QUARTERLY MONTHLY WEEKLY DAILY (IT) AUDIT CHECK LIST
•
0 likes•27 views
This checklist can be used as a Quarterly, Monthly, Weekly or Daily checklist for your internal IT Audit. Contact us for all your IT infrastructure and services requirements.
Report
Share
Report
Share
Download to read offline
Recommended
QUARTERLY MONTHLY WEEKLY DAILY (IT) AUDIT CHECK LIST.pdf

Data loss or theft can certainly put a damper on your holidays. Losing important information or having personal data compromised can be distressing. It's always wise to take precautions to prevent such issues during your holiday. Please follow useful tips & tricks to secure your devices and network.
Get IT Audit regular checklist & VI Scan complimentary tool. Click on the above image to claim now...
About tools?
Regular IT audits with a defined checklist can be instrumental in preventing data loss or theft. It ensures that security measures are up-to-date and functioning effectively, identifies vulnerabilities or weaknesses in systems, and helps in implementing necessary safeguards to protect against potential data breaches or loss. Having a structured checklist ensures thorough coverage and adherence to security protocols.
Vibranium Cleaning Tool (VIScan) is a software tool developed by Vibranium that is designed to scan and clean your computer of malware and other security threats. The tool is compatible with Windows XP, 7, 8, 8.1, 10, and 11 operating systems. The tool is designed to be easy to use and can be used by anyone with basic computer skills.
Hem Infotech is a Cybersecurity company helping companies in the implementation of data security, management & backup solutions using the latest tools & techniques.
Team Hem Infotech
Service Assurance Constructs for Achieving Network Transformation - Sunku Ran...

Transformation of network softwarization towards 5G inherently requires satisfying the requirements across a broad scope of verticals while maintaining Quality of Service (QoS) and Quality of Experience (QoE) criteria required to satisfy various network slice constraints. This session with hands-on lab introduces 3 key elements of service assurance – Monitoring, Presentation & provisioning layers and introduction to various cloud-native open source frameworks like Collectd, Influxdb, Grafana, Prometheus, Kafka and Platform for Network Data Analytics (PNDA).
Service Assurance Constructs for Achieving Network Transformation by Sunku Ra...

The document discusses integrating platform telemetry into various monitoring and automation systems. It describes using Collectd to collect metrics from the platform and exposing them through plugins to systems like Prometheus, Kafka, OpenStack Telemetry (Ceilometer), ONAP and PNDA. Integrating the platform telemetry enables closed-loop automation and predictive analytics on the platform resources and services.
ManageEngine Firewall Analyzer training

In this session, you'll learn the basics of setting up Firewall Analyzer by configuring firewall devices and application settings. You'll also see all the different ways to import logs, as well as an overview of various ad hoc reports
Defects mining in exchanges - medvedev, klimakov, yamkovi

This document discusses Exactpro's approach to testing exchange trading systems. It provides an overview of Exactpro as a company focused on functional and non-functional testing of financial market infrastructures. It then discusses Exactpro's testing approach, including creating load profiles, performance testing, resilience testing, automation of resilience testing, and defects mining from test data. Specific techniques covered include monitoring tools deployment, data collection, storage and analysis to identify issues and ensure system resilience.
Criticalcontrolsofcyberdefensefinal 100128032433 Phpapp02

The document outlines 20 critical controls for cyber defense that organizations should implement, including:
1) Implementing boundary defenses like firewalls and proxies to control inbound and outbound network traffic.
2) Ensuring secure configurations for network devices and enforcing standard security profiles for wireless networks and devices.
3) Limiting unauthorized software and hardware on systems by maintaining inventories and using whitelisting tools.
4) Establishing secure baseline configurations for systems through hardening, patching, and change monitoring processes.
Critical Controls Of Cyber Defense

The document outlines 20 critical controls for cyber defense that organizations should implement, including:
1) Implementing boundary defenses like firewalls and proxies to control inbound and outbound network traffic.
2) Ensuring secure configurations on network devices and enforcing wireless security best practices.
3) Limiting ports, protocols, and services to only those that are necessary and scanning for vulnerabilities.
4) Implementing controls like malware prevention, patch management, and hardware/software security standards to protect systems.
Proof of Concept Guide for ManageEngine OpManager

The objective of this OpManager POC is to provide step-by-step instructions about how to set up a stand-alone OpManager environment to be used for demonstrating the functions and features of
the products, using customer data, infrastructure and workloads.
Recommended
QUARTERLY MONTHLY WEEKLY DAILY (IT) AUDIT CHECK LIST.pdf

Data loss or theft can certainly put a damper on your holidays. Losing important information or having personal data compromised can be distressing. It's always wise to take precautions to prevent such issues during your holiday. Please follow useful tips & tricks to secure your devices and network.
Get IT Audit regular checklist & VI Scan complimentary tool. Click on the above image to claim now...
About tools?
Regular IT audits with a defined checklist can be instrumental in preventing data loss or theft. It ensures that security measures are up-to-date and functioning effectively, identifies vulnerabilities or weaknesses in systems, and helps in implementing necessary safeguards to protect against potential data breaches or loss. Having a structured checklist ensures thorough coverage and adherence to security protocols.
Vibranium Cleaning Tool (VIScan) is a software tool developed by Vibranium that is designed to scan and clean your computer of malware and other security threats. The tool is compatible with Windows XP, 7, 8, 8.1, 10, and 11 operating systems. The tool is designed to be easy to use and can be used by anyone with basic computer skills.
Hem Infotech is a Cybersecurity company helping companies in the implementation of data security, management & backup solutions using the latest tools & techniques.
Team Hem Infotech
Service Assurance Constructs for Achieving Network Transformation - Sunku Ran...

Transformation of network softwarization towards 5G inherently requires satisfying the requirements across a broad scope of verticals while maintaining Quality of Service (QoS) and Quality of Experience (QoE) criteria required to satisfy various network slice constraints. This session with hands-on lab introduces 3 key elements of service assurance – Monitoring, Presentation & provisioning layers and introduction to various cloud-native open source frameworks like Collectd, Influxdb, Grafana, Prometheus, Kafka and Platform for Network Data Analytics (PNDA).
Service Assurance Constructs for Achieving Network Transformation by Sunku Ra...

