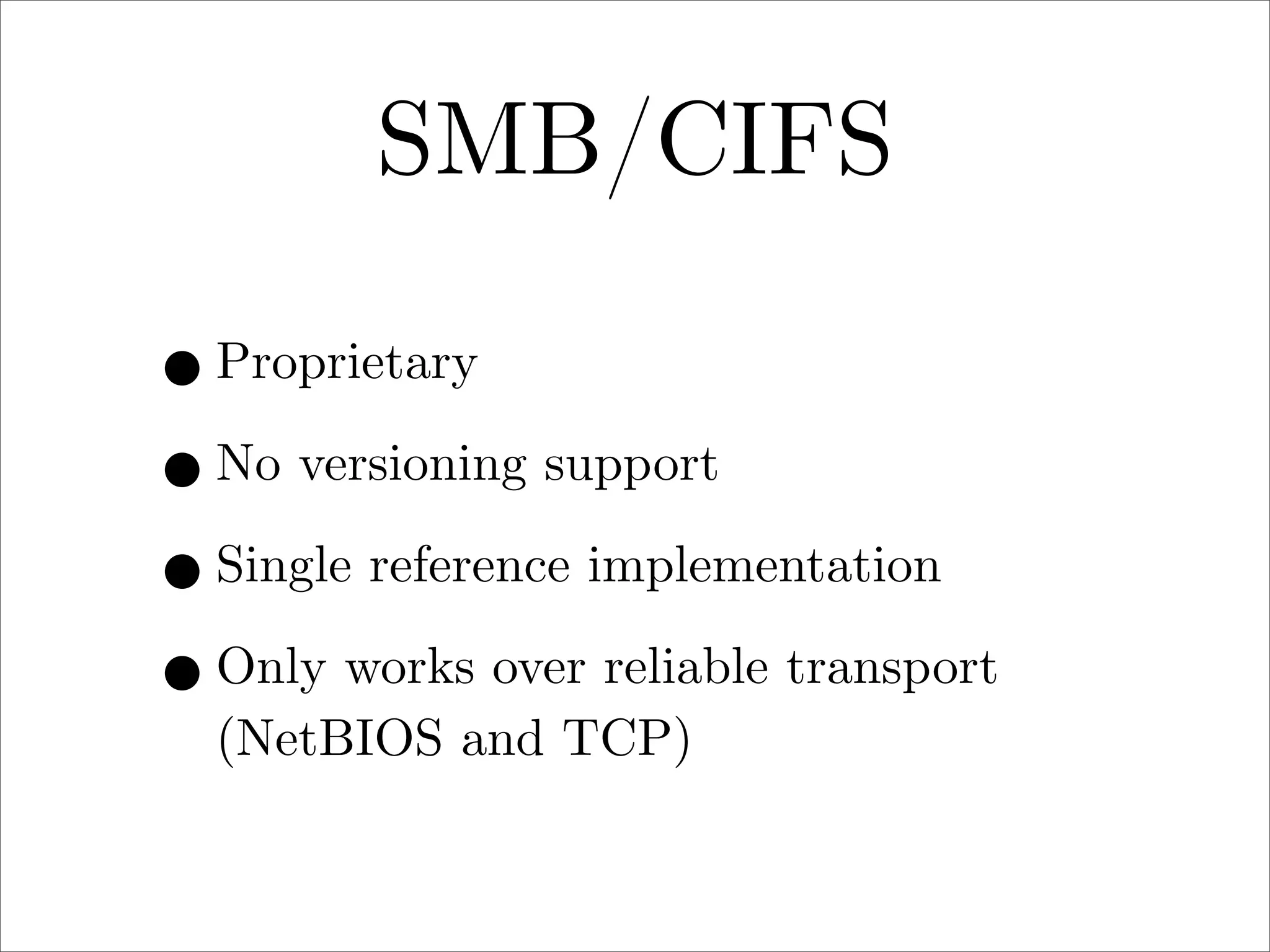
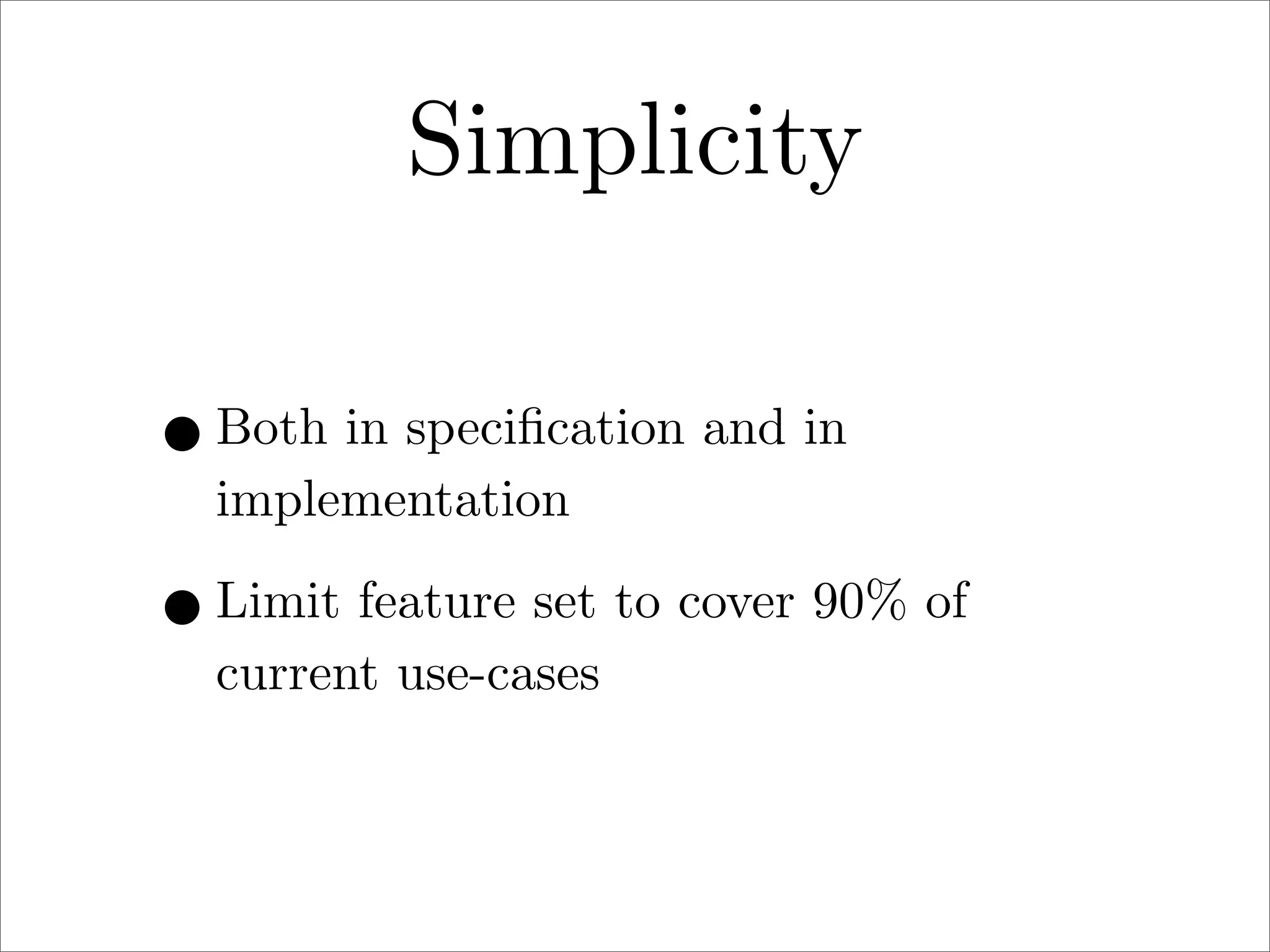
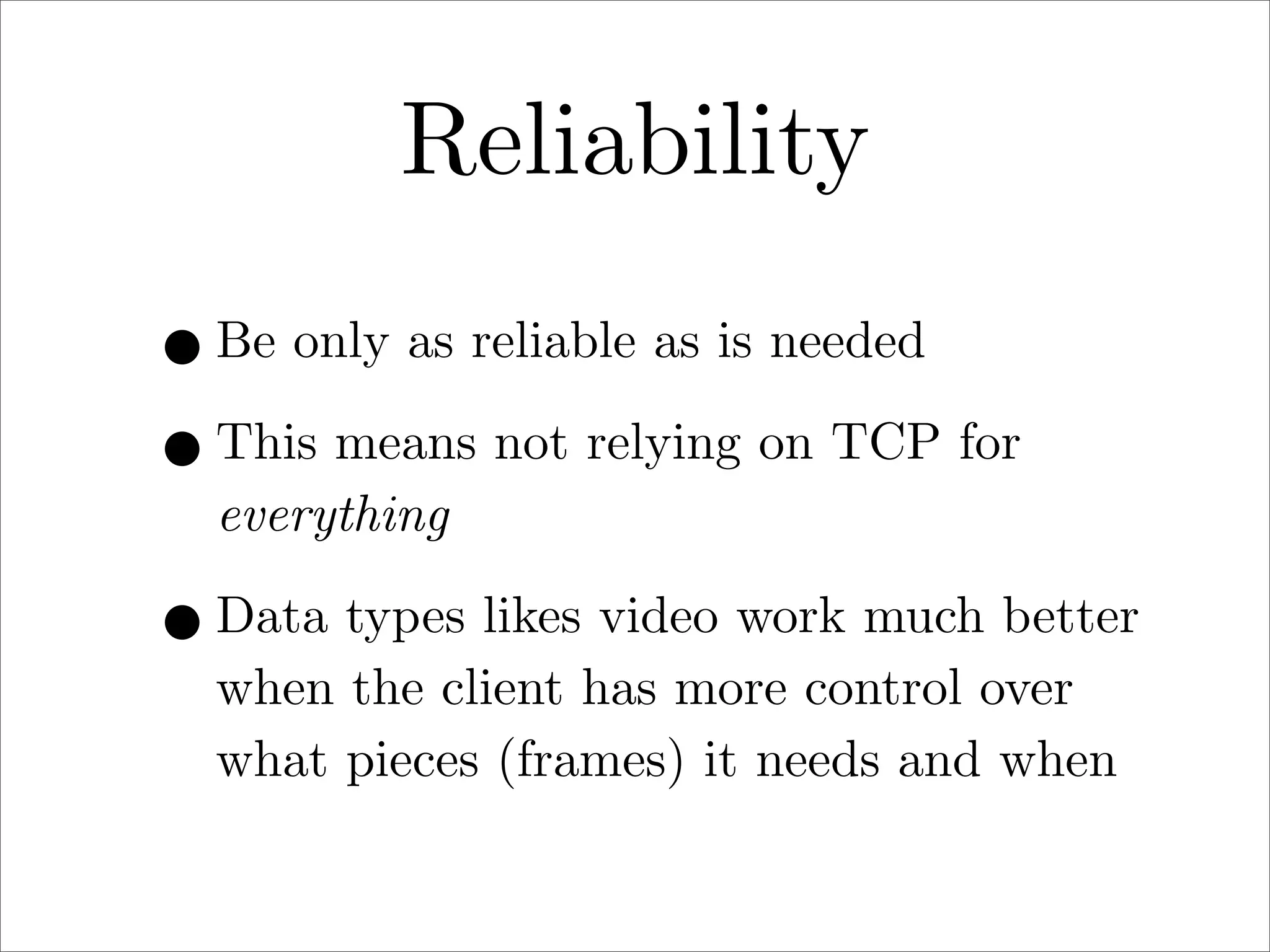
