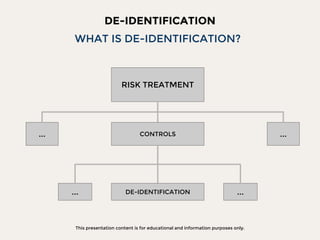
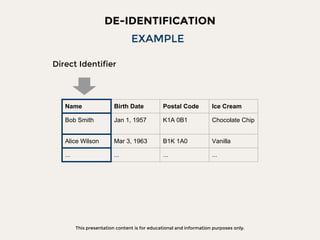
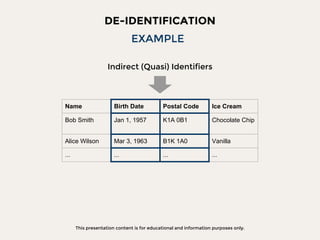
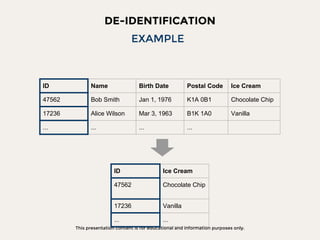
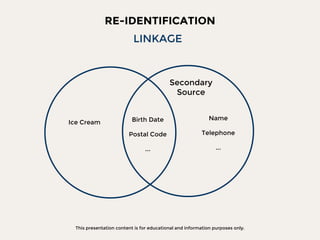
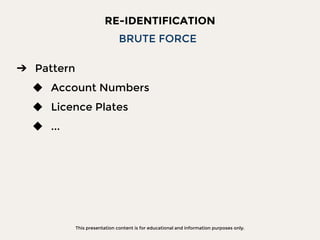
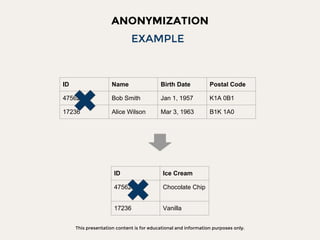
The document discusses data privacy focusing on de-identification and anonymization techniques, emphasizing the importance of removing personal identifiers to protect individuals' privacy. It outlines processes, challenges, and examples of both de-identification, which is reversible, and anonymization, which is irreversible. Additionally, it covers risk management and references relevant studies and guidelines in the field.