The document discusses integrating platform telemetry into various monitoring and automation systems. It describes using Collectd to collect metrics from the platform and exposing them through plugins to systems like Prometheus, Kafka, OpenStack Telemetry (Ceilometer), ONAP and PNDA. Integrating the platform telemetry enables closed-loop automation and predictive analytics on the platform resources and services.
ManageEngine Firewall Analyzer training

In this session, you'll learn the basics of setting up Firewall Analyzer by configuring firewall devices and application settings. You'll also see all the different ways to import logs, as well as an overview of various ad hoc reports
Defects mining in exchanges - medvedev, klimakov, yamkovi

This document discusses Exactpro's approach to testing exchange trading systems. It provides an overview of Exactpro as a company focused on functional and non-functional testing of financial market infrastructures. It then discusses Exactpro's testing approach, including creating load profiles, performance testing, resilience testing, automation of resilience testing, and defects mining from test data. Specific techniques covered include monitoring tools deployment, data collection, storage and analysis to identify issues and ensure system resilience.
Criticalcontrolsofcyberdefensefinal 100128032433 Phpapp02

The document outlines 20 critical controls for cyber defense that organizations should implement, including:
1) Implementing boundary defenses like firewalls and proxies to control inbound and outbound network traffic.
2) Ensuring secure configurations for network devices and enforcing standard security profiles for wireless networks and devices.
3) Limiting unauthorized software and hardware on systems by maintaining inventories and using whitelisting tools.
4) Establishing secure baseline configurations for systems through hardening, patching, and change monitoring processes.
Critical Controls Of Cyber Defense

The document outlines 20 critical controls for cyber defense that organizations should implement, including:
1) Implementing boundary defenses like firewalls and proxies to control inbound and outbound network traffic.
2) Ensuring secure configurations on network devices and enforcing wireless security best practices.
3) Limiting ports, protocols, and services to only those that are necessary and scanning for vulnerabilities.
4) Implementing controls like malware prevention, patch management, and hardware/software security standards to protect systems.
Proof of Concept Guide for ManageEngine OpManager

The objective of this OpManager POC is to provide step-by-step instructions about how to set up a stand-alone OpManager environment to be used for demonstrating the functions and features of
the products, using customer data, infrastructure and workloads.
Event log analyzer by me 

This document discusses Manage Engine's Eventlog Analyzer product. It provides an overview of the software, including its editions, system requirements, installation process, and key features. The features section describes the various logs and reports that can be monitored and generated, including dashboards, security logs, application logs, compliance reports, user monitoring, and alert capabilities. It also outlines the configuration options for managing hosts, applications, importing/archiving data, scheduling reports, and customizing alerts and filters.
Firewall Analyzer - Middle East Workshop

This document describes ManageEngine Firewall Analyzer, which provides log analytics and configuration management for network security devices. It allows users to view traffic statistics, security statistics, manage devices and rules, and analyze logs. The software monitors firewall activities, detects anomalies in rules, provides compliance reporting, and recommends best practices to improve security posture. It supports over 50 vendors and offers basic and distributed editions for organizations of different sizes.
Check point nerc cip compliance

This letter summarizes security features in Check Point products that help prevent malicious software. The products use specialized, purpose-built operating systems that make integrating third-party antivirus software unfeasible. However, the operating systems lack interfaces that viruses could use to infect the system. Additional security measures include firewall rules that block external connections, hardened appliances with unnecessary ports closed, stateful inspection of all traffic, and logging and auditing of administrator commands.
Novatek- Regulatory Compliant User Requirement 21CFR Part 11 & Annex 11.pdf

Novatek- Regulatory Compliant User Requirement 21CFR Part 11 & Annex 11.pdf
Viavi_TeraVM Core Emulator.pptx

This document provides an overview and instructions for using TeraVM Core software for emulating 5G network cores. The key points are:
- TeraVM Core can fully emulate 2G, 3G, 4G and 5G network nodes and core functions through state-of-the-art control plane emulation and high performance user plane traffic simulation.
- It supports emulation of 4G/5G SA and NSA cores, along with procedures like registration, authentication, handovers and session management.
- The GUI allows configuring the emulated topology and elements, viewing counters and traces, running test cases with different subscriber groups and traffic profiles, and analyzing results.
IRJET- A Study on Penetration Testing using Metasploit Framework

1) The document describes a study on penetration testing using the Metasploit framework. It outlines the various phases of a penetration test - information gathering, scanning, vulnerability discovery, exploitation, and report generation.
2) Specific techniques used in the study include the wafw00f tool to check for firewalls, xhydra for brute force password cracking, Nmap for scanning systems, and Metasploit modules like smb_ms17_010 and psexec for exploiting vulnerabilities.
3) The study was able to gain remote access to a Windows 7 system by exploiting the Eternalblue vulnerability using Metasploit and obtain a meterpreter session, demonstrating a successful penetration test.
Penetration testing using metasploit framework

1) The document describes a study on penetration testing using the Metasploit framework. It outlines the various phases of a penetration test - information gathering, scanning, vulnerability discovery, exploitation, and report generation.
2) Specific techniques used in the study include the WAFW00F tool to check for firewalls, Nmap for scanning systems to identify services and operating systems, and Metasploit modules like smb_ms17_010 and psexec for discovering and exploiting vulnerabilities.
3) The study was able to gain remote access to a Windows 7 system by exploiting the Eternalblue vulnerability using Metasploit and obtain a meterpreter session, demonstrating a successful penetration test.
1_WTTx LTM Main Slide_Huawei_Presentation.pdf

