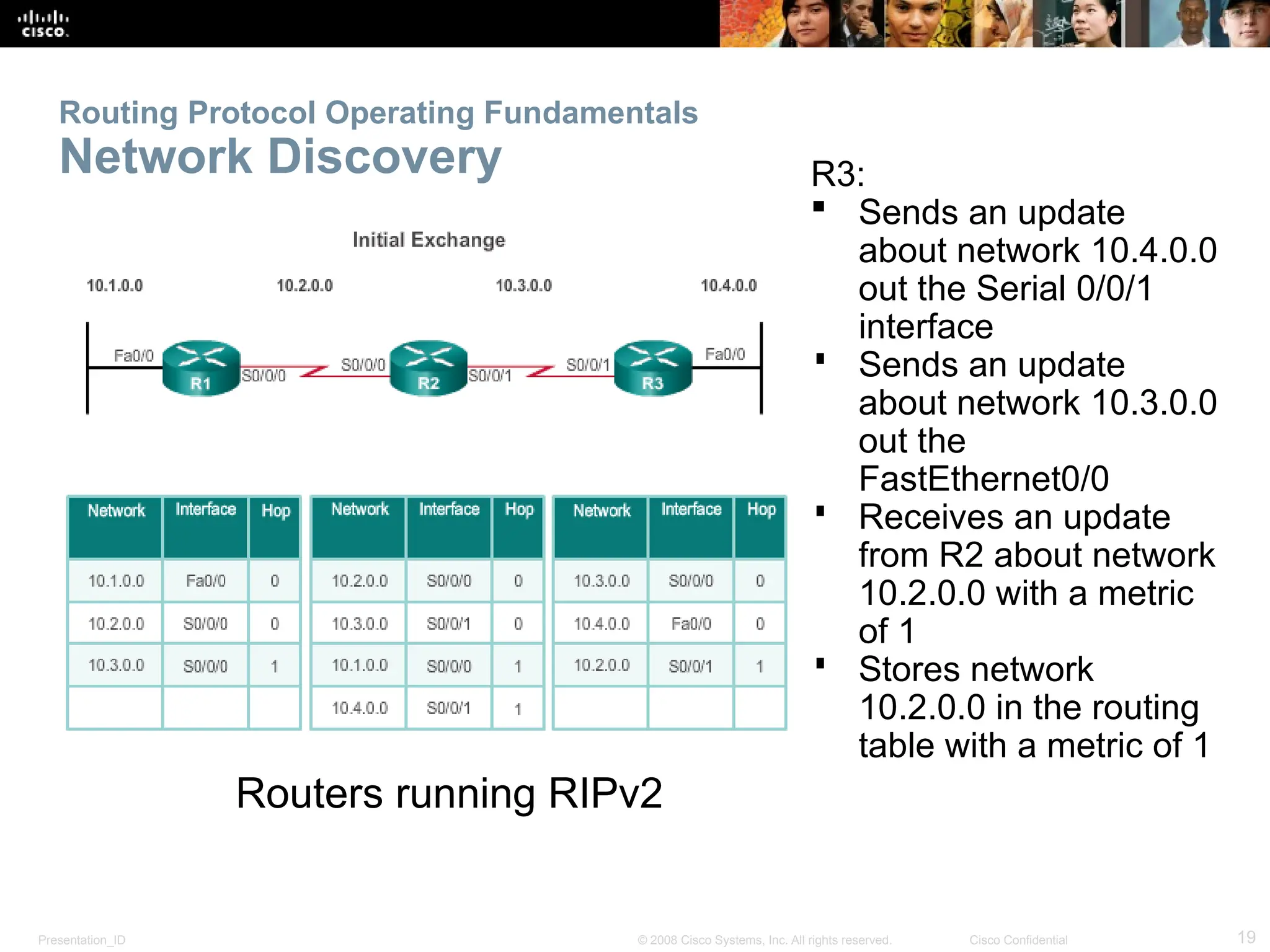
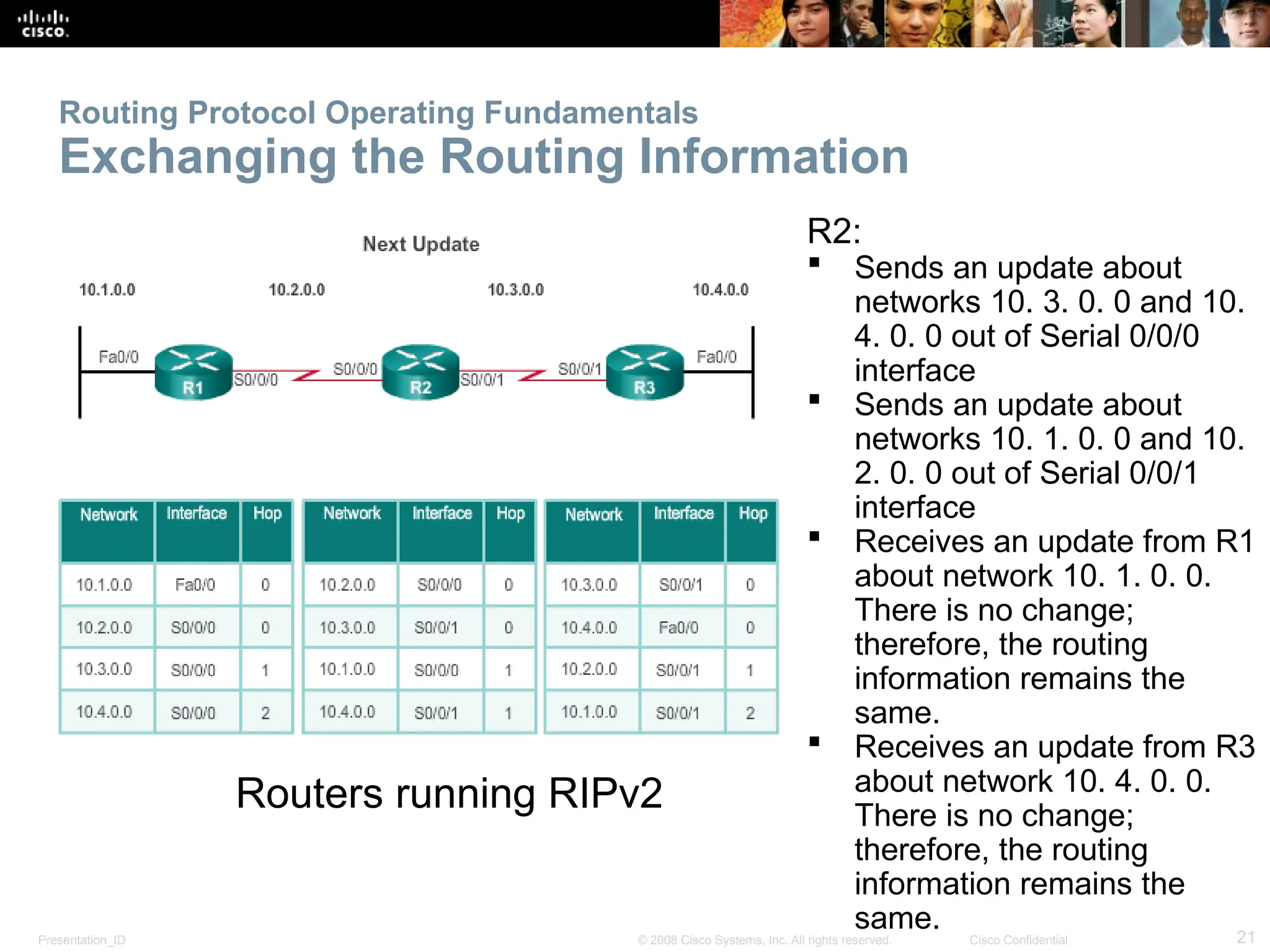
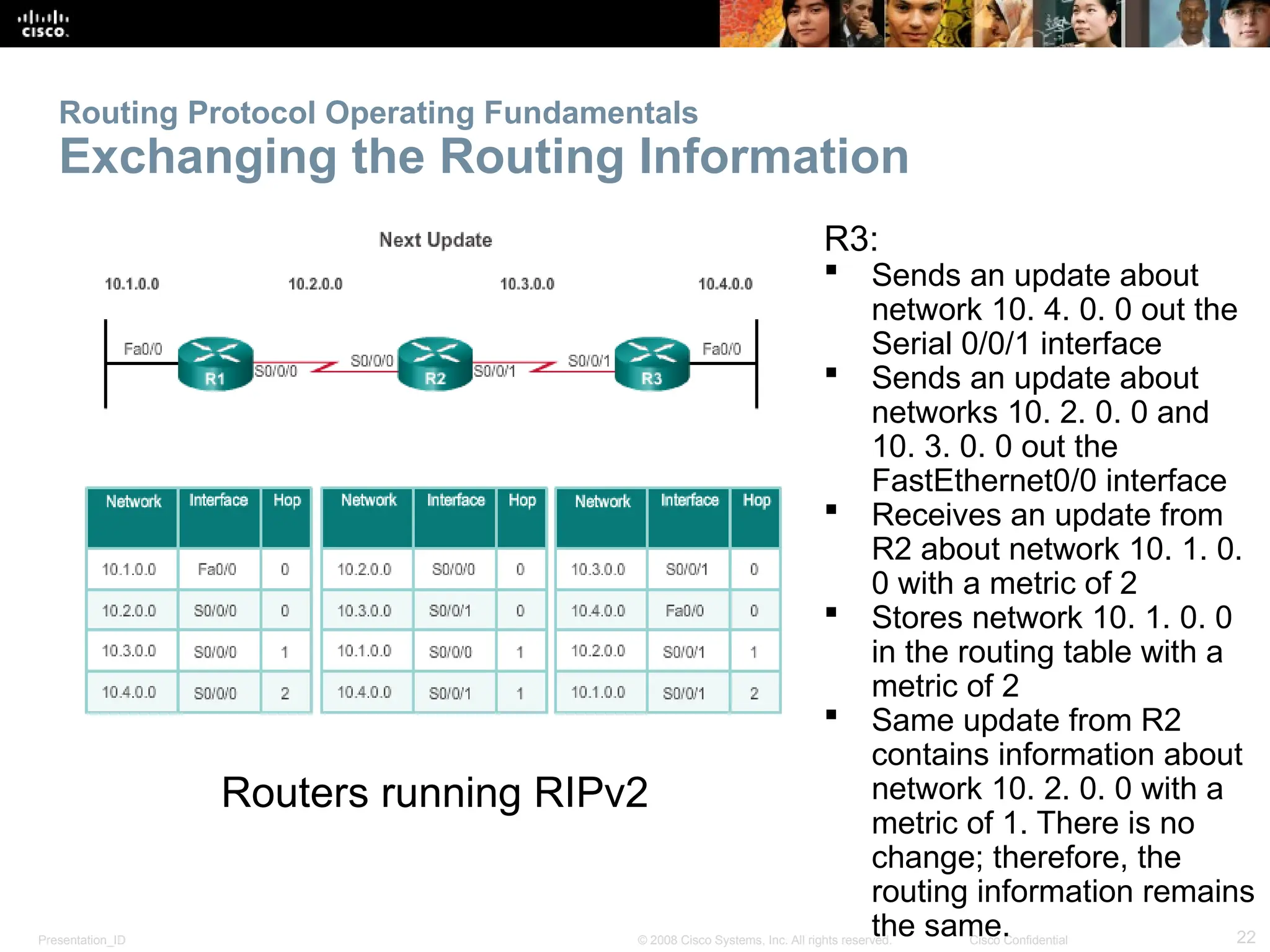
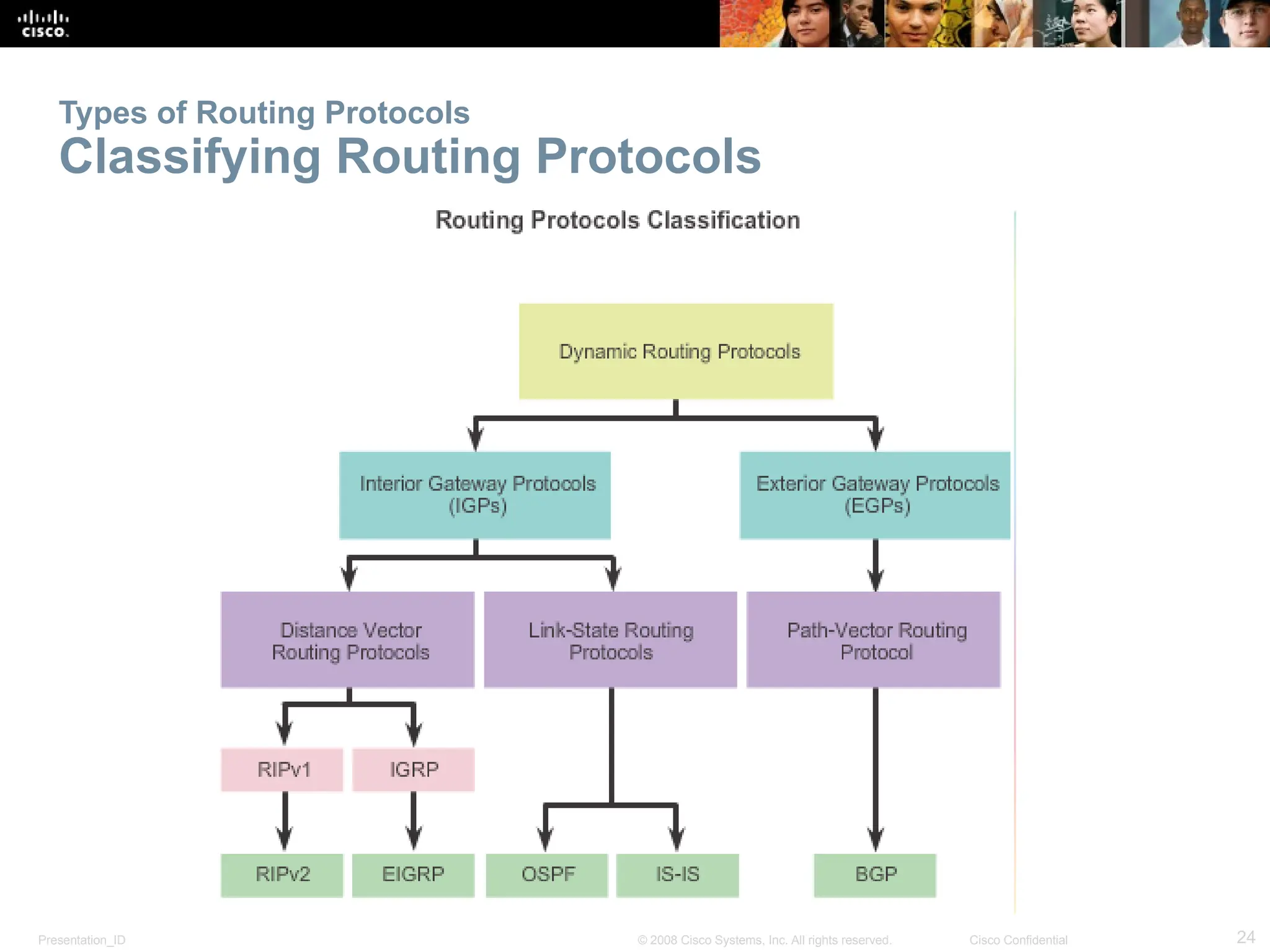
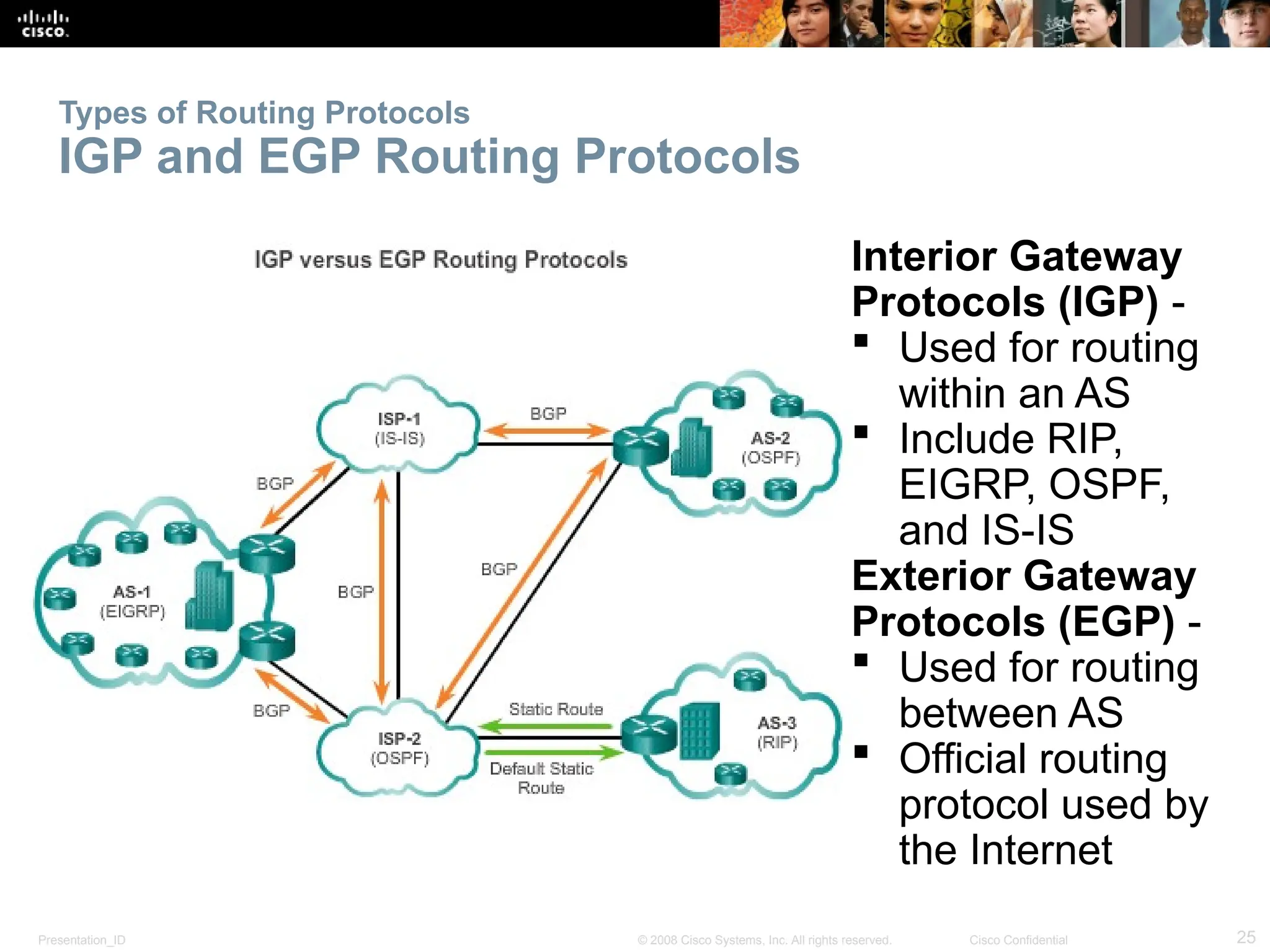
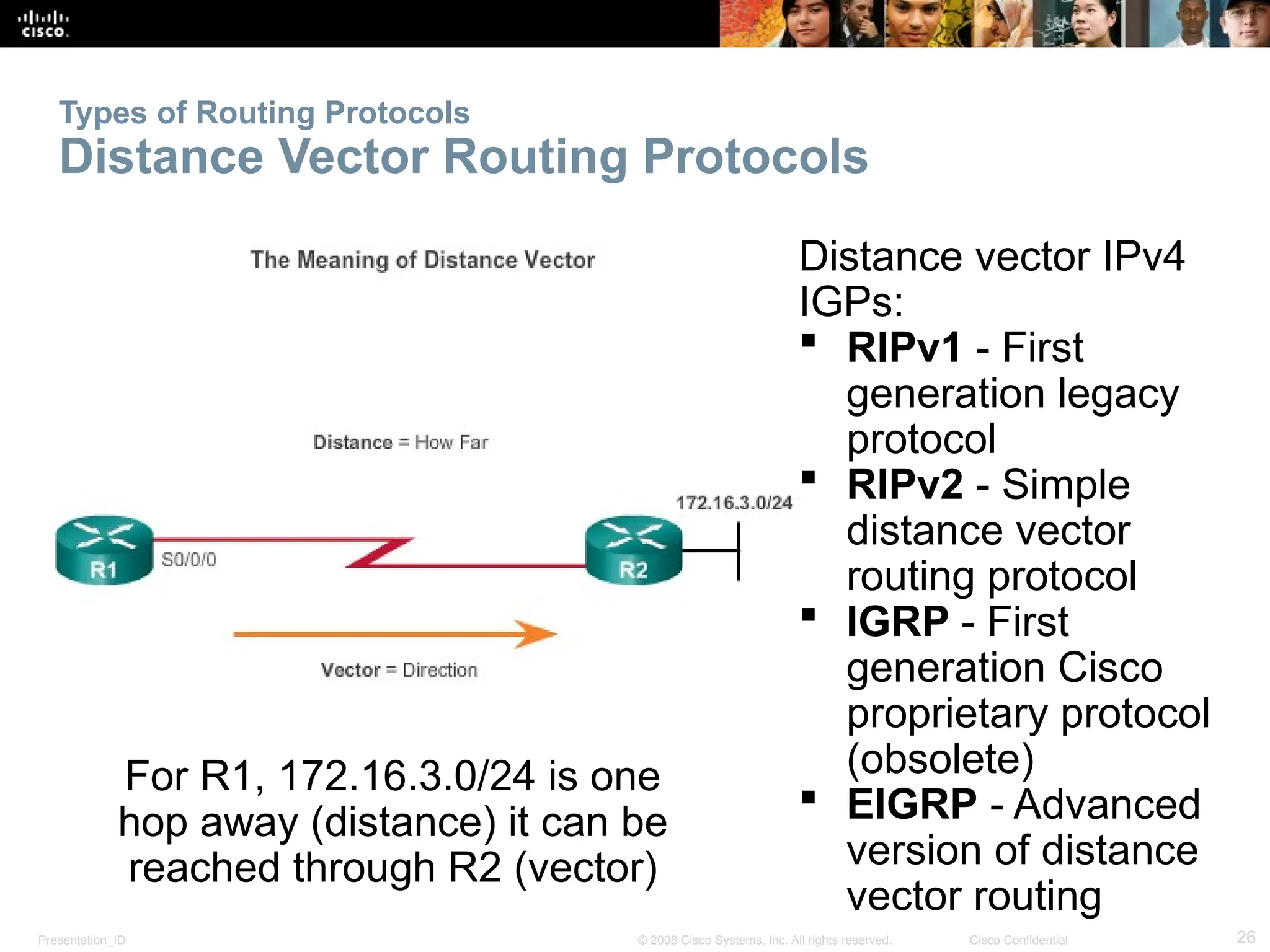
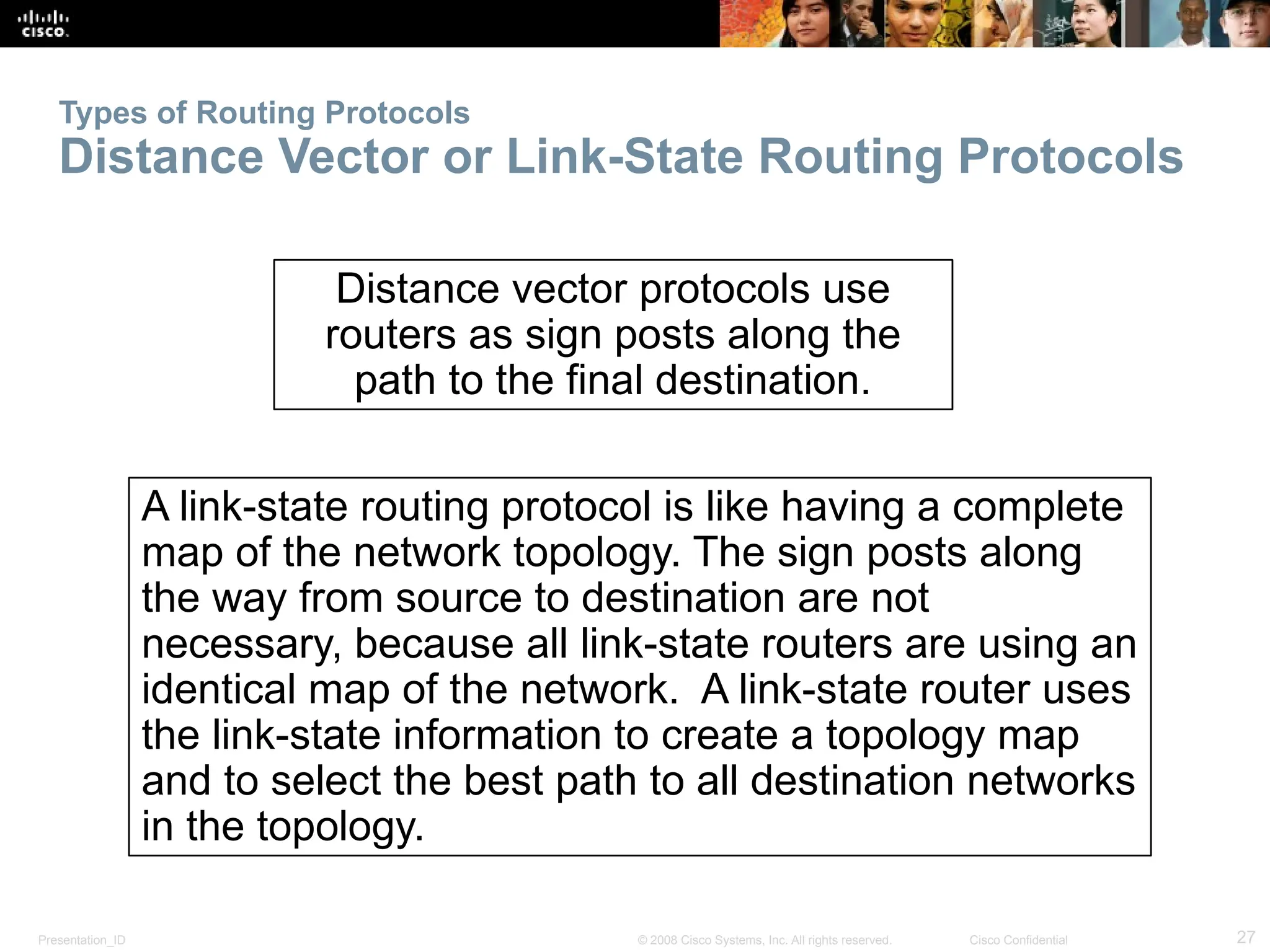
