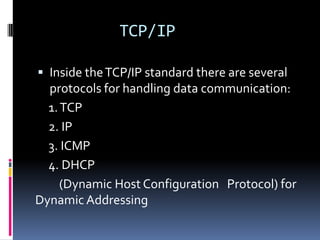
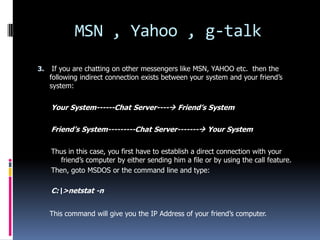
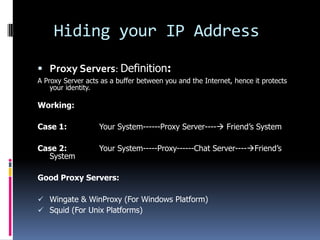
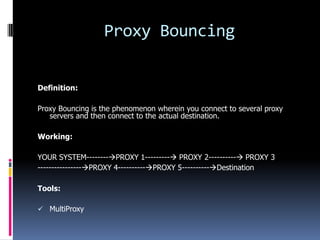
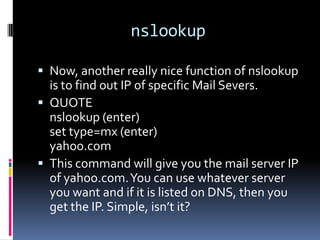
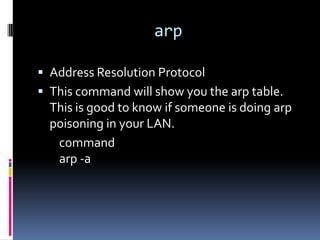
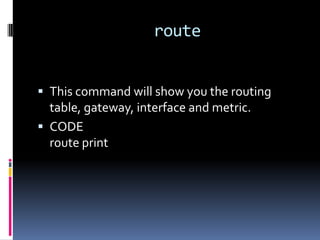
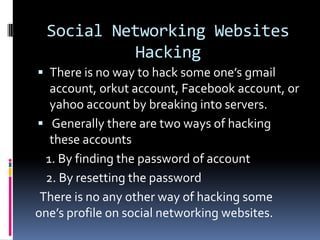
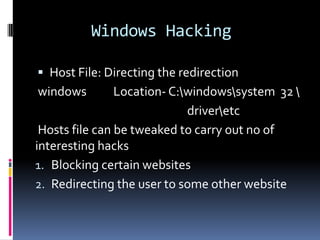
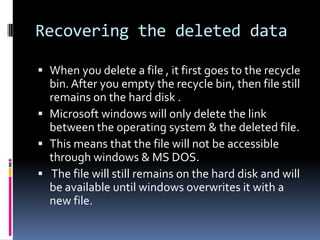
This document introduces the concept of ethical hacking. It begins by defining hacking as finding solutions to real-life problems, and clarifies that the original meaning of "hack" was not related to computers. It then discusses how the term entered computer culture at MIT in the 1960s, where hackers were students who solved problems in innovative ways, unlike "tools" who just attended class. The document outlines some traits of good hacks and provides examples. It emphasizes that media misconstrues hackers as criminals, and explains that real hackers have strong ethics and help catch cyber criminals, unlike crackers who hack systems illegally. The rest of the document provides an overview of skills, subjects, and basic concepts needed for ethical hacking.