1) The document describes a WTTx Suite that enables end-to-end provisioning and management of networks and customer premise equipment (CPE).
2) It includes a Lightweight Terminal Management (LTM) component that allows for remote management of CPEs, including service provisioning, software upgrades, fault diagnosis, and performance monitoring.
3) The LTM provides insights into network and CPE performance, helps identify issues for network expansion/optimization, and assists with remote troubleshooting and maintenance of CPEs to improve service quality and user experience.
Paper sharing_Edge based intrusion detection for IOT devices

From International Journal of Information Management
Authors:ANAND MUDGERIKAR, PUNEET SHARMA,
ELISA BERTINO (2020)
Agentless System Crawler - InterConnect 2016

IBM speaker guidelines mandate including forward-looking and legal disclaimer slides in presentations. All presentations must include mandatory notices and disclaimers slides before the conclusion. Speakers should refer to additional legal guidance documents and have materials reviewed by legal if concerned. Final presentations are due by February 5th, 2016 and must follow a specific file naming convention. Disclosures for forward-looking statements are available at a specified link. Instructions should be removed before finalizing presentations.
SteelCentral NetSensor 3.0

Riverbed® SteelCentral™ NetSensor provides agentless infrastructure component monitoring and synthetic testing to deliver a comprehensive picture of how infrastructure is affecting network and application performance. http://rvbd.ly/1LNL1S5
ANTIVIRUS

The document summarizes the results of a performance test of 21 antivirus and internet security products on a Windows 8.1 system. The test measured the impact of the security software on common tasks like file copying and downloading. It found that suite products have a higher impact than antivirus-only products due to running more background processes. The test used standard tools to ensure accurate and replicable results. Overall system performance is also affected by factors like hardware specifications, having unnecessary programs running, and failing to keep software up to date.
Monitor and manage everything Cisco using OpManager

Cisco, The leader in enterprise networking and communication technology exposes lot of proprietary and standard protocols/ technologies to monitor and manage its devices. To name few SNMP, CDP, NetFlow, NBAR, CBQoS, IP SLA, & much more… Know how to monitor and manage everything Cisco using ManageEngine OpManager.
Performance dec 2010

The document summarizes the results of a performance test of 21 antivirus programs conducted by AV-Comparatives in November 2010. The test measured the impact of each antivirus program on system performance across various tasks like file copying, application launching, and using a performance testing suite. On-access scanners were found to have some negative impact on performance due to the system resources required to continuously monitor files. Factors other than the antivirus program itself, like outdated hardware or a cluttered hard drive, could also negatively influence performance. The test aimed to provide an indication of each product's performance impact rather than definitive comparisons.
Copy of learn_the_art_of_firewall_security(1)

Firewall Analyzer is a tool that analyzes firewall logs to generate various reports. It discusses how Firewall Analyzer helps meet challenges by tracking URL activities, user bandwidth, securing networks, and performing audits. The document outlines how to install, configure and import logs into Firewall Analyzer. It describes the different types of reports that can be generated for traffic analysis, security analysis, and device management. It also discusses how to set up alarms and notifications. Questions from users are addressed at the end regarding issues like seeing traffic bytes, VPN user details, and required hard drive space.
Introduction to Trusted Computing

The document discusses trusted computing and provides details on its architecture and uses. The trusted computing architecture uses a trusted platform module (TPM) to measure the boot process and software running on a device. It establishes a chain of trust from the hardware to the operating system and applications. While trusted computing aims to increase security and privacy, issues around its impact on privacy have prevented widespread adoption.
ANET SureLog SIEM IntelligentResponse

The correlation systems consist of two parts.
1. Detection
2. Response
The response part is divided in two sub-parts as alarm and taking action.
The detection module, the response module if it detects an event.
• Sending email
• Executing a script
o Visual basic
o Batch file
o Perlscript
o Phytonscript
• Executing java code
• Running application
• Updating dynamic list. For example adding or removing IP address in forbidden IP address list. Dynamically updating this list for those who try more than 3 failed logon accesses in last week, or adding a benign IP or URL that triggered an alarm to a Whitelist so that false positives aren’t generated in the future
Ranjith kumar Nagisetty(AndiordApp and PostSiliconTest Engineer)_Resume

This document contains a resume summary for Ranjith Kumar Nagisetty. It outlines his work experience testing mobile devices and chipsets over 4 years at Wipro and Qualcomm. It details his technical skills which include Java, Android tools, SQL, and scripting languages. It also lists his education as a B.Tech in Electrical and Electronics Engineering from Jawaharlal Nehru Technological University in 2010. Key projects involved system hardware and post-silicon validation testing, thermal and power profiling, and testing various mobile applications on Android platforms.
Fortinet ixia ottawa, june 2013

What's next in next generation firewalls and testing. Fortinet / Ixia presentation, Ottawa, June 20, 2013.
PlantConnect insights

This document describes PlantConnect Insights, a historian and data management solution for industrial facilities. It can acquire data from multiple sources, store it either on-premises or in the cloud, and handle both continuous and batch production processes. Key features include data acquisition, alarm management, custom logic execution, dashboards, reporting, and security controls. The solution was implemented for a dairy plant in Gujarat, India to provide real-time reporting and maintenance alerts from 7 connected devices.
Hem infotech - Ur IT Partner

Hem Infotech was founded in 2002 with Main Focus Area Of computer sales and Services. Working With CoSme's, Corporates Along With State, Central & Semi Govt. Depts. Providing Computer Hardware & Services For More Than 15 Years Now.
We r Distributors, Business Associates & Oem Service Providers For Brands Like Hp, Dell, Acer, Ncomputing, Qnap, Cyberoam, Enjay, Quick Heal, Zicom Etc.
Check Short Video Describes About Us :- https://www.youtube.com/watch?v=eHznDKatp3U
Purav Shah
Team Hem Infotech
Hp z workstations designed for architechts, interiors & construction 2

Accelerate Autodesk workflows with HP Z Workstations :-
HP helps you stay ahead of the curve with professional desktop and mobile workstations designed for large and complex datasets, dispersed teams, and tight deadlines. HP Z Workstations deliver the innovation, high performance, expandability, and extreme reliability you need to deliver your BIM, Digital Prototyping, and 3D CAD projects in less time.
More Related Content
Similar to QUARTERLY MONTHLY WEEKLY DAILY (IT) AUDIT CHECK LIST
Event log analyzer by me 

