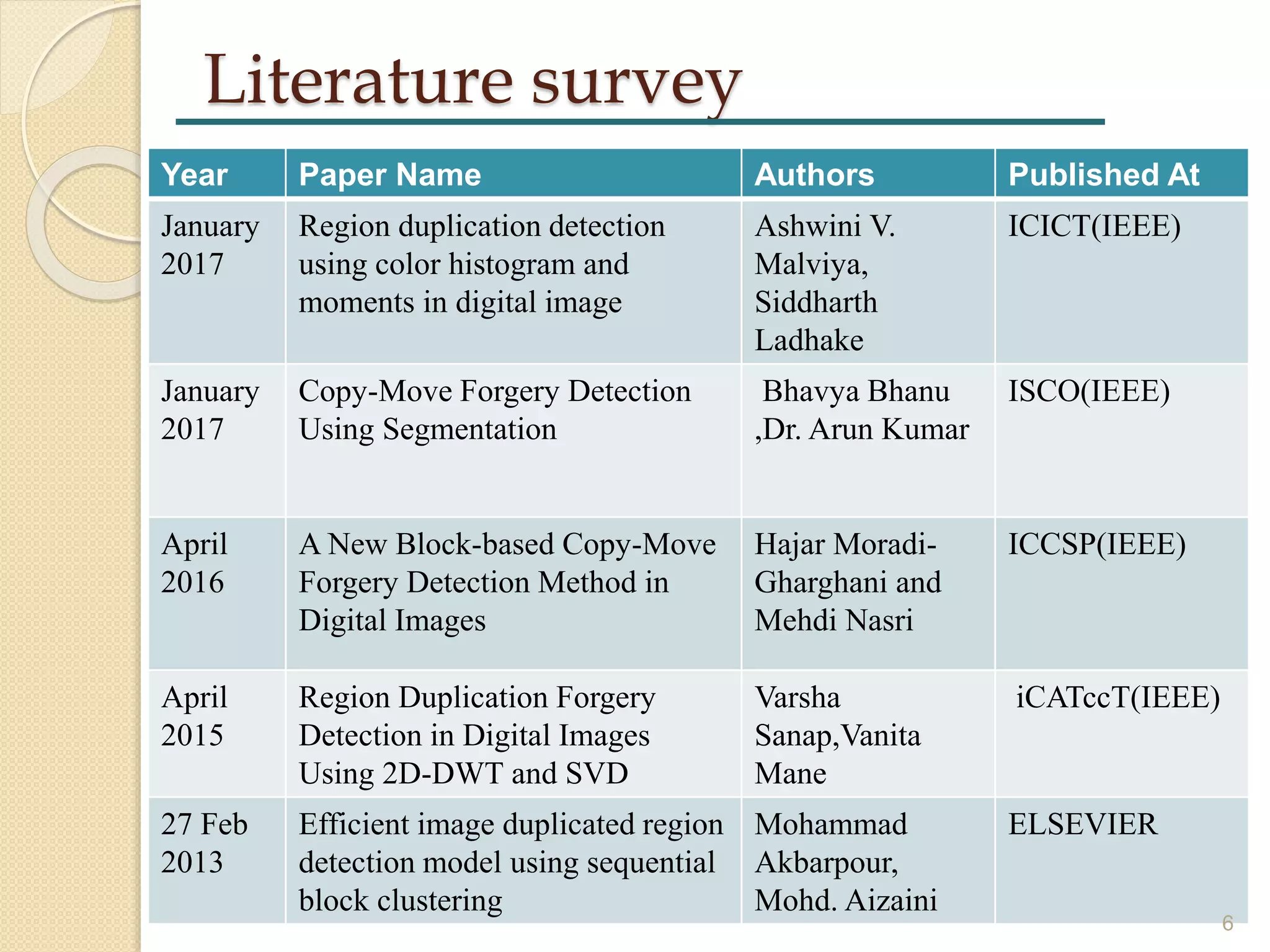
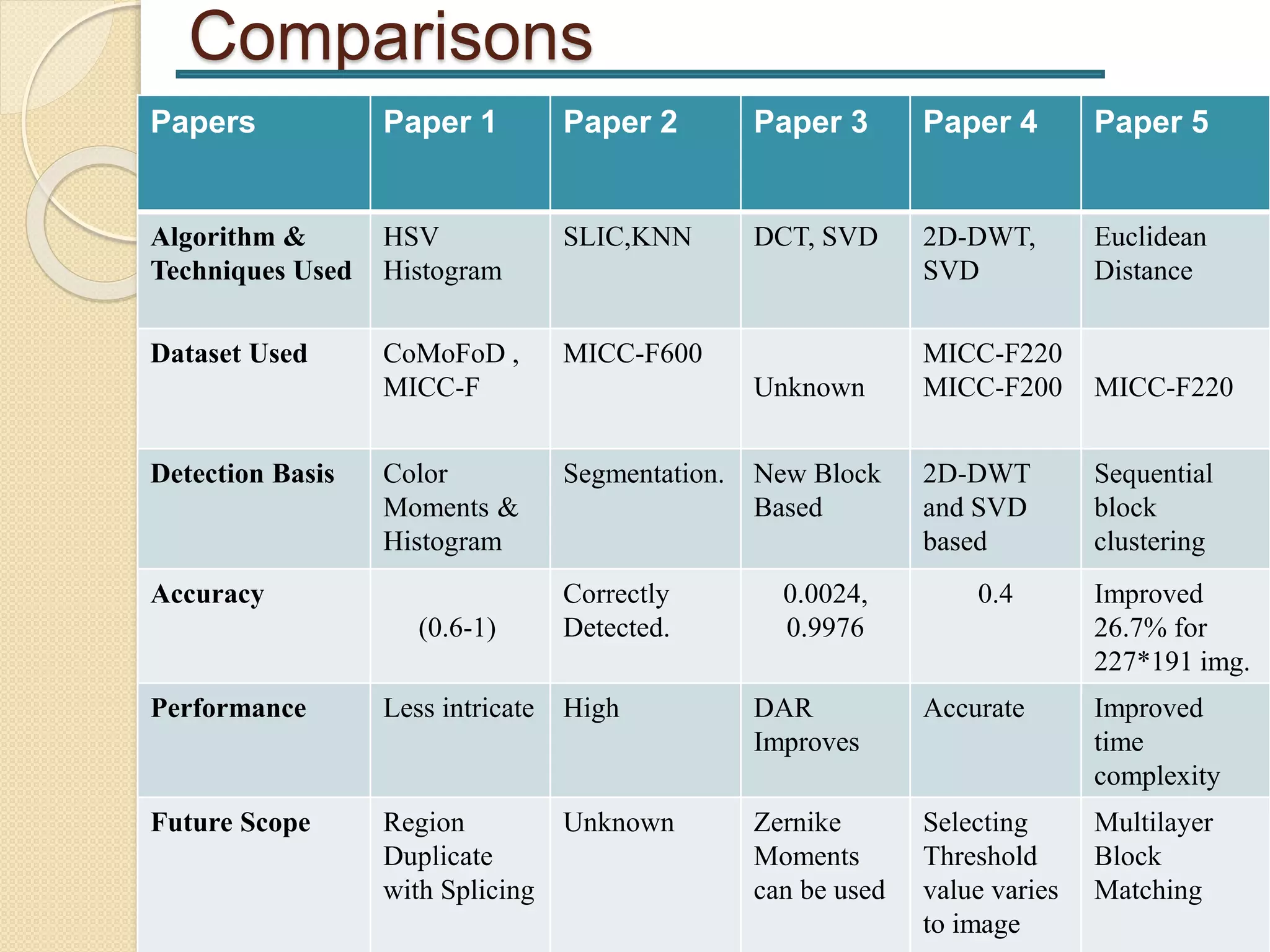
The document presents a study on region duplication forgery detection in digital images, outlining the process of image forgery and methods for detecting it, such as copy-move forgery. It provides a literature survey of several papers detailing different algorithms and techniques, including their comparisons and applications in fields like medical imaging and legal documentation. The presentation concludes with future directions for improving detection accuracy using advanced techniques.



