Embed presentation
Downloaded 30 times


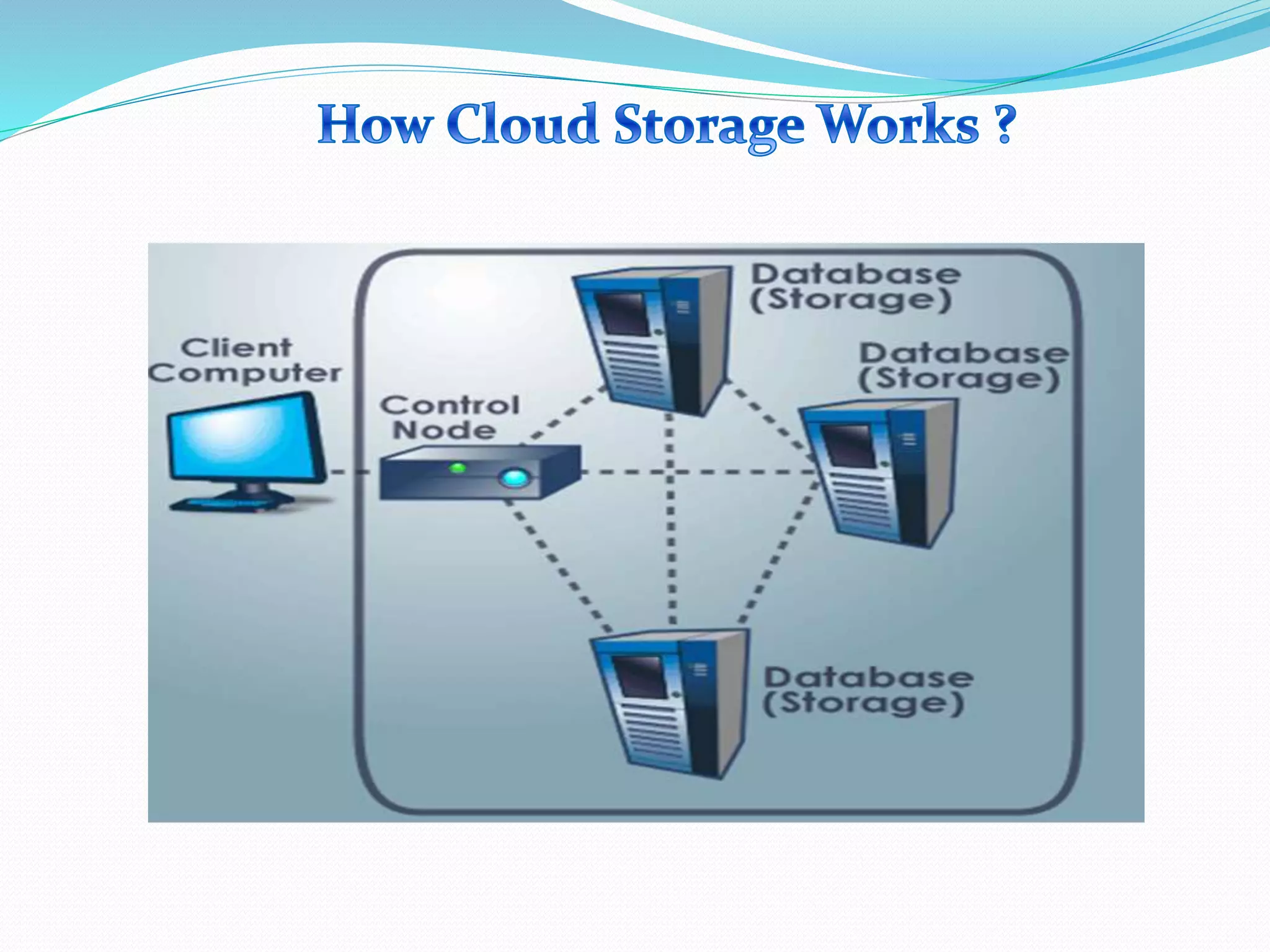



