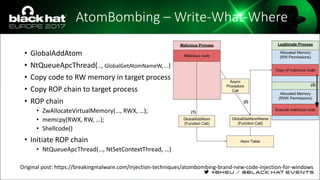
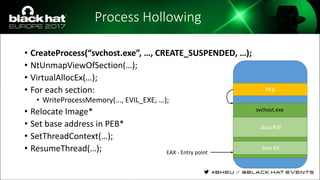
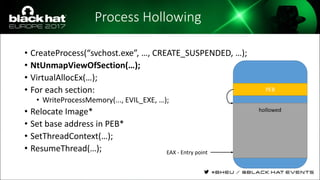
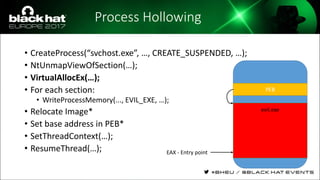
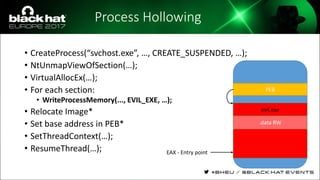
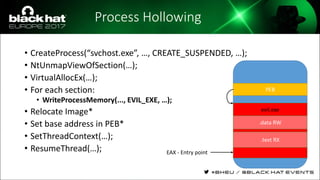
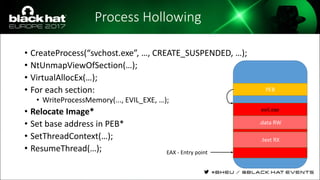
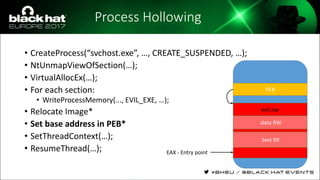
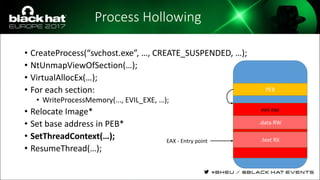
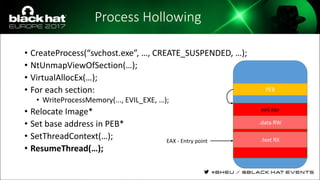
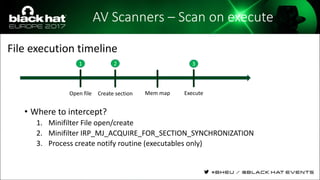
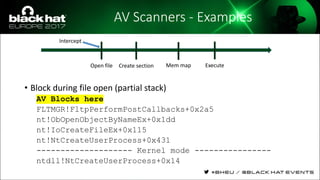
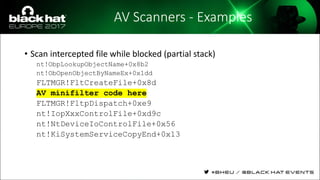
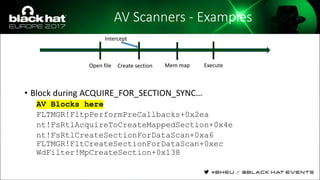
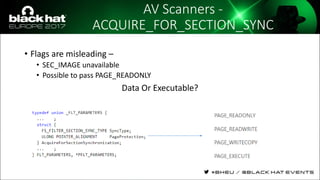
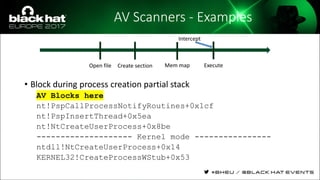
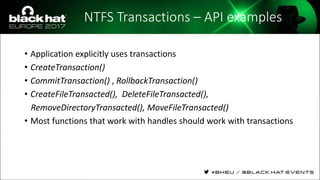
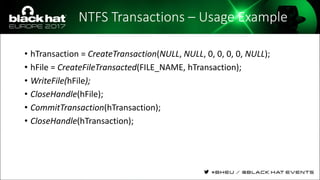
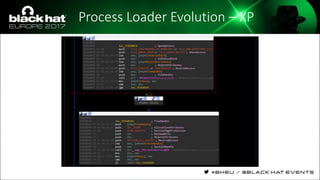
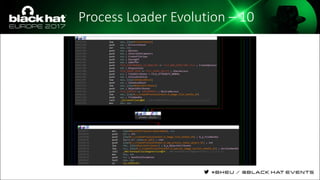
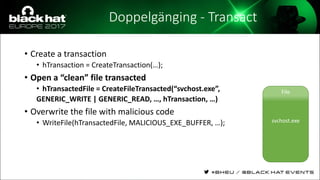
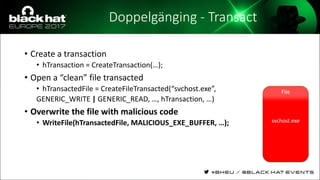
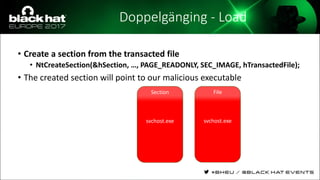
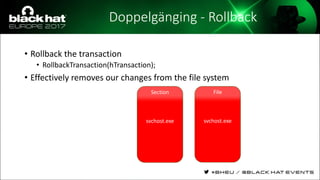
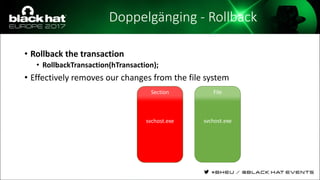
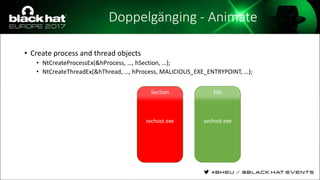
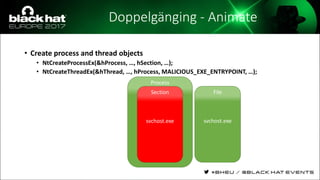
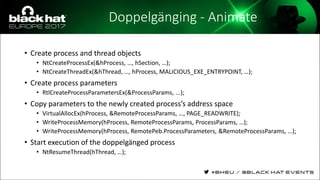
The document discusses evasion techniques used by malware to avoid detection from antivirus scanners. It provides a brief history of techniques like process hollowing and code injection methods. It then summarizes how antivirus scanners work by intercepting processes like file opening and memory mapping. The document also discusses how NTFS transactions on Windows allow for file operations to occur transactionally.


![GhostWritingA paradox: Writing to another process without opening it nor actually writing to it
• Find 2 patterns in NTDLL
• Move pattern
• mov [REG1], REG2 ; mov [eax], ebx
• ret
• Jmp pattern
• jmp 0x0 ;(eb fe)
• Write-What-Where(What, Where)
• SetThreadContext(…):
• EIP=Move pattern
• ESP=NewStack
• REG1=Where
• REG2=What
Original post by c0de90e7: http://blog.txipinet.com/2007/04/05/69-a-paradox-writing-to-another-process-without-openning-it-nor-actually-writing-to-it/](https://image.slidesharecdn.com/eu-17-liberman-lost-in-transaction-process-doppelganging-180507203036/85/Process-Doppelganging-6-320.jpg)