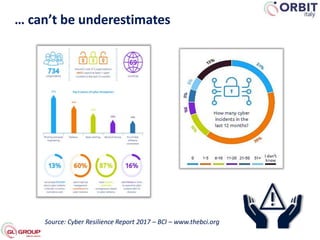
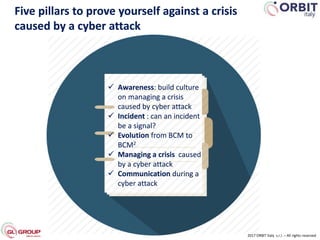
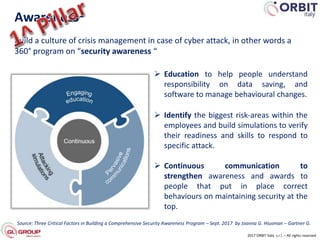
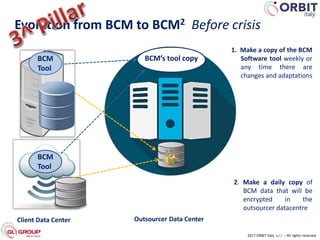
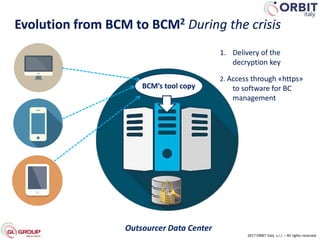
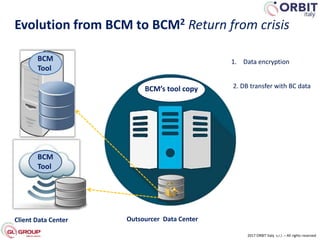
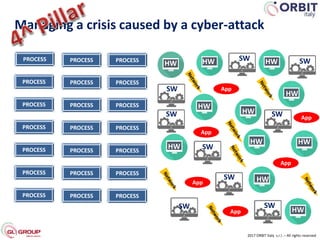
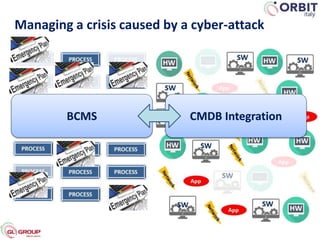
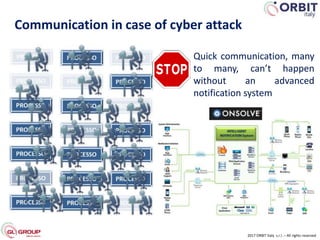
Roberto Perego from ORBIT Italy gave a presentation at the 7th ME Business & IT Resilience Summit in Dubai on facing a cyber attack as a business continuity manager. He discussed five pillars for being resilient against a crisis caused by a cyber attack: building an awareness culture, treating incidents as potential signals of attack, evolving business continuity management plans to also address cyber attacks, managing an actual crisis, and effective communication during an attack. Perego argued that business continuity managers need tools that can help monitor for early signals of attack, enable continuity plans to respond to cyber incidents, and ensure effective crisis communication.