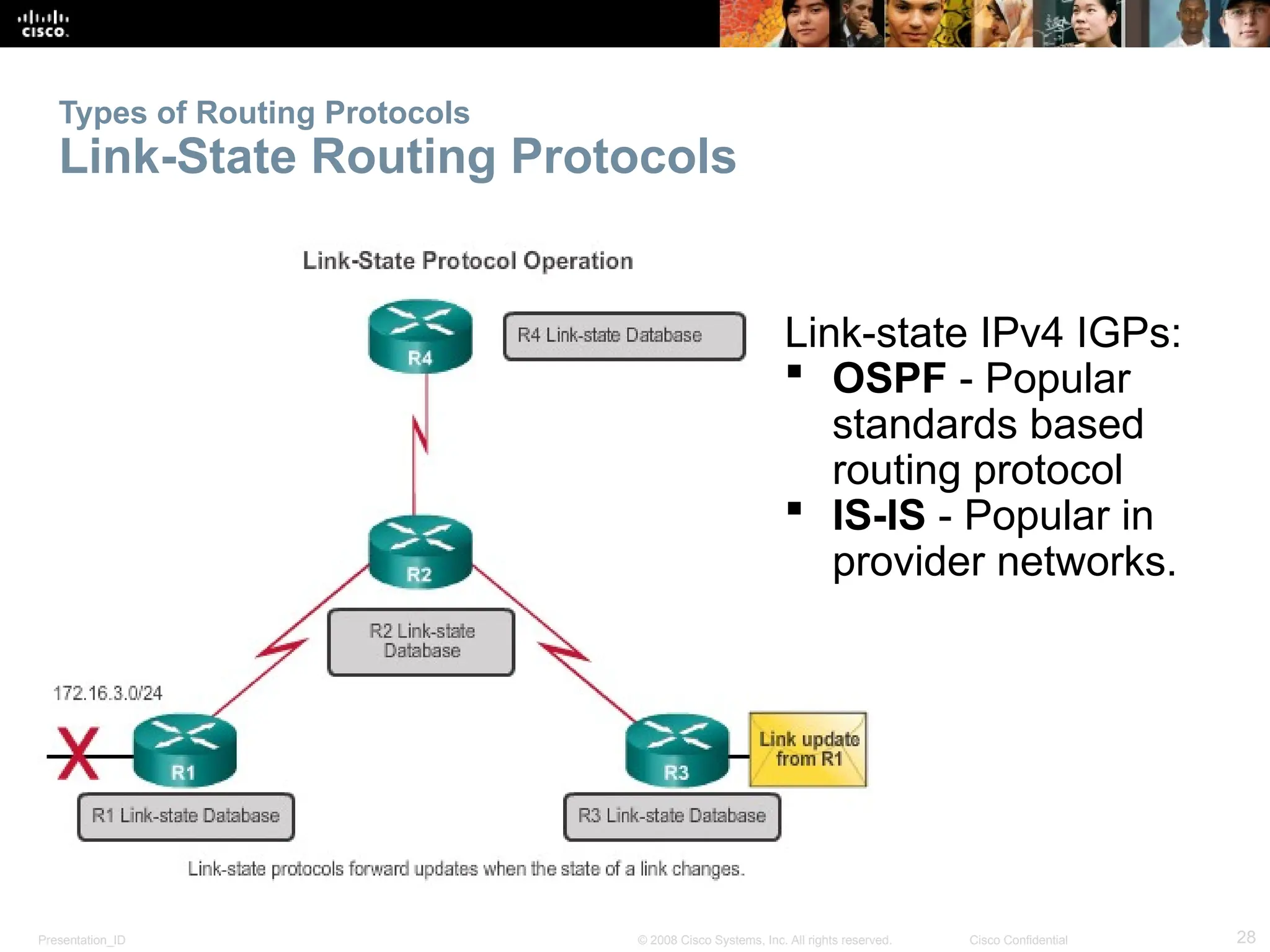
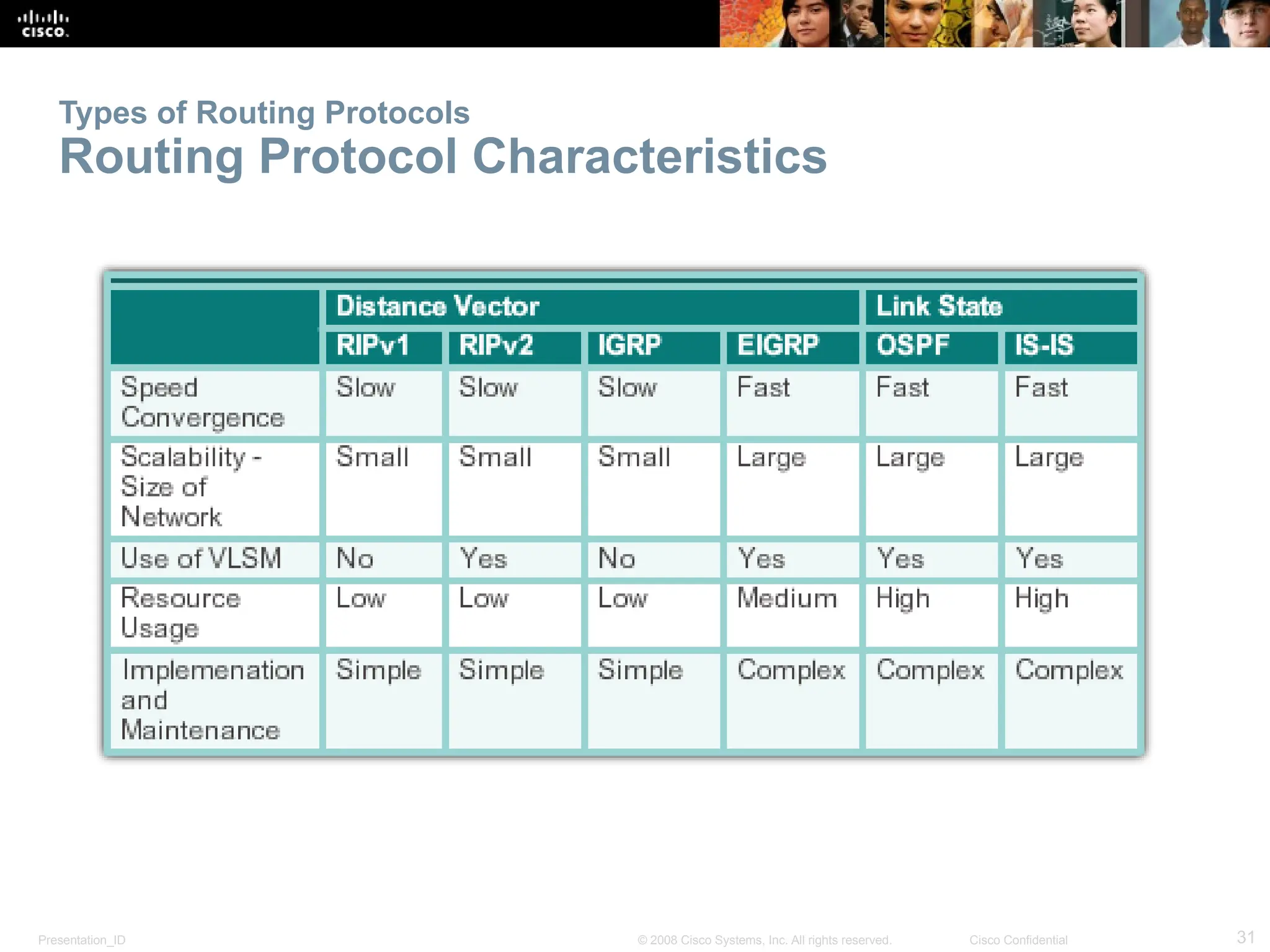
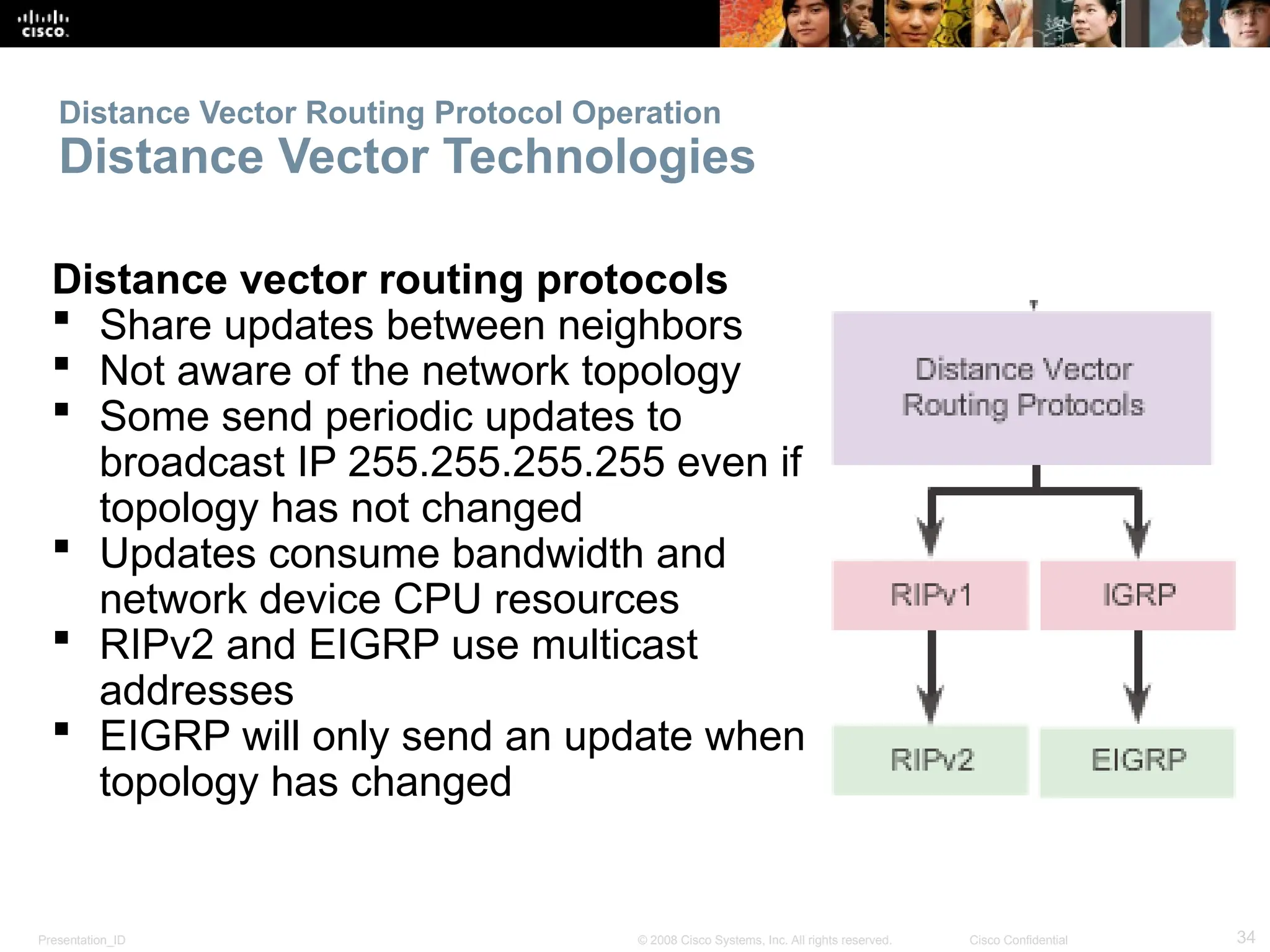
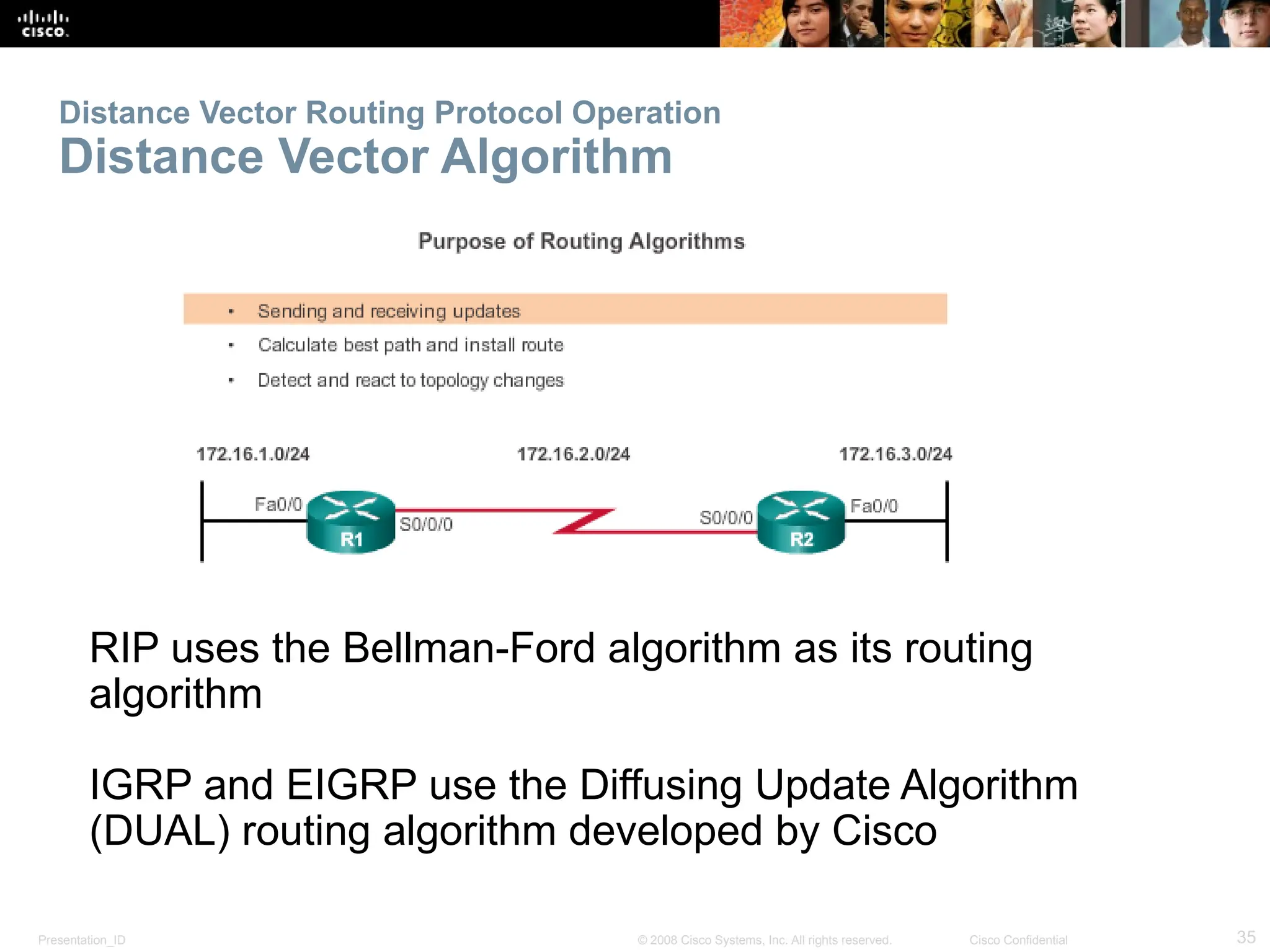
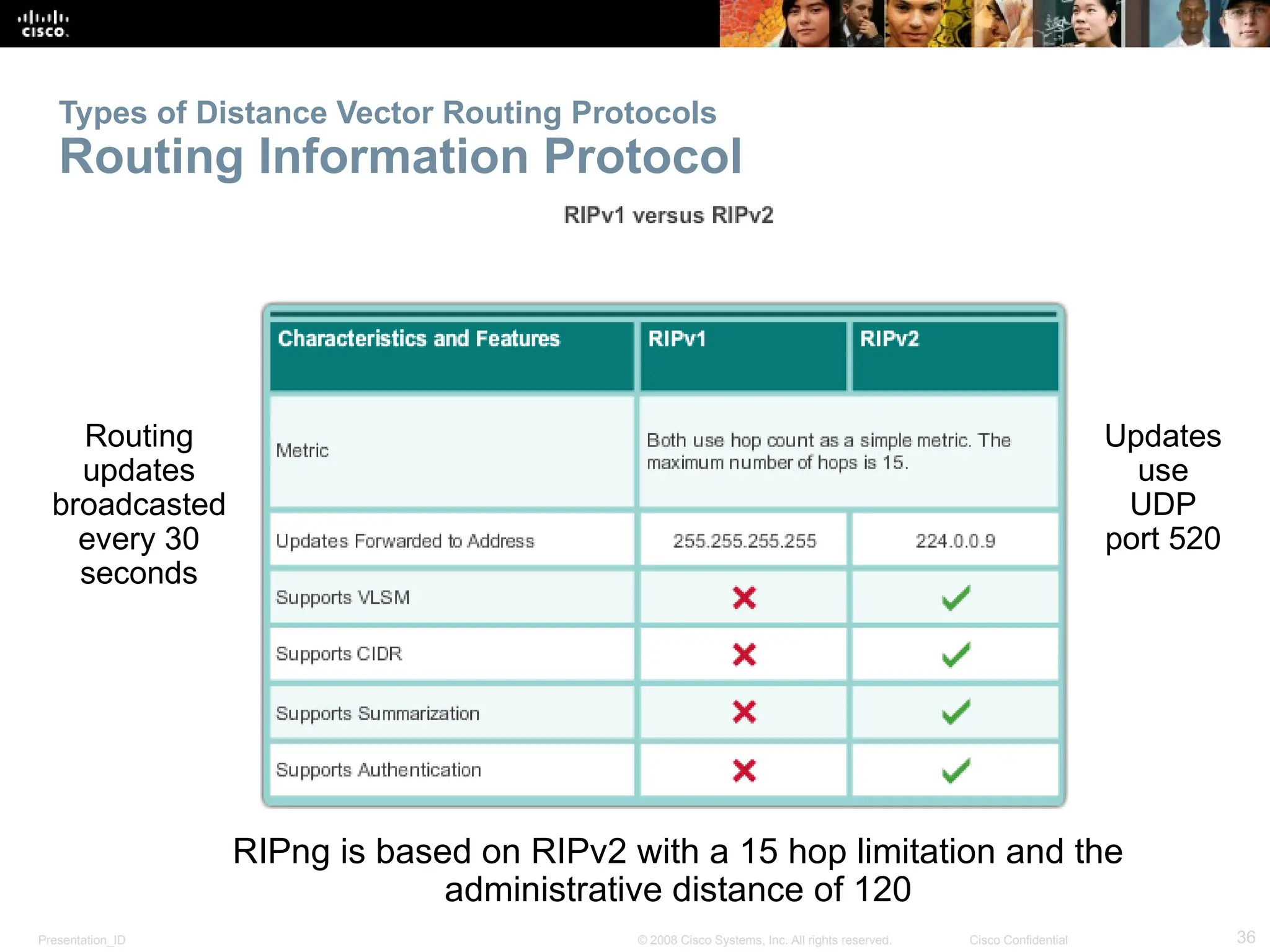
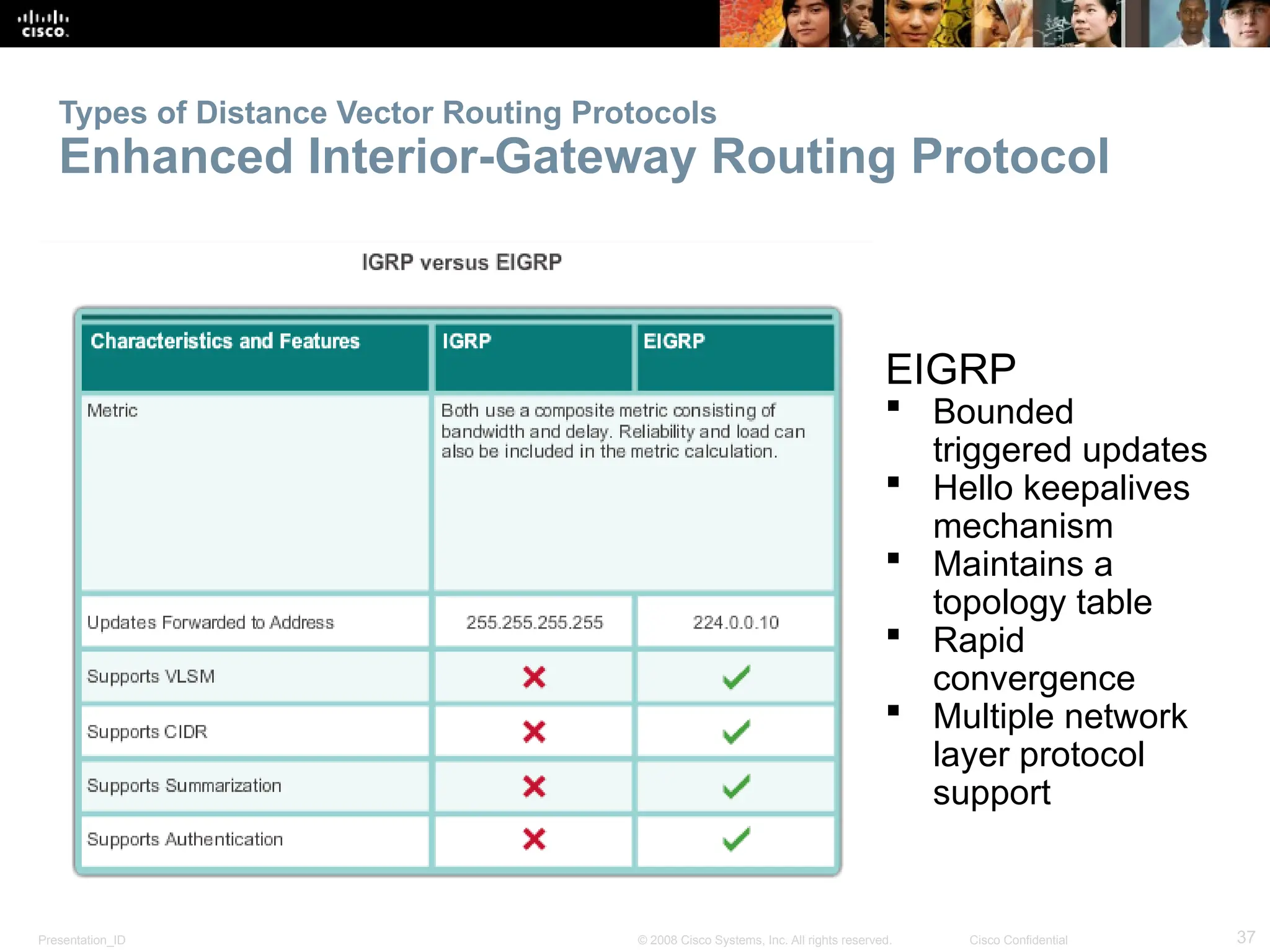
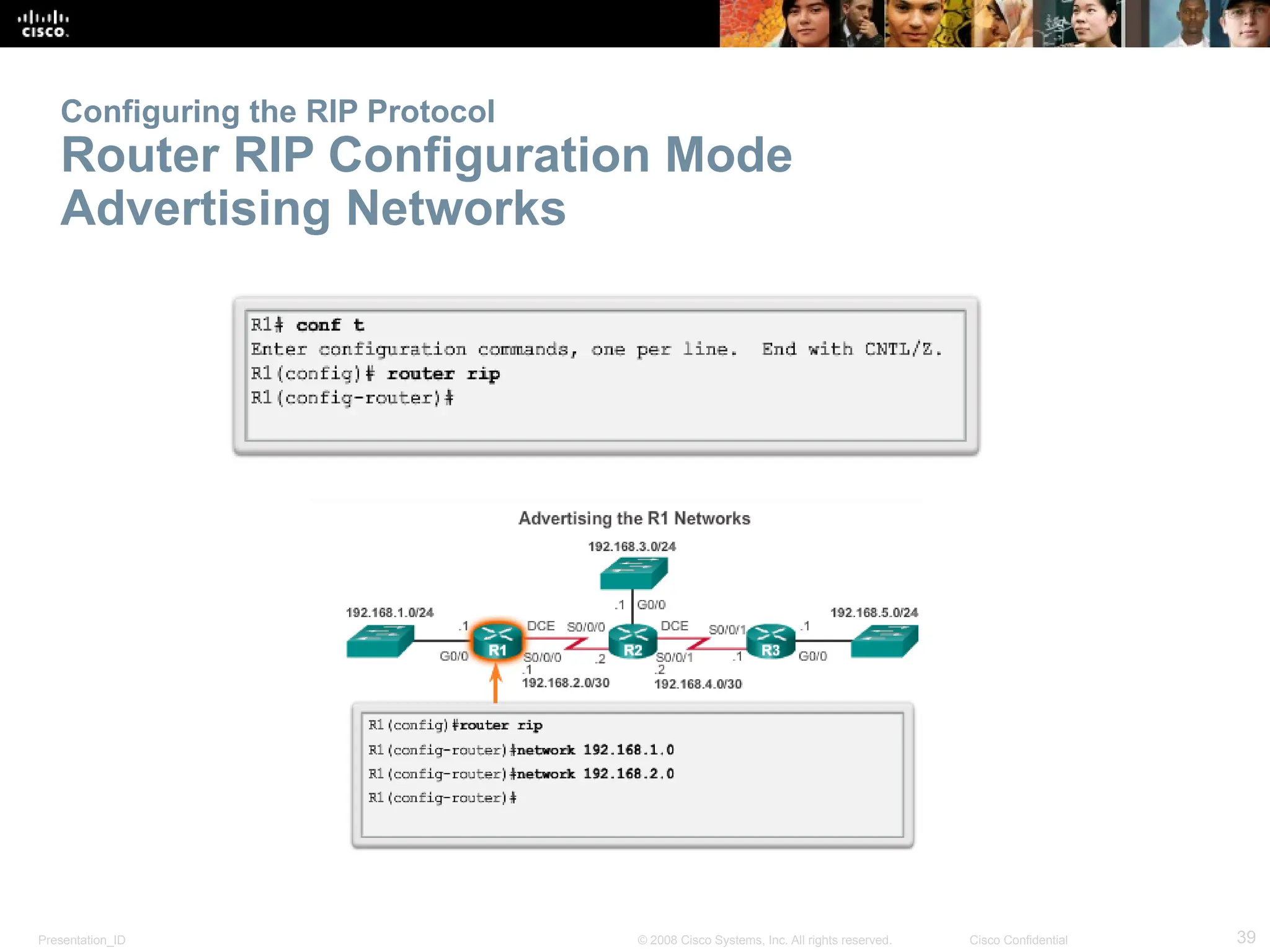
