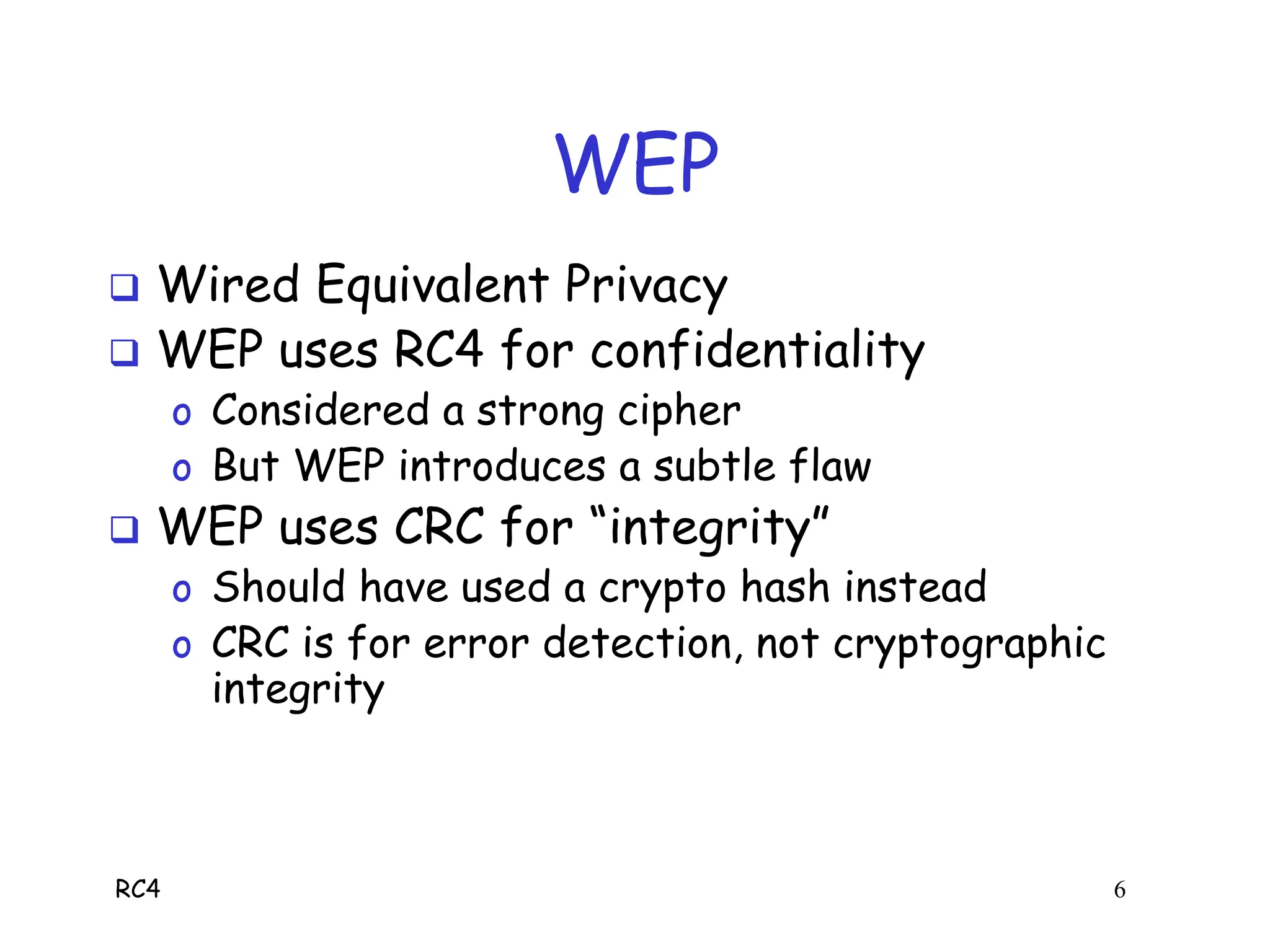
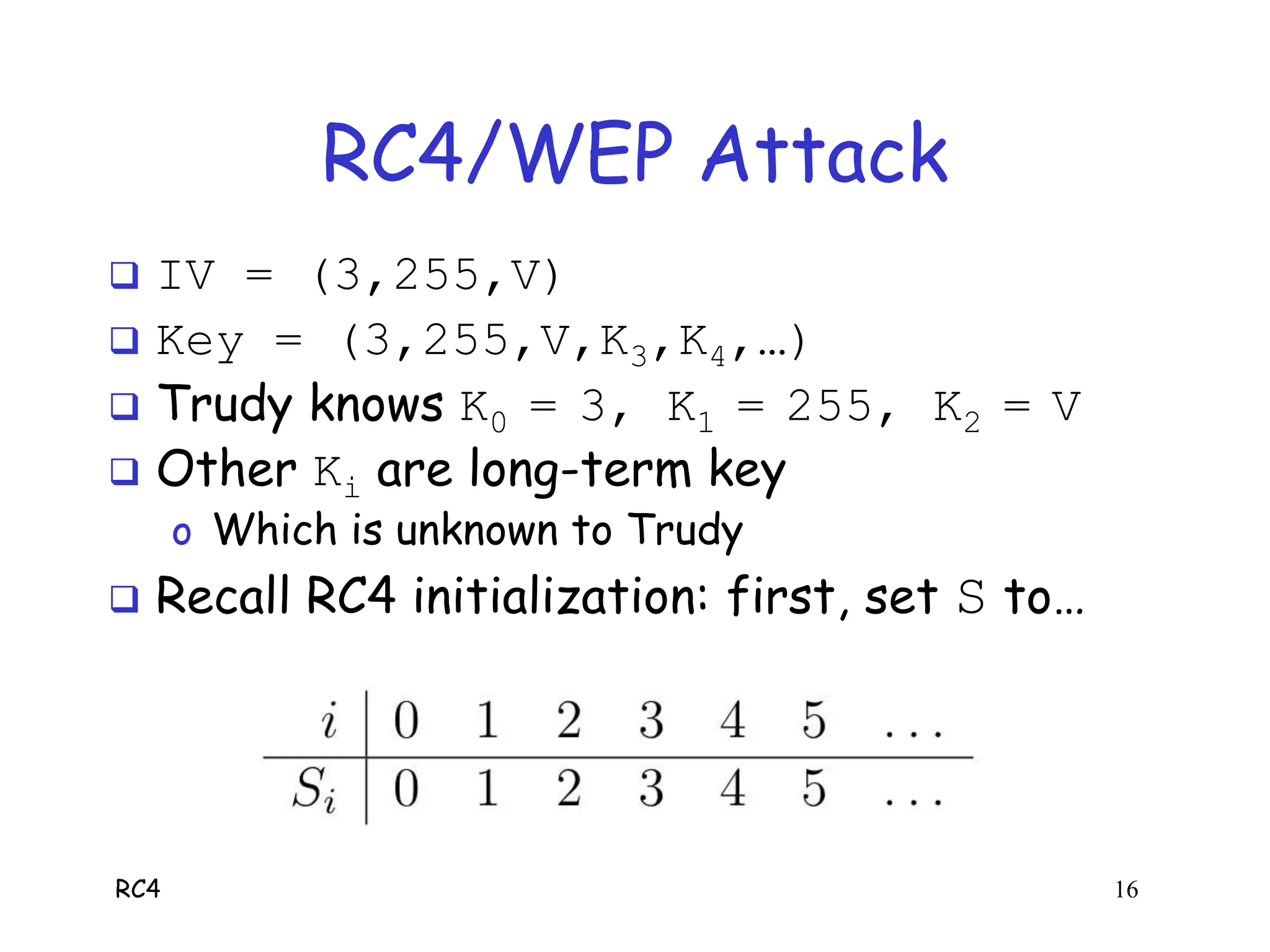
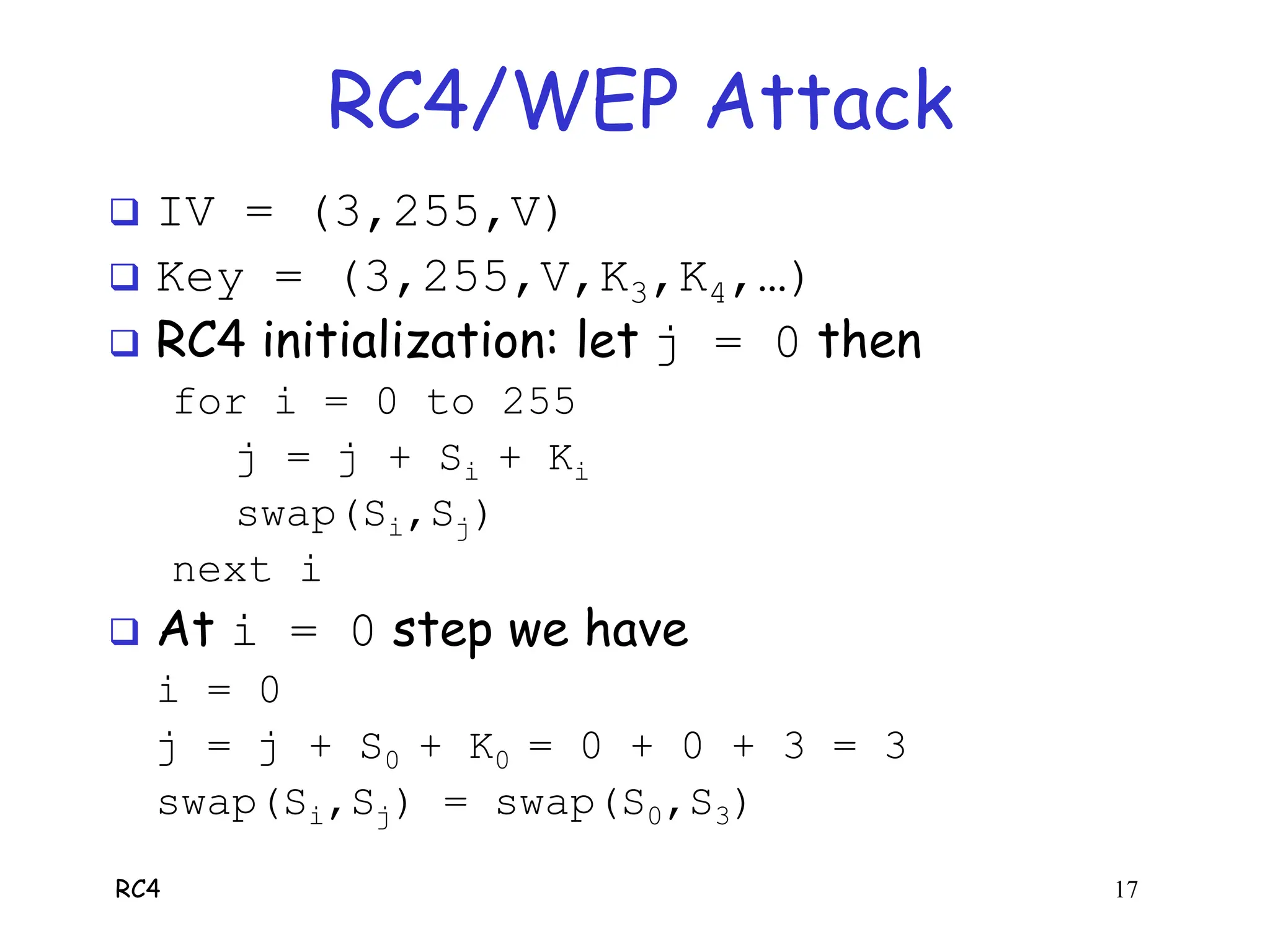