This document discusses Manage Engine's Eventlog Analyzer product. It provides an overview of the software, including its editions, system requirements, installation process, and key features. The features section describes the various logs and reports that can be monitored and generated, including dashboards, security logs, application logs, compliance reports, user monitoring, and alert capabilities. It also outlines the configuration options for managing hosts, applications, importing/archiving data, scheduling reports, and customizing alerts and filters.
Firewall Analyzer - Middle East Workshop

This document describes ManageEngine Firewall Analyzer, which provides log analytics and configuration management for network security devices. It allows users to view traffic statistics, security statistics, manage devices and rules, and analyze logs. The software monitors firewall activities, detects anomalies in rules, provides compliance reporting, and recommends best practices to improve security posture. It supports over 50 vendors and offers basic and distributed editions for organizations of different sizes.
Check point nerc cip compliance

This letter summarizes security features in Check Point products that help prevent malicious software. The products use specialized, purpose-built operating systems that make integrating third-party antivirus software unfeasible. However, the operating systems lack interfaces that viruses could use to infect the system. Additional security measures include firewall rules that block external connections, hardened appliances with unnecessary ports closed, stateful inspection of all traffic, and logging and auditing of administrator commands.
Novatek- Regulatory Compliant User Requirement 21CFR Part 11 & Annex 11.pdf

Novatek- Regulatory Compliant User Requirement 21CFR Part 11 & Annex 11.pdf
Viavi_TeraVM Core Emulator.pptx

This document provides an overview and instructions for using TeraVM Core software for emulating 5G network cores. The key points are:
- TeraVM Core can fully emulate 2G, 3G, 4G and 5G network nodes and core functions through state-of-the-art control plane emulation and high performance user plane traffic simulation.
- It supports emulation of 4G/5G SA and NSA cores, along with procedures like registration, authentication, handovers and session management.
- The GUI allows configuring the emulated topology and elements, viewing counters and traces, running test cases with different subscriber groups and traffic profiles, and analyzing results.
IRJET- A Study on Penetration Testing using Metasploit Framework

1) The document describes a study on penetration testing using the Metasploit framework. It outlines the various phases of a penetration test - information gathering, scanning, vulnerability discovery, exploitation, and report generation.
2) Specific techniques used in the study include the wafw00f tool to check for firewalls, xhydra for brute force password cracking, Nmap for scanning systems, and Metasploit modules like smb_ms17_010 and psexec for exploiting vulnerabilities.
3) The study was able to gain remote access to a Windows 7 system by exploiting the Eternalblue vulnerability using Metasploit and obtain a meterpreter session, demonstrating a successful penetration test.
Penetration testing using metasploit framework

1) The document describes a study on penetration testing using the Metasploit framework. It outlines the various phases of a penetration test - information gathering, scanning, vulnerability discovery, exploitation, and report generation.
2) Specific techniques used in the study include the WAFW00F tool to check for firewalls, Nmap for scanning systems to identify services and operating systems, and Metasploit modules like smb_ms17_010 and psexec for discovering and exploiting vulnerabilities.
3) The study was able to gain remote access to a Windows 7 system by exploiting the Eternalblue vulnerability using Metasploit and obtain a meterpreter session, demonstrating a successful penetration test.
1_WTTx LTM Main Slide_Huawei_Presentation.pdf

1) The document describes a WTTx Suite that enables end-to-end provisioning and management of networks and customer premise equipment (CPE).
2) It includes a Lightweight Terminal Management (LTM) component that allows for remote management of CPEs, including service provisioning, software upgrades, fault diagnosis, and performance monitoring.
3) The LTM provides insights into network and CPE performance, helps identify issues for network expansion/optimization, and assists with remote troubleshooting and maintenance of CPEs to improve service quality and user experience.
Paper sharing_Edge based intrusion detection for IOT devices

From International Journal of Information Management
Authors:ANAND MUDGERIKAR, PUNEET SHARMA,
ELISA BERTINO (2020)
Agentless System Crawler - InterConnect 2016

IBM speaker guidelines mandate including forward-looking and legal disclaimer slides in presentations. All presentations must include mandatory notices and disclaimers slides before the conclusion. Speakers should refer to additional legal guidance documents and have materials reviewed by legal if concerned. Final presentations are due by February 5th, 2016 and must follow a specific file naming convention. Disclosures for forward-looking statements are available at a specified link. Instructions should be removed before finalizing presentations.
SteelCentral NetSensor 3.0

Riverbed® SteelCentral™ NetSensor provides agentless infrastructure component monitoring and synthetic testing to deliver a comprehensive picture of how infrastructure is affecting network and application performance. http://rvbd.ly/1LNL1S5
ANTIVIRUS

The document summarizes the results of a performance test of 21 antivirus and internet security products on a Windows 8.1 system. The test measured the impact of the security software on common tasks like file copying and downloading. It found that suite products have a higher impact than antivirus-only products due to running more background processes. The test used standard tools to ensure accurate and replicable results. Overall system performance is also affected by factors like hardware specifications, having unnecessary programs running, and failing to keep software up to date.
Monitor and manage everything Cisco using OpManager

Cisco, The leader in enterprise networking and communication technology exposes lot of proprietary and standard protocols/ technologies to monitor and manage its devices. To name few SNMP, CDP, NetFlow, NBAR, CBQoS, IP SLA, & much more… Know how to monitor and manage everything Cisco using ManageEngine OpManager.
Performance dec 2010

The document summarizes the results of a performance test of 21 antivirus programs conducted by AV-Comparatives in November 2010. The test measured the impact of each antivirus program on system performance across various tasks like file copying, application launching, and using a performance testing suite. On-access scanners were found to have some negative impact on performance due to the system resources required to continuously monitor files. Factors other than the antivirus program itself, like outdated hardware or a cluttered hard drive, could also negatively influence performance. The test aimed to provide an indication of each product's performance impact rather than definitive comparisons.
Copy of learn_the_art_of_firewall_security(1)

