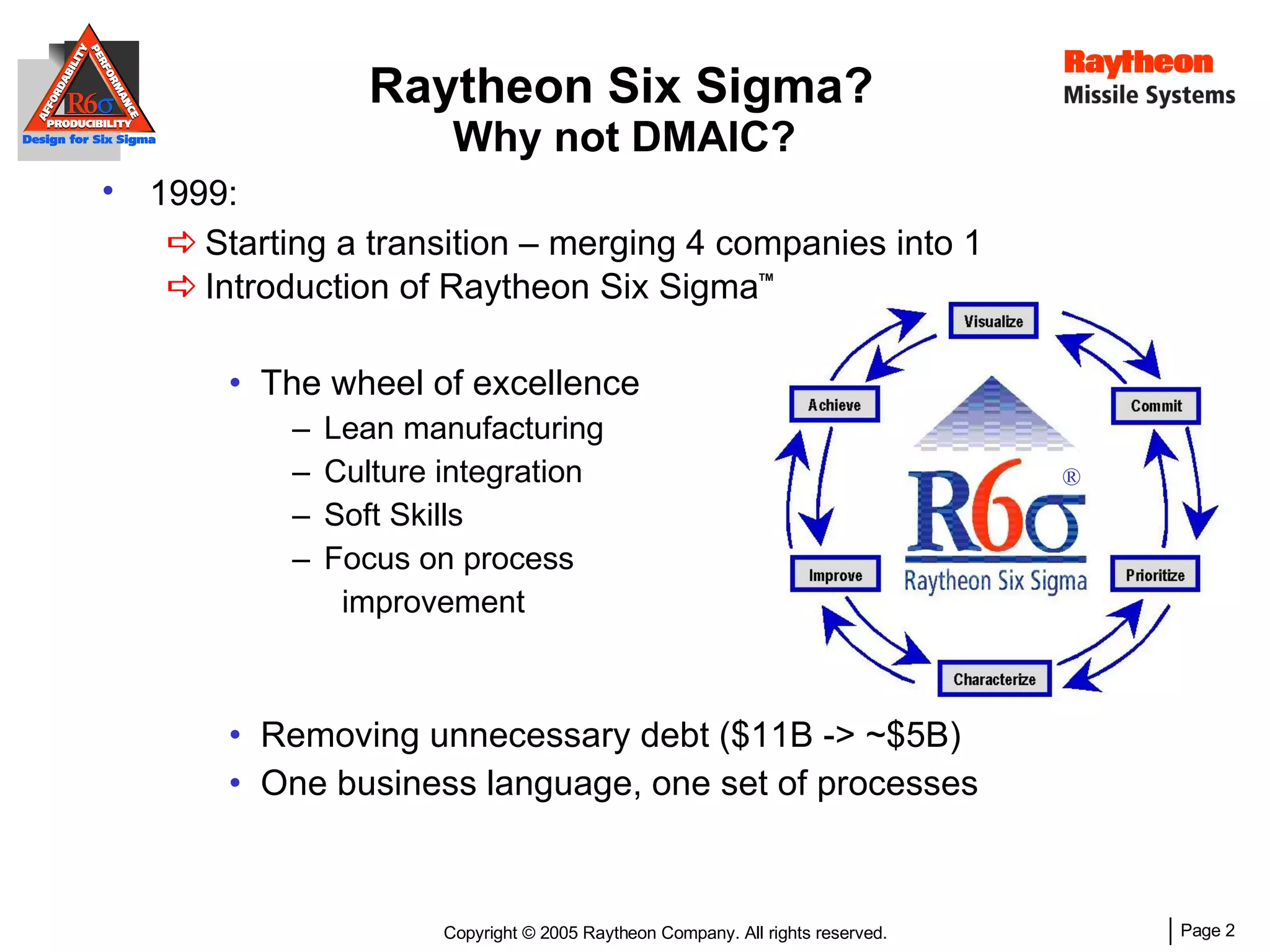
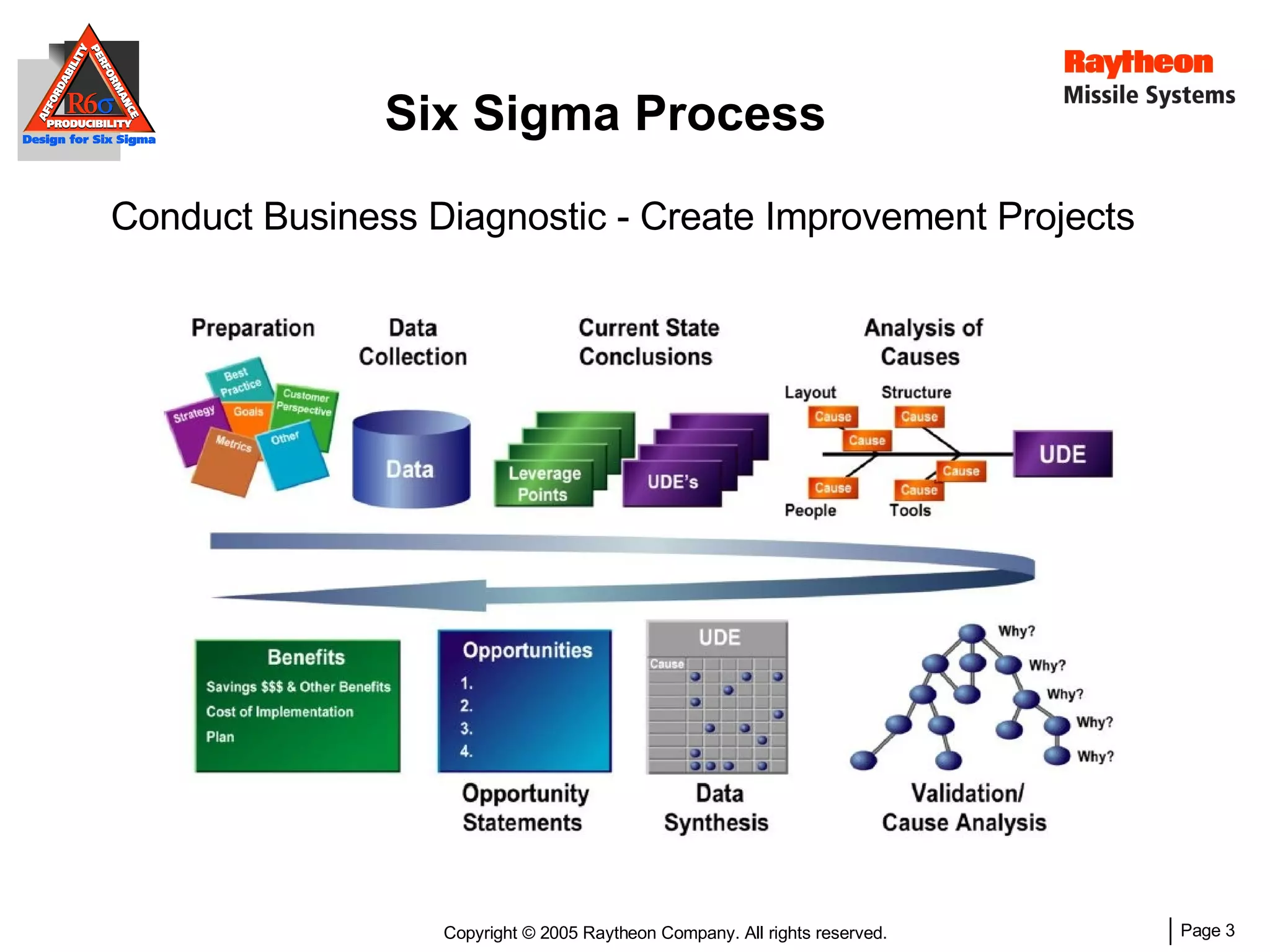
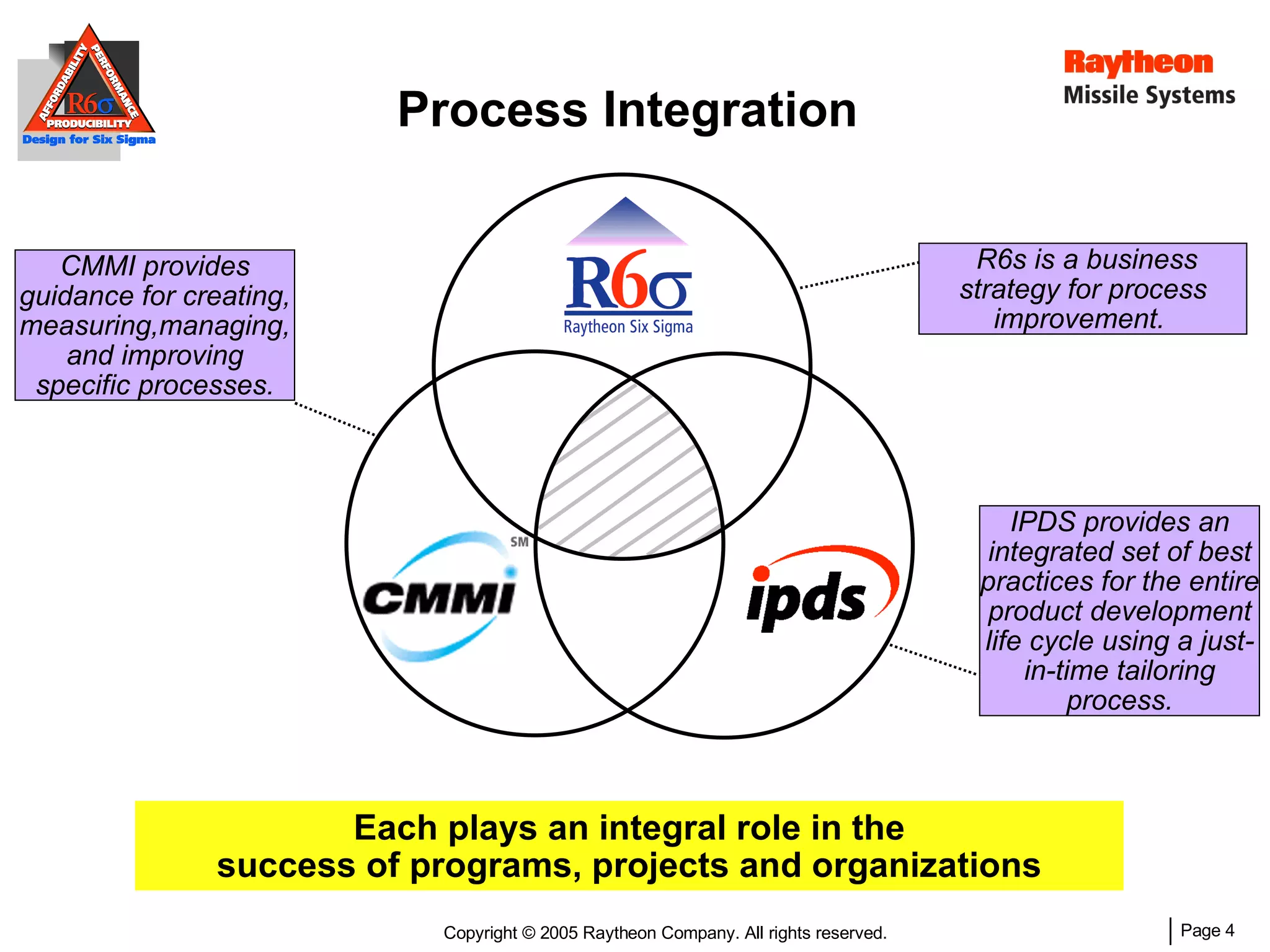
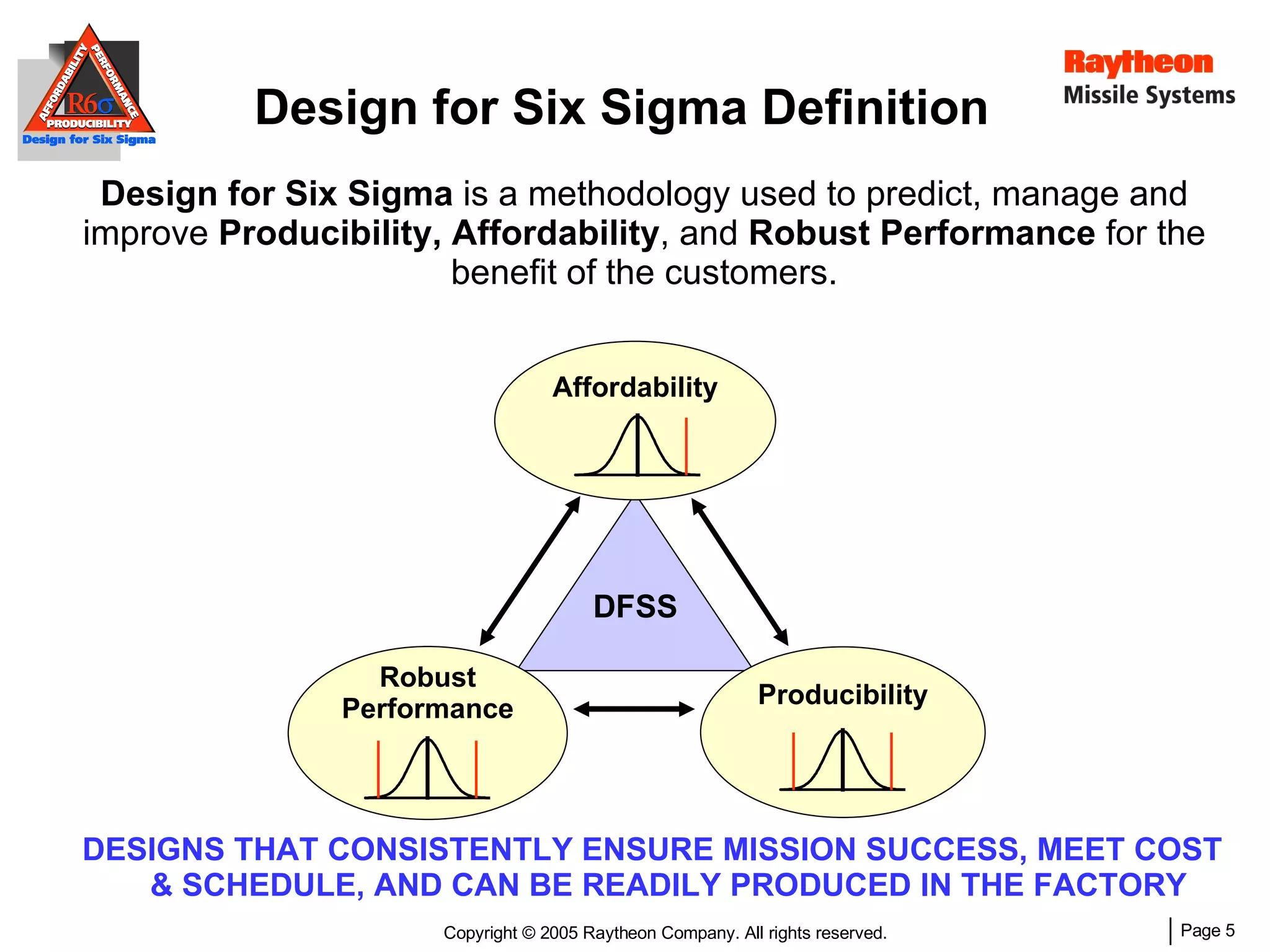
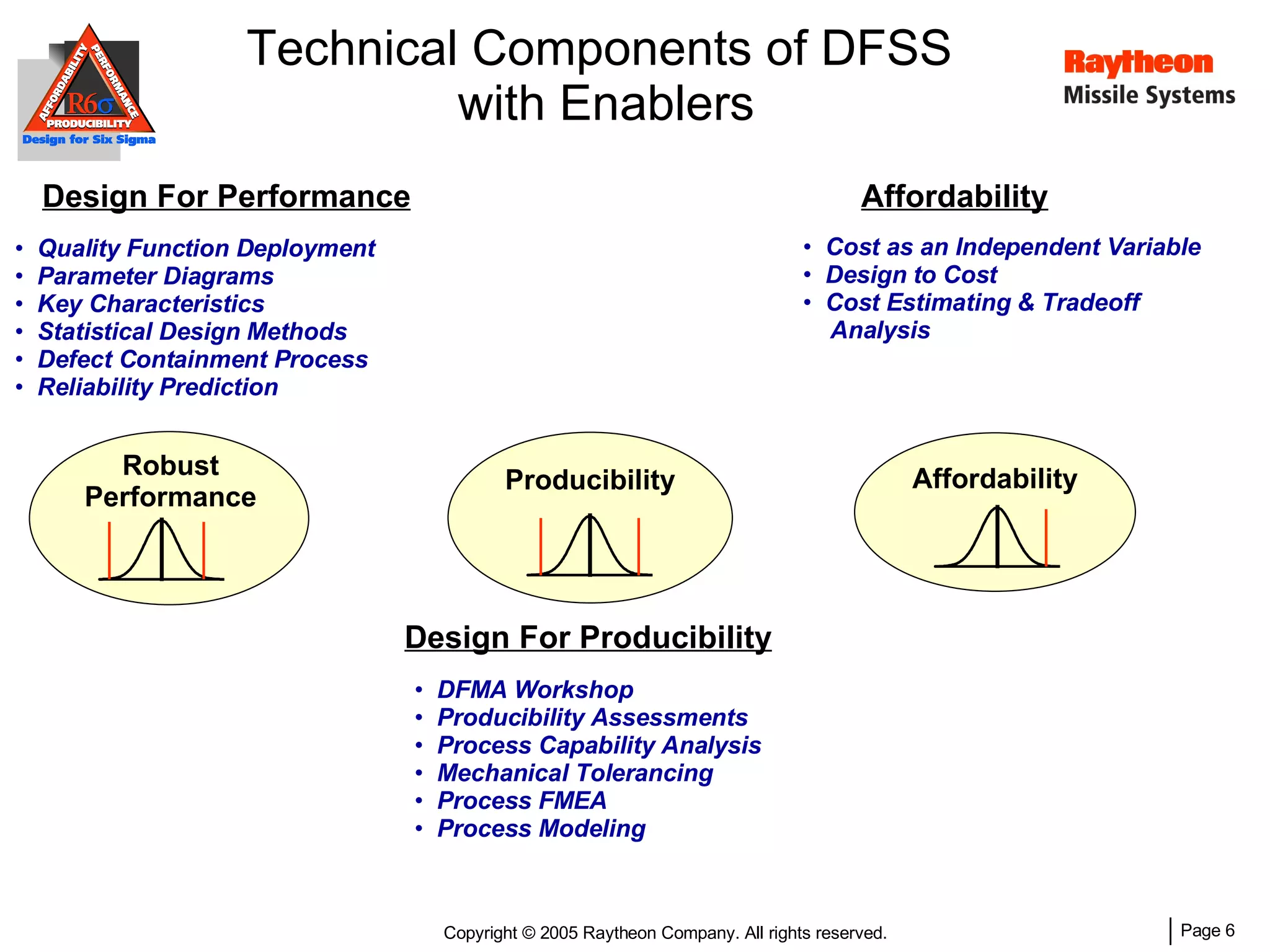
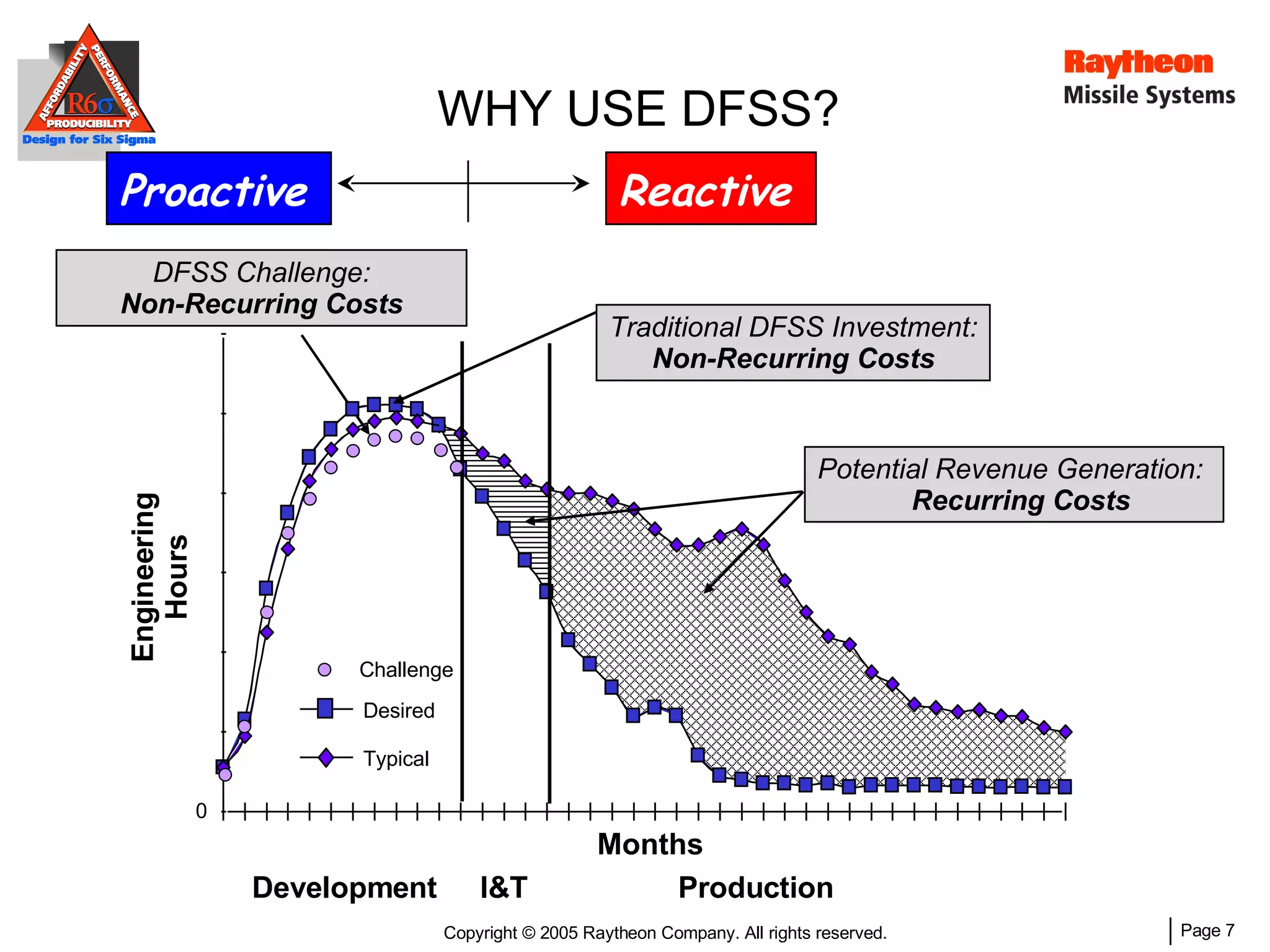