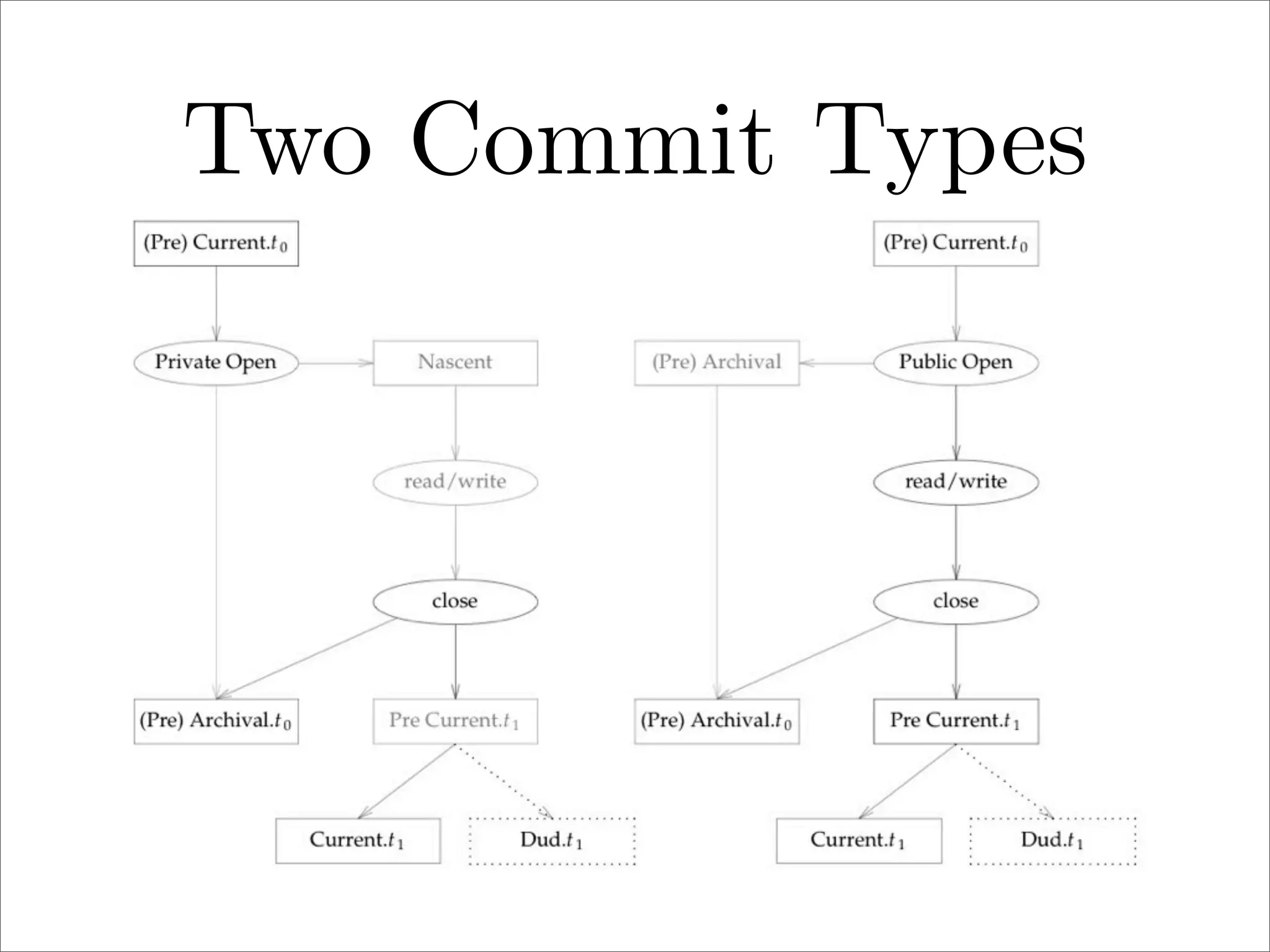
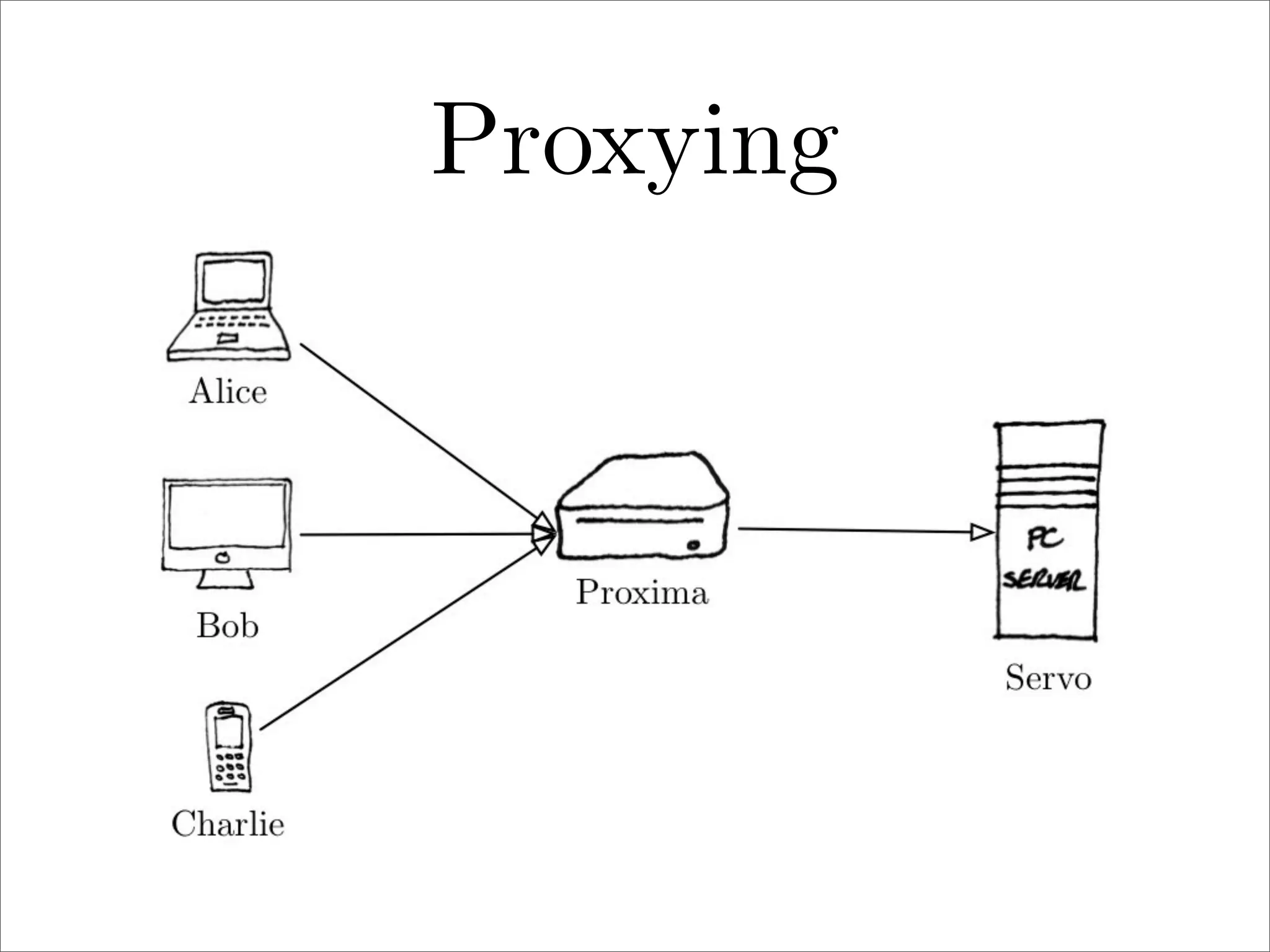
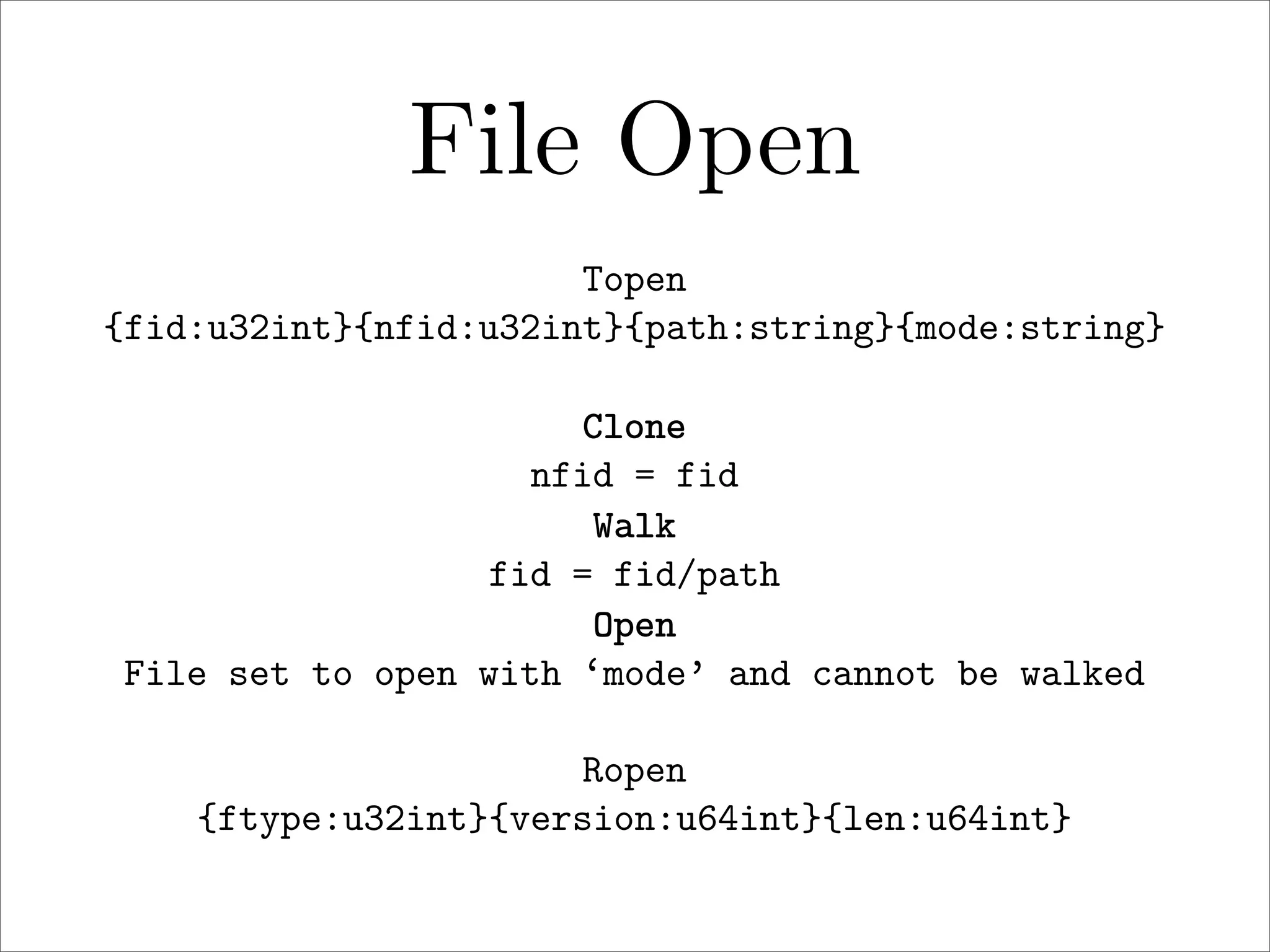