Firewall Analyzer is a tool that analyzes firewall logs to generate various reports. It discusses how Firewall Analyzer helps meet challenges by tracking URL activities, user bandwidth, securing networks, and performing audits. The document outlines how to install, configure and import logs into Firewall Analyzer. It describes the different types of reports that can be generated for traffic analysis, security analysis, and device management. It also discusses how to set up alarms and notifications. Questions from users are addressed at the end regarding issues like seeing traffic bytes, VPN user details, and required hard drive space.
Introduction to Trusted Computing

The document discusses trusted computing and provides details on its architecture and uses. The trusted computing architecture uses a trusted platform module (TPM) to measure the boot process and software running on a device. It establishes a chain of trust from the hardware to the operating system and applications. While trusted computing aims to increase security and privacy, issues around its impact on privacy have prevented widespread adoption.
ANET SureLog SIEM IntelligentResponse

The correlation systems consist of two parts.
1. Detection
2. Response
The response part is divided in two sub-parts as alarm and taking action.
The detection module, the response module if it detects an event.
• Sending email
• Executing a script
o Visual basic
o Batch file
o Perlscript
o Phytonscript
• Executing java code
• Running application
• Updating dynamic list. For example adding or removing IP address in forbidden IP address list. Dynamically updating this list for those who try more than 3 failed logon accesses in last week, or adding a benign IP or URL that triggered an alarm to a Whitelist so that false positives aren’t generated in the future
Ranjith kumar Nagisetty(AndiordApp and PostSiliconTest Engineer)_Resume

This document contains a resume summary for Ranjith Kumar Nagisetty. It outlines his work experience testing mobile devices and chipsets over 4 years at Wipro and Qualcomm. It details his technical skills which include Java, Android tools, SQL, and scripting languages. It also lists his education as a B.Tech in Electrical and Electronics Engineering from Jawaharlal Nehru Technological University in 2010. Key projects involved system hardware and post-silicon validation testing, thermal and power profiling, and testing various mobile applications on Android platforms.
Fortinet ixia ottawa, june 2013

What's next in next generation firewalls and testing. Fortinet / Ixia presentation, Ottawa, June 20, 2013.
PlantConnect insights

This document describes PlantConnect Insights, a historian and data management solution for industrial facilities. It can acquire data from multiple sources, store it either on-premises or in the cloud, and handle both continuous and batch production processes. Key features include data acquisition, alarm management, custom logic execution, dashboards, reporting, and security controls. The solution was implemented for a dairy plant in Gujarat, India to provide real-time reporting and maintenance alerts from 7 connected devices.
Similar to QUARTERLY MONTHLY WEEKLY DAILY (IT) AUDIT CHECK LIST (20)
Novatek- Regulatory Compliant User Requirement 21CFR Part 11 & Annex 11.pdf

Novatek- Regulatory Compliant User Requirement 21CFR Part 11 & Annex 11.pdf
IRJET- A Study on Penetration Testing using Metasploit Framework

IRJET- A Study on Penetration Testing using Metasploit Framework
Paper sharing_Edge based intrusion detection for IOT devices

Paper sharing_Edge based intrusion detection for IOT devices
Monitor and manage everything Cisco using OpManager

Monitor and manage everything Cisco using OpManager
Ranjith kumar Nagisetty(AndiordApp and PostSiliconTest Engineer)_Resume

Ranjith kumar Nagisetty(AndiordApp and PostSiliconTest Engineer)_Resume
More from Hem Infotech
Hem infotech - Ur IT Partner

Hem Infotech was founded in 2002 with Main Focus Area Of computer sales and Services. Working With CoSme's, Corporates Along With State, Central & Semi Govt. Depts. Providing Computer Hardware & Services For More Than 15 Years Now.
We r Distributors, Business Associates & Oem Service Providers For Brands Like Hp, Dell, Acer, Ncomputing, Qnap, Cyberoam, Enjay, Quick Heal, Zicom Etc.
Check Short Video Describes About Us :- https://www.youtube.com/watch?v=eHznDKatp3U
Purav Shah
Team Hem Infotech
Hp z workstations designed for architechts, interiors & construction 2

Accelerate Autodesk workflows with HP Z Workstations :-
HP helps you stay ahead of the curve with professional desktop and mobile workstations designed for large and complex datasets, dispersed teams, and tight deadlines. HP Z Workstations deliver the innovation, high performance, expandability, and extreme reliability you need to deliver your BIM, Digital Prototyping, and 3D CAD projects in less time.
Hp z workstations designed for architechts, interiors & construction 1

Accelerate Autodesk workflows with HP Z Workstations :-
HP helps you stay ahead of the curve with professional desktop and mobile workstations designed for large and complex datasets, dispersed teams, and tight deadlines. HP Z Workstations deliver the innovation, high performance, expandability, and extreme reliability you need to deliver your BIM, Digital Prototyping, and 3D CAD projects in less time.
AEC Presentation

This document discusses Hem Infotech, a leading IT consulting firm in Ahmedabad, India. Purav Shah is the founder of Hem Infotech, which has a presence across 22 Indian states. The company distributes products from HP, Dell, and other brands. Hem Infotech aims to add at least 50 new customer accounts in 2019. The document also discusses HP workstation solutions for architecture, engineering, construction, and other industries.
Ops range brochure

HP offers a range of PageWide printers and MFPs that provide fast, high-quality color printing using new PageWide printing technology. Key features include print speeds up to 70 ppm, low cost per page compared to lasers, energy efficiency using up to 71% less energy than lasers, and security features to protect devices, data, and documents. HP also offers managed color printers and MFPs targeted at high-volume printing environments with additional features such as higher duty cycles and more paper handling options.
Hem Infotech Company profile