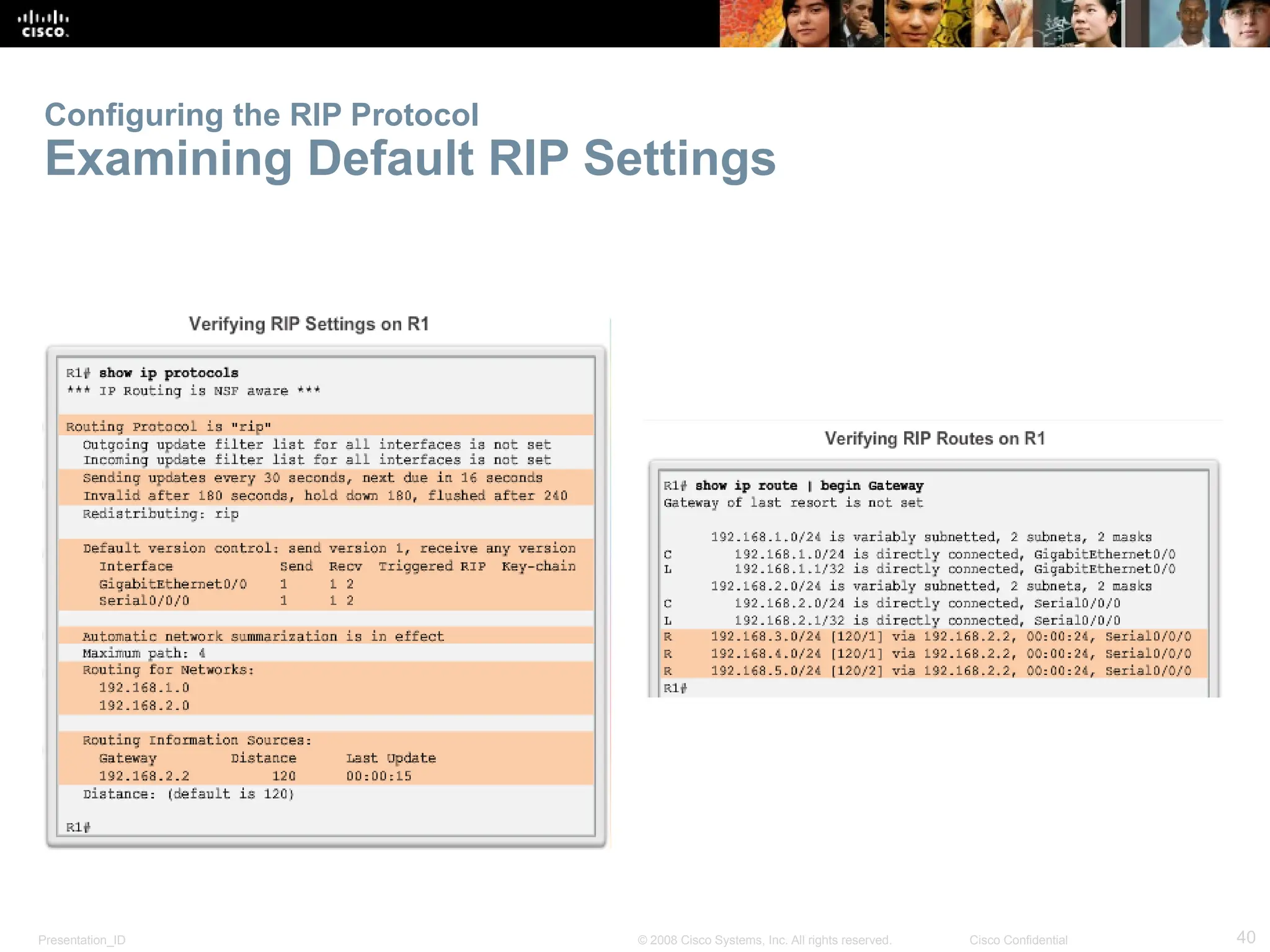
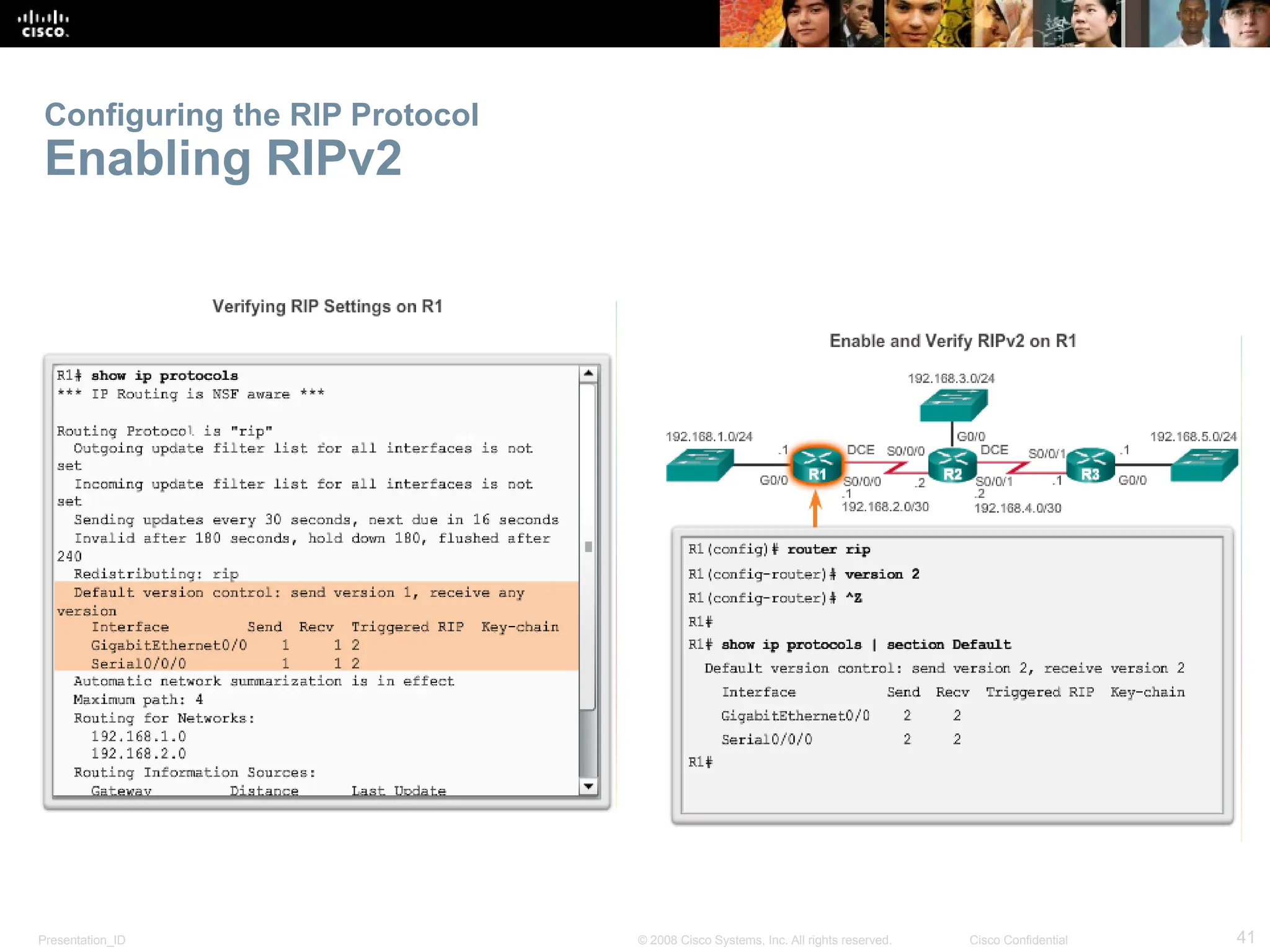
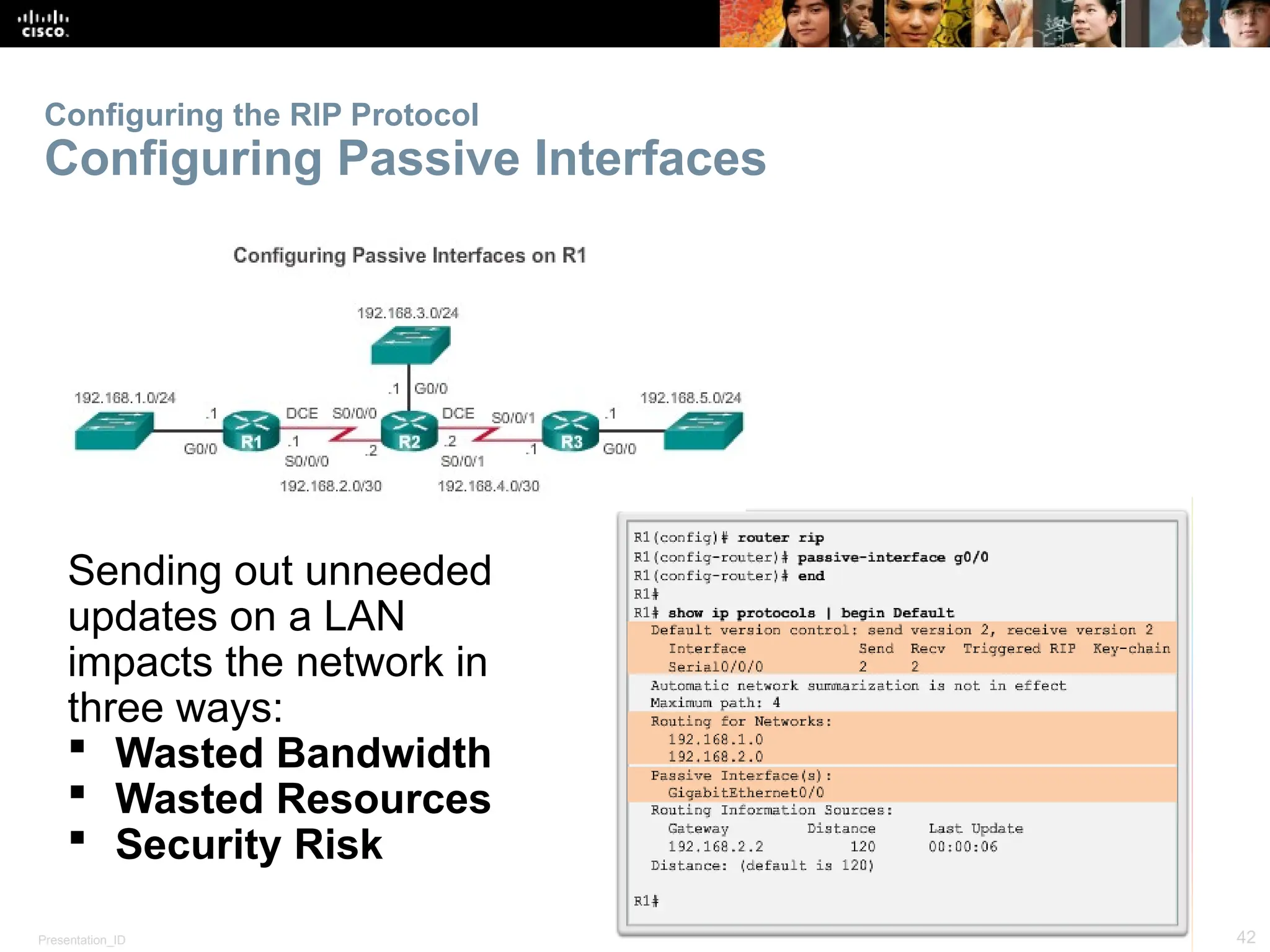
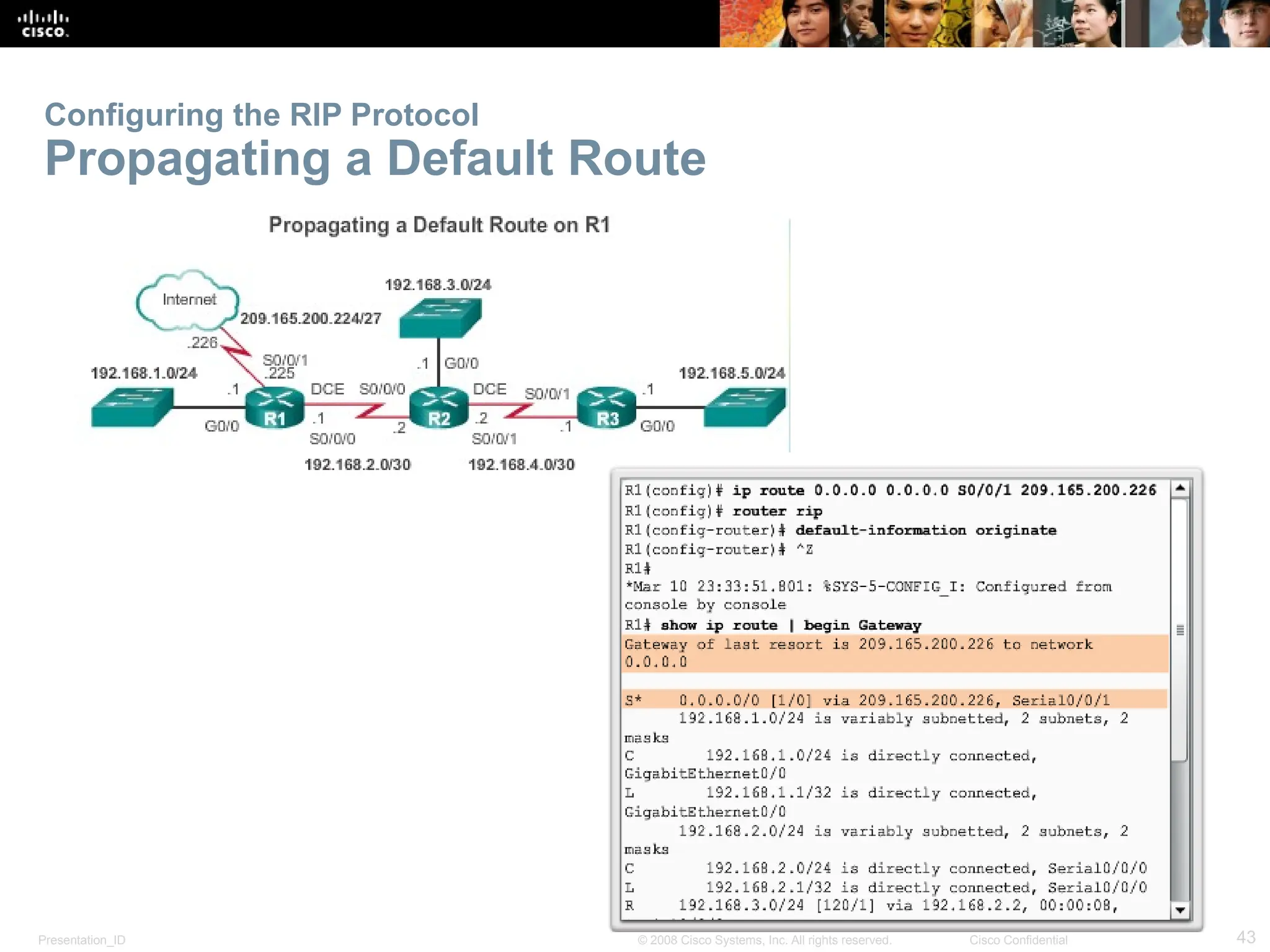
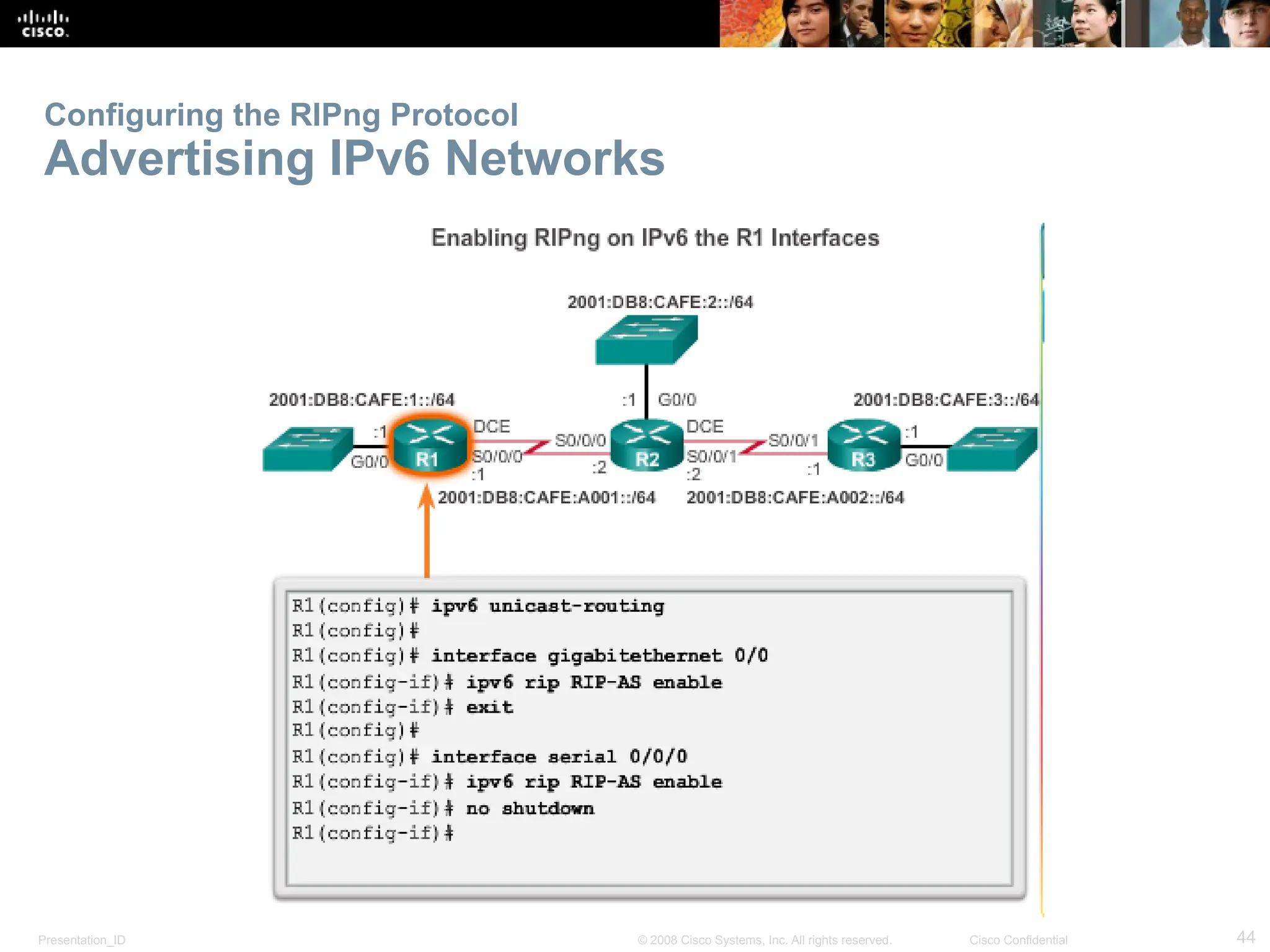
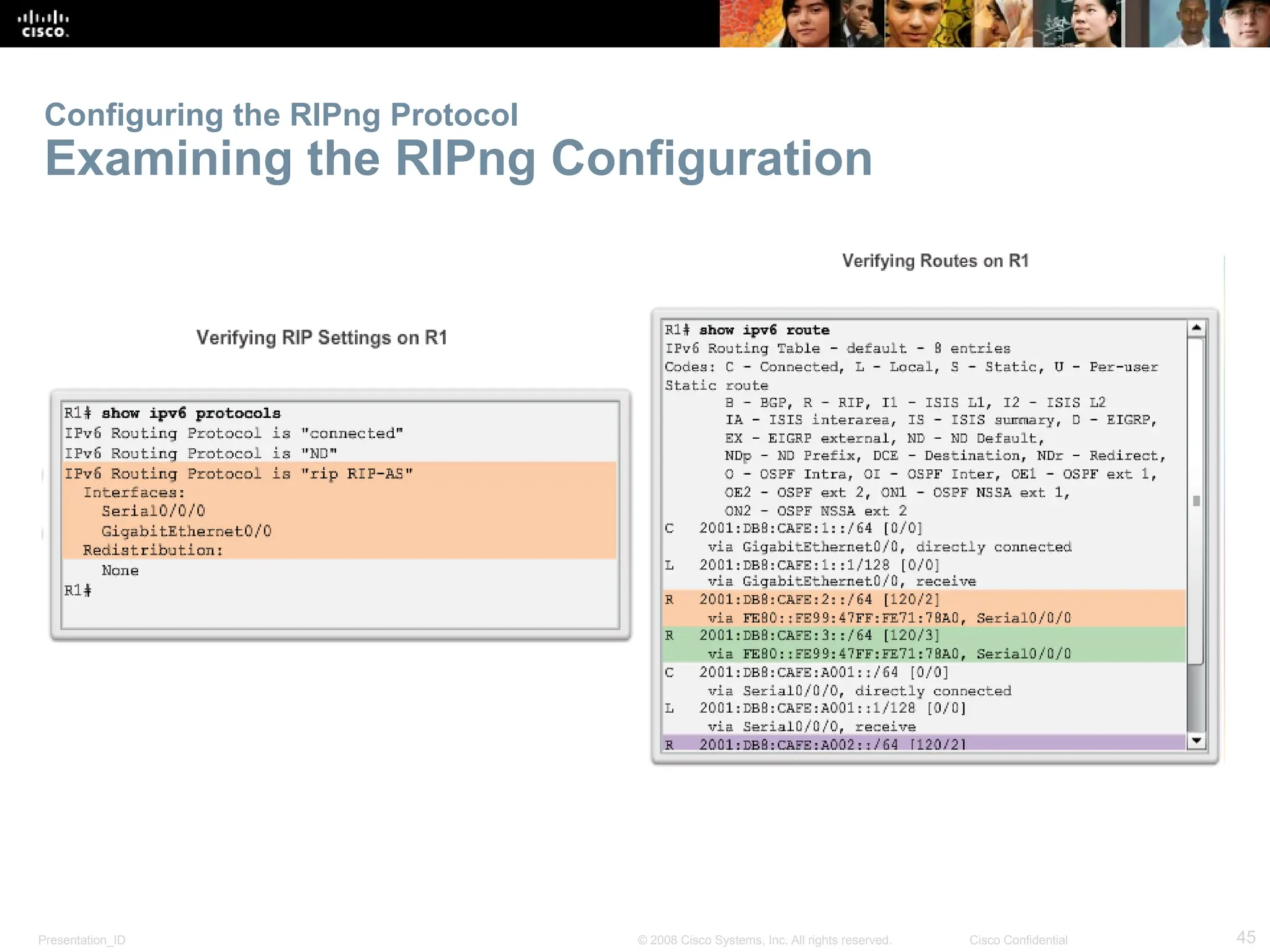
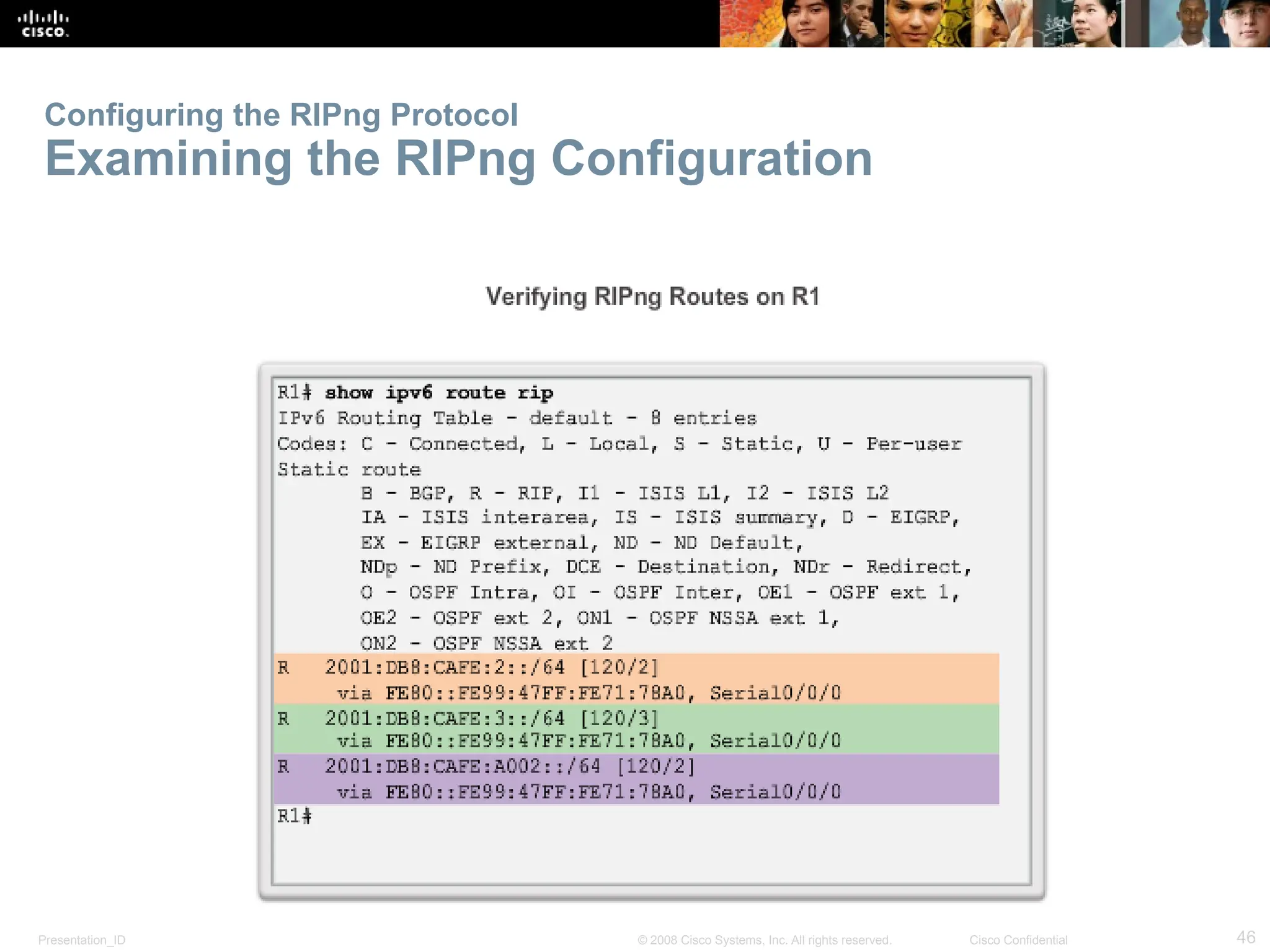
