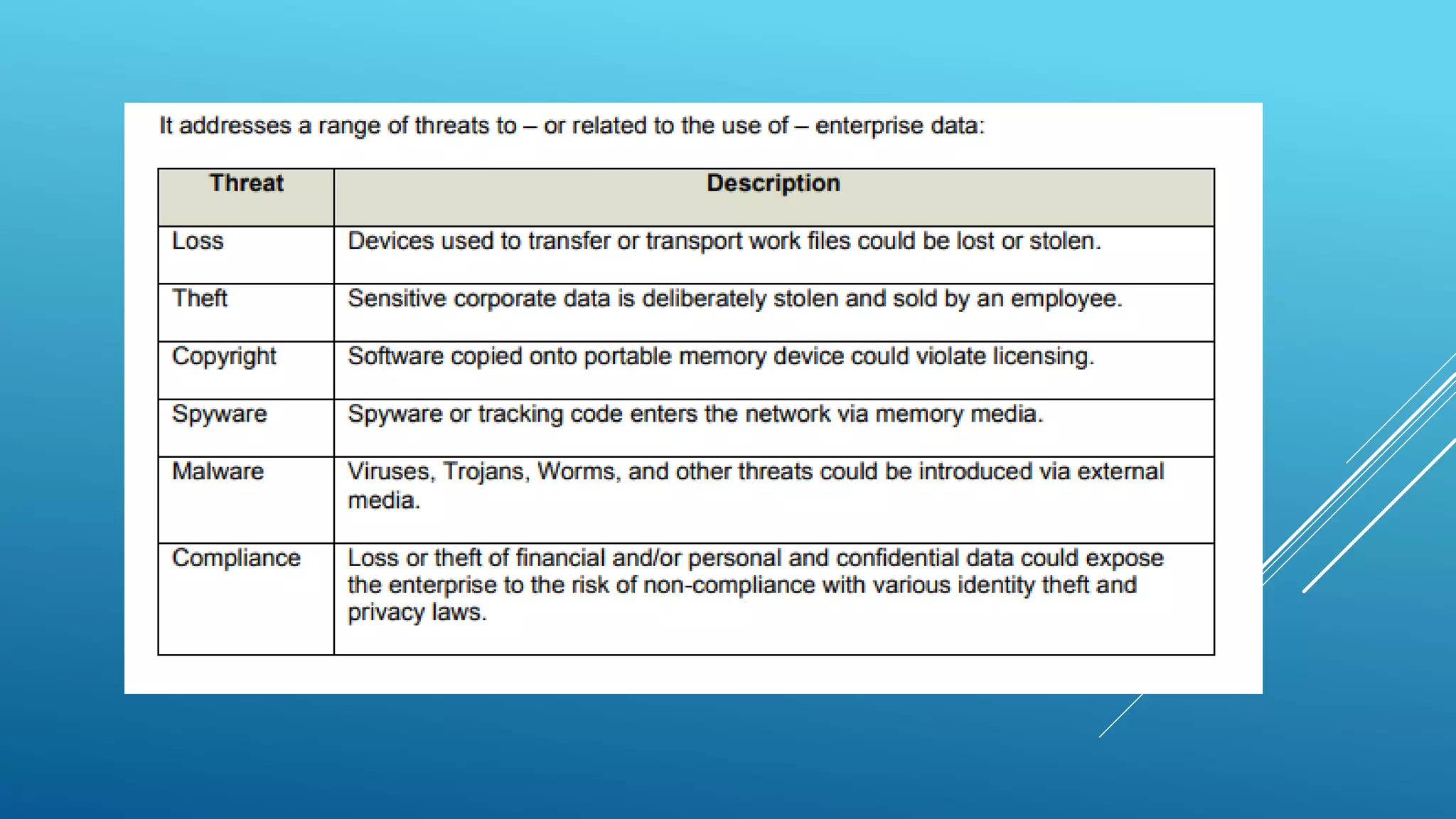
This document outlines an IT network security policy for a trust. It defines controls to help ensure confidentiality, integrity and availability of information on the network. It covers: responsibilities of information security managers to protect the network; annual risk assessments of the network; physical security measures for network equipment; access controls for trust staff, third parties, and wireless access; software installation restrictions; data backup and restoration procedures; and an acceptable use policy for removable media.