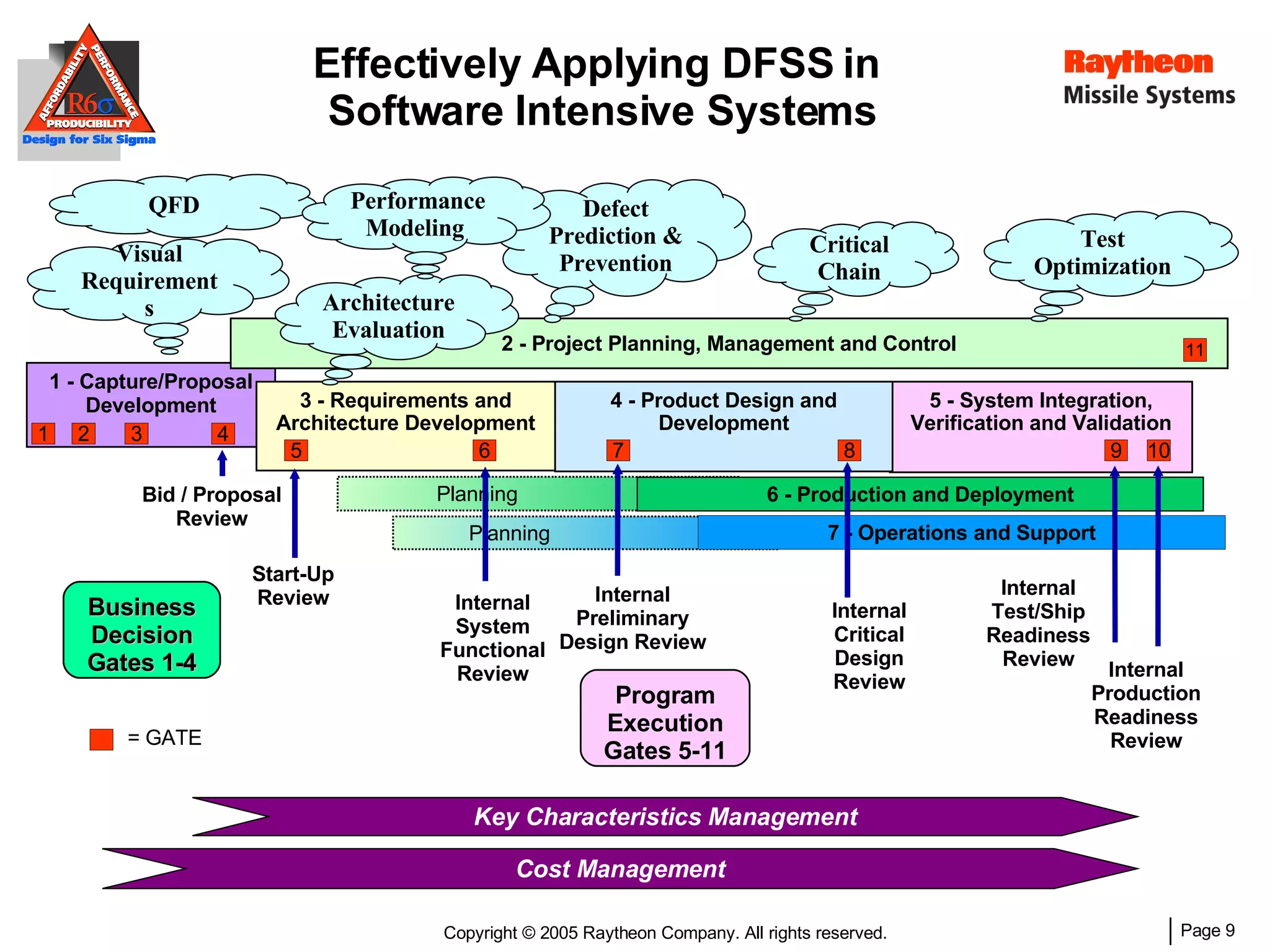
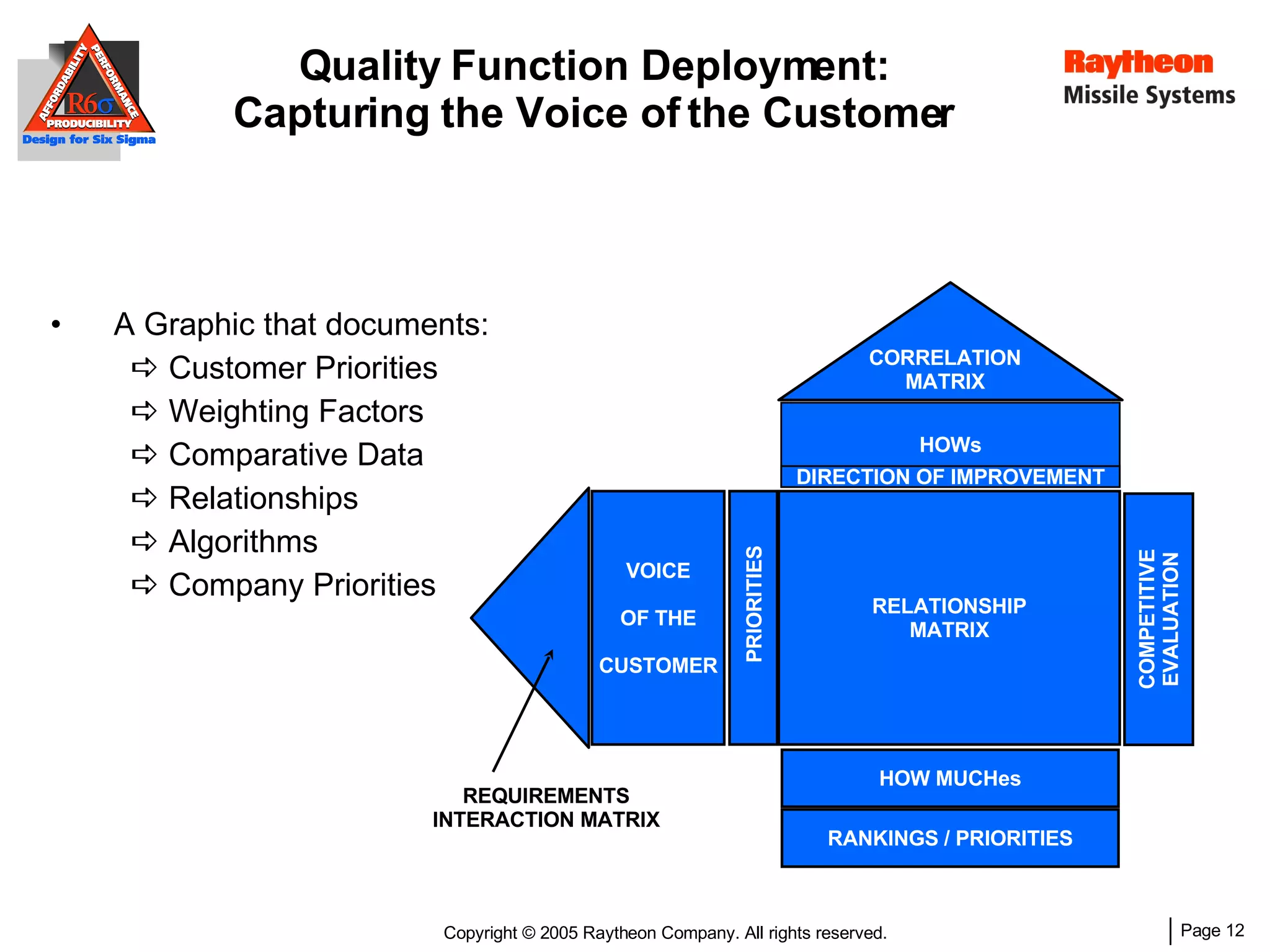
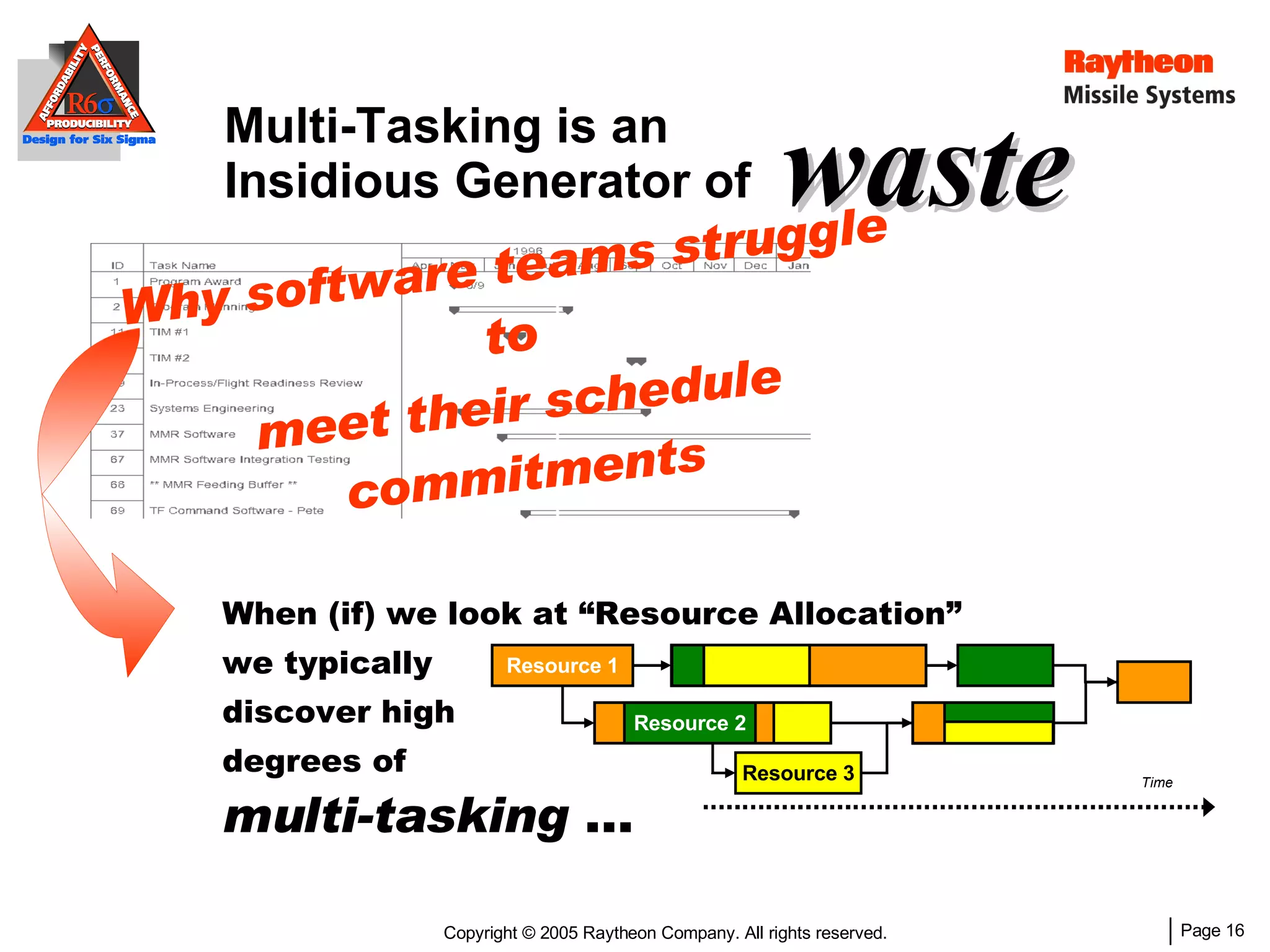
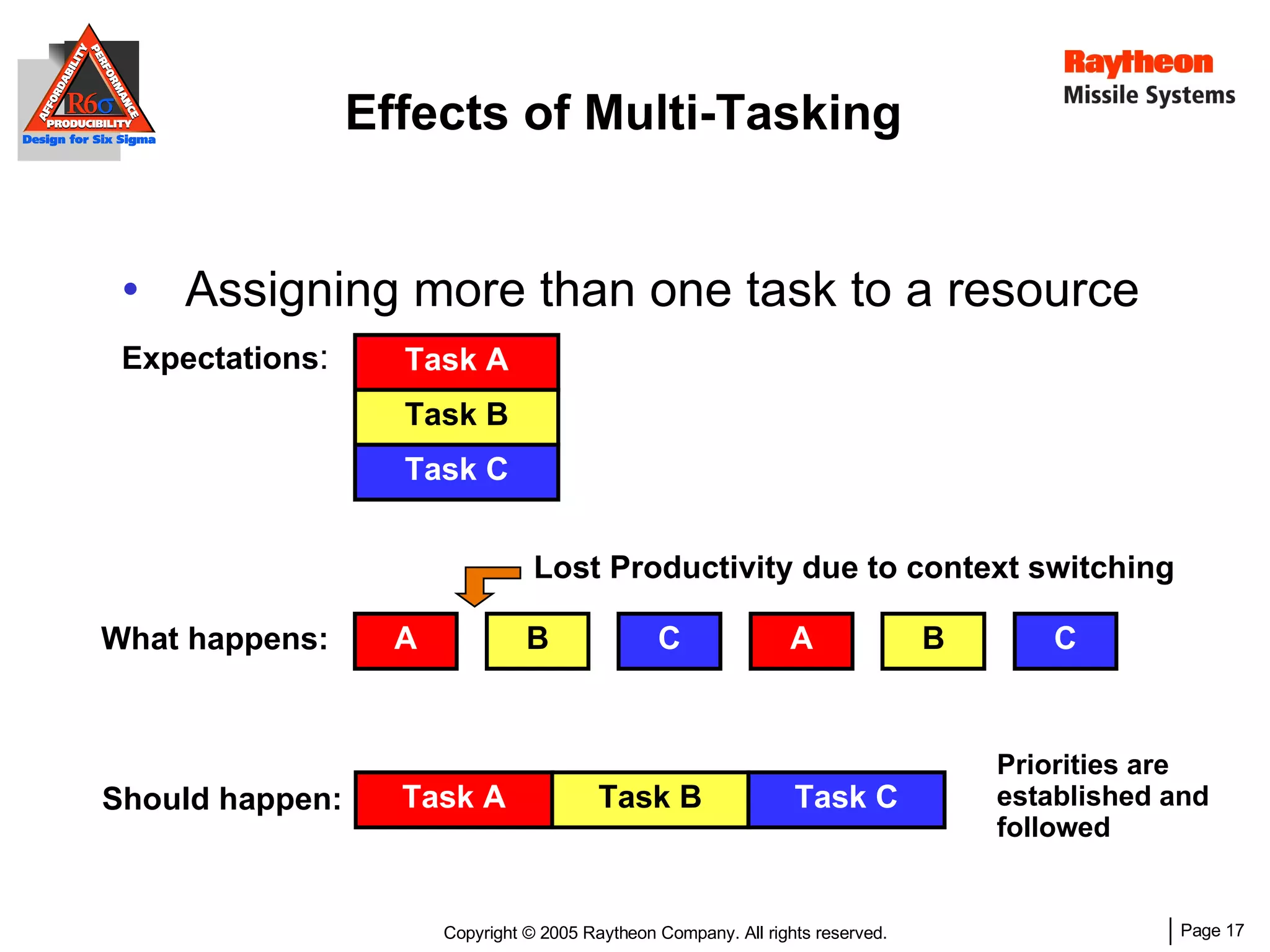
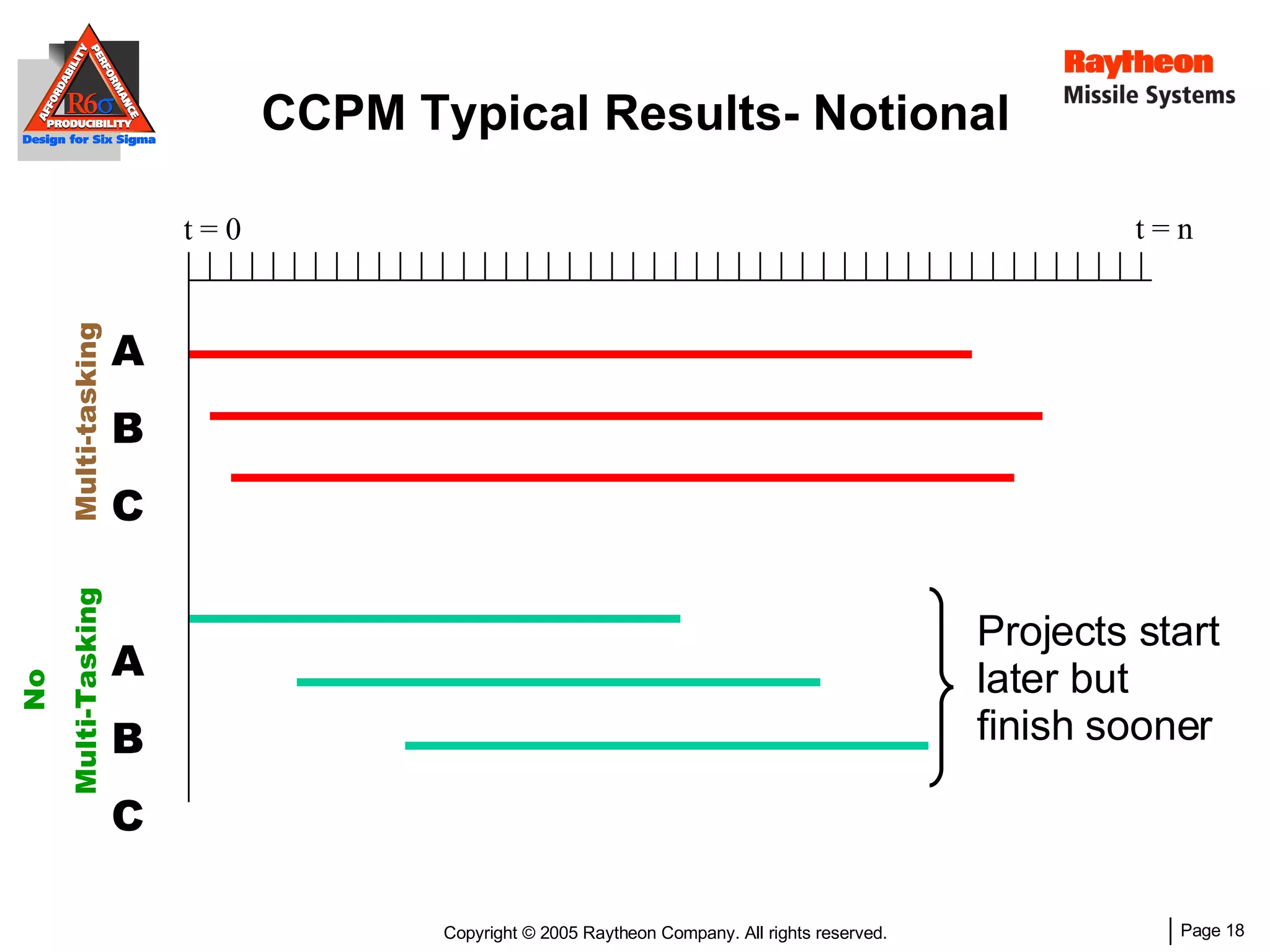
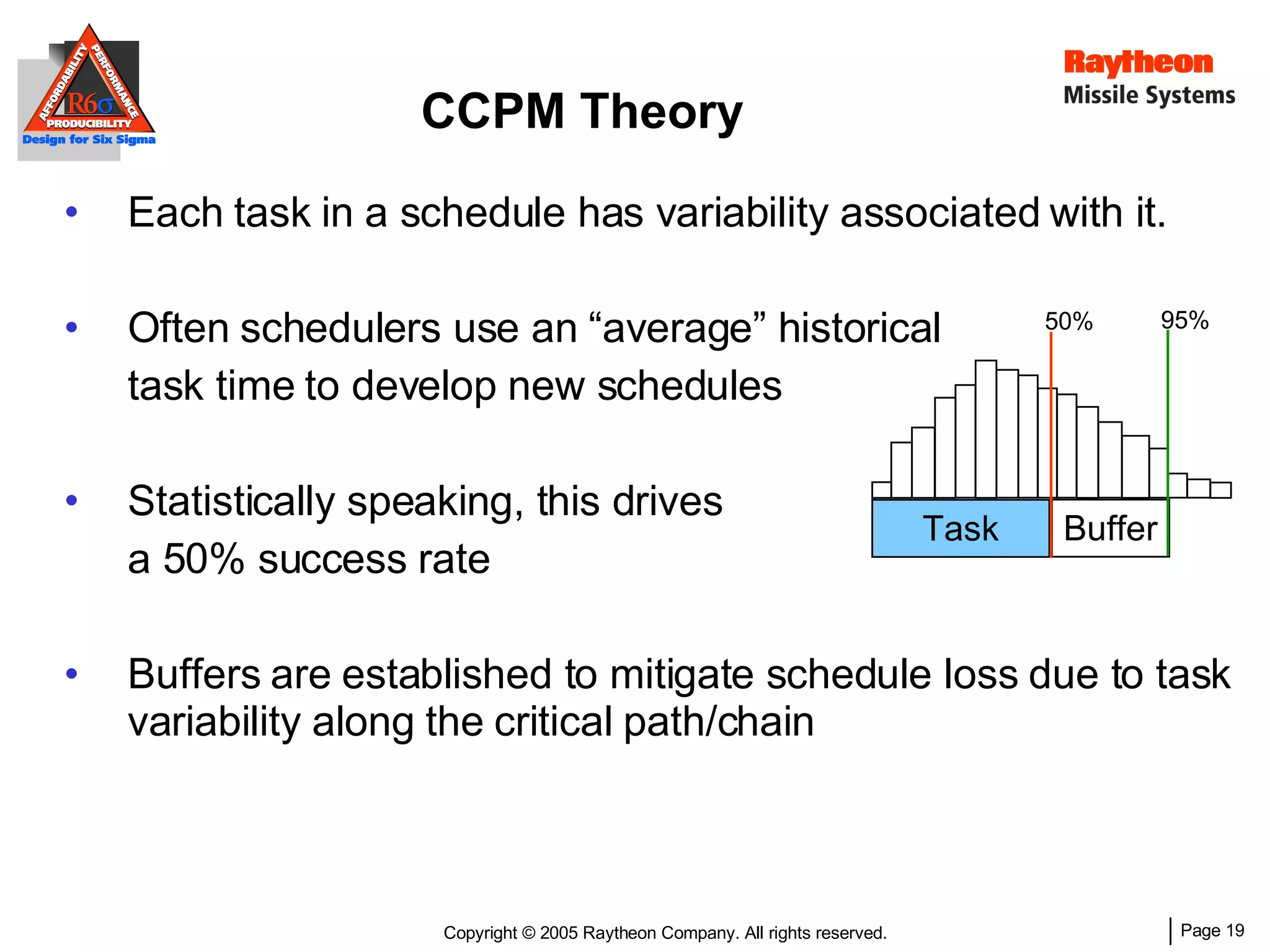