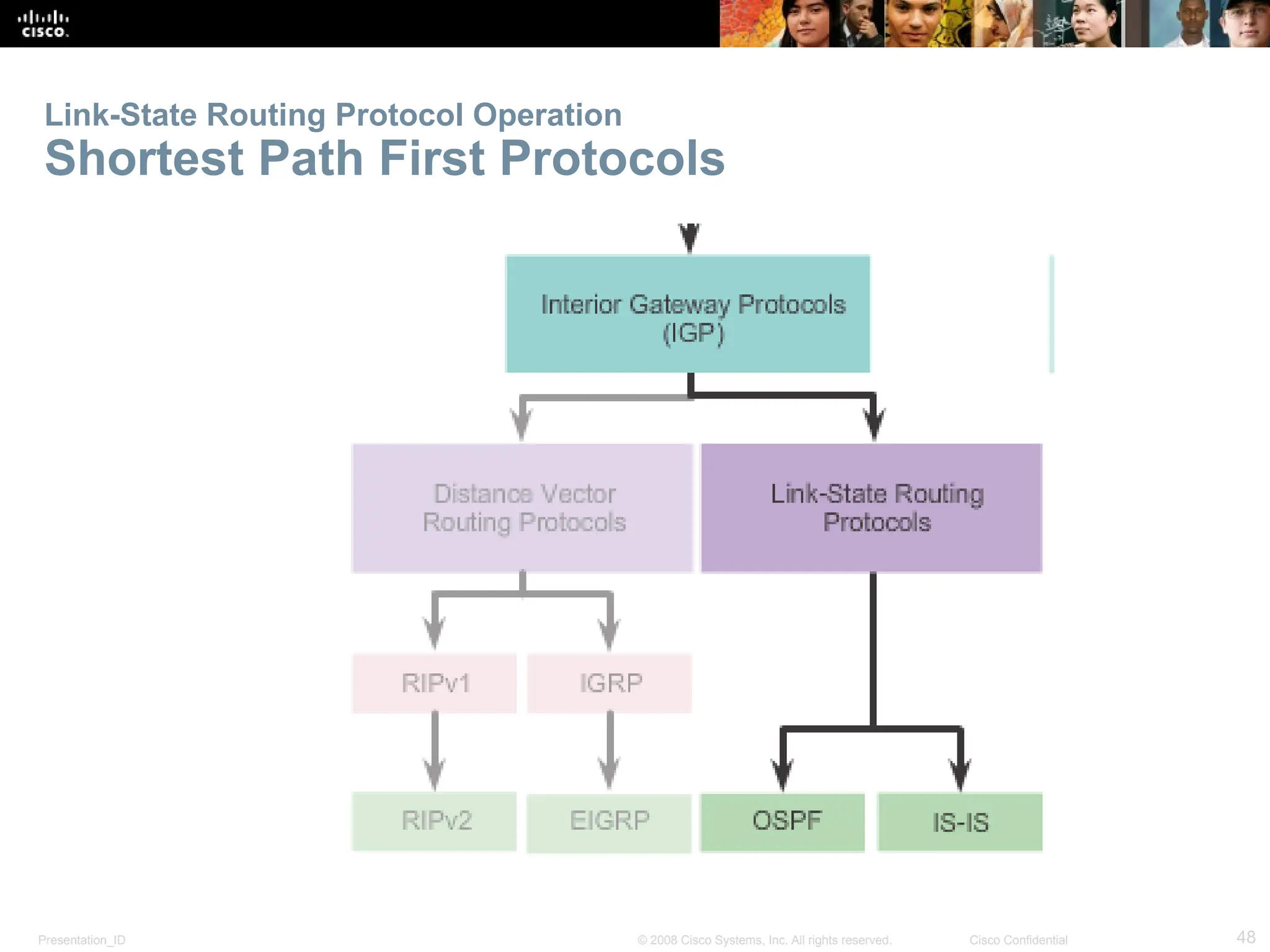
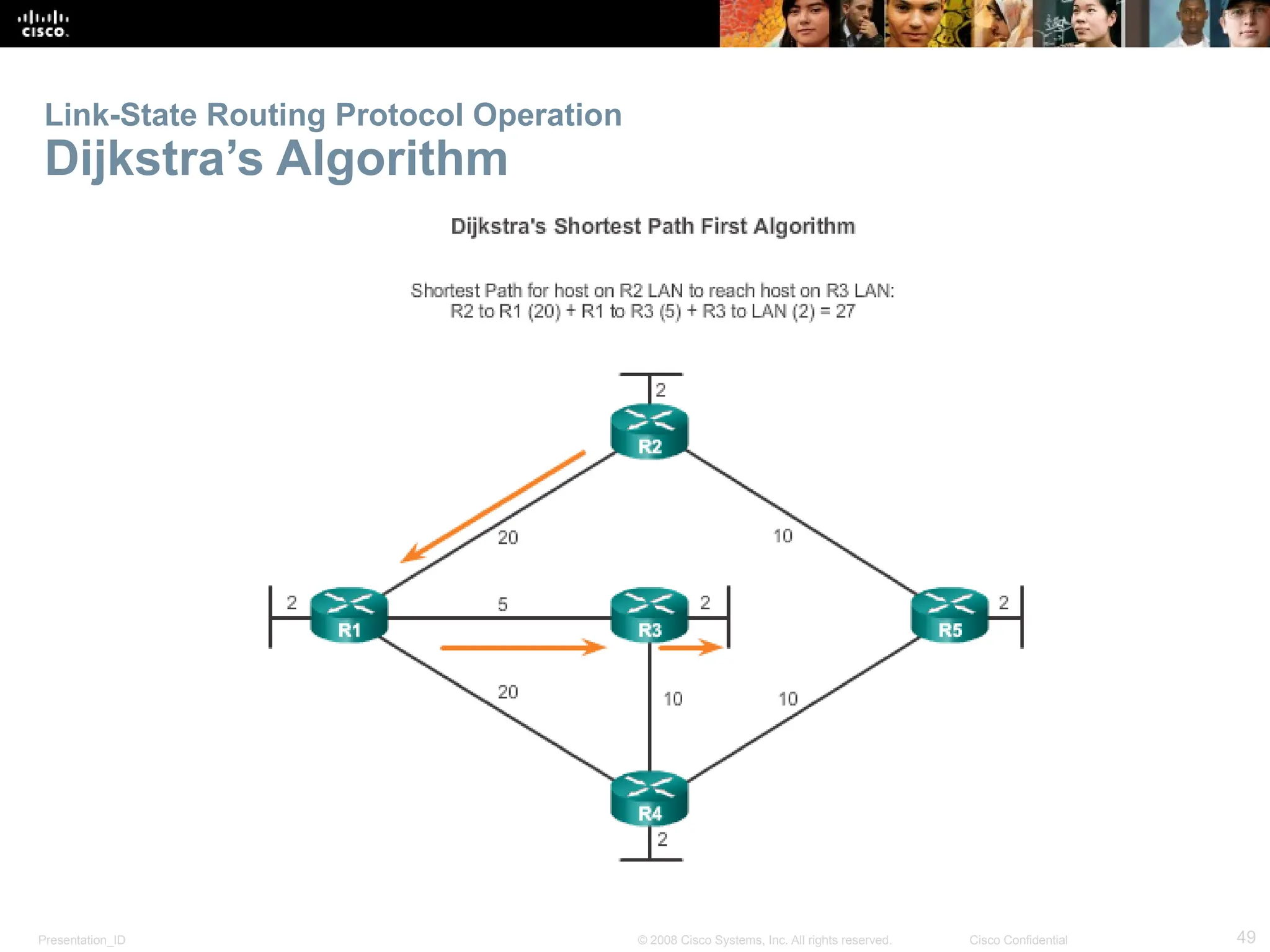
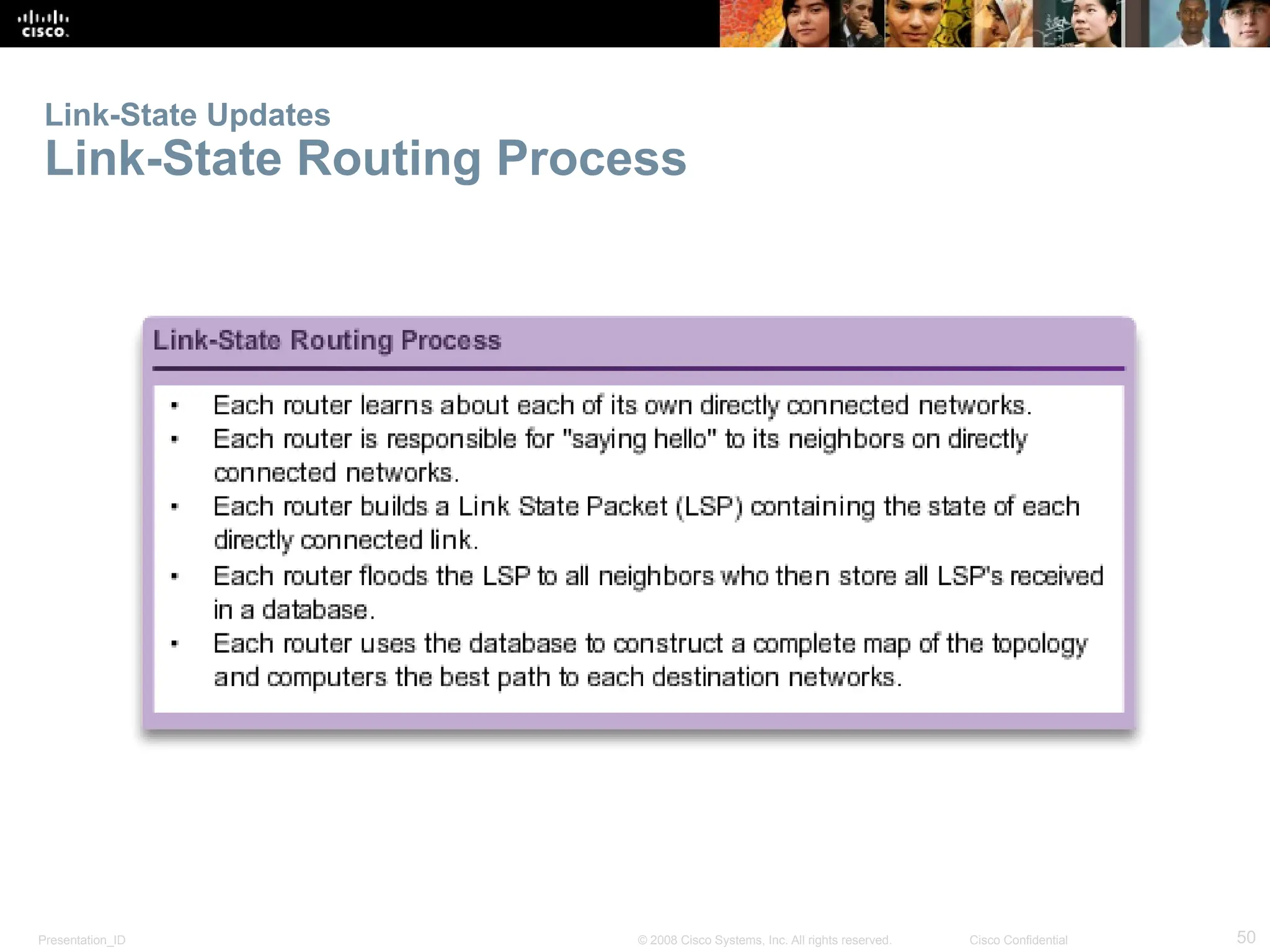
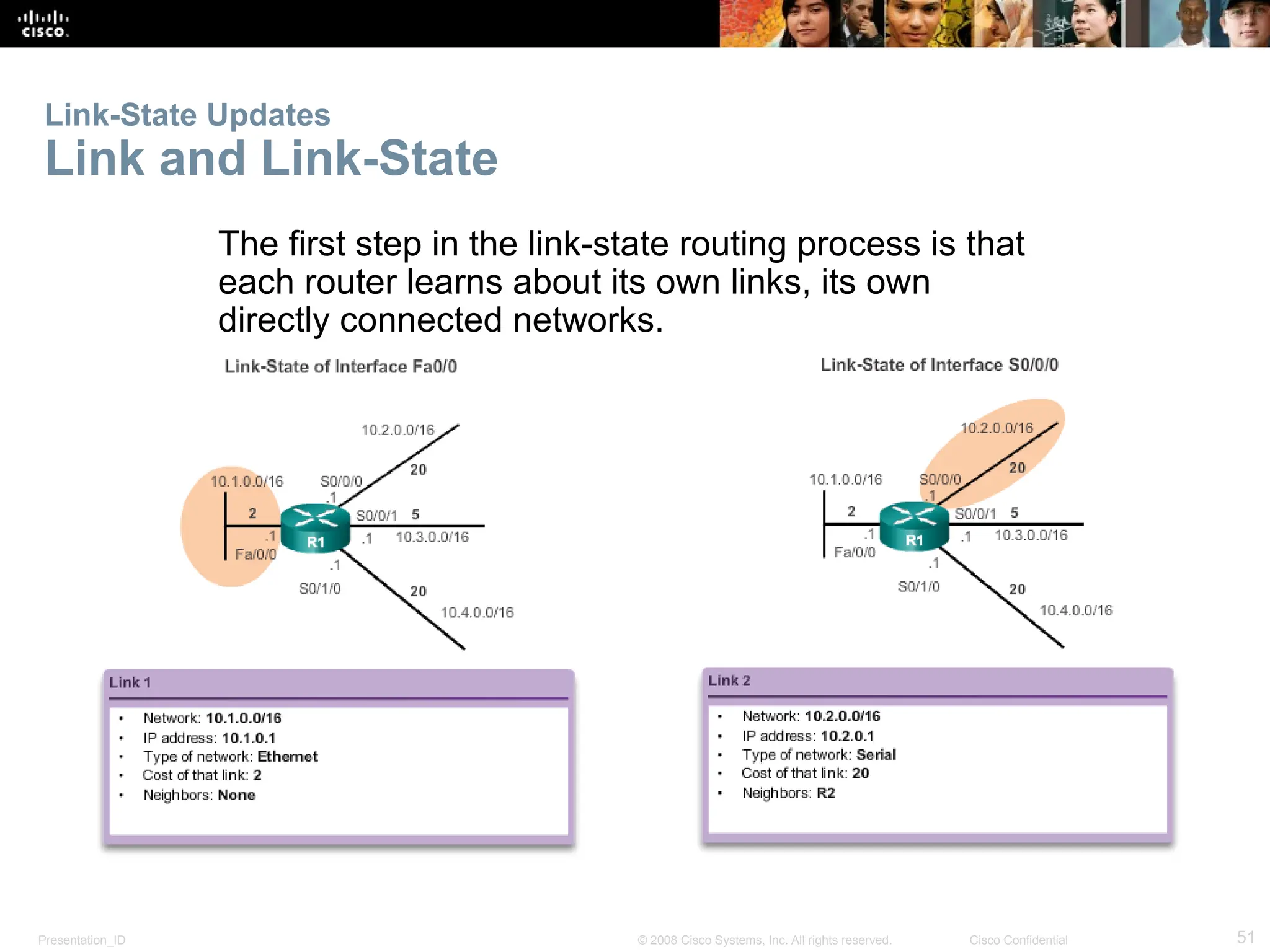
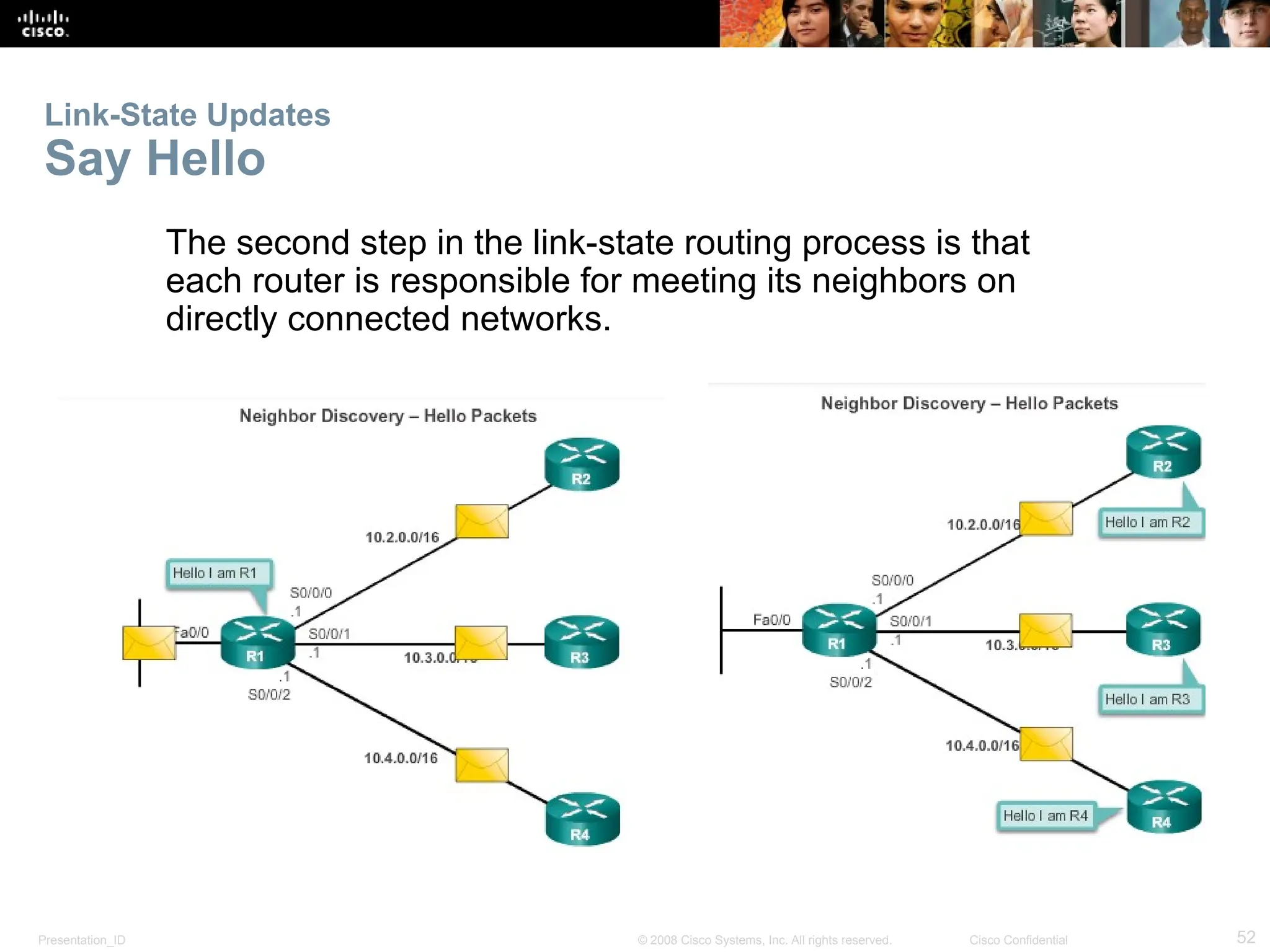
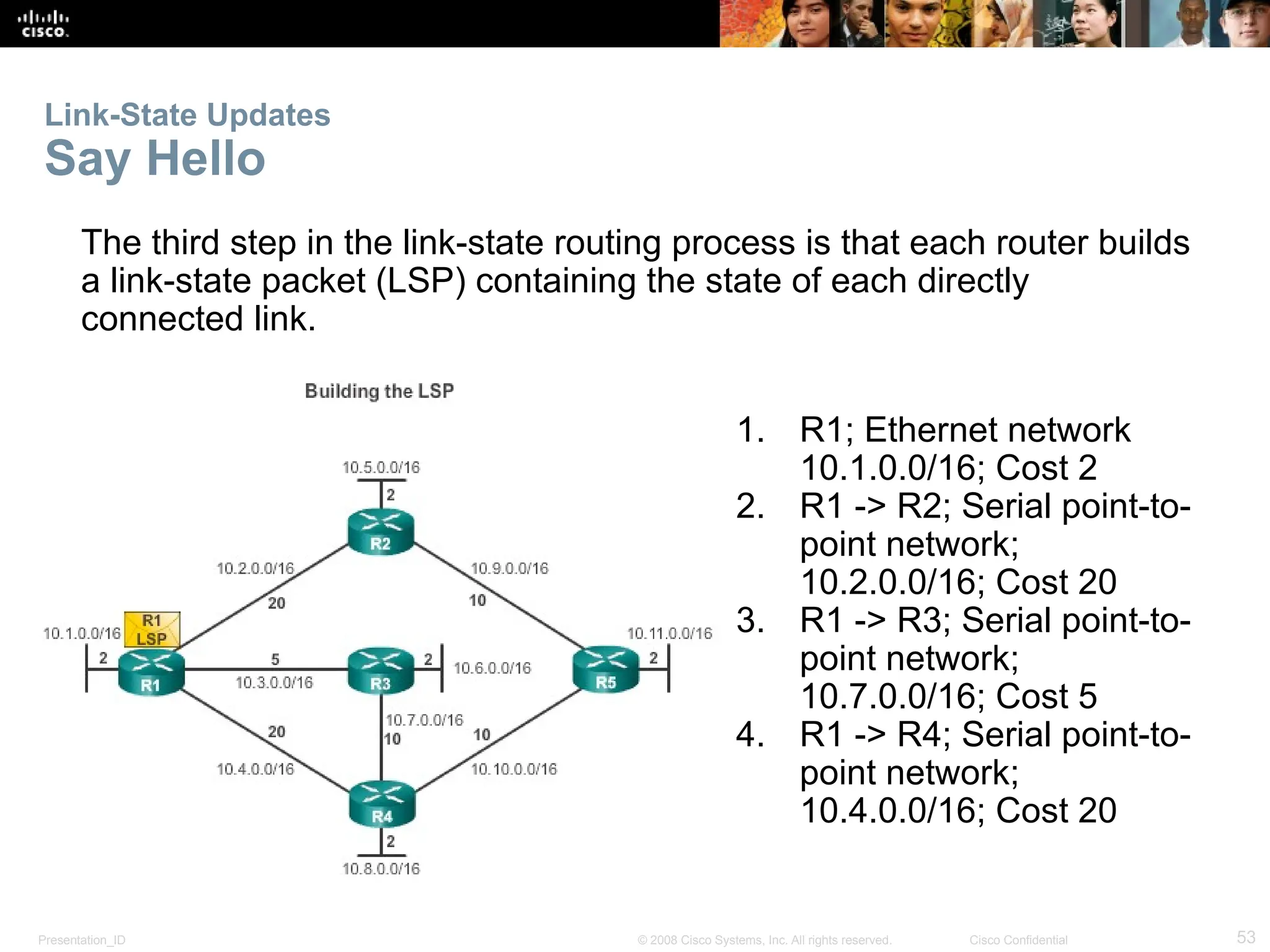
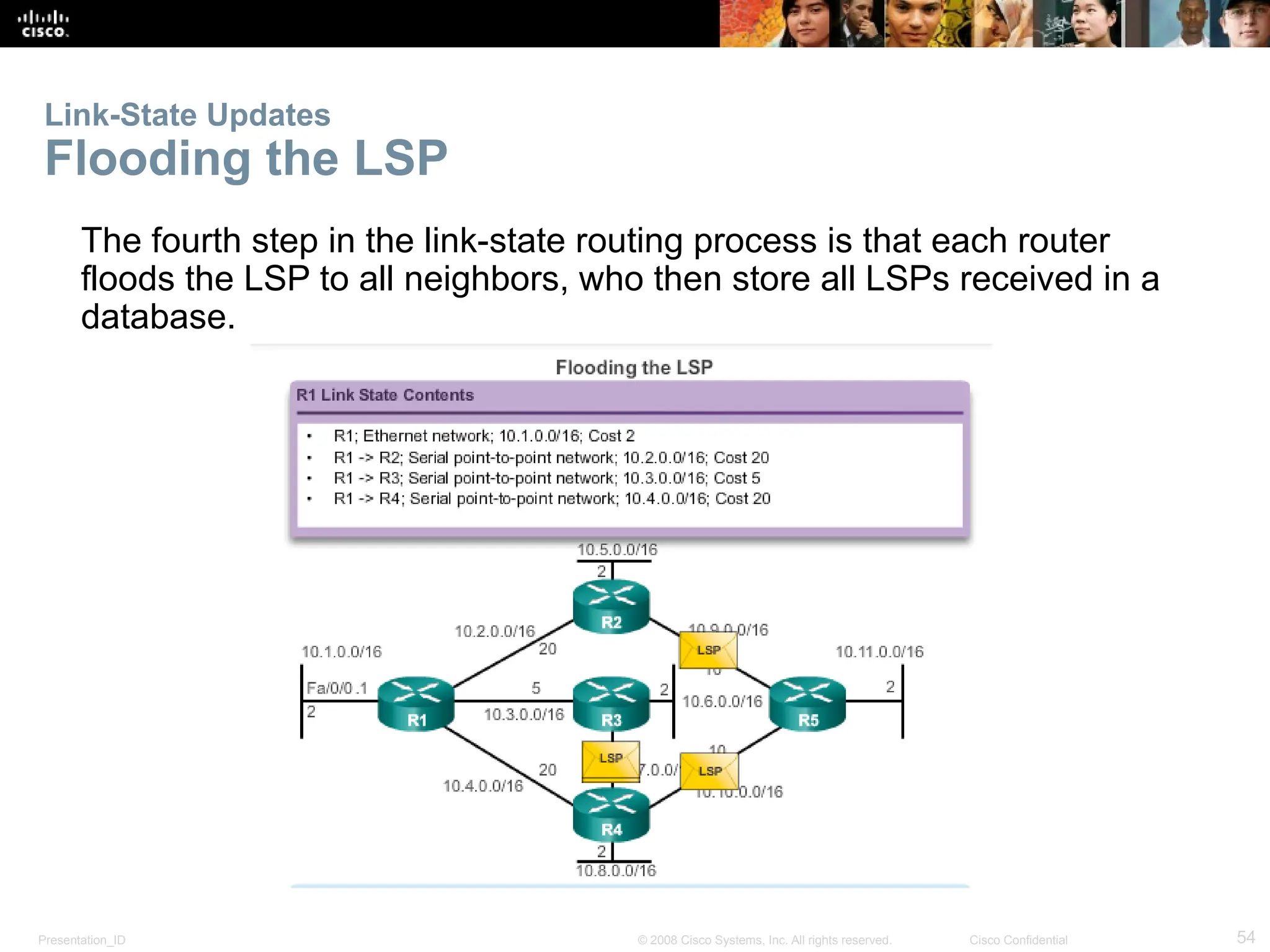
