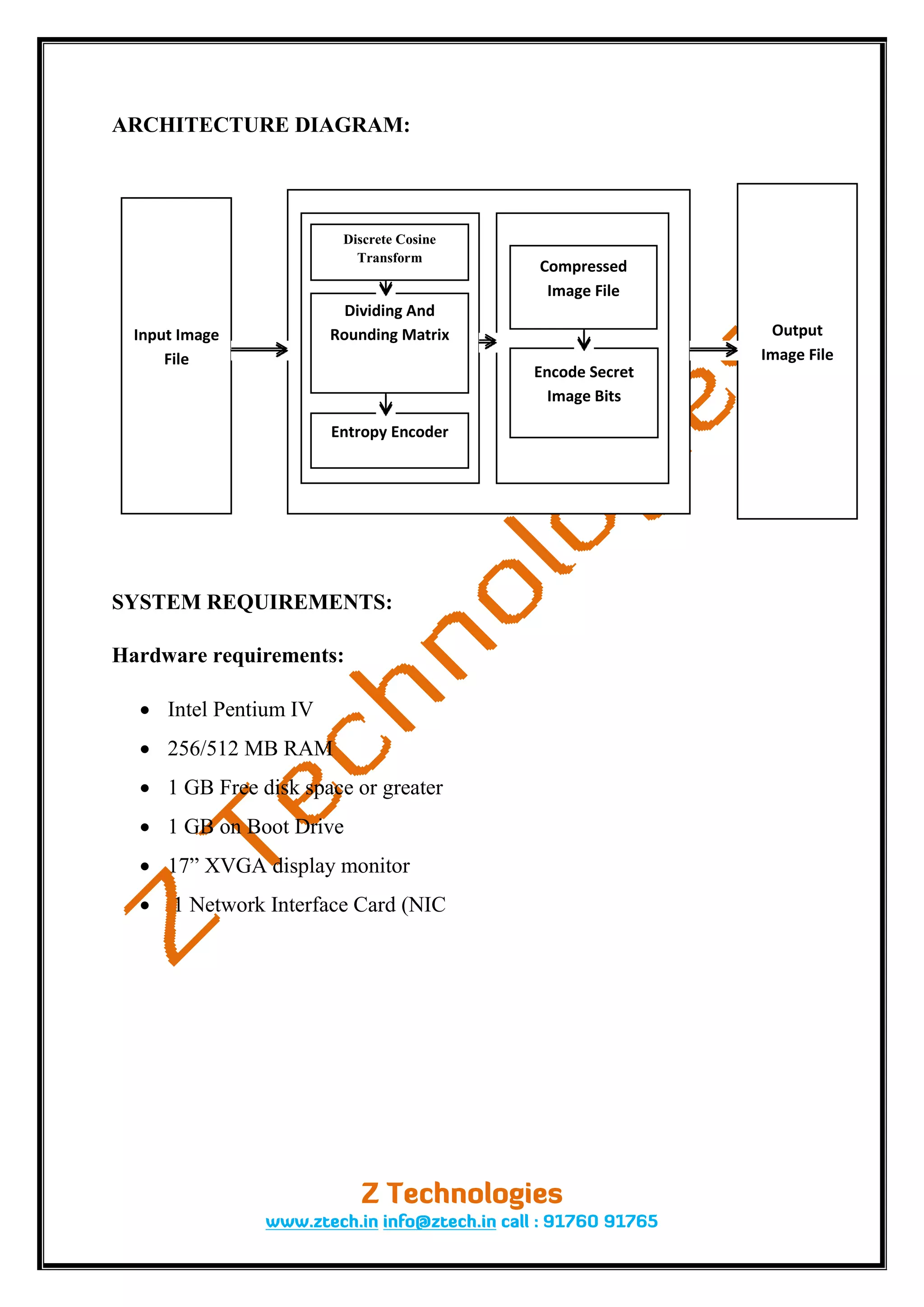
The document presents a new channel selection rule for JPEG steganography aimed at enhancing security and reducing errors during data hiding in compressed video. It evaluates the performance of data-hiding algorithms based on metrics such as data size overhead and reconstruction quality, and proposes a method that minimizes distortion and improves security using least significant bit (LSB) embedding and advanced encryption standards (AES). The proposed system overcomes the limitations of existing systems by utilizing advanced techniques to reduce compression errors and enhance robustness.