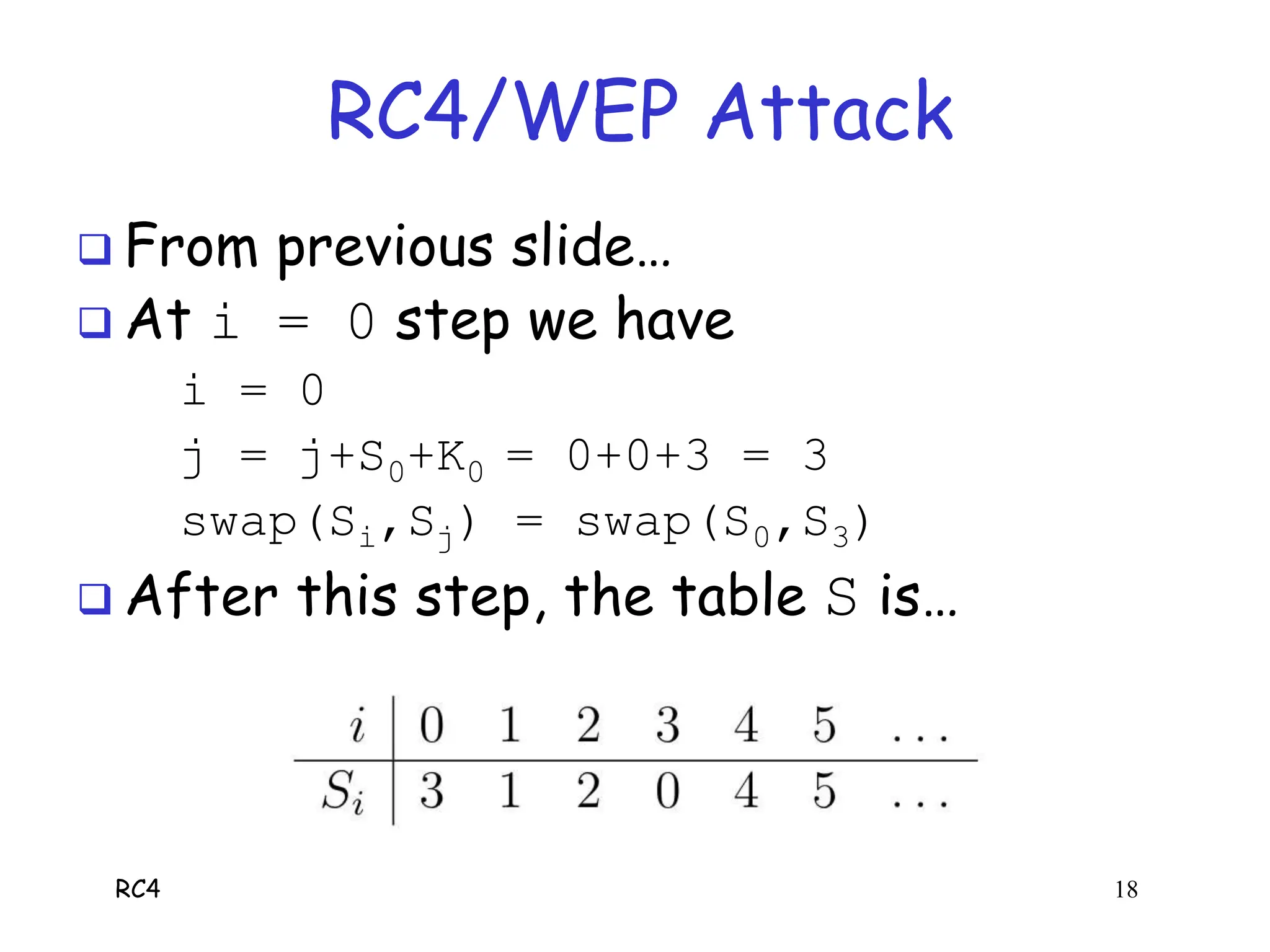
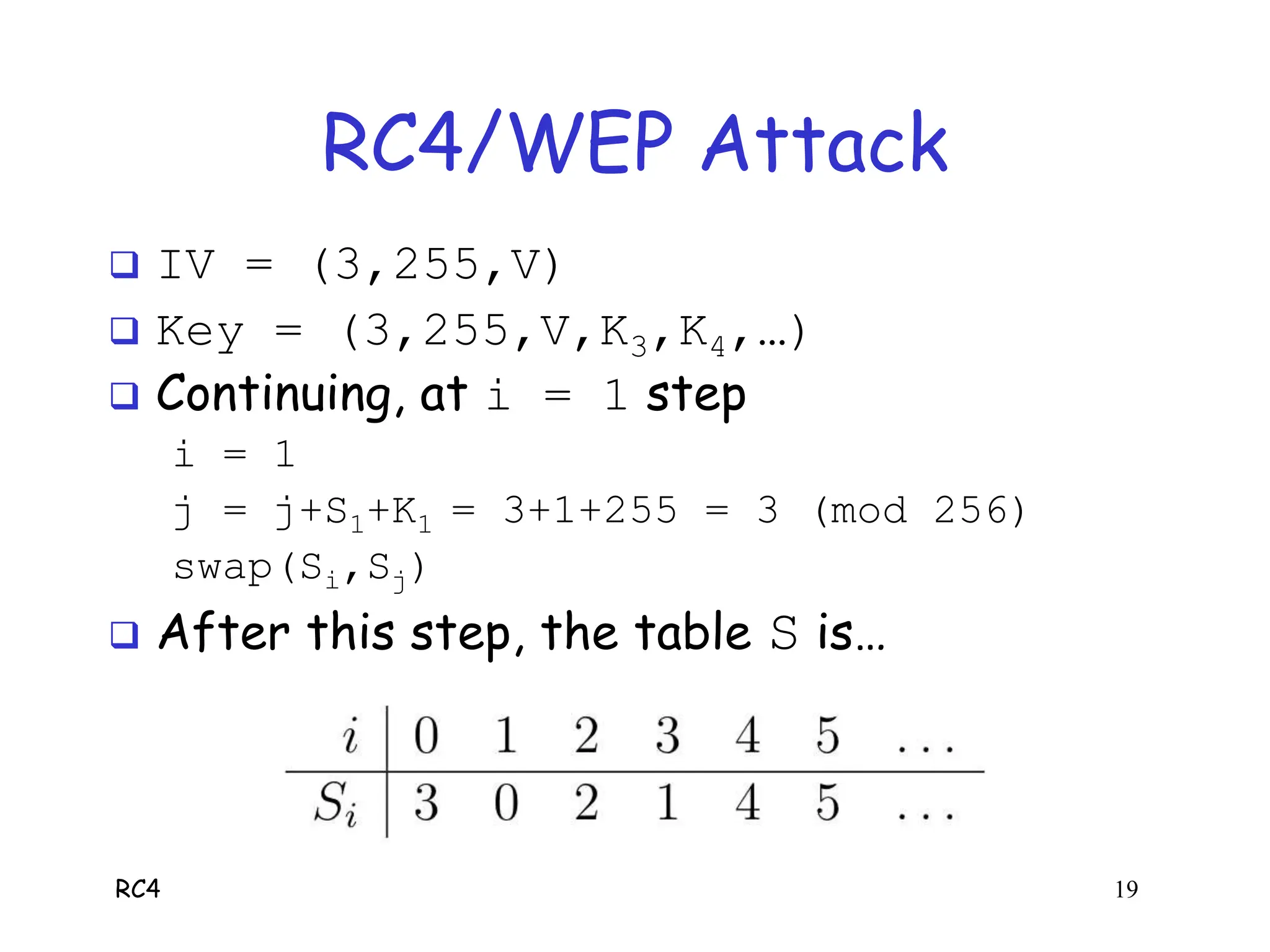
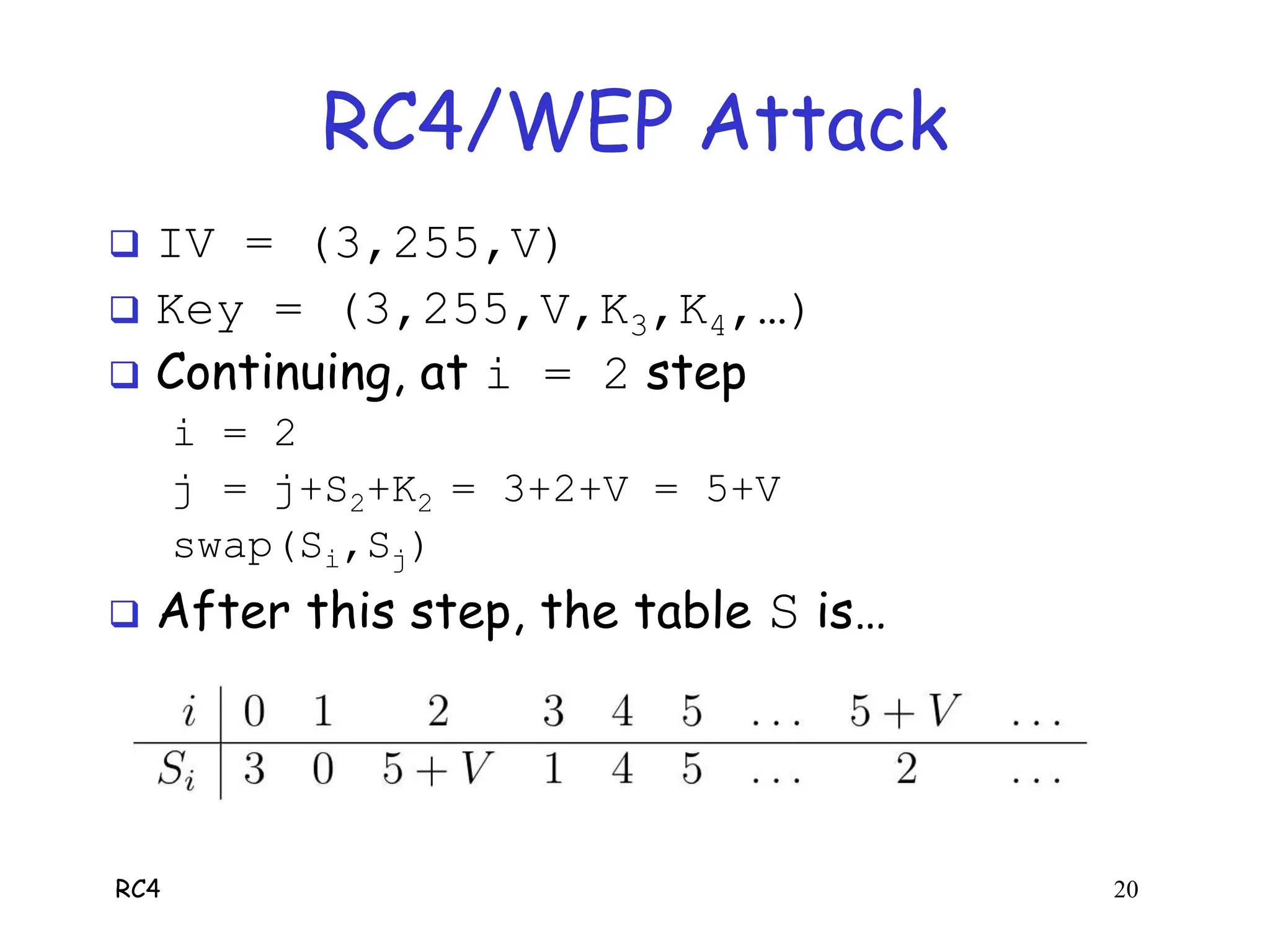
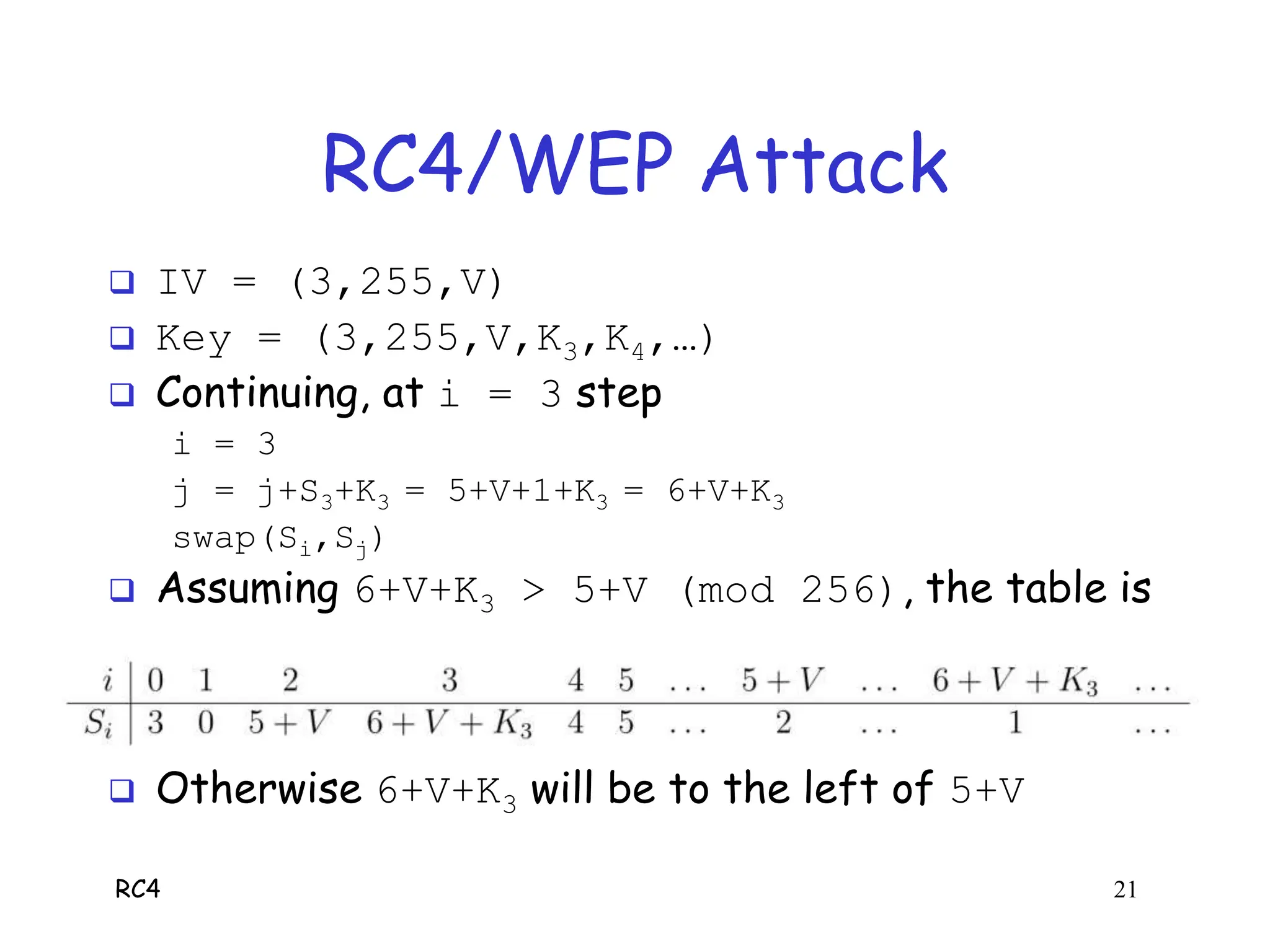