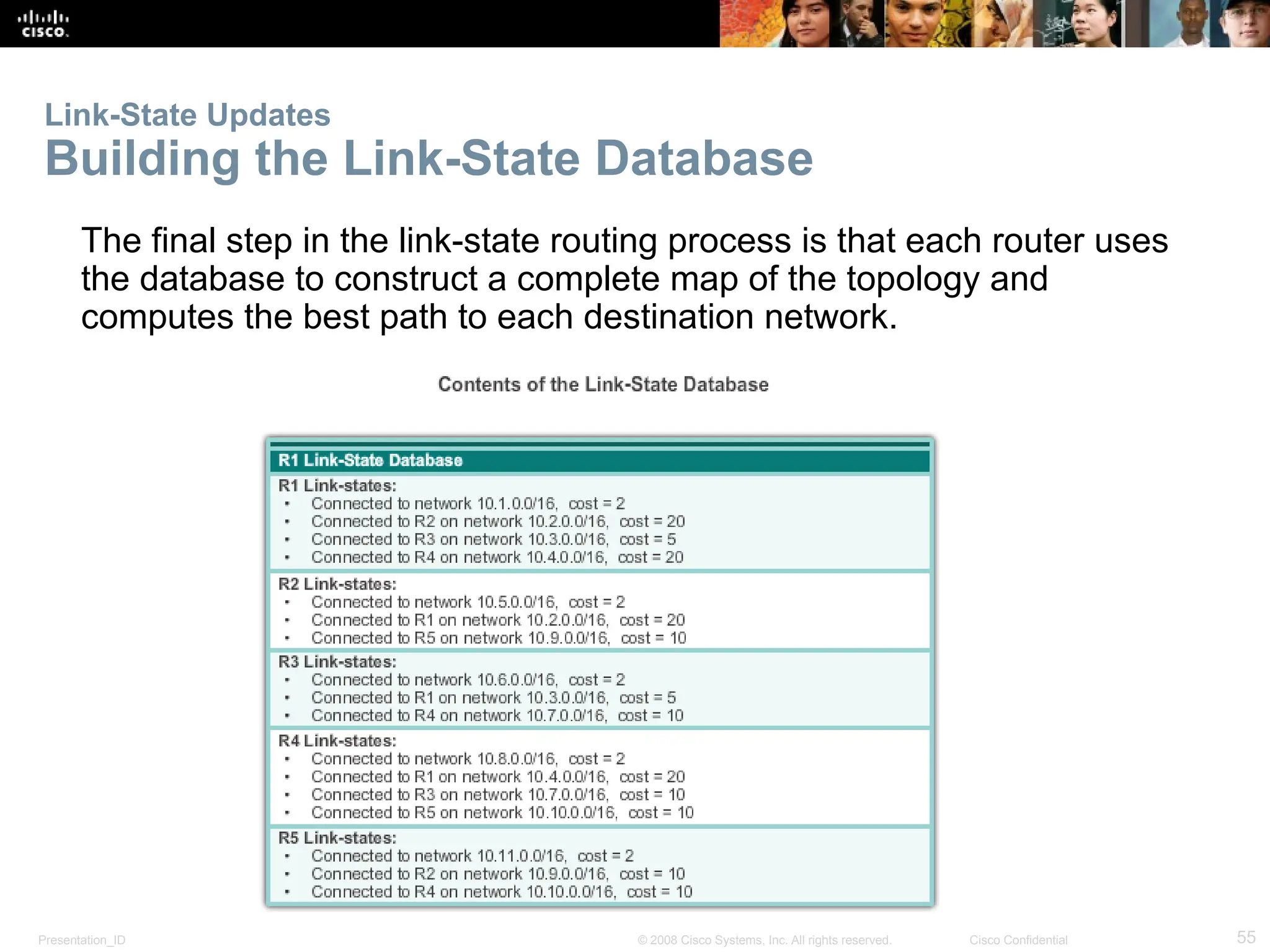
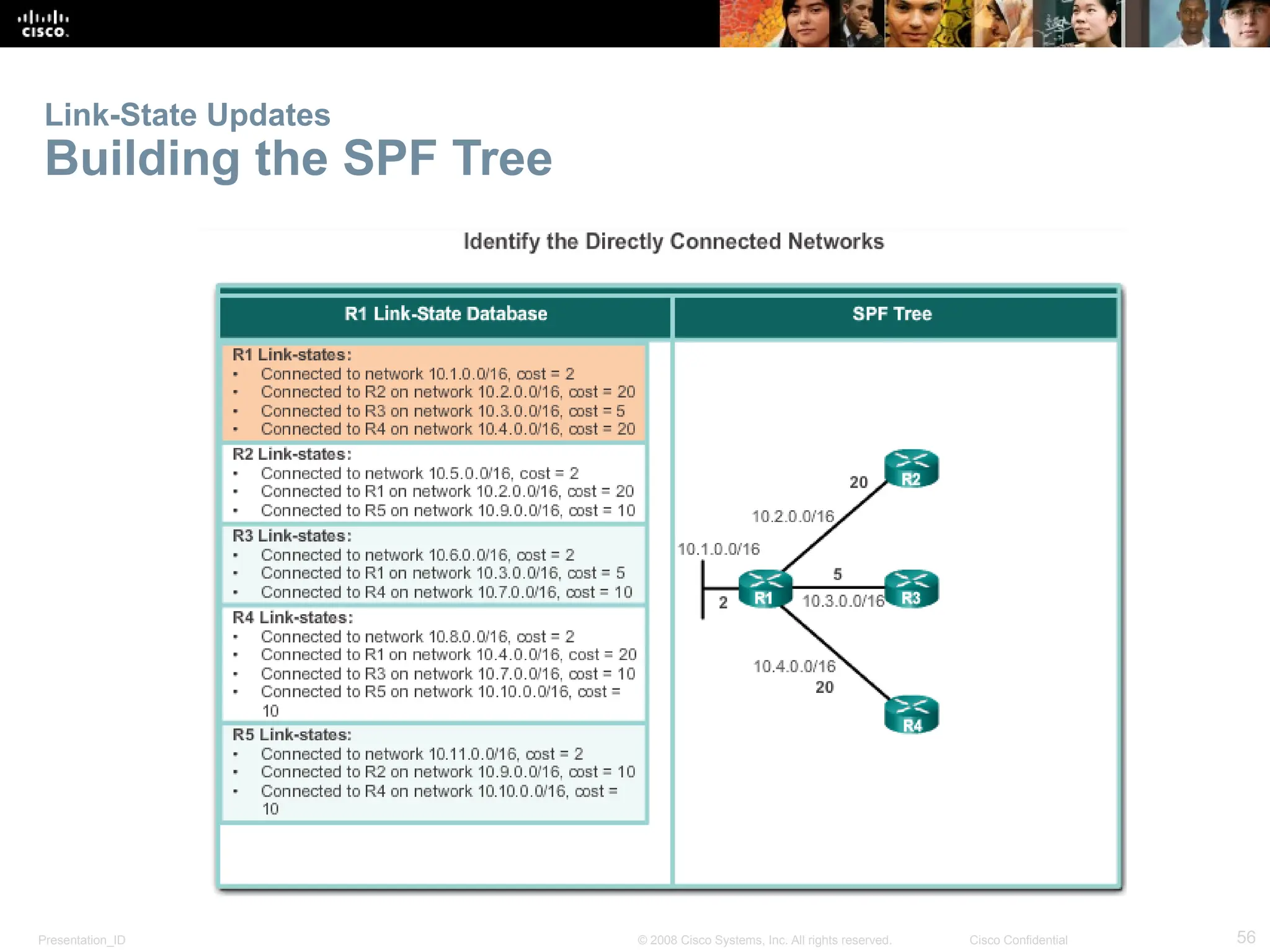
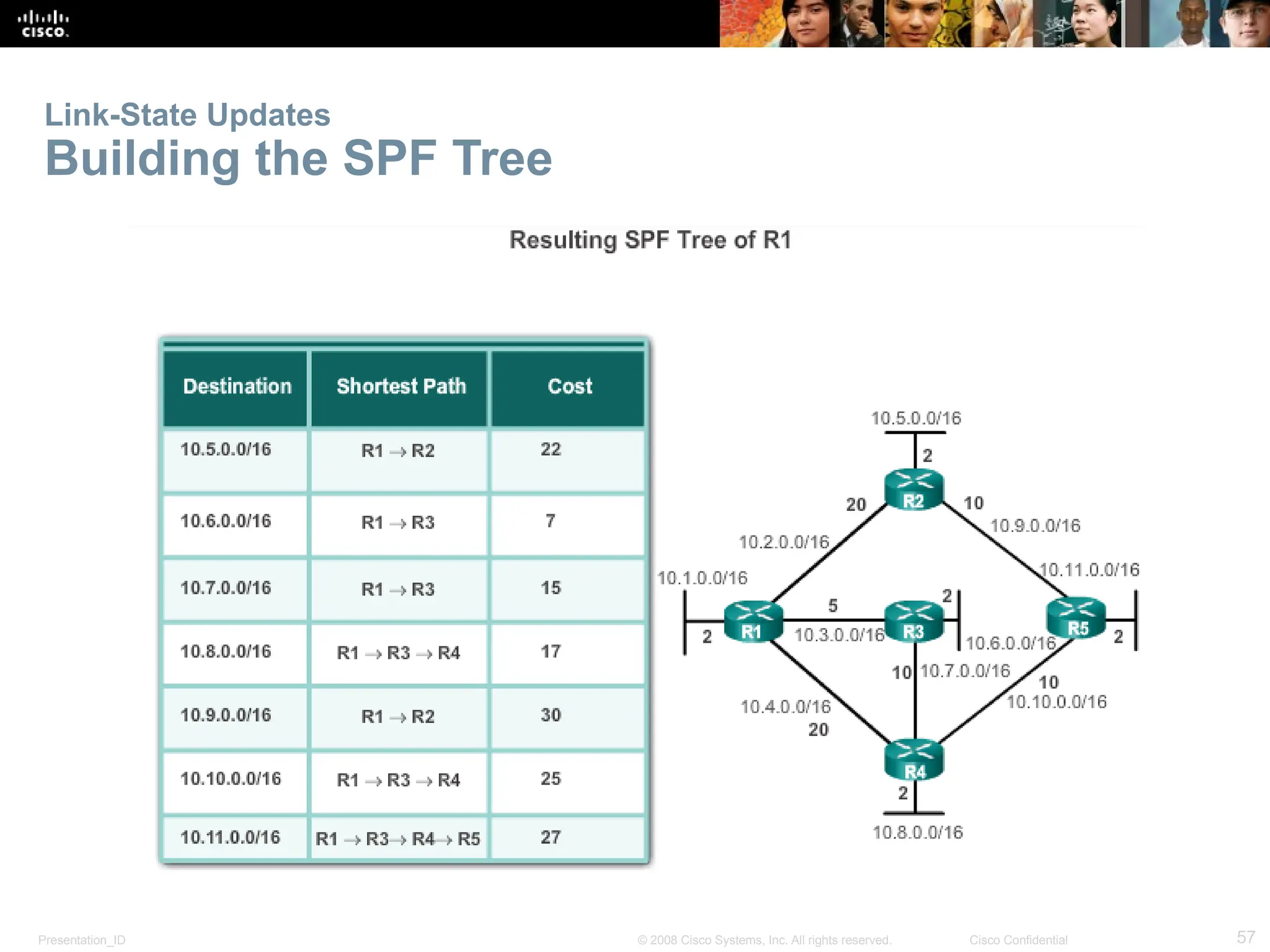
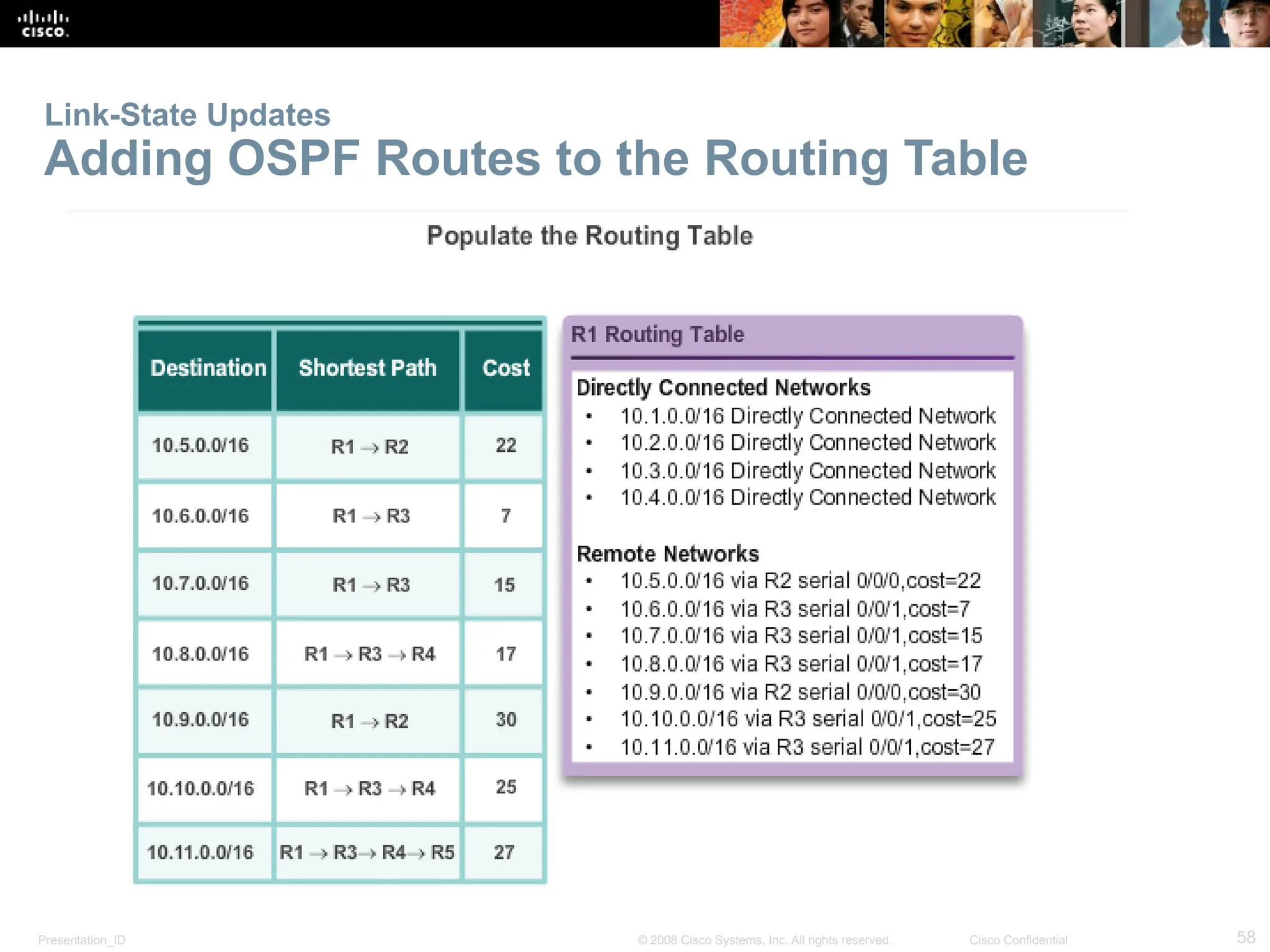
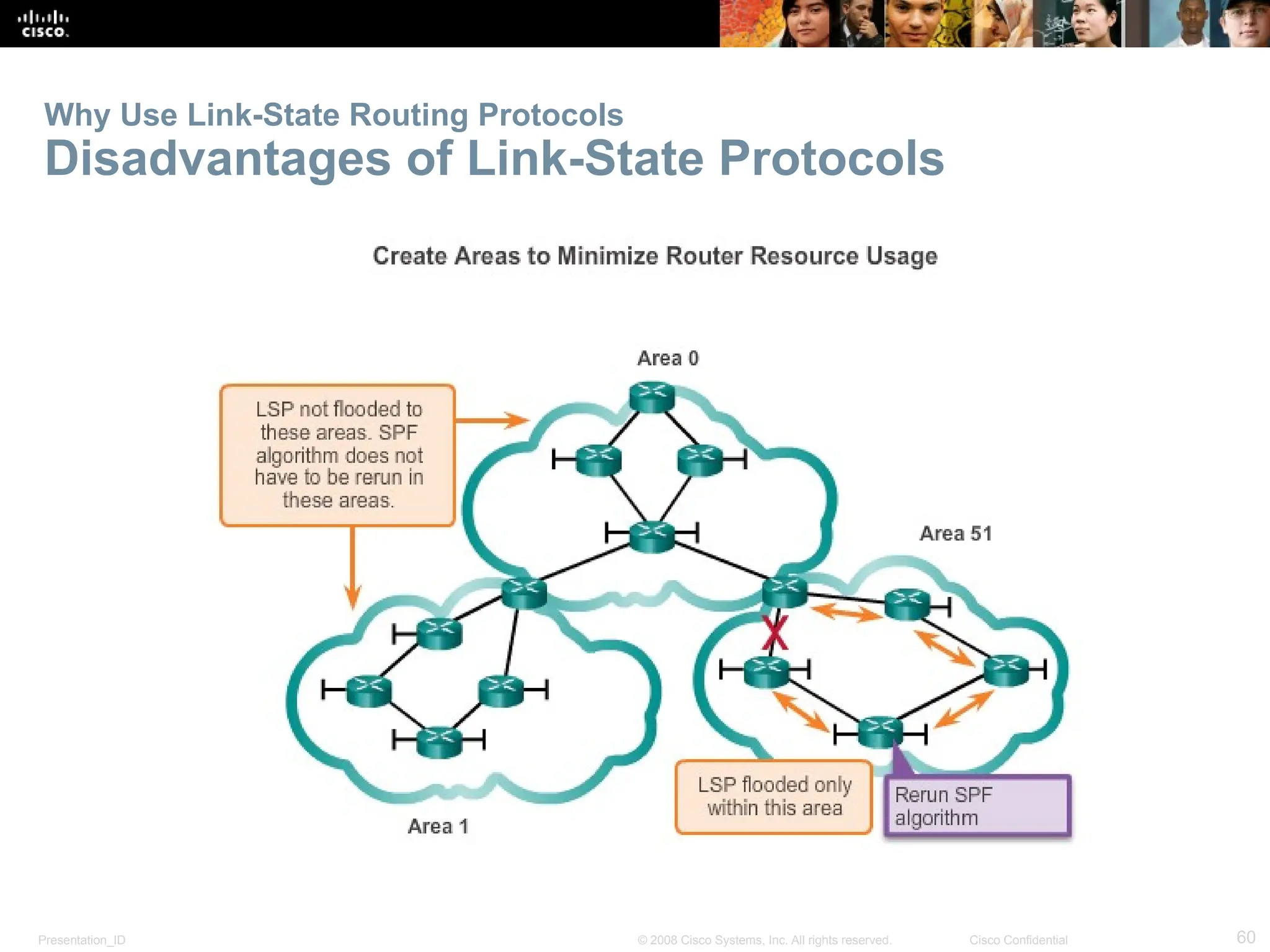
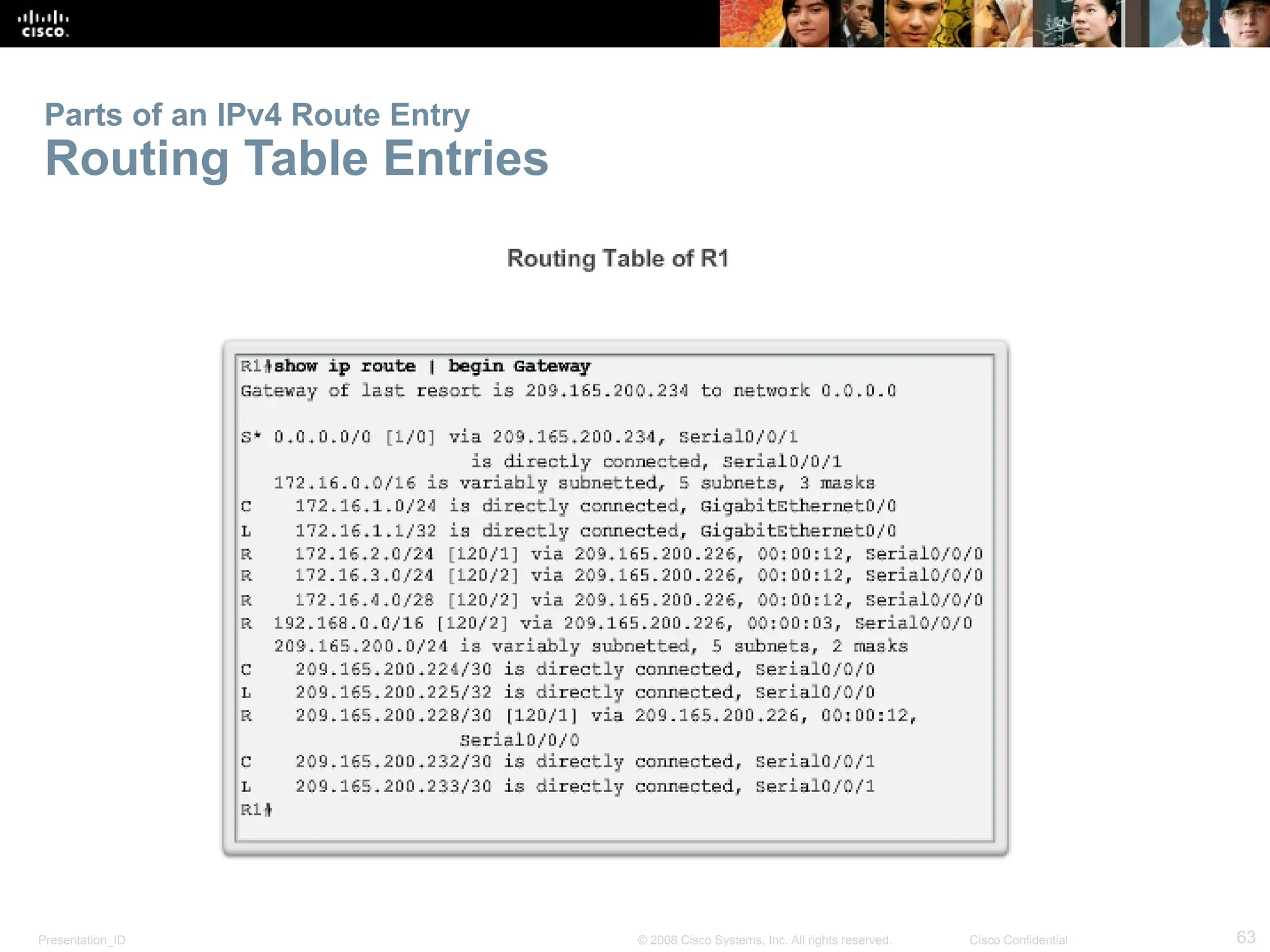