![Introduction(3/3)
Figure 2.-Image Authentication Techniques[6]
5](https://image.slidesharecdn.com/regionduplicationforgerydetectionindigitalimages-180325175447/75/Region-duplication-forgery-detection-in-digital-images-5-2048.jpg)
![Paper 1: Region duplication detection using color
histogram and moments in digital image[1]
Figure3. Proposed Algorithm
7](https://image.slidesharecdn.com/regionduplicationforgerydetectionindigitalimages-180325175447/75/Region-duplication-forgery-detection-in-digital-images-7-2048.jpg)
![Image Segmentation
Input image
Matching Stage
Displaying Detected
CMF Regions
Inliers Estimation
Patch Matching
Feature Extraction
Detection Result
Figure-4. Flowchart of proposed method 8
Paper 2:Copy-Move Forgery Detection Using
Segmentation[2]
Final Stage](https://image.slidesharecdn.com/regionduplicationforgerydetectionindigitalimages-180325175447/75/Region-duplication-forgery-detection-in-digital-images-8-2048.jpg)
![Divide into
overlapping
block
Threshold
Parameters
Input image
Applying 2-D
DCT &
Quantization
Extracting
feature(SVD)
Remove
Distributed
Matching
Output image
Figure-5 . Forgery detection process 9
Lexicographicall
y ordering
Paper 3: A New Block-based Copy-Move Forgery
Detection Method in Digital Images[3]](https://image.slidesharecdn.com/regionduplicationforgerydetectionindigitalimages-180325175447/75/Region-duplication-forgery-detection-in-digital-images-9-2048.jpg)
![10
Forgery Org.
Image
Performance
Measurement
Hit Rate
Extract R,G,B
Channel
Apply 2D-DWT
Apply Block
Processing
Candidate Block
Selection
Apply SVD on Each
block
Forged Block
Detection
FDRMiss Rate
Figure-6 . Proposed Algorithm
Paper 4: Region Duplication Forgery detection in
Digital Images Using 2D-DWT and SVD[4]](https://image.slidesharecdn.com/regionduplicationforgerydetectionindigitalimages-180325175447/75/Region-duplication-forgery-detection-in-digital-images-10-2048.jpg)
![Figure-7 . Flowchart
11
Paper 5:Efficient image duplicated region detection
model using sequential block clustering[5]](https://image.slidesharecdn.com/regionduplicationforgerydetectionindigitalimages-180325175447/75/Region-duplication-forgery-detection-in-digital-images-11-2048.jpg)



![References
[1] Ashwini V. Malviya, Siddharth Ladhake ,”Region duplication detection using
color histogram and moments in digital image”,in ICICT(IEEE) ,January 2017.
[2] Bhavya Bhanu , Dr. Arun Kumar.”Copy-Move Forgery Detection Using
Segmentation”,in IEEE Tran. January 2017.
[3] Hajar Moradi-Gharghani and Mehdi Nasri ,”A New Block-based Copy-Move
Forgery Detection Method in Digital Images” in IEEE Tran.,April 2016.
[4]Vanita Manikrao Mane, Varsha Karbhari Sanap , ”Region Duplication Forgery
Detection in Digital Images Using 2D-DWT and SVD”, IEEE Trans. April 2015.
[5] Mohammad Akbarpour, Mohd. Aizaini ,”Efficient image duplicated region
detection model using sequential block clustering”, in ELSEVIER, Feb 2013
[6] Saba Mushtaq and Ajaz Hussain Mir,”Digital Image Forgeries and Passive Image
Authentication Techniques: A Survey”IEEE Tranct.2010.
16](https://image.slidesharecdn.com/regionduplicationforgerydetectionindigitalimages-180325175447/75/Region-duplication-forgery-detection-in-digital-images-16-2048.jpg)