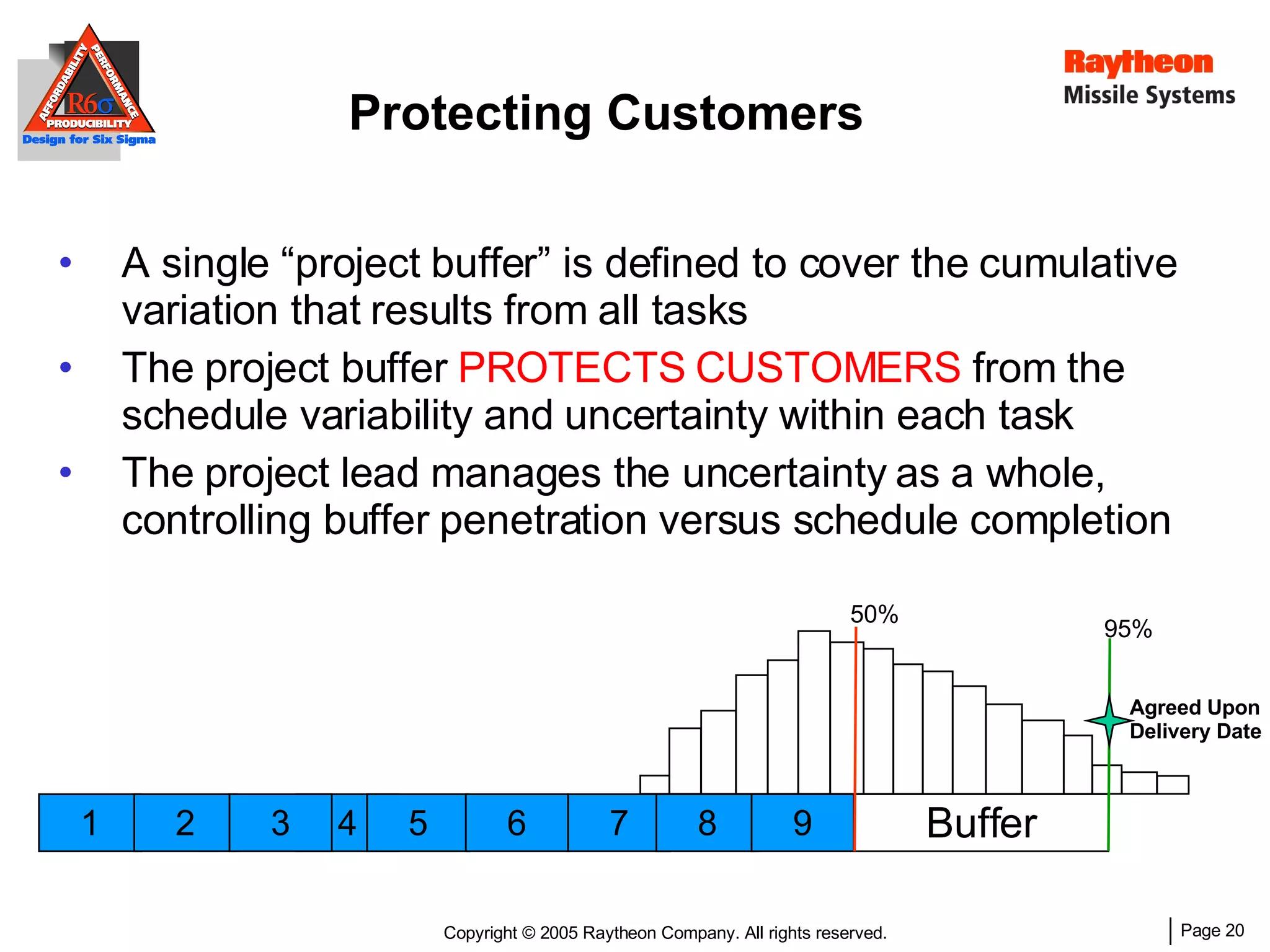
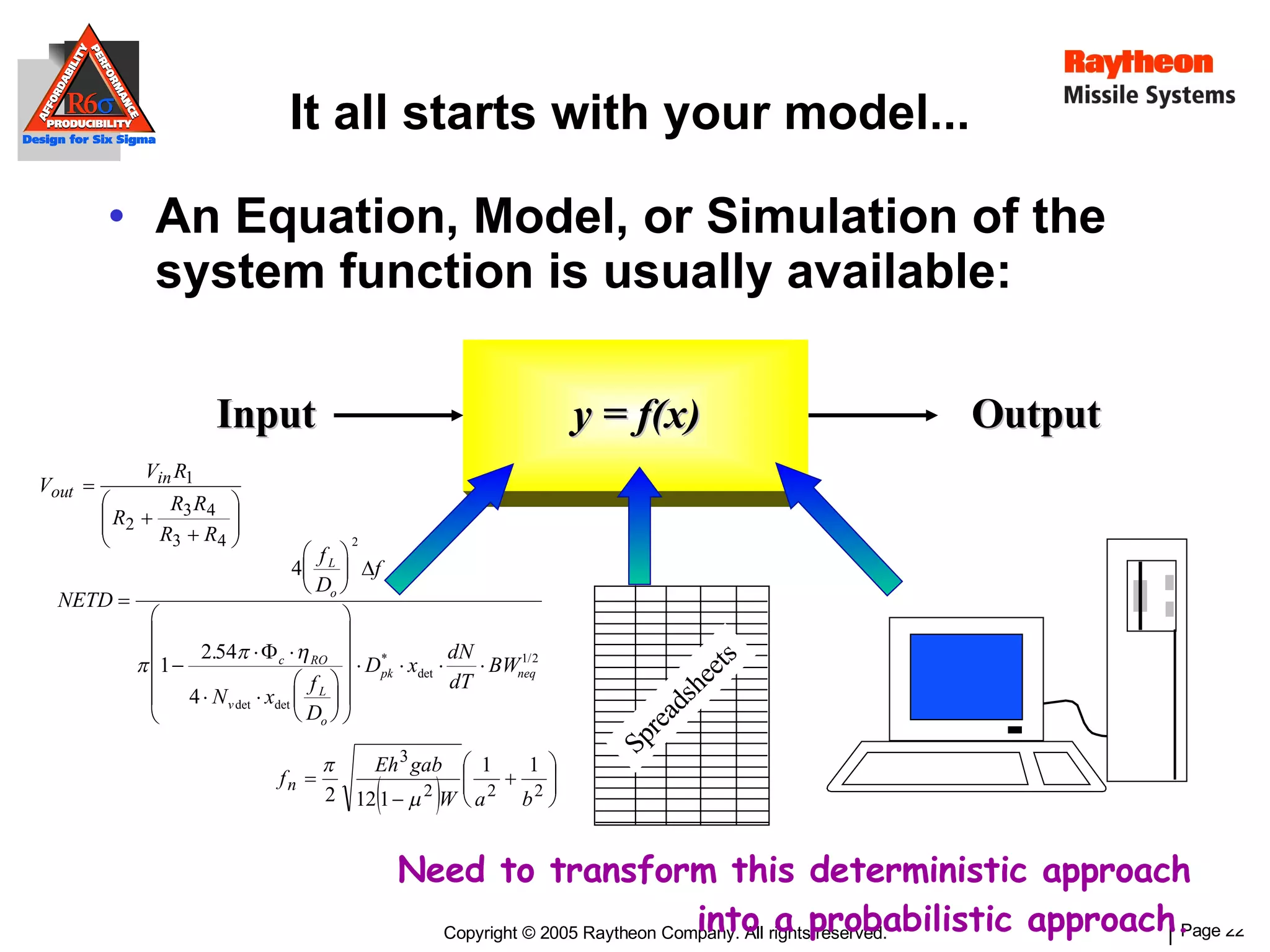
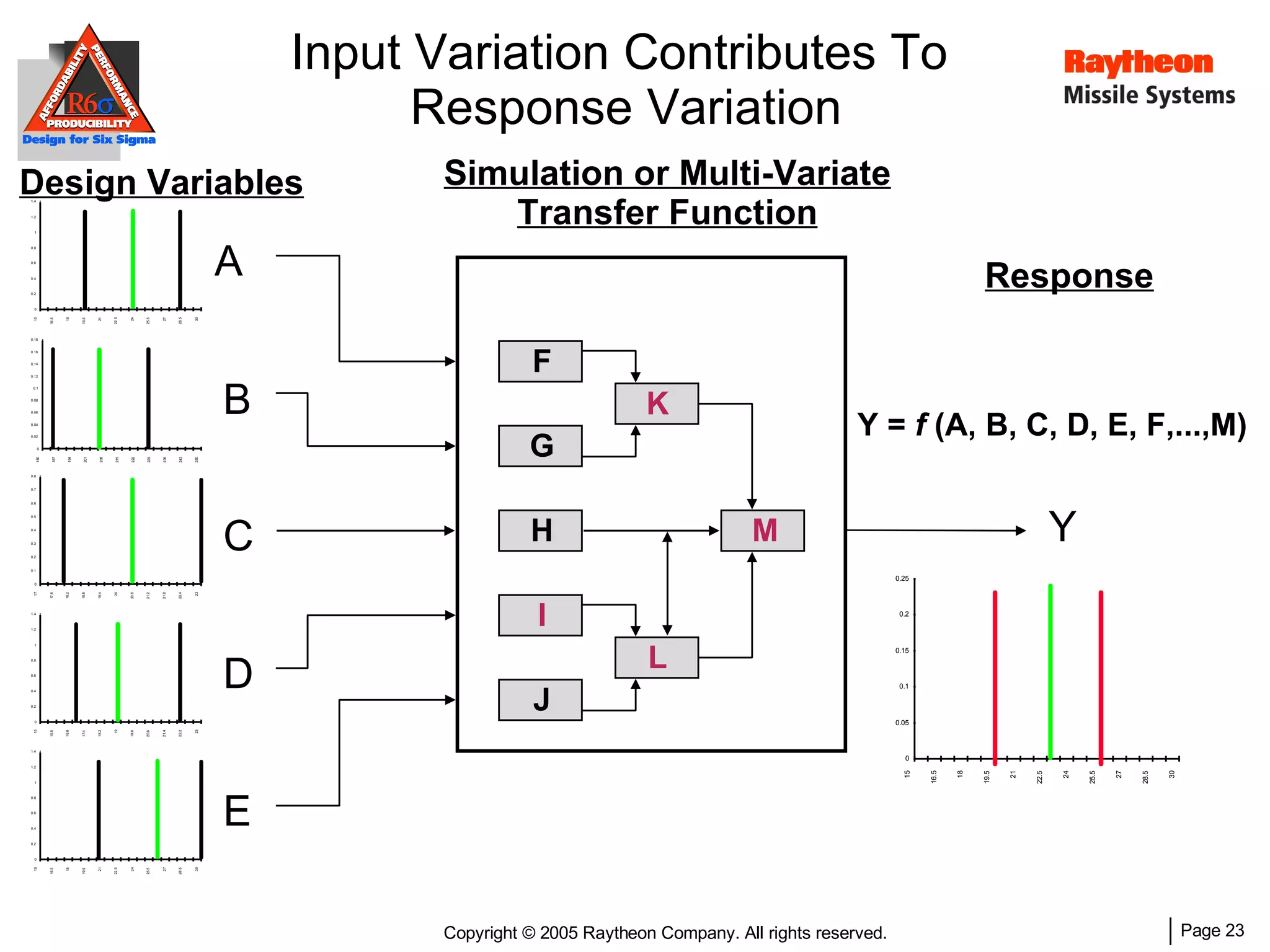
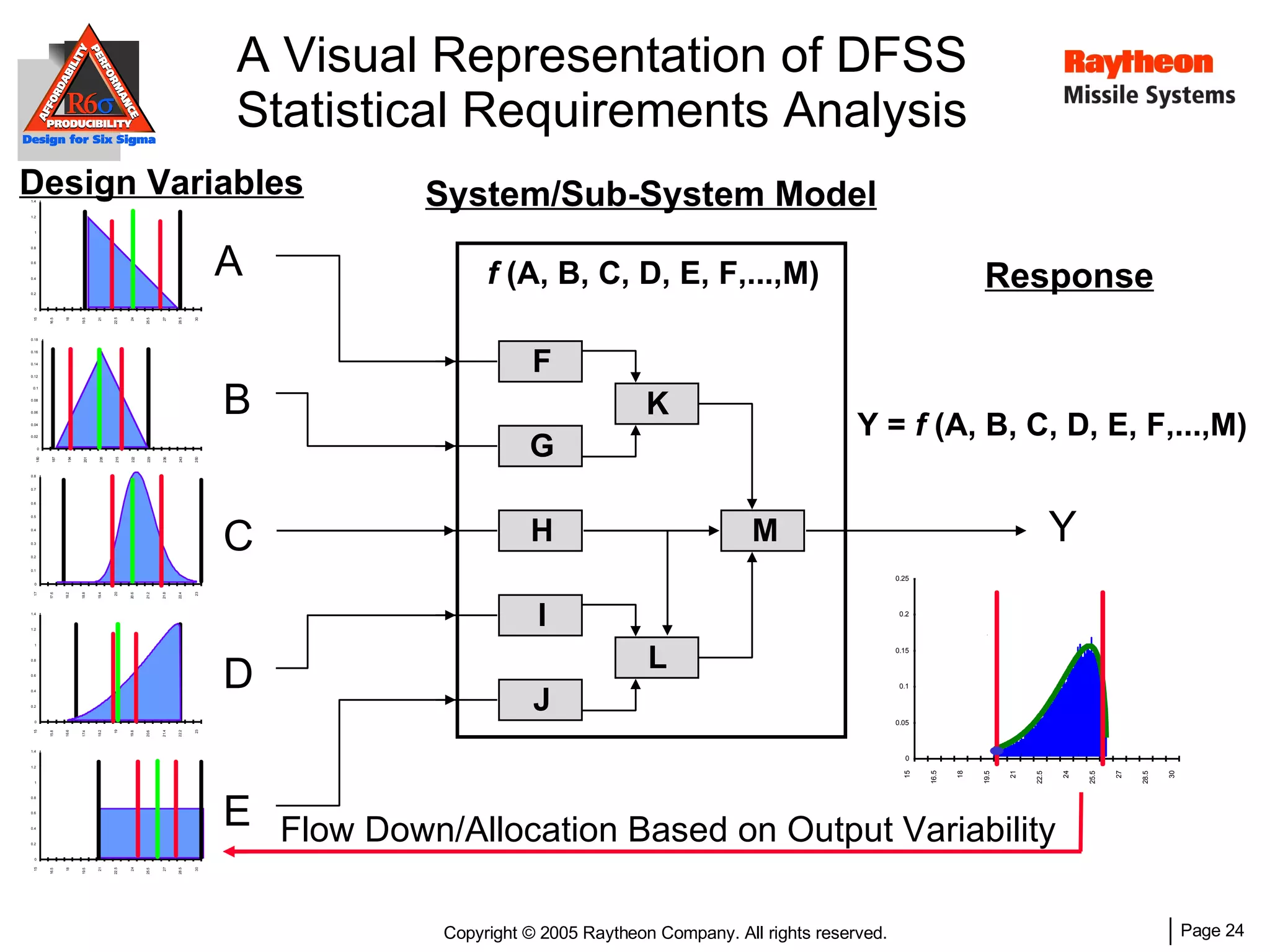
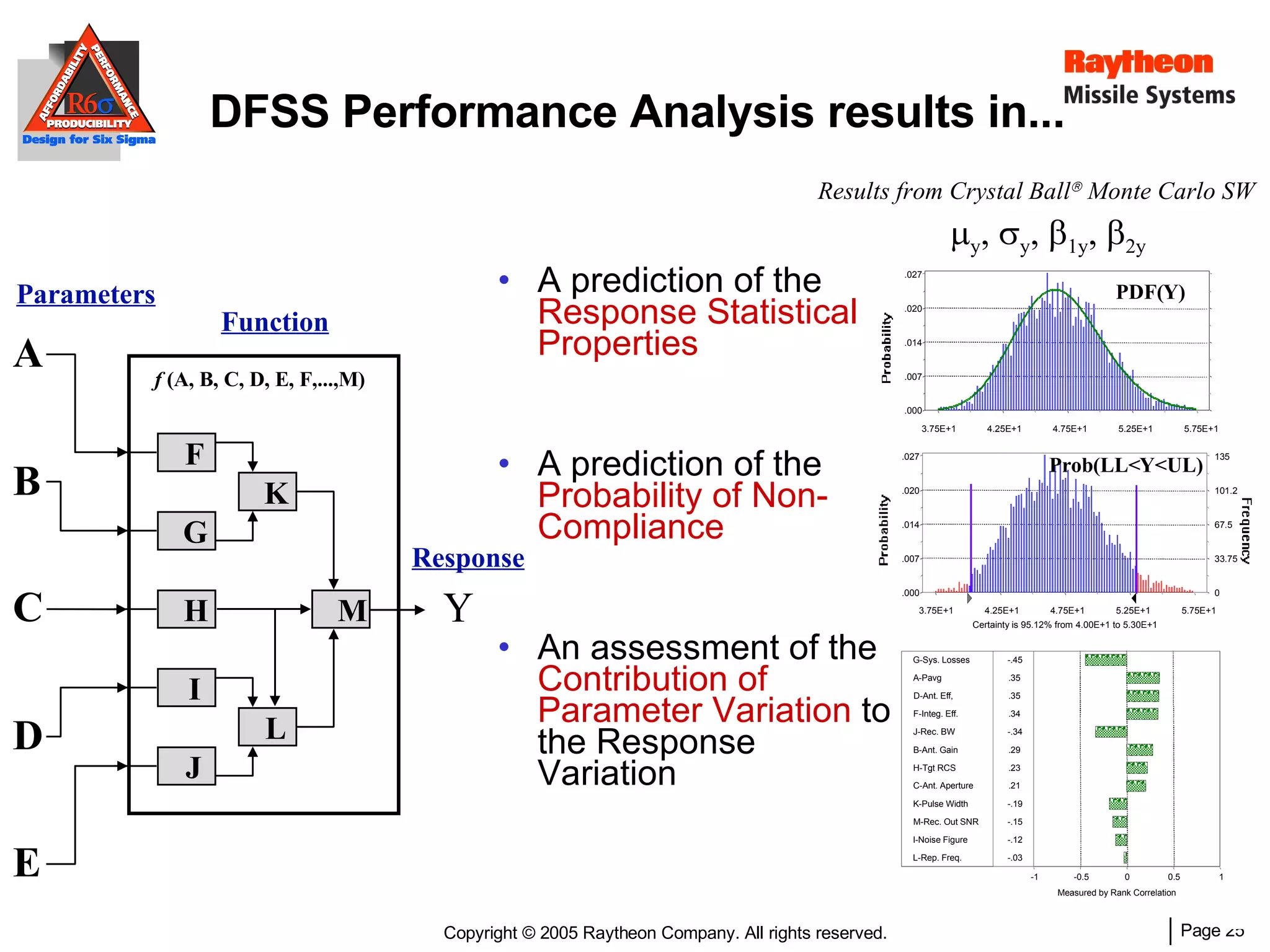