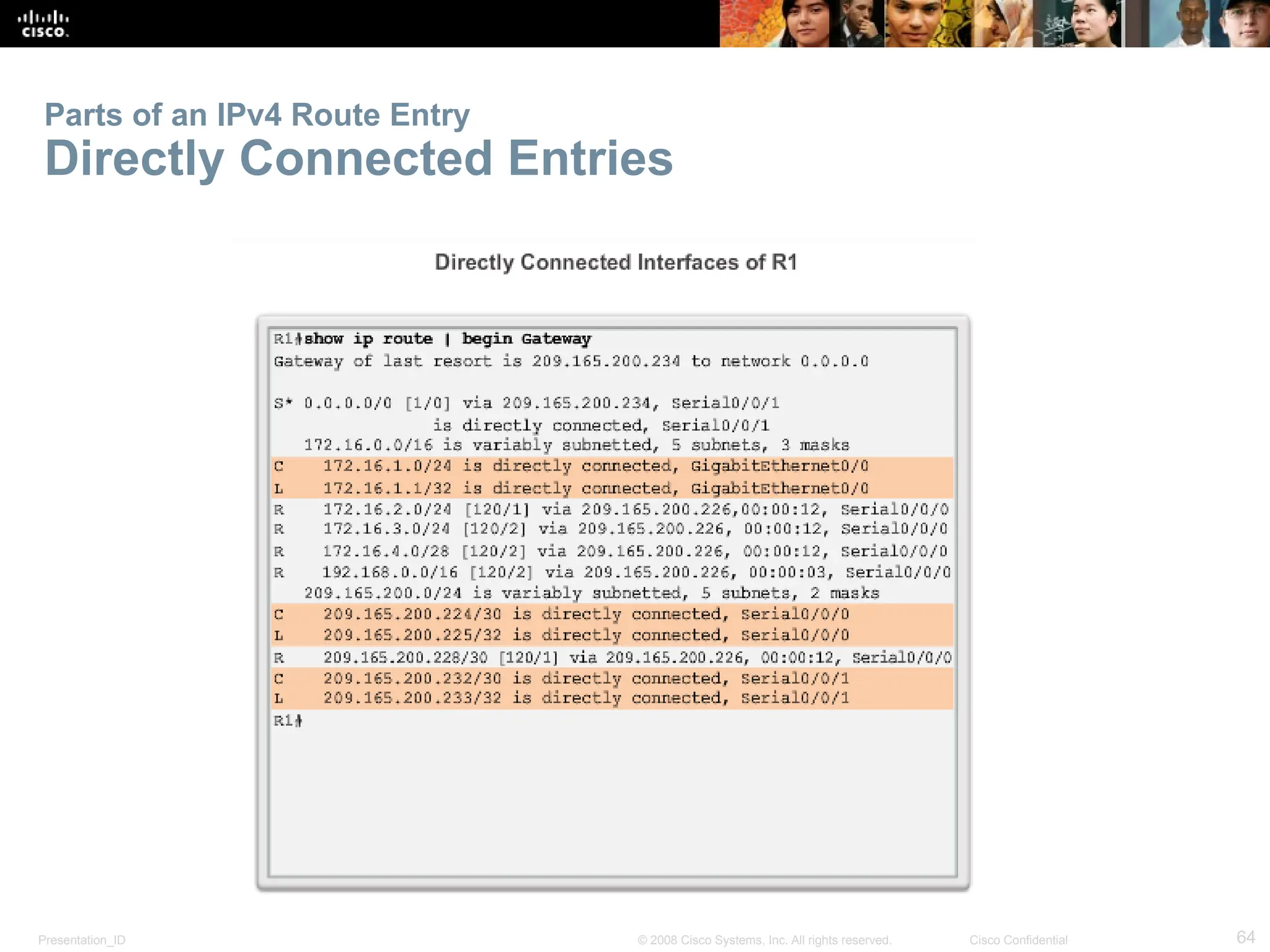
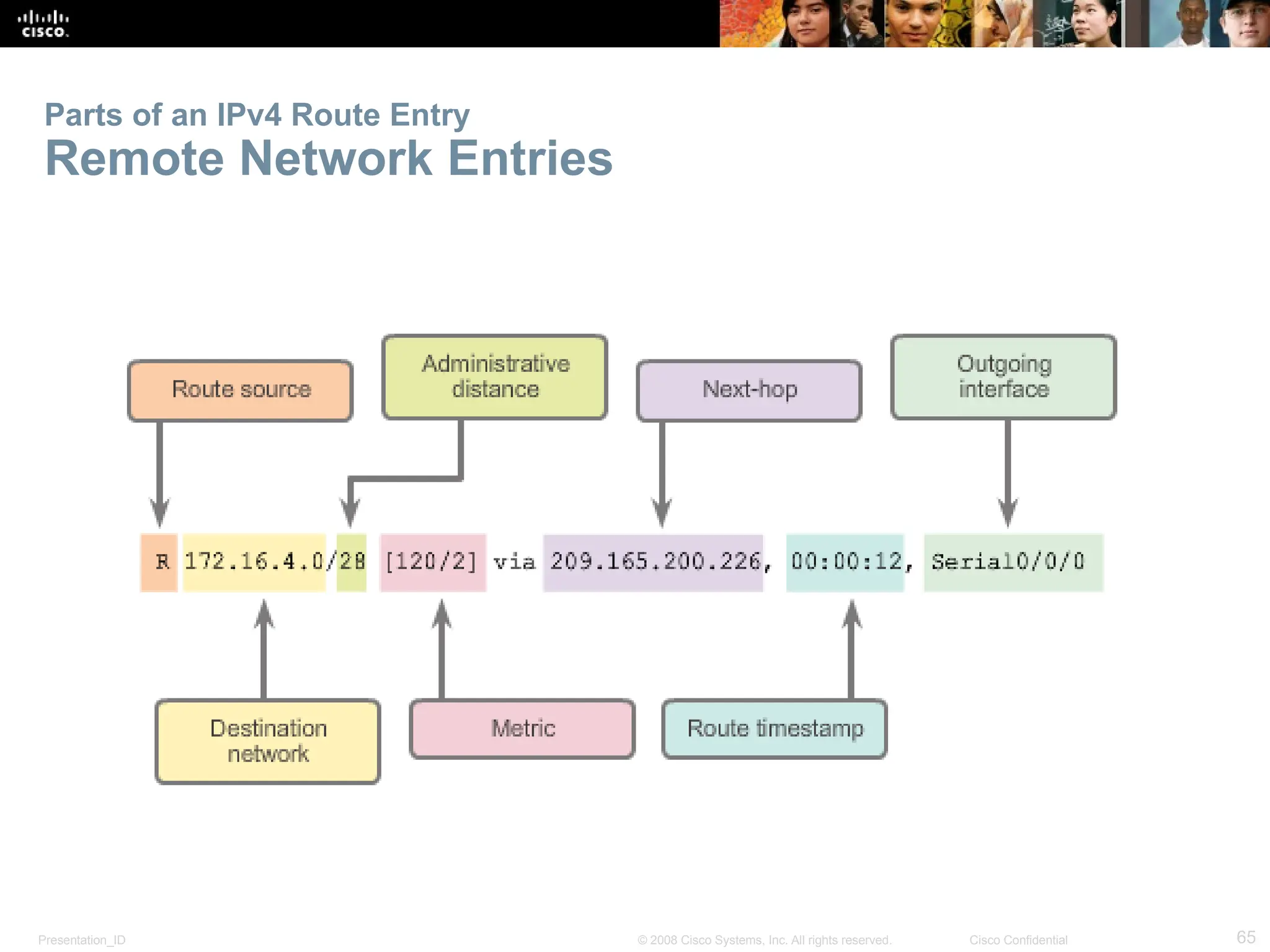
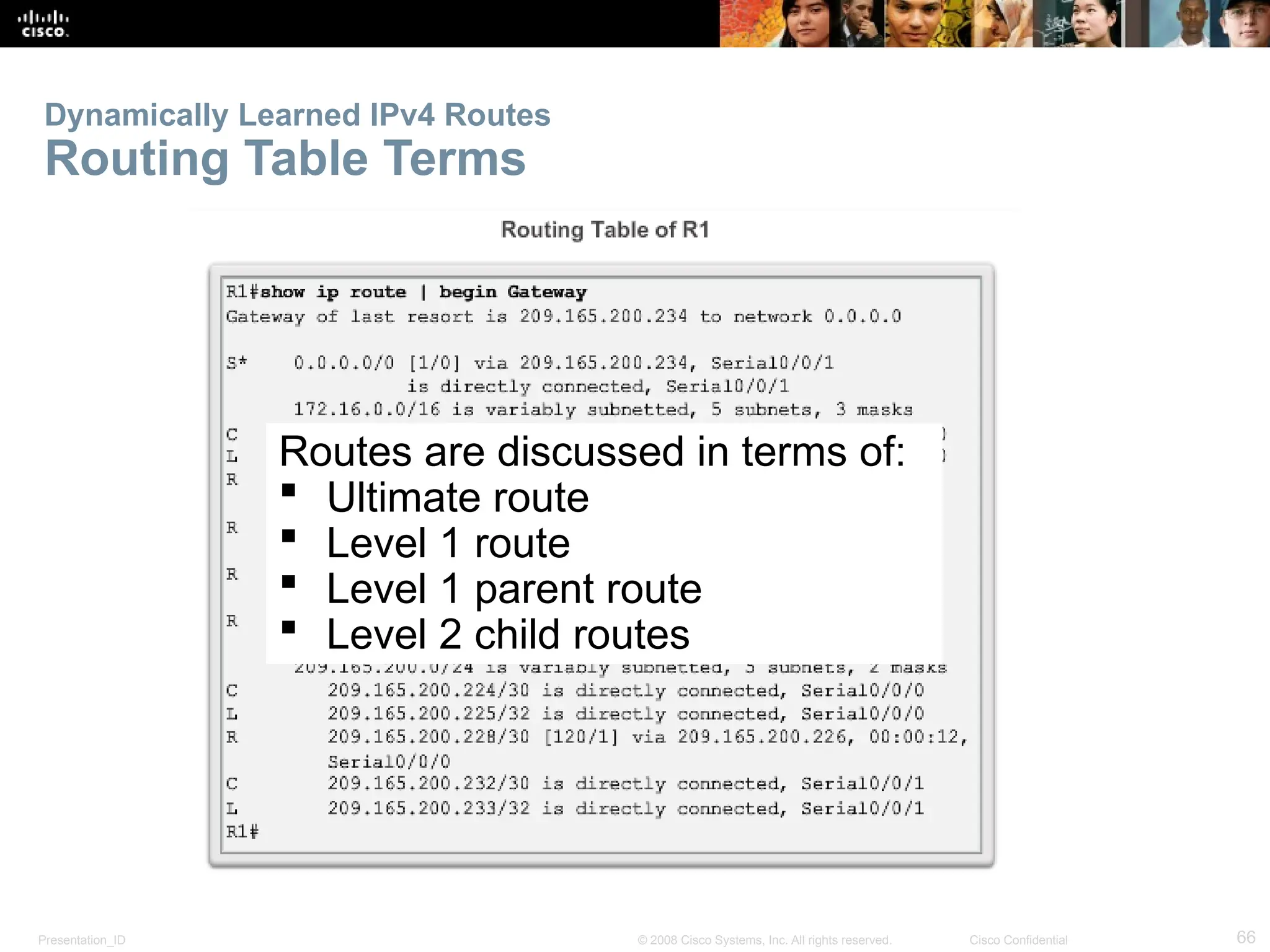
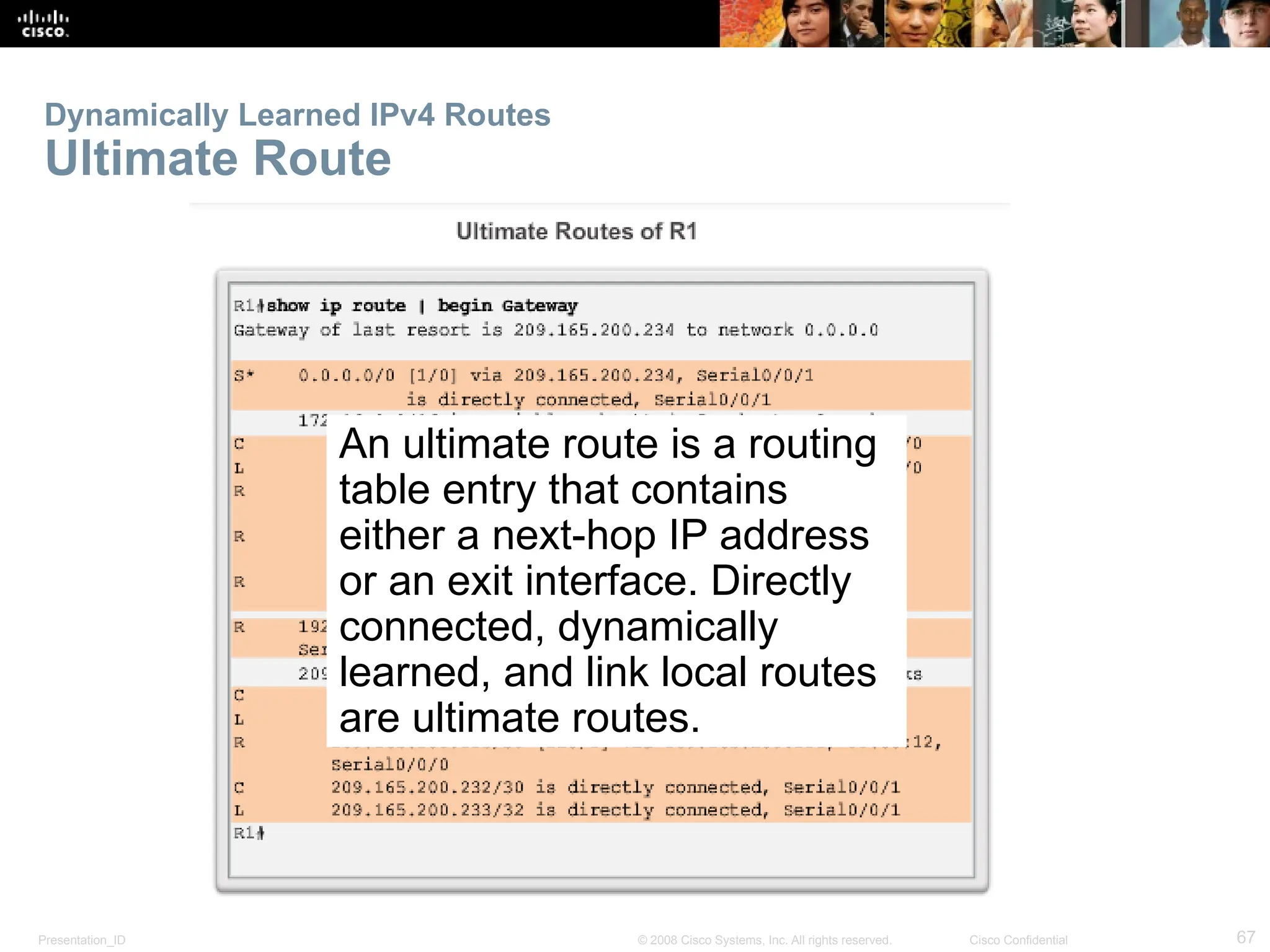
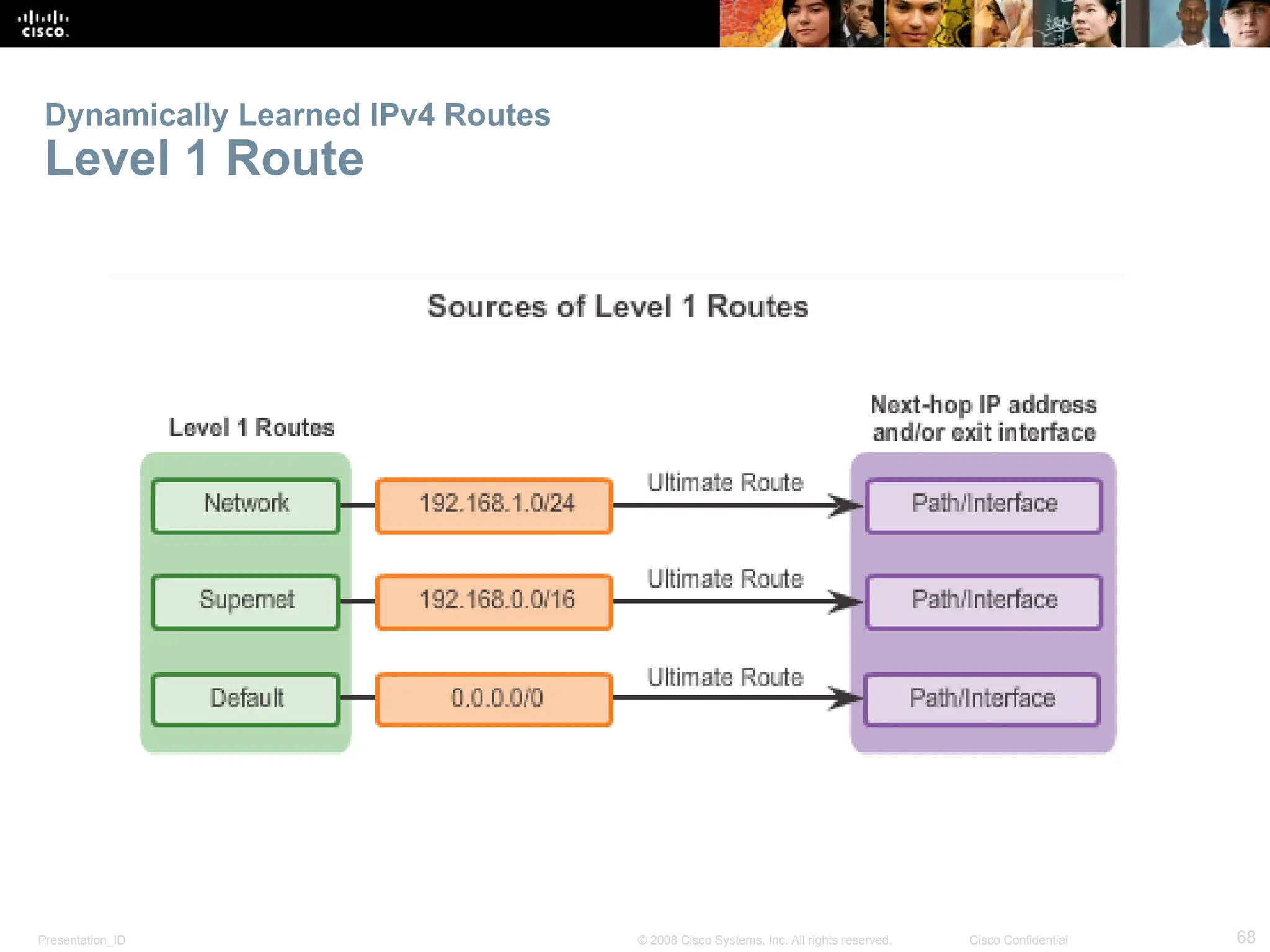
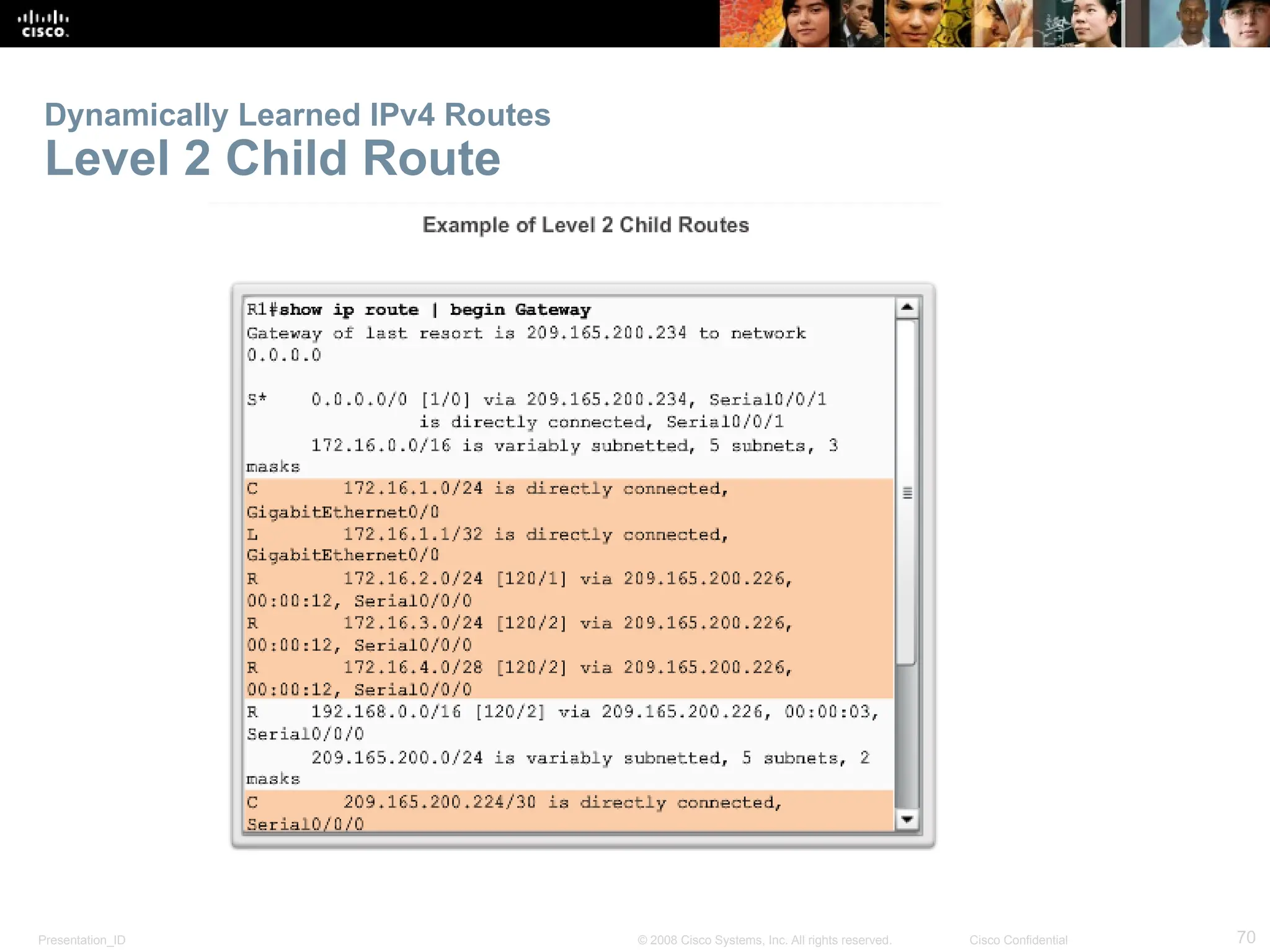
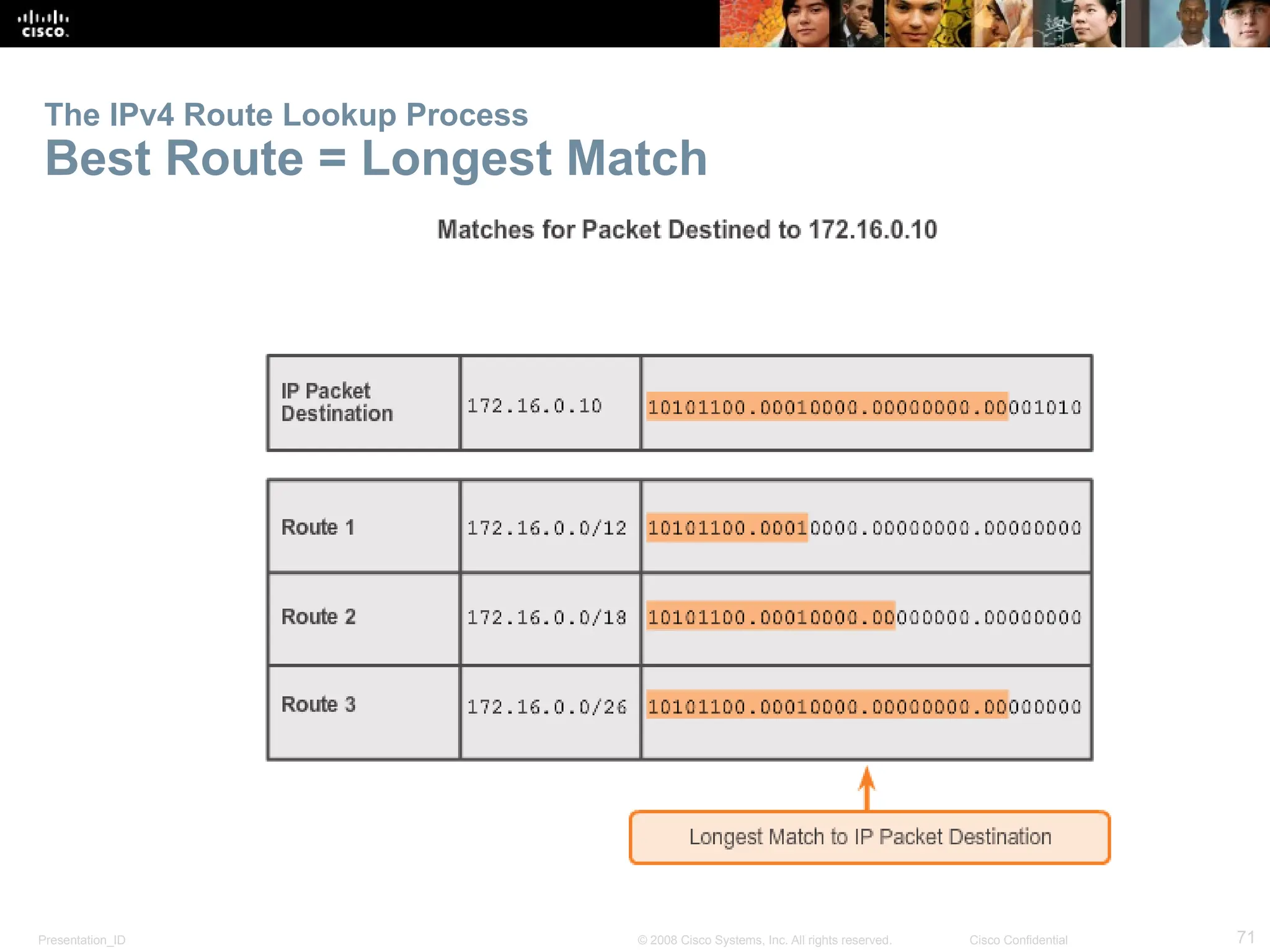
