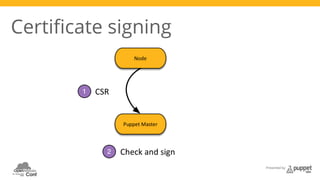
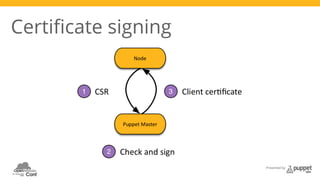
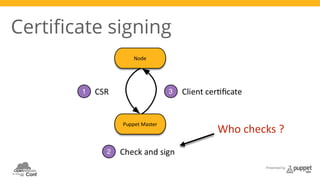
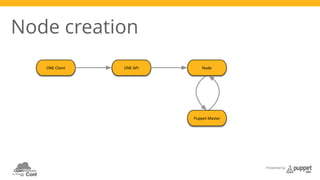
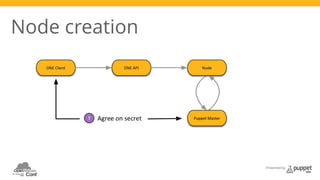
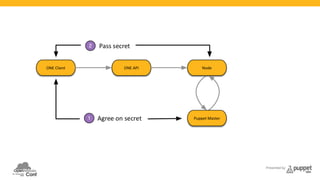
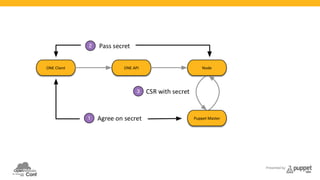
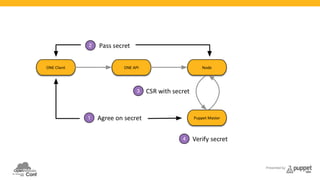
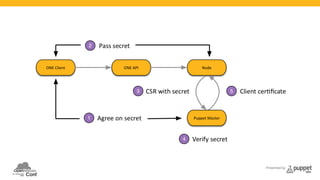
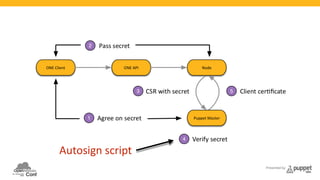
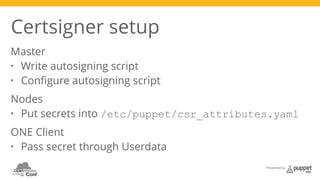
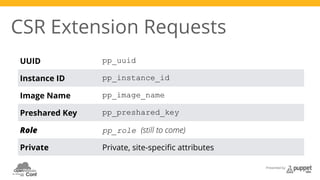
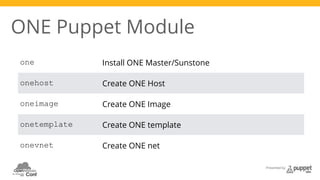
The document presents a deep dive into configuration management using Puppet, detailing an example manifest for managing a web server and instances in a cloud environment. It covers key topics such as infrastructure as code, autosigning scripts, and building images, while introducing various Puppet modules for managing resources. Additionally, it touches on the fundamentals of instance provisioning and management with tools like Razor, and provides links to further resources and modules for enhanced functionality.






![Presented by
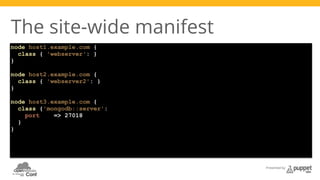
A basic manifest
class webserver {
package { 'httpd':
ensure => latest
} ->
file { '/etc/httpd/conf.d/local.conf':
ensure => file,
mode => 644,
source => 'puppet:///modules/httpd/local.conf',
} ->
service { 'httpd':
ensure => running,
enable => true,
subscribe => File['/etc/httpd/conf.d/local.conf'],
}
}](https://image.slidesharecdn.com/puppetandopennebula-davidlutterkort-141205070956-conversion-gate01/85/OpenNebula-Conf-2014-Puppet-and-OpenNebula-David-Lutterkort-9-320.jpg)
![Presented by
Override via inheritance
class webserver2 inherits webserver {
File['/etc/httpd/conf.d/local.conf'] {
source => 'puppet:///modules/httpd/other-local.conf',
}
}](https://image.slidesharecdn.com/puppetandopennebula-davidlutterkort-141205070956-conversion-gate01/85/OpenNebula-Conf-2014-Puppet-and-OpenNebula-David-Lutterkort-10-320.jpg)




![Presented by
Instance management
ec2_instance { 'name-of-instance':
ensure => present,
region => 'us-east-1',
availability_zone => 'us-east-1a',
image_id => ‘ami-ttylinux',
instance_type => 't1.micro',
monitoring => true,
key_name => 'name-of-existing-key',
security_groups => ['group1', 'group2'],
user_data => template('module/user-data.erb')
}](https://image.slidesharecdn.com/puppetandopennebula-davidlutterkort-141205070956-conversion-gate01/85/OpenNebula-Conf-2014-Puppet-and-OpenNebula-David-Lutterkort-17-320.jpg)