Hem Infotech is an IT consultancy established in 2002 in Ahmedabad, Gujarat, India. It has over 20 experienced IT professionals and focuses on industries like finance, hospitality, education, and government. It provides services including AMC, thin clients, CRM, public WiFi, and IT solution integration. Hem Infotech aims to improve its expertise in core domains and new technologies to enhance its service offerings and support customers' IT infrastructure needs.
BNI Connect Made Easy

This document discusses expanding one's business reach through BNI-Connect, a global business networking organization. It provides key statistics about BNI-Connect's global and India-specific membership and referrals. It then offers tips on who to connect with to achieve business goals, such as friends, occupation networks, and social groups. It emphasizes the importance of completing one's online profile and attending BNI-Connect training to learn more details and get more referrals and business revenue.
Hem infotech company profile

Hem Infotech was founded in 2002 with Main Focus Area Of computer sales and maintenance.
Currently We operate under Five verticals namely Computer Maintenance - AMC, Thin Client - World's Smallest & Lowest Energy Computing, Telephony - Crm/Erp Integration, It Consultancy - AUDIT & SOLUTION SUPPORT & Public Wifi.
We r Business Associates & Oem Service Partner For Brands Like Hp, Ncomputing, Qnap, Sophos, Enjay, Purple Etc.
Currently Maintaining 20000+ Hardwares With 1000+ Customers.
18+ Well Experience, Certified Technical Team Focusing Govt., Banking, Education, Finance, Hospitality Etc..
We r Gujarat's One Of Very Few Companies Using Crm Based Systematic Mechanism For Quick & Accurate Support.
Hp printer September range brochure

This document provides information about HP inkjet printers and all-in-one devices. It includes:
- Details on several DeskJet and DeskJet Ink Advantage models ranging from basic print and copy functionality to more advanced photo printing and wireless connectivity. Print speeds, cartridge yields and prices are listed for each.
- Information on the HP DeskJet GT series which uses high-capacity ink tanks instead of cartridges, providing lower cost per page printing. Models are available with various page yields and print speeds listed.
- Mentions of features like mobile printing apps, auto-duplexing, touchscreens and bulk ink bottle inclusion on certain models. Low cost replacement cartridges are highlighted across
Wise paa s-sales_kit_and_roadmap_2017h1 (003)

This document describes WISE-PaaS, an IoT software platform and marketplace from Embedded IoT Group. It provides remote monitoring and management of connected devices, integration of security and recovery solutions, and scalable support for up to 1000 device connections. The platform offers a marketplace for third-party software and services, as well as tools for software updating, upgrading, and scheduling via REST APIs. It also describes the WISE-PaaS alliance program and rewards structure called WISE-Point that aims to create a win-win partnership for IoT solution development and business growth.
HP Printers Best Offers - April

This document provides information about several HP printer models, including the DeskJet GT 5820 and 5810 inkjet all-in-one printers. It lists the key features of each printer such as print speed, resolution, paper handling capabilities, mobile printing support, and supply costs. The document also provides pricing and warranty information for HP's DeskJet inkjet and OfficeJet Pro business inkjet printer lines.
Exchange offer process -HP Printer

This document outlines HP's printer buyback program in India which offers customers discounts on select new HP ink advantage printers when exchanging an old HP printer. The program allows customers to register online to receive a voucher with their discount amount, then purchase an eligible new printer from a participating retailer while submitting their voucher and old printer. Retailers can then claim back the discount amount by submitting the customer's voucher information online along with proof of the new printer purchase. HP will arrange to pick up the old printer for recycling and reimburse the retailer within 10 days once the claim is approved and old printer received. The program runs from April 30 to May 30, 2017.
HP Printers - March Brochure

This document provides specifications for several HP printer models, including the DeskJet GT 5820 and 5810 ink tank printers, and several DeskJet Ink Advantage all-in-one printer models. For each printer, the summary lists key features such as print speed, resolution, paper handling capabilities, wireless functions, supplies information like cartridge costs and page yields, and warranty information. It recommends printers for users with low or high printing requirements based on features and supplies costs.
Hem Infotech - Work Profile

The document discusses managed IT services and shared computing. It provides an overview of managed IT services, listing benefits such as preventative maintenance, remote monitoring and management, unlimited help desk support, security, backup and disaster recovery. It also discusses how shared computing can save organizations over 40% on hardware, 90% on electricity, 70% on maintenance, and over 40% on licensing and antivirus through virtualizing workloads on a single high-powered server rather than multiple individual computers. The document provides an example of a Dell server supporting 31 simultaneous users running various applications with only 63% CPU usage.
Hp Printer Brochure For Customer Reference

Dear Customer,
Find Detailed Brochure Helps You In Buying Decision Of Hp Ink tank, Officejet, Laserjet Printer, Scanner & Consumable. It May Available Online @ Best Offer But Make Check Warranty Support Before Click Order.
Our Team Will Help You In Buying Process. Just Give Us Model Number. Our Prices Will Be +5% Then Any Online Best Offer Due To Local Taxation But Get Peace Of Mind With Direct Company Warranty.
Thanks Team Hp Ahmedabad For Sharing Informative Document For Customer Help
Technically Yours
Purav Shah
Hem Infotech
9327000722
More from Hem Infotech (16)
Hp z workstations designed for architechts, interiors & construction 2

Hp z workstations designed for architechts, interiors & construction 2
Hp z workstations designed for architechts, interiors & construction 1

Hp z workstations designed for architechts, interiors & construction 1
Recently uploaded
20240609 QFM020 Irresponsible AI Reading List May 2024

Everything I found interesting about the irresponsible use of machine intelligence in May 2024
Observability Concepts EVERY Developer Should Know -- DeveloperWeek Europe.pdf

Monitoring and observability aren’t traditionally found in software curriculums and many of us cobble this knowledge together from whatever vendor or ecosystem we were first introduced to and whatever is a part of your current company’s observability stack.
While the dev and ops silo continues to crumble….many organizations still relegate monitoring & observability as the purview of ops, infra and SRE teams. This is a mistake - achieving a highly observable system requires collaboration up and down the stack.
I, a former op, would like to extend an invitation to all application developers to join the observability party will share these foundational concepts to build on:
National Security Agency - NSA mobile device best practices

