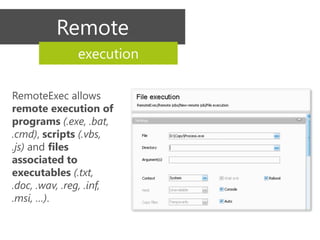
RemoteExec is a utility application designed for administrators managing multiple Windows systems, facilitating remote installations, updates, and executions. Key features include deployment of .msi packages, remote execution of scripts, automated reporting, and integrated scheduling for tasks. It is an agentless solution that enhances security and efficiency in managing system tasks across networks.