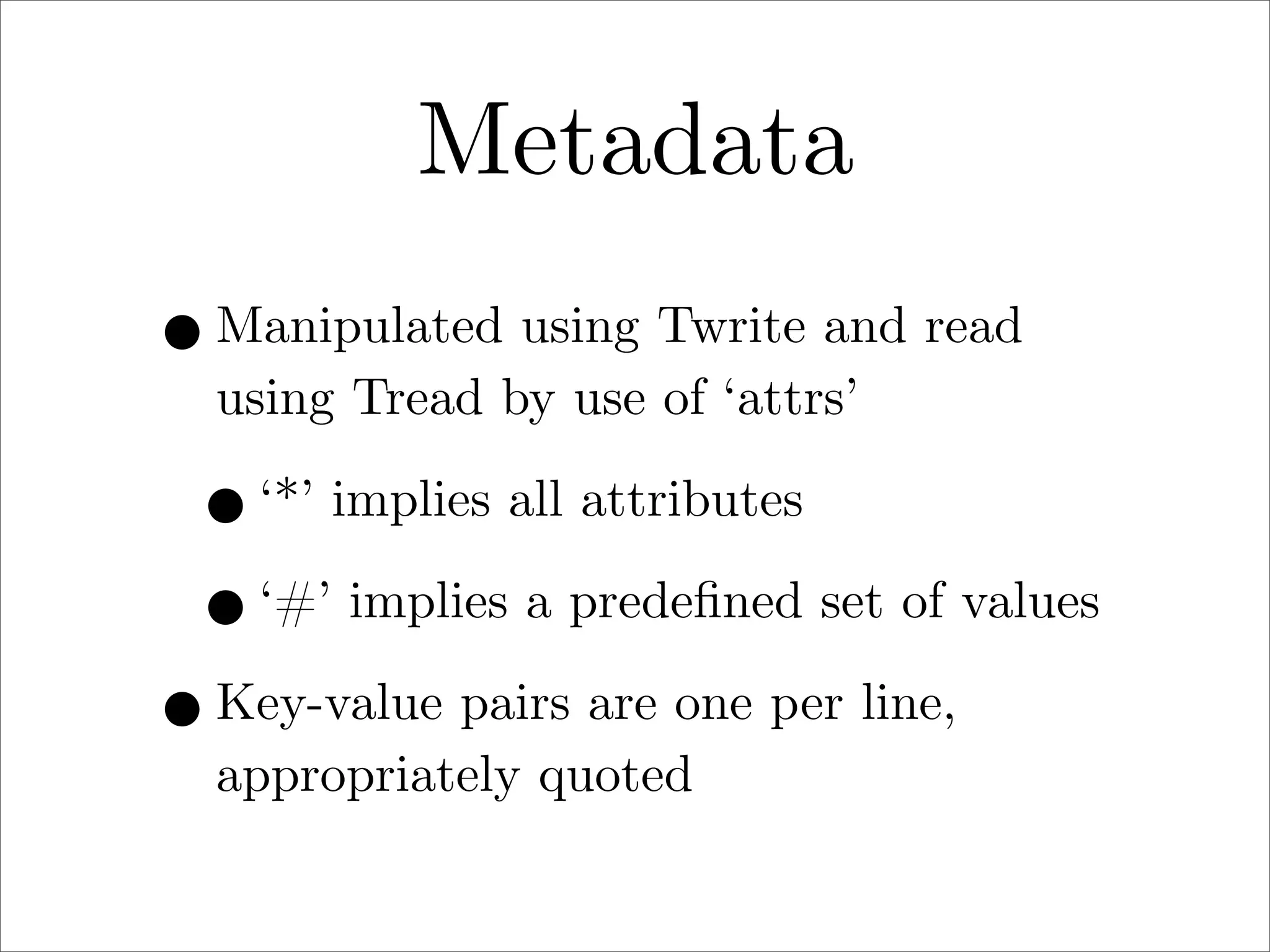
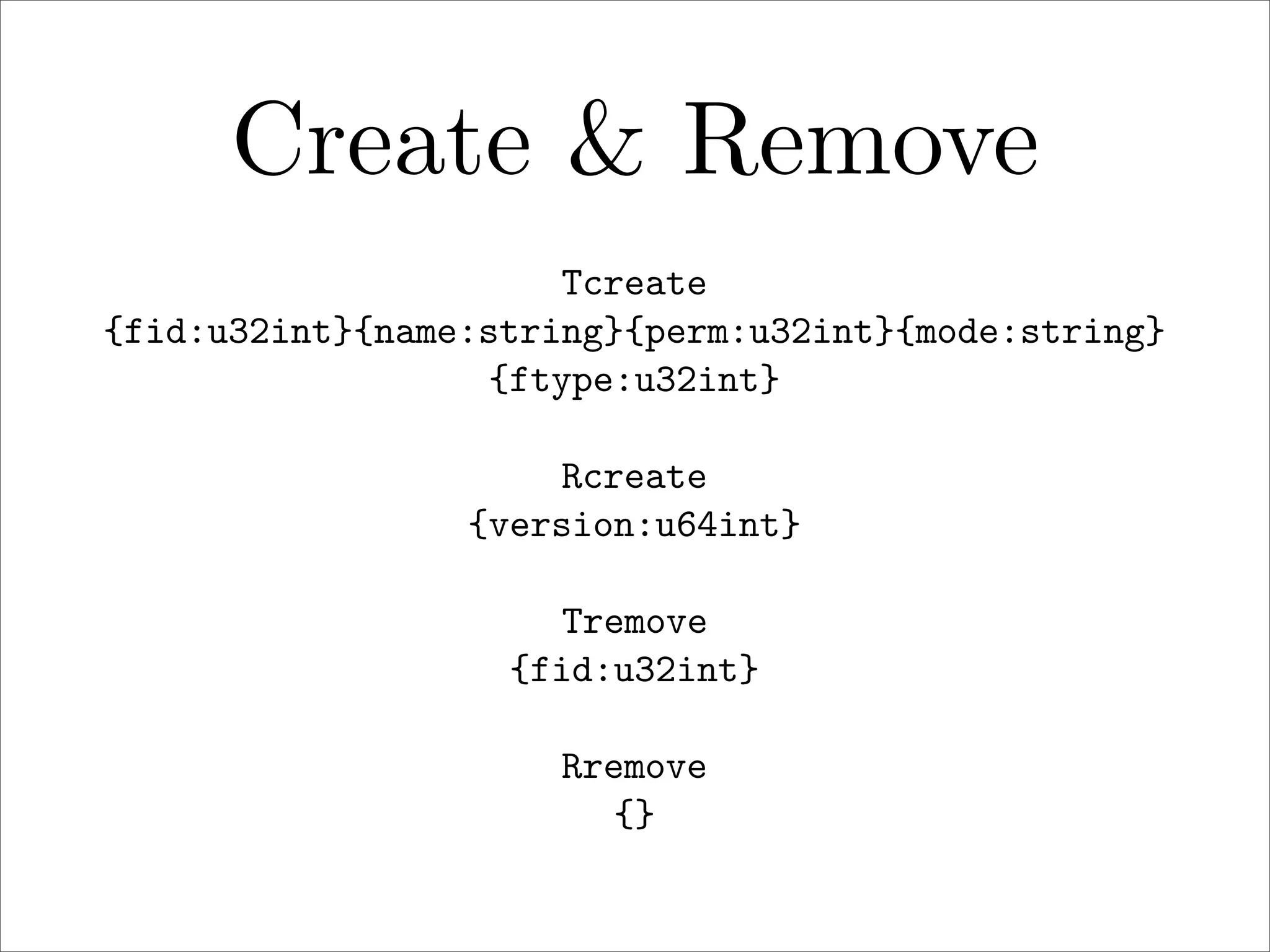