Threats to mobile devices are more prevalent and increasing in scope and complexity. Users of mobile devices desire to take full advantage of the features
available on those devices, but many of the features provide convenience and capability but sacrifice security. This best practices guide outlines steps the users can take to better protect personal devices and information.
GraphSummit Singapore | The Art of the Possible with Graph - Q2 2024

Neha Bajwa, Vice President of Product Marketing, Neo4j
Join us as we explore breakthrough innovations enabled by interconnected data and AI. Discover firsthand how organizations use relationships in data to uncover contextual insights and solve our most pressing challenges – from optimizing supply chains, detecting fraud, and improving customer experiences to accelerating drug discoveries.
Pushing the limits of ePRTC: 100ns holdover for 100 days

At WSTS 2024, Alon Stern explored the topic of parametric holdover and explained how recent research findings can be implemented in real-world PNT networks to achieve 100 nanoseconds of accuracy for up to 100 days.
20 Comprehensive Checklist of Designing and Developing a Website

Dive into the world of Website Designing and Developing with Pixlogix! Looking to create a stunning online presence? Look no further! Our comprehensive checklist covers everything you need to know to craft a website that stands out. From user-friendly design to seamless functionality, we've got you covered. Don't miss out on this invaluable resource! Check out our checklist now at Pixlogix and start your journey towards a captivating online presence today.
Removing Uninteresting Bytes in Software Fuzzing

Imagine a world where software fuzzing, the process of mutating bytes in test seeds to uncover hidden and erroneous program behaviors, becomes faster and more effective. A lot depends on the initial seeds, which can significantly dictate the trajectory of a fuzzing campaign, particularly in terms of how long it takes to uncover interesting behaviour in your code. We introduce DIAR, a technique designed to speedup fuzzing campaigns by pinpointing and eliminating those uninteresting bytes in the seeds. Picture this: instead of wasting valuable resources on meaningless mutations in large, bloated seeds, DIAR removes the unnecessary bytes, streamlining the entire process.
In this work, we equipped AFL, a popular fuzzer, with DIAR and examined two critical Linux libraries -- Libxml's xmllint, a tool for parsing xml documents, and Binutil's readelf, an essential debugging and security analysis command-line tool used to display detailed information about ELF (Executable and Linkable Format). Our preliminary results show that AFL+DIAR does not only discover new paths more quickly but also achieves higher coverage overall. This work thus showcases how starting with lean and optimized seeds can lead to faster, more comprehensive fuzzing campaigns -- and DIAR helps you find such seeds.
- These are slides of the talk given at IEEE International Conference on Software Testing Verification and Validation Workshop, ICSTW 2022.
20240605 QFM017 Machine Intelligence Reading List May 2024

Everything I found interesting about machines behaving intelligently during May 2024
Encryption in Microsoft 365 - ExpertsLive Netherlands 2024

In this session I delve into the encryption technology used in Microsoft 365 and Microsoft Purview. Including the concepts of Customer Key and Double Key Encryption.
Full-RAG: A modern architecture for hyper-personalization

Mike Del Balso, CEO & Co-Founder at Tecton, presents "Full RAG," a novel approach to AI recommendation systems, aiming to push beyond the limitations of traditional models through a deep integration of contextual insights and real-time data, leveraging the Retrieval-Augmented Generation architecture. This talk will outline Full RAG's potential to significantly enhance personalization, address engineering challenges such as data management and model training, and introduce data enrichment with reranking as a key solution. Attendees will gain crucial insights into the importance of hyperpersonalization in AI, the capabilities of Full RAG for advanced personalization, and strategies for managing complex data integrations for deploying cutting-edge AI solutions.
Mind map of terminologies used in context of Generative AI

Mind map of common terms used in context of Generative AI.
Communications Mining Series - Zero to Hero - Session 1

This session provides introduction to UiPath Communication Mining, importance and platform overview. You will acquire a good understand of the phases in Communication Mining as we go over the platform with you. Topics covered:
• Communication Mining Overview
• Why is it important?
• How can it help today’s business and the benefits
• Phases in Communication Mining
• Demo on Platform overview
• Q/A
Generative AI Deep Dive: Advancing from Proof of Concept to Production

Join Maher Hanafi, VP of Engineering at Betterworks, in this new session where he'll share a practical framework to transform Gen AI prototypes into impactful products! He'll delve into the complexities of data collection and management, model selection and optimization, and ensuring security, scalability, and responsible use.
Building RAG with self-deployed Milvus vector database and Snowpark Container...

This talk will give hands-on advice on building RAG applications with an open-source Milvus database deployed as a docker container. We will also introduce the integration of Milvus with Snowpark Container Services.
Artificial Intelligence for XMLDevelopment

In the rapidly evolving landscape of technologies, XML continues to play a vital role in structuring, storing, and transporting data across diverse systems. The recent advancements in artificial intelligence (AI) present new methodologies for enhancing XML development workflows, introducing efficiency, automation, and intelligent capabilities. This presentation will outline the scope and perspective of utilizing AI in XML development. The potential benefits and the possible pitfalls will be highlighted, providing a balanced view of the subject.
We will explore the capabilities of AI in understanding XML markup languages and autonomously creating structured XML content. Additionally, we will examine the capacity of AI to enrich plain text with appropriate XML markup. Practical examples and methodological guidelines will be provided to elucidate how AI can be effectively prompted to interpret and generate accurate XML markup.
Further emphasis will be placed on the role of AI in developing XSLT, or schemas such as XSD and Schematron. We will address the techniques and strategies adopted to create prompts for generating code, explaining code, or refactoring the code, and the results achieved.
The discussion will extend to how AI can be used to transform XML content. In particular, the focus will be on the use of AI XPath extension functions in XSLT, Schematron, Schematron Quick Fixes, or for XML content refactoring.
The presentation aims to deliver a comprehensive overview of AI usage in XML development, providing attendees with the necessary knowledge to make informed decisions. Whether you’re at the early stages of adopting AI or considering integrating it in advanced XML development, this presentation will cover all levels of expertise.
By highlighting the potential advantages and challenges of integrating AI with XML development tools and languages, the presentation seeks to inspire thoughtful conversation around the future of XML development. We’ll not only delve into the technical aspects of AI-powered XML development but also discuss practical implications and possible future directions.
Introducing Milvus Lite: Easy-to-Install, Easy-to-Use vector database for you...