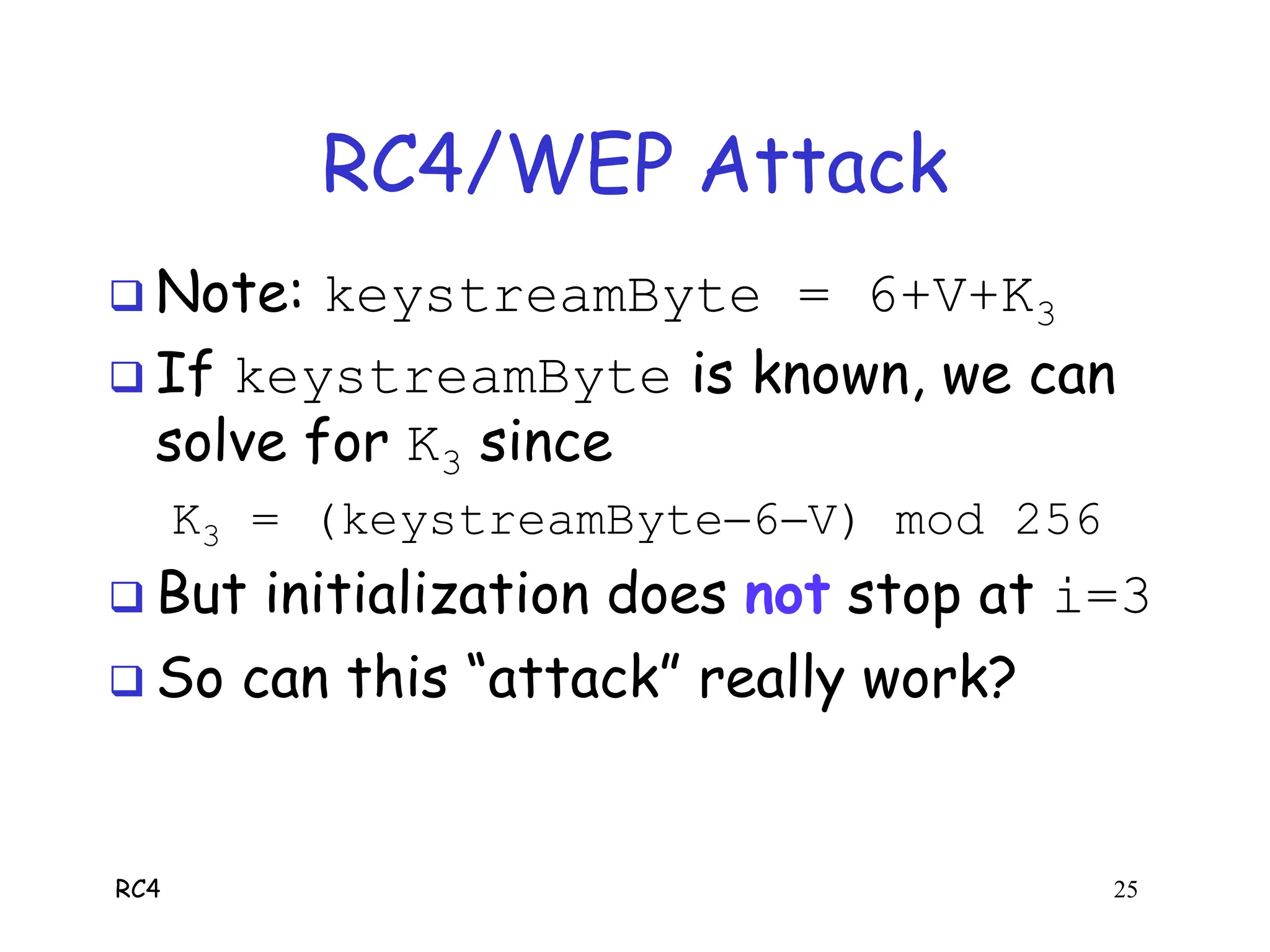
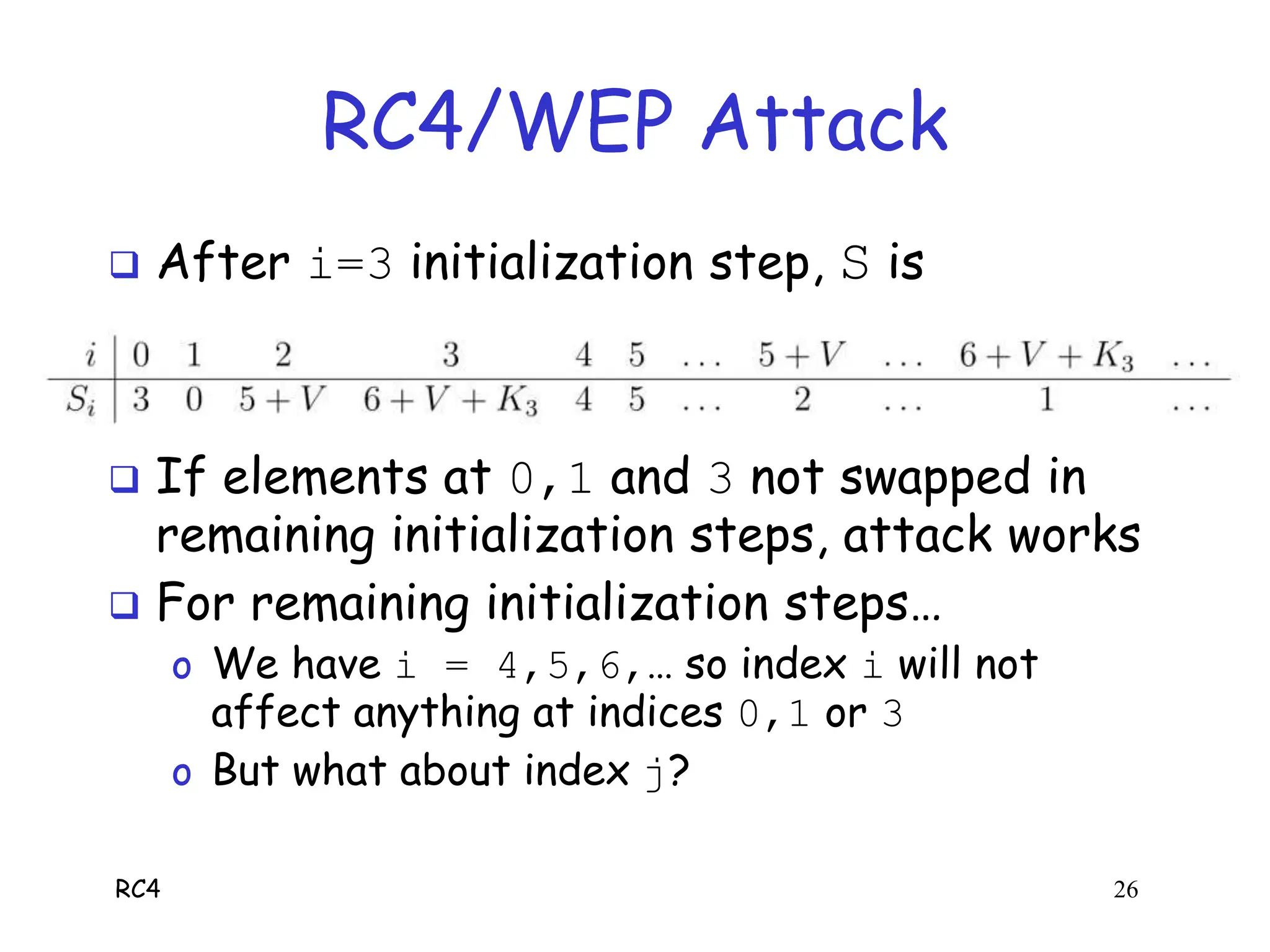
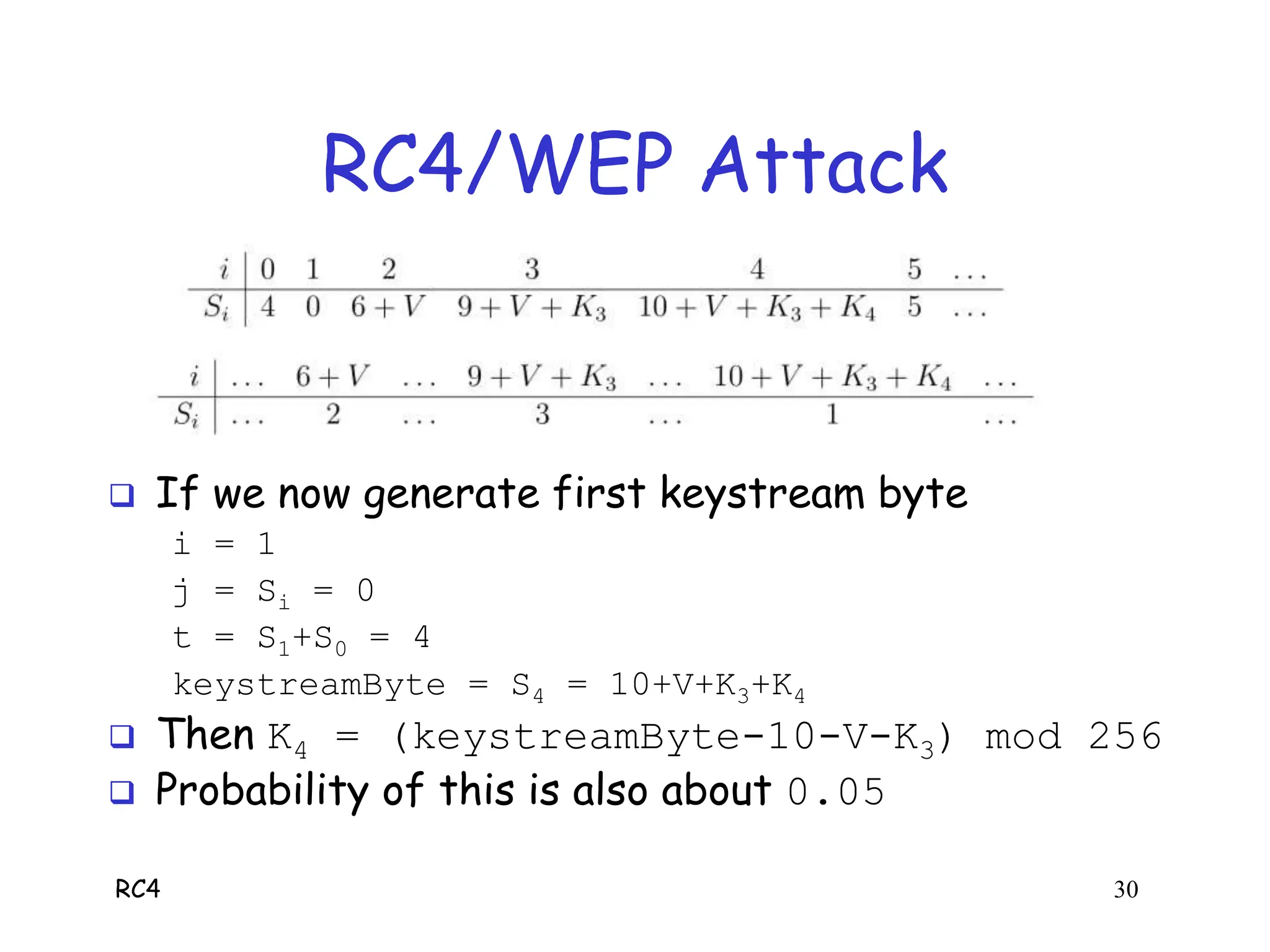