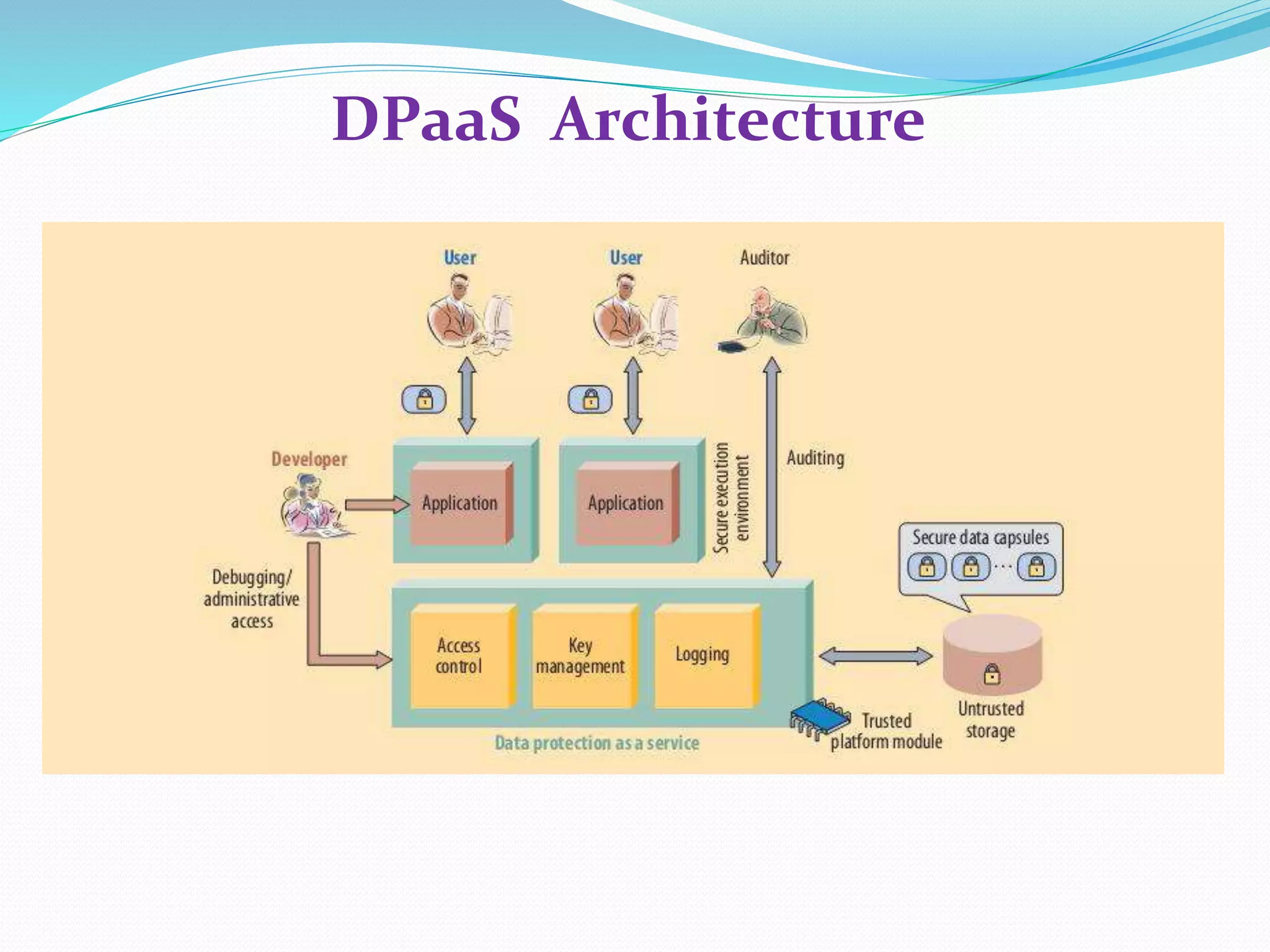
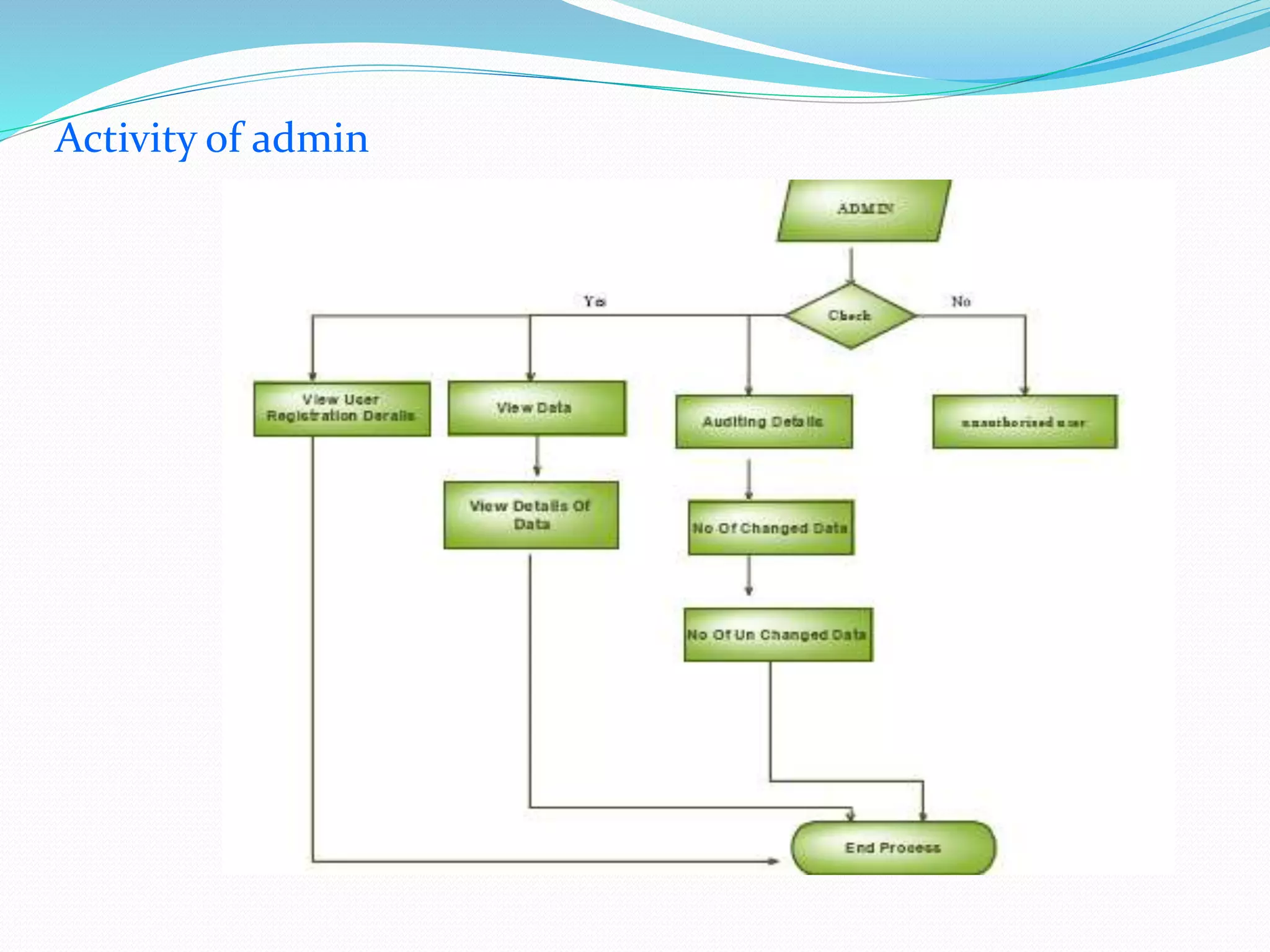