Join us to introduce Milvus Lite, a vector database that can run on notebooks and laptops, share the same API with Milvus, and integrate with every popular GenAI framework. This webinar is perfect for developers seeking easy-to-use, well-integrated vector databases for their GenAI apps.
Goodbye Windows 11: Make Way for Nitrux Linux 3.5.0!

As the digital landscape continually evolves, operating systems play a critical role in shaping user experiences and productivity. The launch of Nitrux Linux 3.5.0 marks a significant milestone, offering a robust alternative to traditional systems such as Windows 11. This article delves into the essence of Nitrux Linux 3.5.0, exploring its unique features, advantages, and how it stands as a compelling choice for both casual users and tech enthusiasts.
Climate Impact of Software Testing at Nordic Testing Days

My slides at Nordic Testing Days 6.6.2024
Climate impact / sustainability of software testing discussed on the talk. ICT and testing must carry their part of global responsibility to help with the climat warming. We can minimize the carbon footprint but we can also have a carbon handprint, a positive impact on the climate. Quality characteristics can be added with sustainability, and then measured continuously. Test environments can be used less, and in smaller scale and on demand. Test techniques can be used in optimizing or minimizing number of tests. Test automation can be used to speed up testing.
Recently uploaded (20)
20240609 QFM020 Irresponsible AI Reading List May 2024

20240609 QFM020 Irresponsible AI Reading List May 2024
Observability Concepts EVERY Developer Should Know -- DeveloperWeek Europe.pdf

Observability Concepts EVERY Developer Should Know -- DeveloperWeek Europe.pdf
National Security Agency - NSA mobile device best practices

National Security Agency - NSA mobile device best practices
GraphSummit Singapore | The Art of the Possible with Graph - Q2 2024

GraphSummit Singapore | The Art of the Possible with Graph - Q2 2024
Pushing the limits of ePRTC: 100ns holdover for 100 days

Pushing the limits of ePRTC: 100ns holdover for 100 days
20 Comprehensive Checklist of Designing and Developing a Website

20 Comprehensive Checklist of Designing and Developing a Website
20240605 QFM017 Machine Intelligence Reading List May 2024

20240605 QFM017 Machine Intelligence Reading List May 2024
Encryption in Microsoft 365 - ExpertsLive Netherlands 2024

Encryption in Microsoft 365 - ExpertsLive Netherlands 2024
Full-RAG: A modern architecture for hyper-personalization

Full-RAG: A modern architecture for hyper-personalization
Mind map of terminologies used in context of Generative AI

Mind map of terminologies used in context of Generative AI
Communications Mining Series - Zero to Hero - Session 1

Communications Mining Series - Zero to Hero - Session 1
Generative AI Deep Dive: Advancing from Proof of Concept to Production

Generative AI Deep Dive: Advancing from Proof of Concept to Production
Building RAG with self-deployed Milvus vector database and Snowpark Container...

Building RAG with self-deployed Milvus vector database and Snowpark Container...
Introducing Milvus Lite: Easy-to-Install, Easy-to-Use vector database for you...

Introducing Milvus Lite: Easy-to-Install, Easy-to-Use vector database for you...
Goodbye Windows 11: Make Way for Nitrux Linux 3.5.0!

Goodbye Windows 11: Make Way for Nitrux Linux 3.5.0!
Climate Impact of Software Testing at Nordic Testing Days

Climate Impact of Software Testing at Nordic Testing Days
QUARTERLY MONTHLY WEEKLY DAILY (IT) AUDIT CHECK LIST
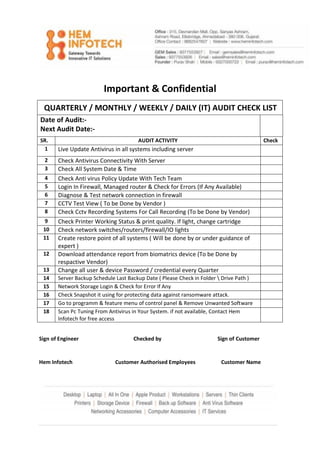
- 1. Important & Confidential QUARTERLY / MONTHLY / WEEKLY / DAILY (IT) AUDIT CHECK LIST Date of Audit:- Next Audit Date:- SR. AUDIT ACTIVITY Check 1 Live Update Antivirus in all systems including server 2 Check Antivirus Connectivity With Server 3 Check All System Date & Time 4 Check Anti virus Policy Update With Tech Team 5 Login In Firewall, Managed router & Check for Errors (If Any Available) 6 Diagnose & Test network connection in firewall 7 CCTV Test View ( To be Done by Vendor ) 8 Check Cctv Recording Systems For Call Recording (To be Done by Vendor) 9 Check Printer Working Status & print quality. If light, change cartridge 10 Check network switches/routers/firewall/IO lights 11 Create restore point of all systems ( Will be done by or under guidance of expert ) 12 Download attendance report from biomatrics device (To be Done by respactive Vendor) 13 Change all user & device Password / credential every Quarter 14 Server Backup Schedule Last Backup Date ( Please Check in Folder Drive Path ) 15 Network Storage Login & Check for Error If Any 16 Check Snapshot it using for protecting data against ransomware attack. 17 Go to programm & feature menu of control panel & Remove Unwanted Software 18 Scan Pc Tuning From Antivirus in Your System. if not available, Contact Hem Infotech for free access Sign of Engineer Checked by Sign of Customer Hem Infotech Customer Authorised Employees Customer Name