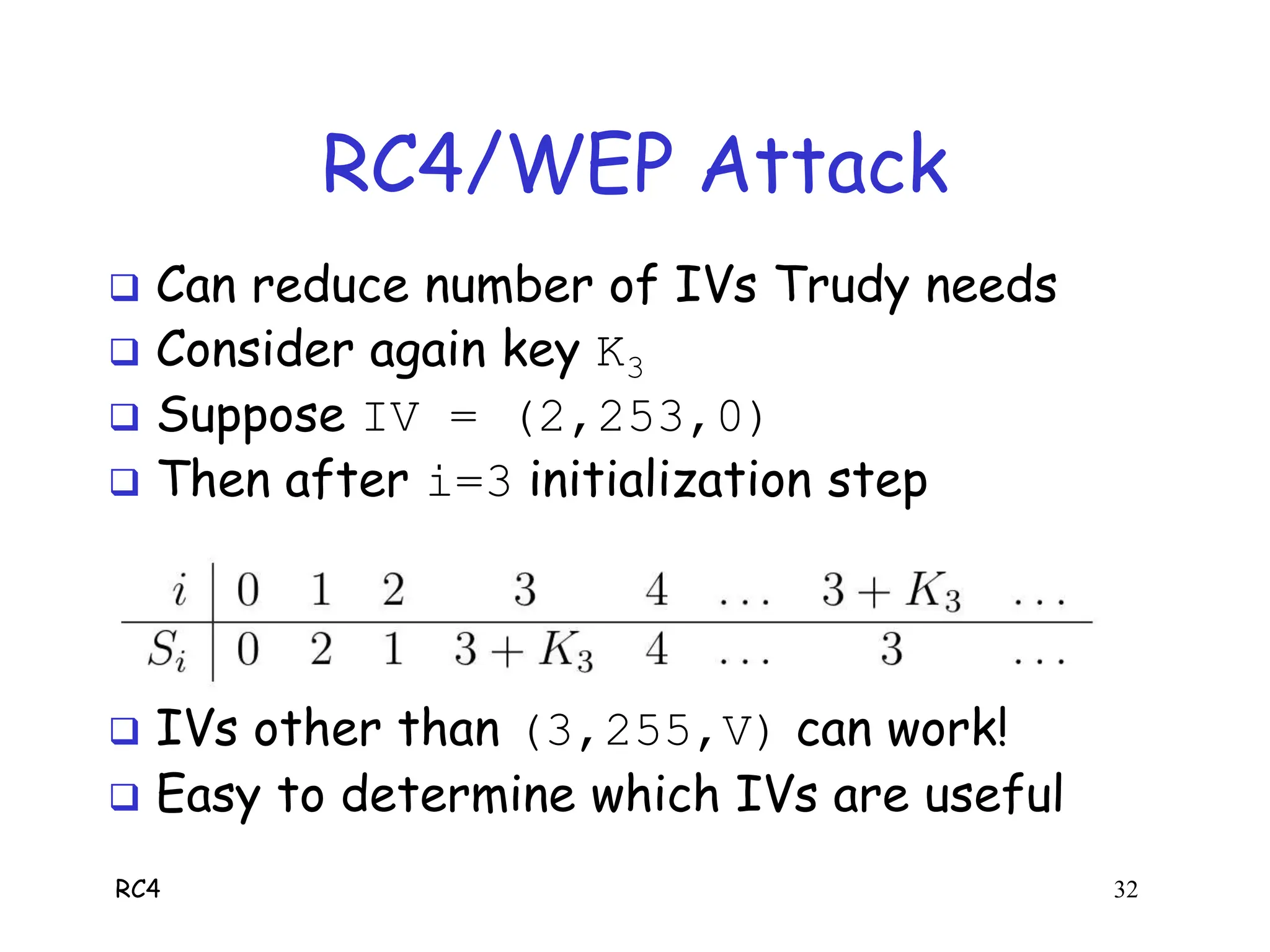
RC4 is a stream cipher invented by Ron Rivest that was used in WEP for wireless network encryption. WEP had flaws in how it used RC4, including reusing initialization vectors which allowed attackers to recover the encryption key by analyzing encrypted packets and known plaintext. The document describes how an attacker could use specific initialization vectors to determine bytes of the key one byte at a time, eventually recovering the full key regardless of its length through a known plaintext attack.