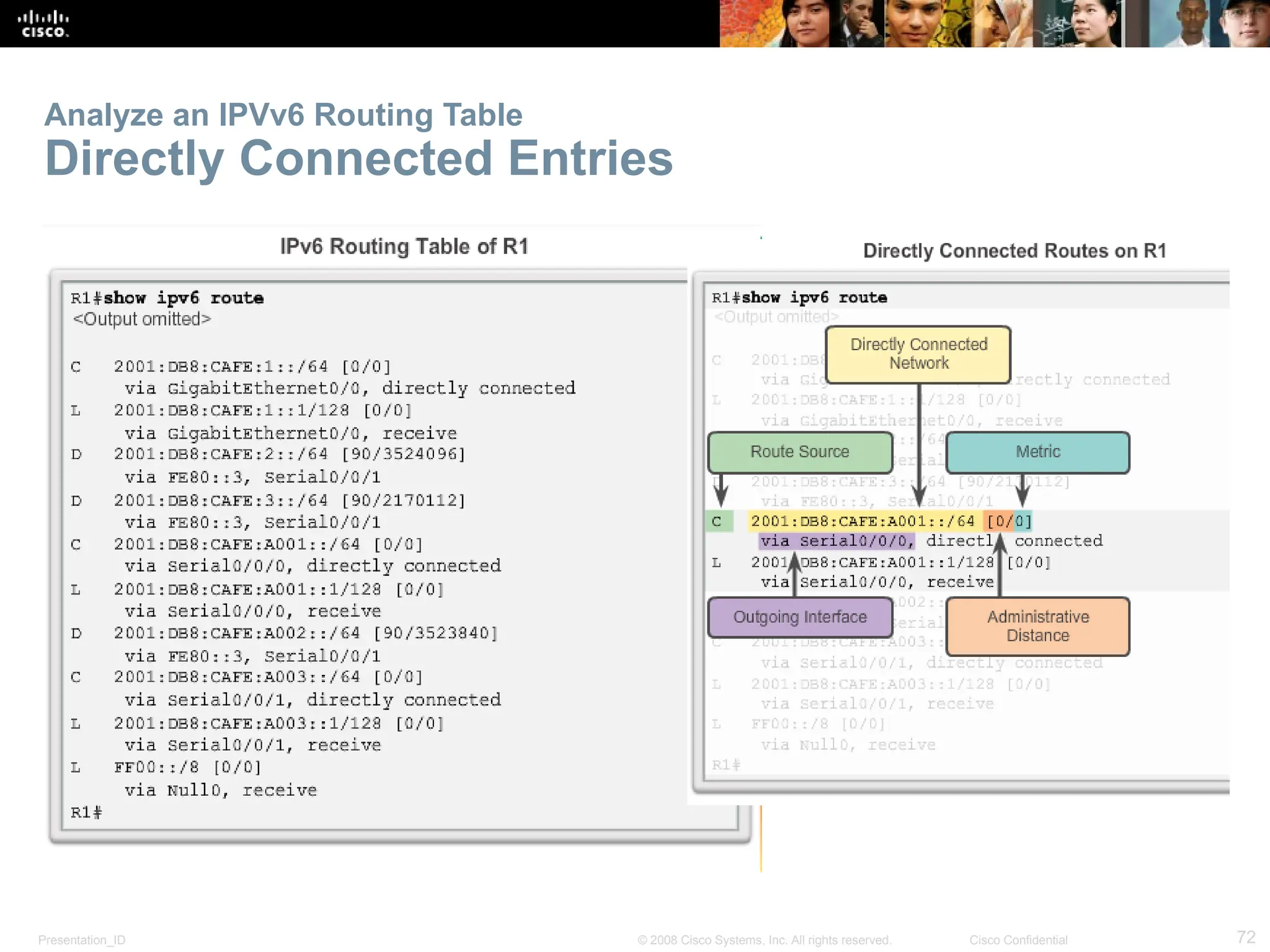
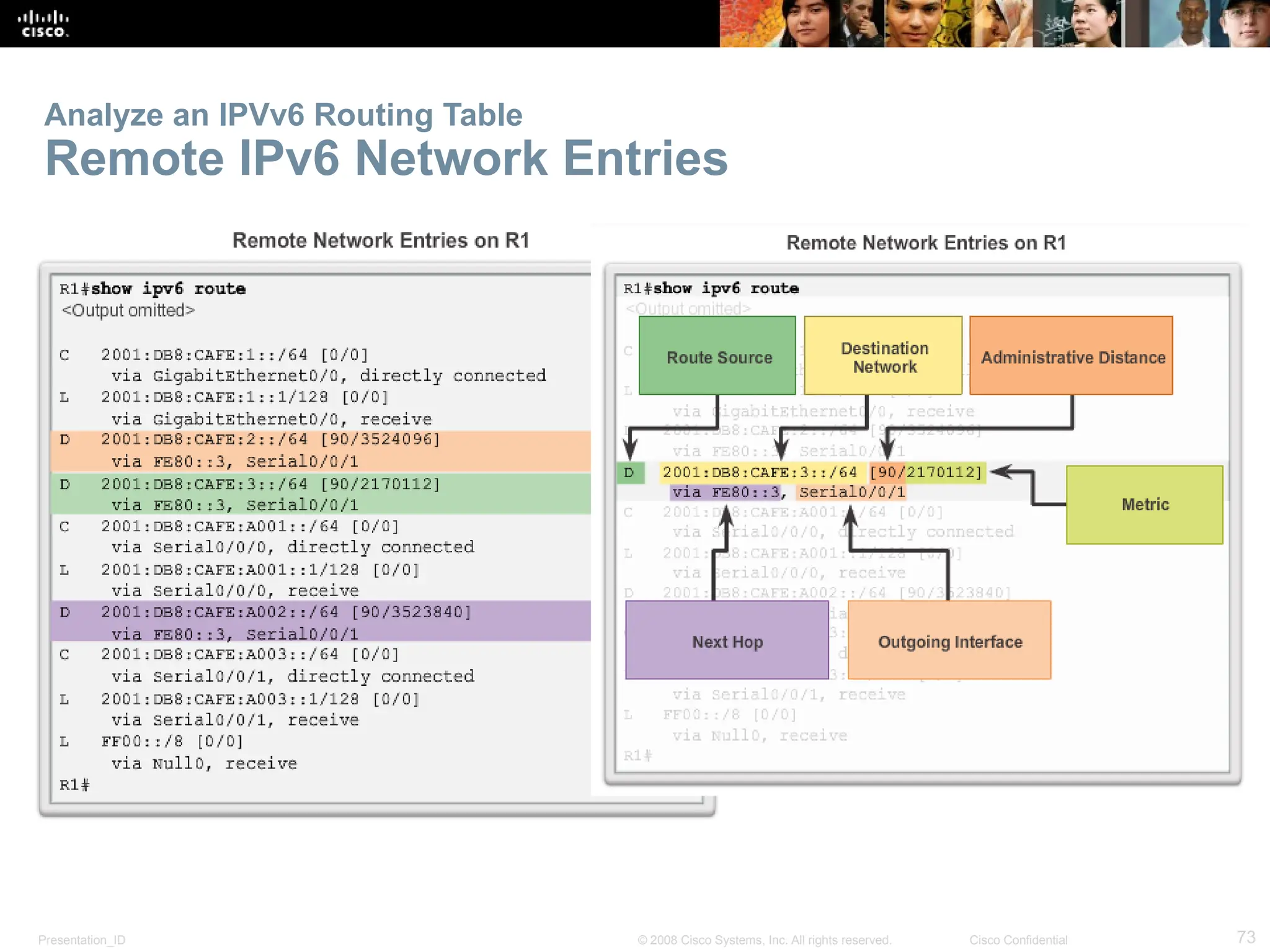
The document provides an overview of dynamic routing protocols, detailing their operation and advantages over static routing, including the processes of network discovery, routing message exchange, and convergence. It classifies various types of routing protocols such as distance vector and link-state, explaining their characteristics and mechanics. Additionally, it covers configuration instructions for protocols like RIP and RIPng, highlighting their administrative features and limitations.