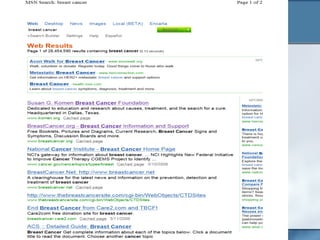
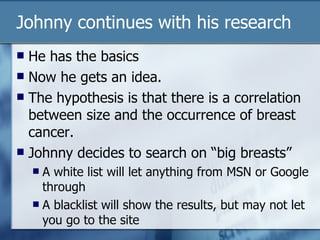
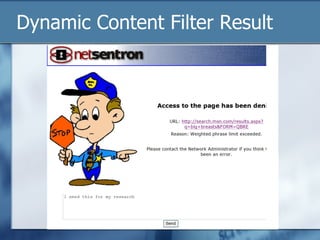
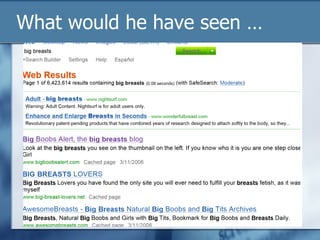
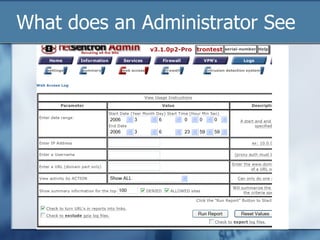
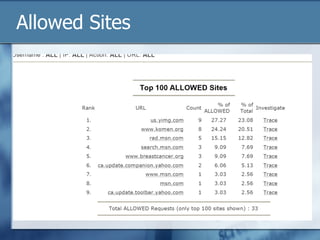
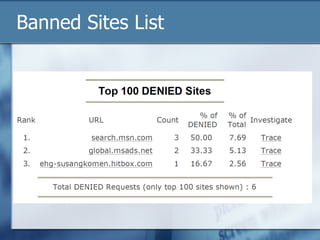
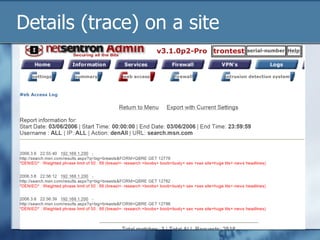
The document discusses the challenges of protecting children from inappropriate internet content, highlighting that a significant percentage of children inadvertently access pornography during educational searches. It emphasizes the importance of implementing effective internet filters and parental guidance to ensure safe online navigation for students, while also considering various filtering strategies like whitelists and blacklists. The need for balanced internet access—using the internet as a valuable research tool while maintaining safety—is a key focus throughout the text.