![RC4 3
RC4 Initialization
Array key contains N bytes of key
Array S always has a permutation of 0,1,…,255
for i = 0 to 255
S[i] = i
K[i] = key[i (mod N)]
next i
j = 0
for i = 0 to 255
j = (j + S[i] + K[i]) (mod 256)
swap(S[i],S[j])
next i
i = j = 0](https://image.slidesharecdn.com/5061616-240416210004-af5a949e/75/Ron-Rivest-4-Information-and-Network-Security-3-2048.jpg)
![RC4 4
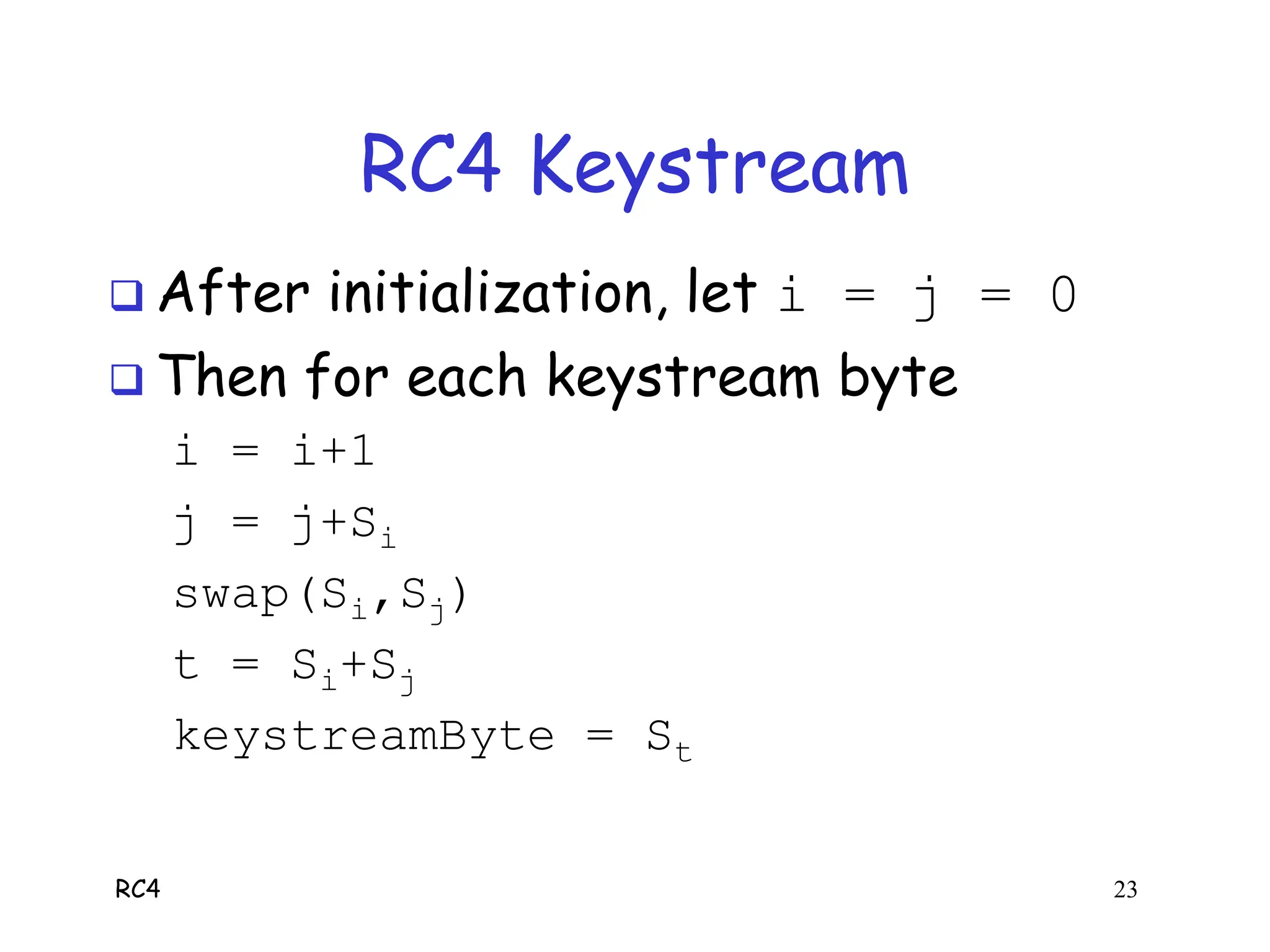
RC4 Keystream
For each keystream byte, swap elements of
array S and select a byte from the array:
i = (i + 1) (mod 256)
j = (j + S[i]) (mod 256)
swap(S[i], S[j])
t = (S[i] + S[j]) (mod 256)
keystreamByte = S[t]
Use keystream bytes like a one-time pad
o XOR to encrypt or decrypt](https://image.slidesharecdn.com/5061616-240416210004-af5a949e/75/Ron-Rivest-4-Information-and-Network-Security-4-2048.jpg)