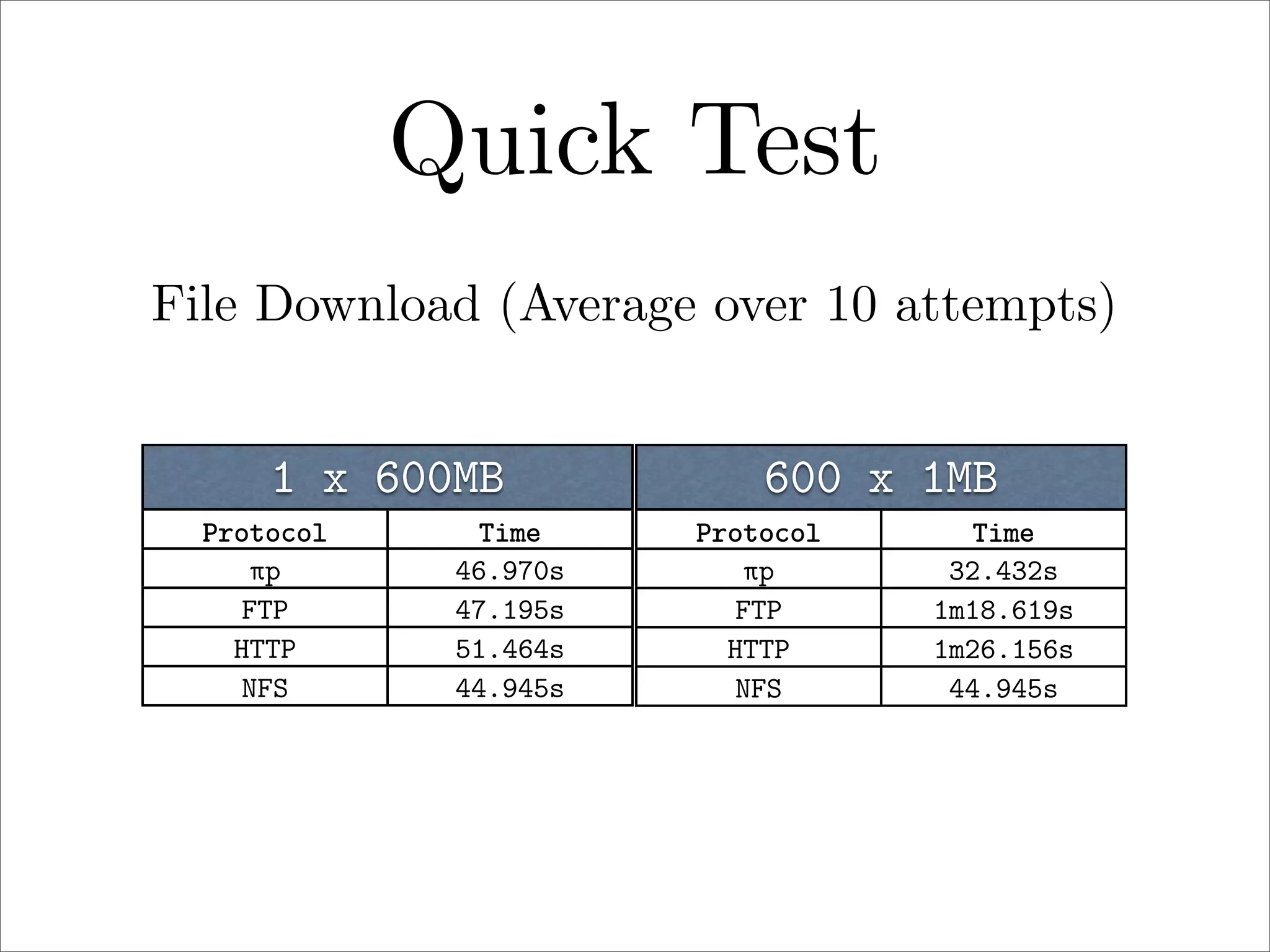
πp is a proposed new distributed file system protocol that aims to be simple, flexible, reliable, and decentralized. It represents the entire internet as a single distributed filesystem and all content is accessed via file operations. The protocol uses a request/response model with basic operations like open, read, write, create, and remove. All non-dynamic files are immutable and versioned using 64-bit timestamps. An implementation of the protocol prototype demonstrated comparable or better performance than FTP and HTTP in file transfer tests.