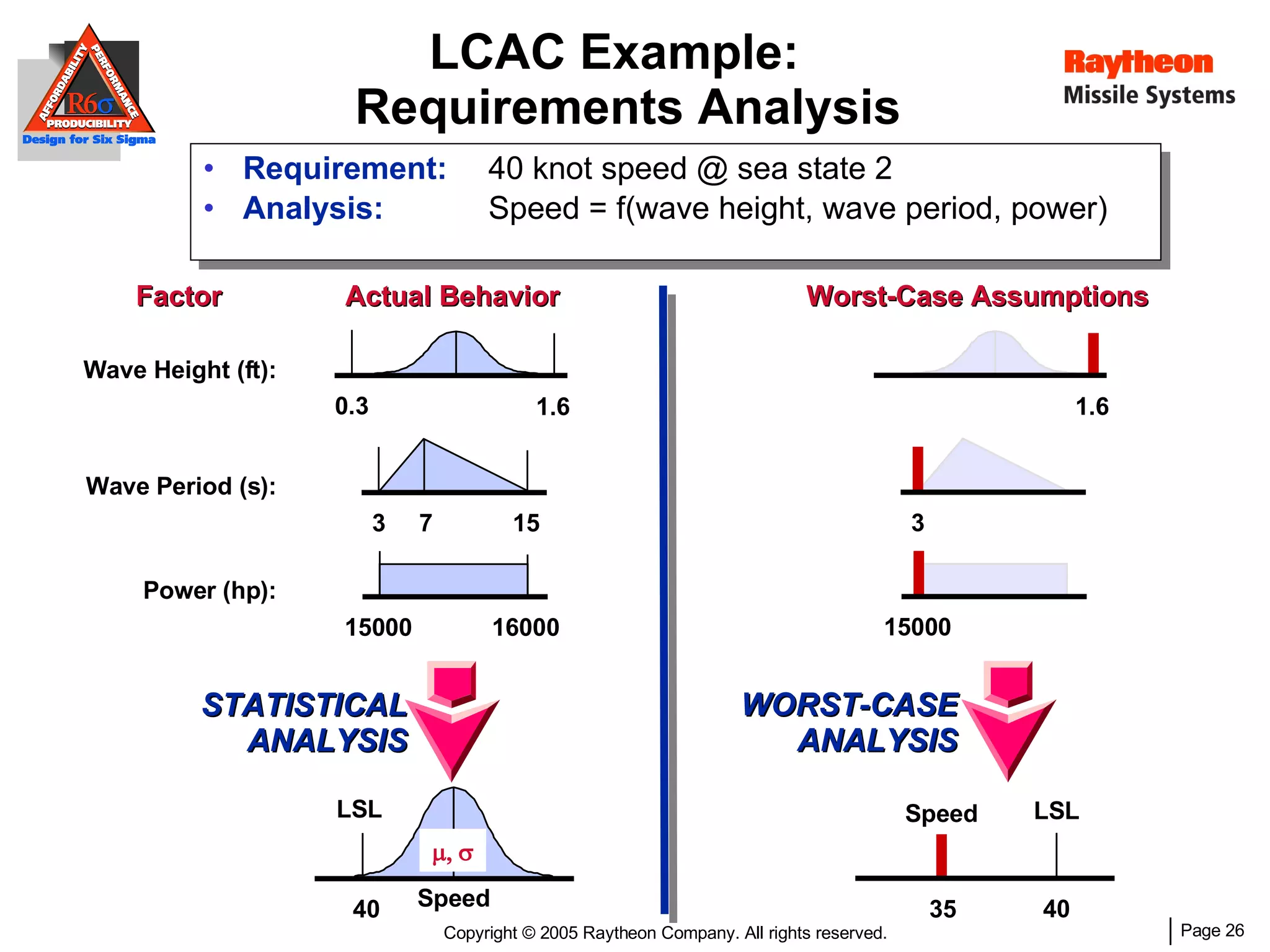
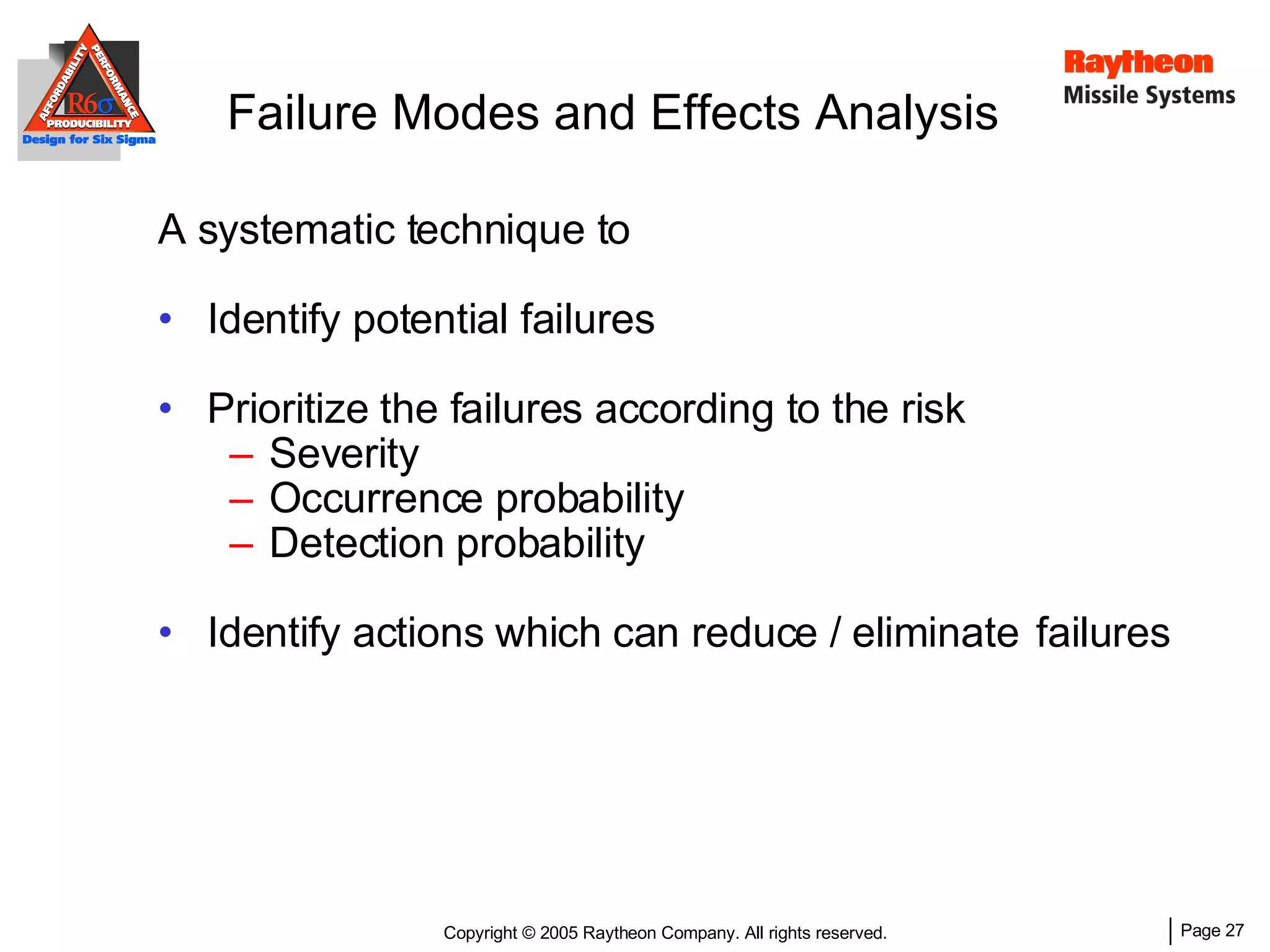
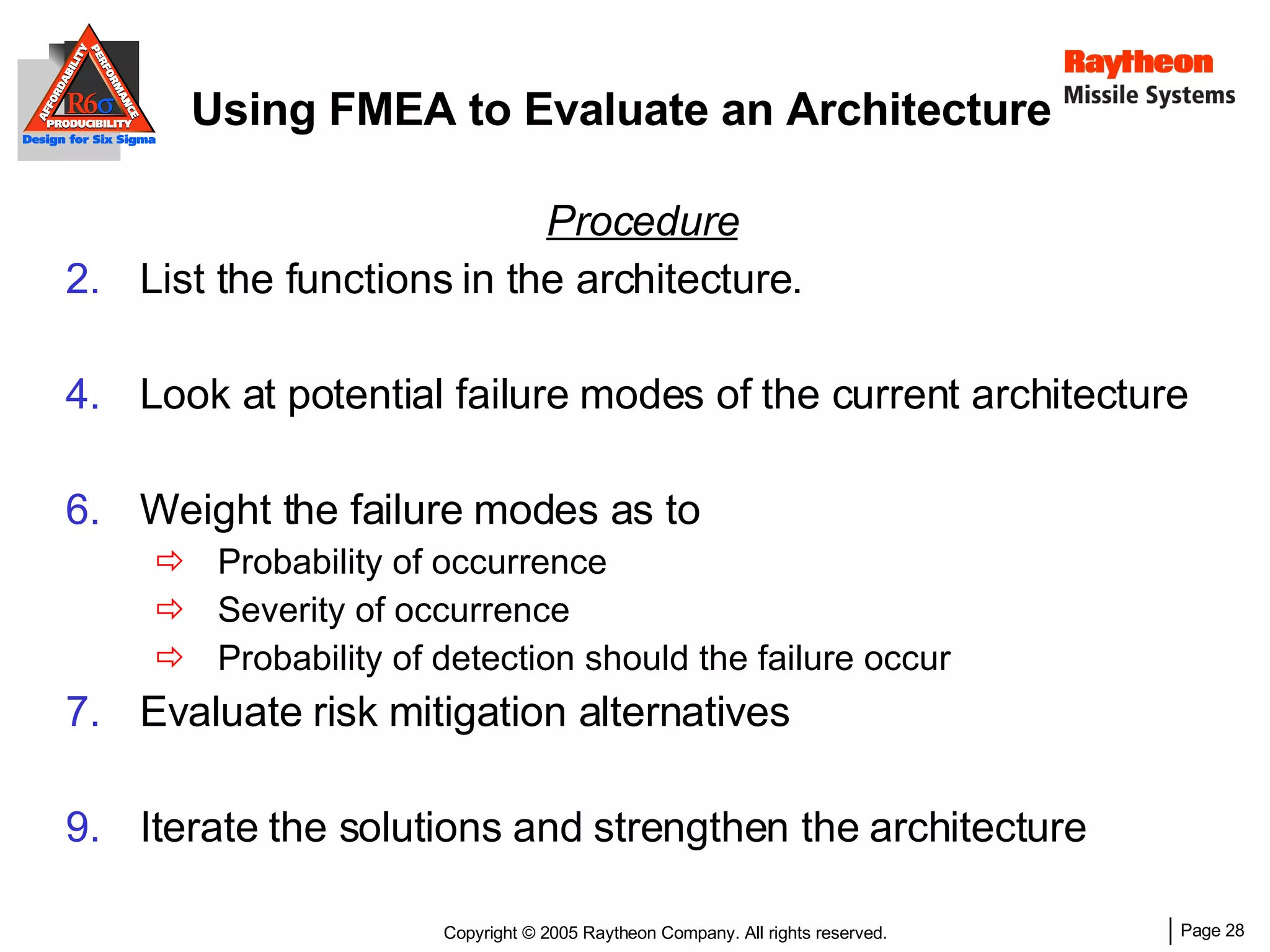
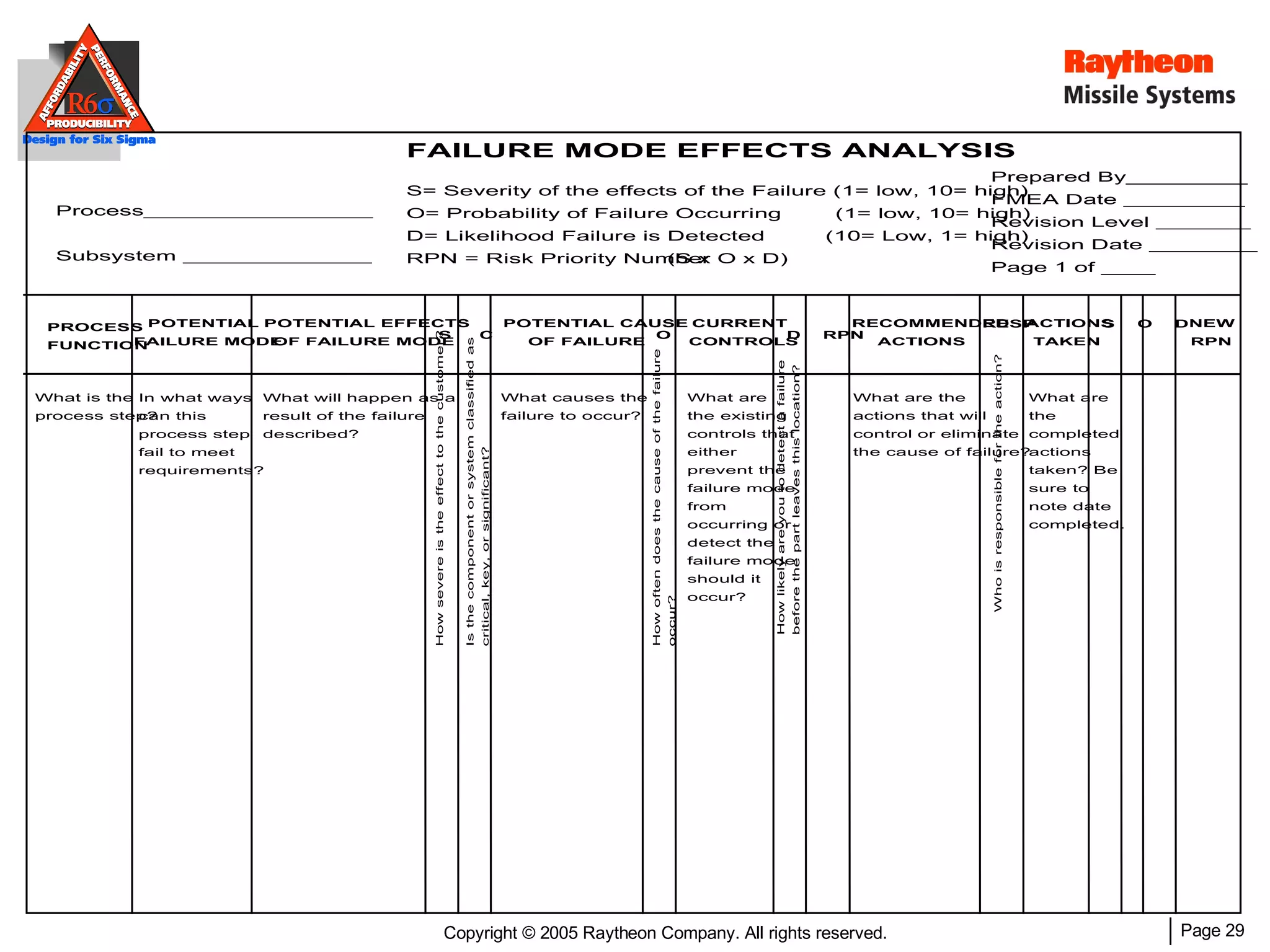
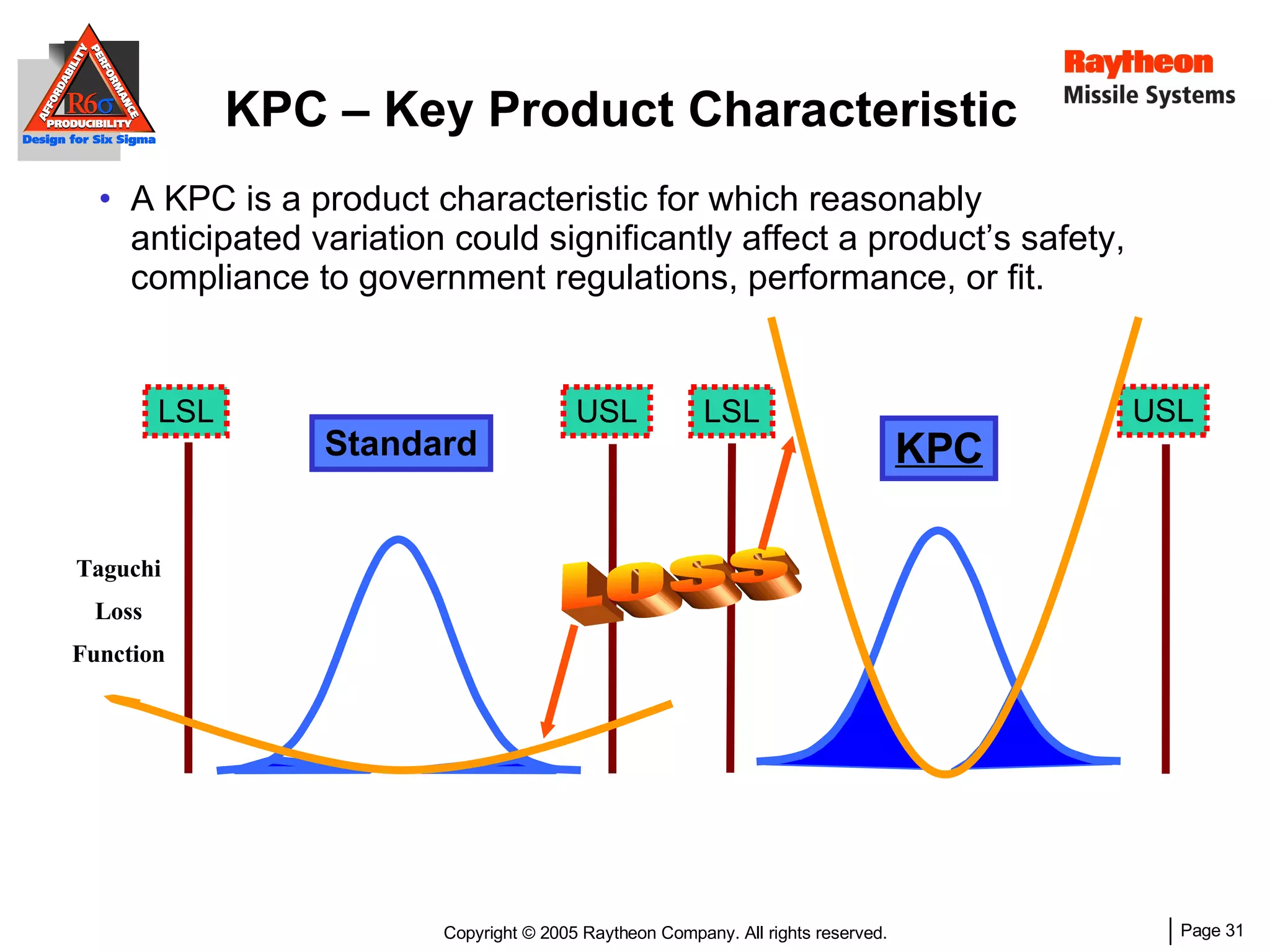
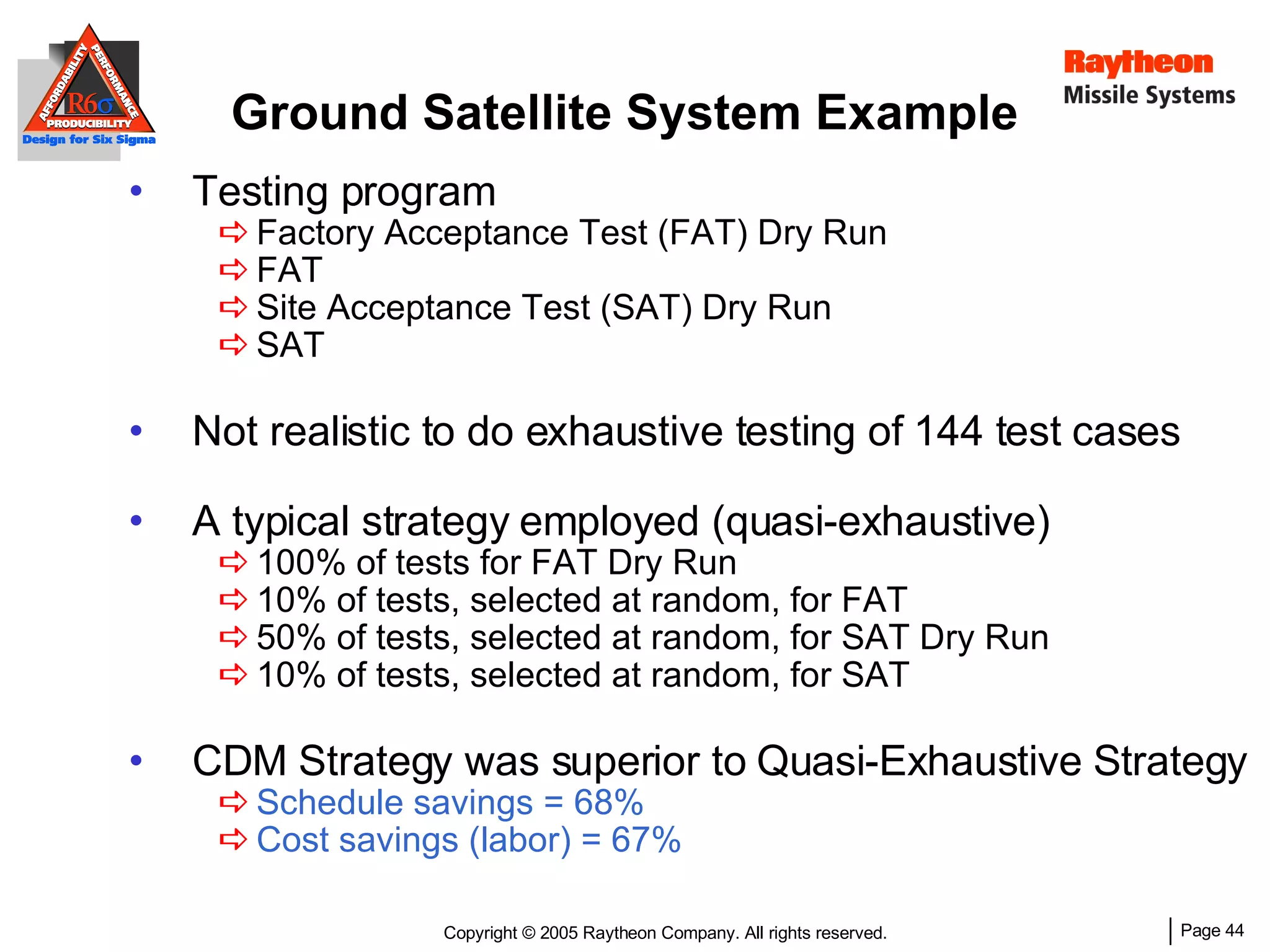
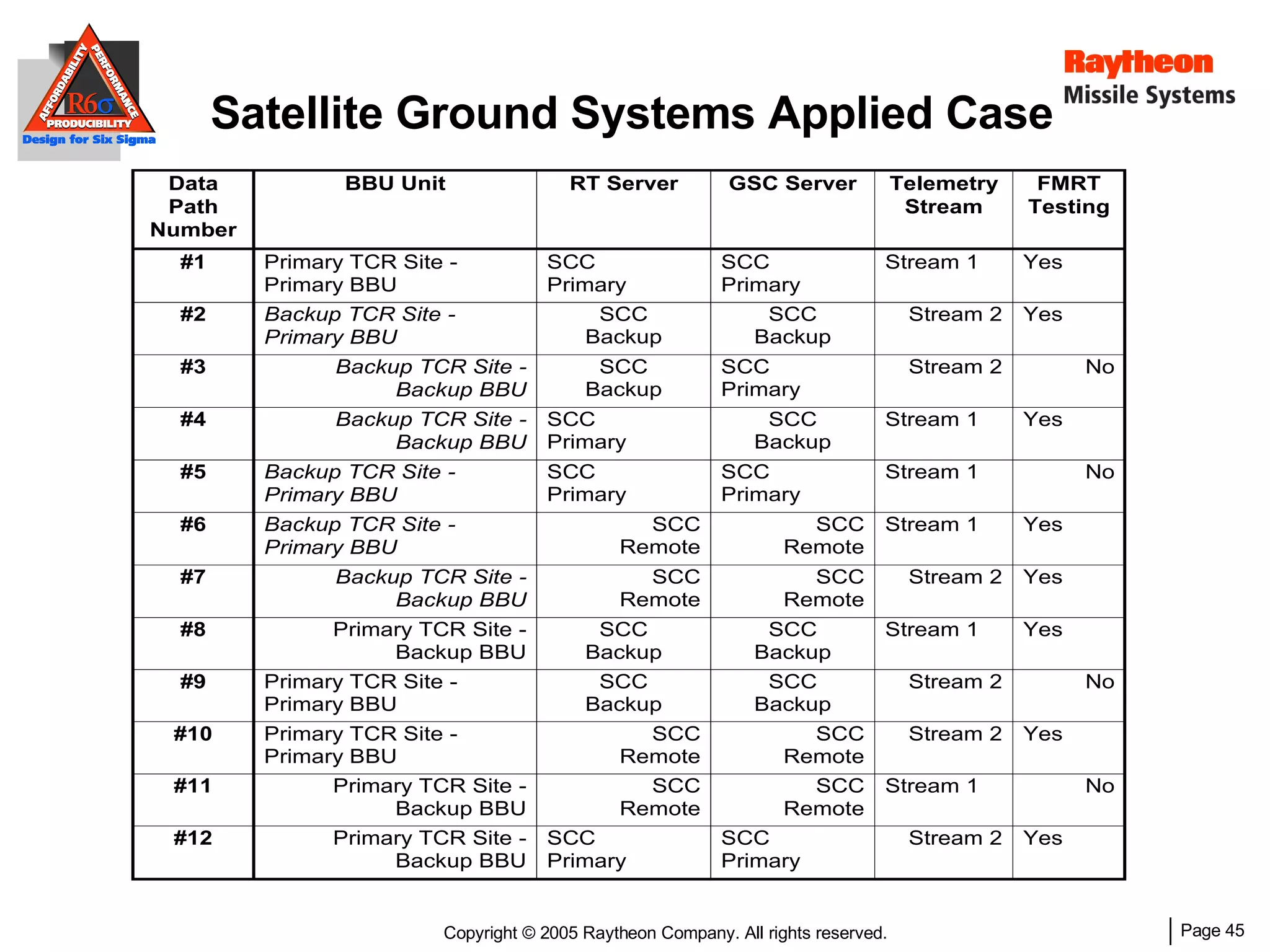
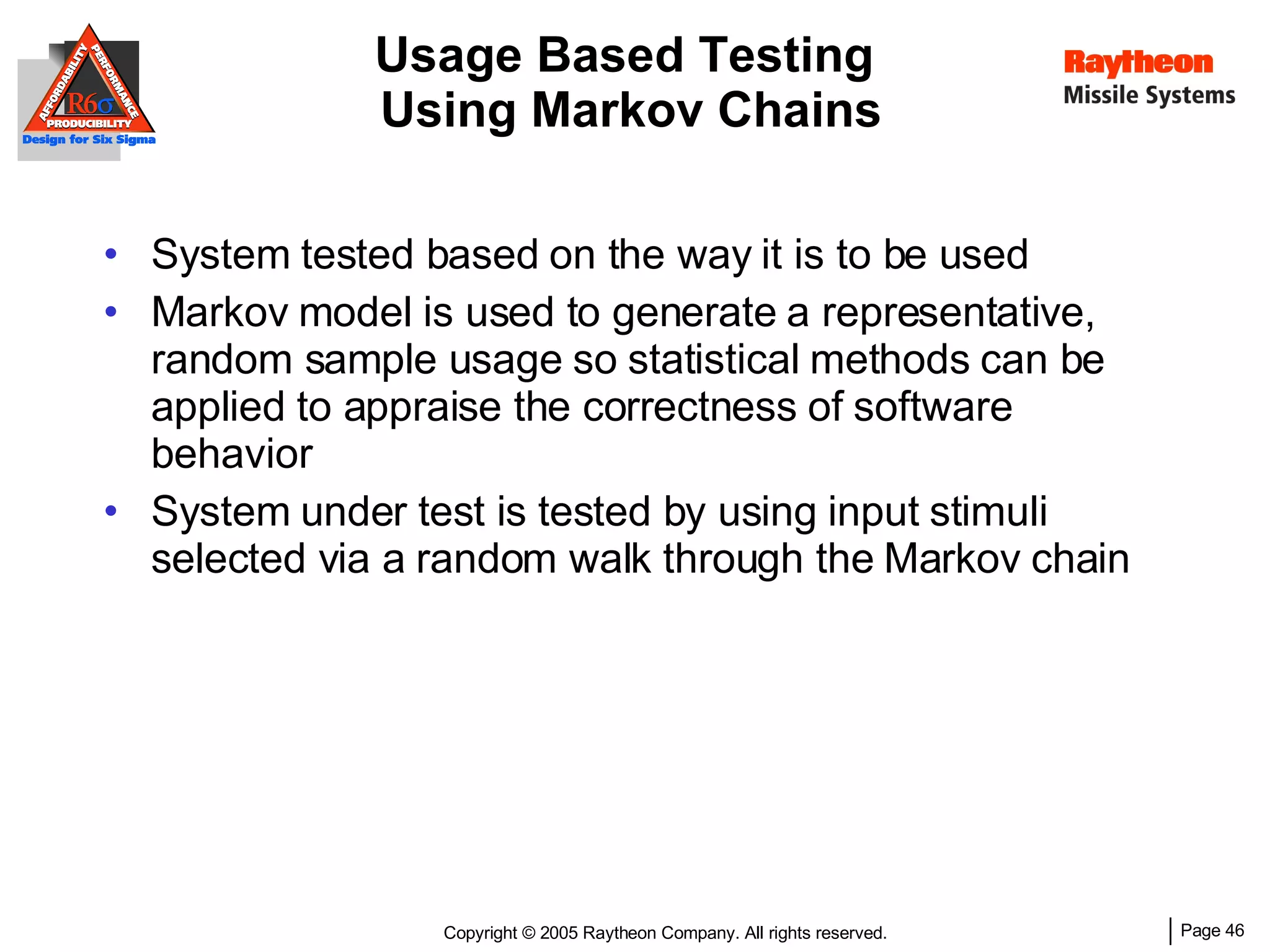
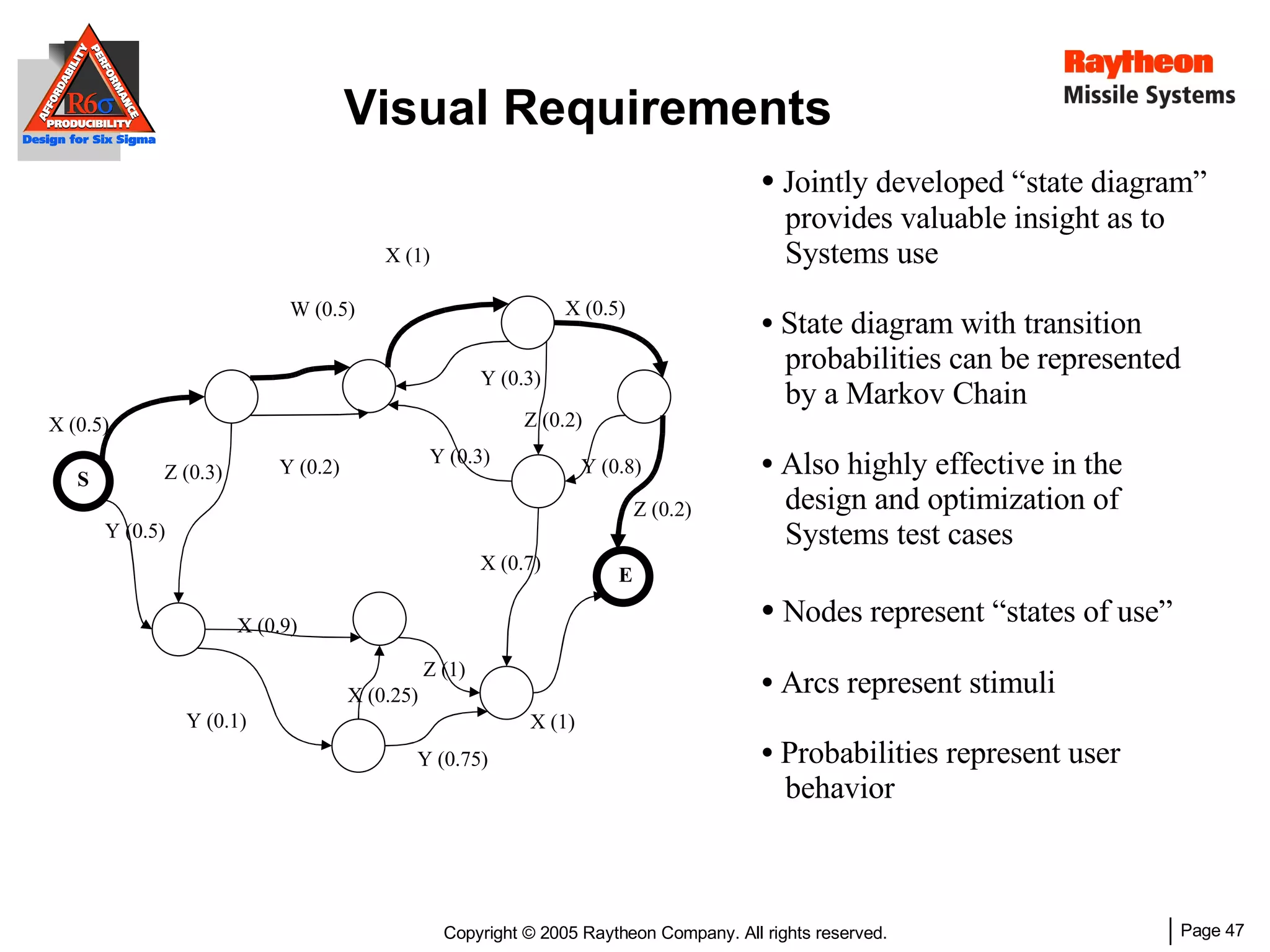
The document discusses using Design for Six Sigma (DFSS) methodology to achieve lean software development at Raytheon Missile Systems. It describes applying DFSS principles across the software development lifecycle, including capturing customer needs, managing costs, designing for producibility and performance, using statistical modeling and simulation, and conducting failure mode and effects analysis. DFSS is presented as a way to optimize software designs for customers' needs while balancing affordability, performance, and testability.
![Using Design for Six Sigma to achieve Lean Software Development at Raytheon Missile Systems Tony Strickland Certified Raytheon Six Sigma Expert (520) 794-7855 [email_address] ®](https://image.slidesharecdn.com/qm007-1212804524649787-9/75/QM-007-Design-for-6-sigma-1-2048.jpg)