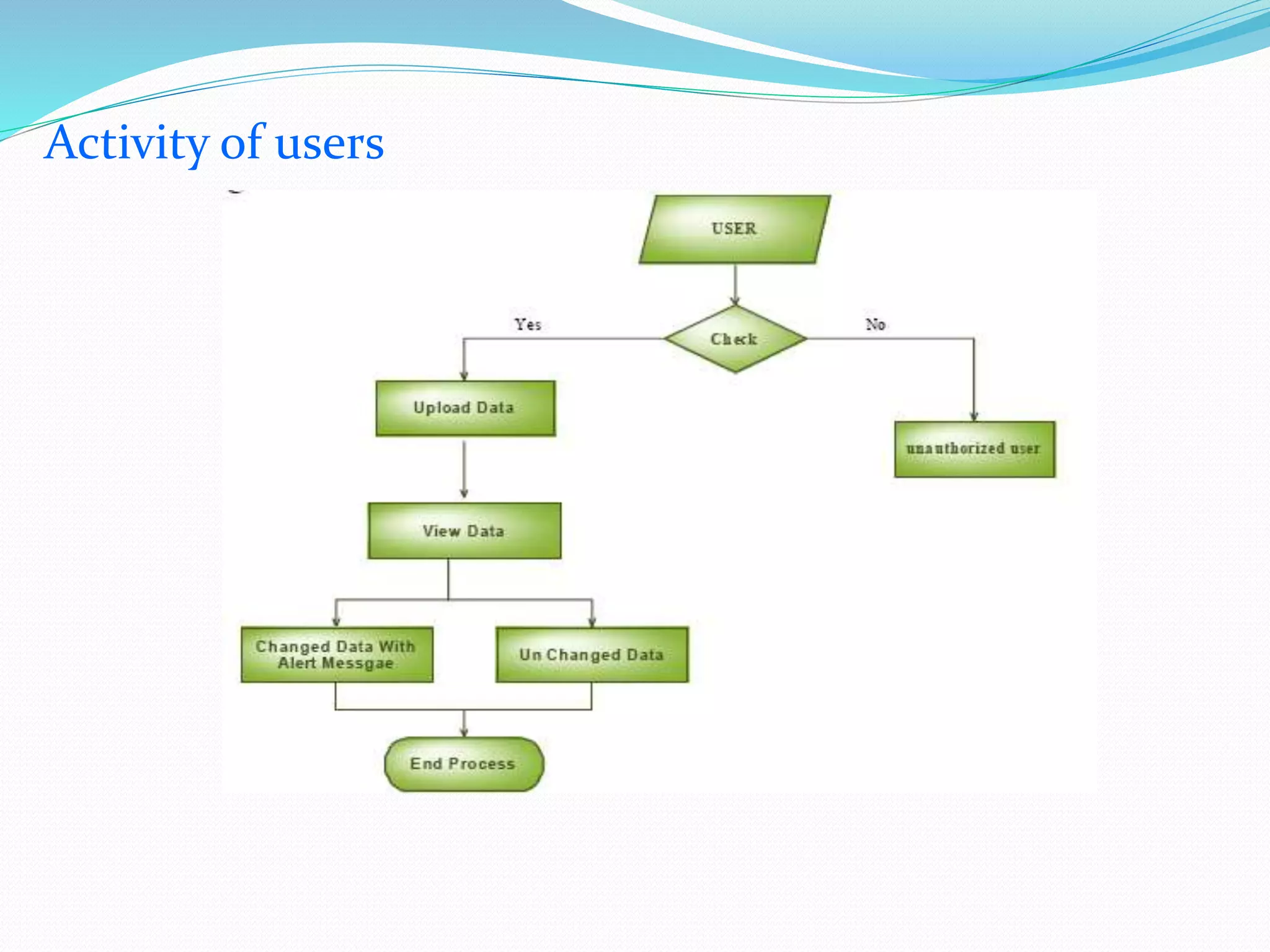
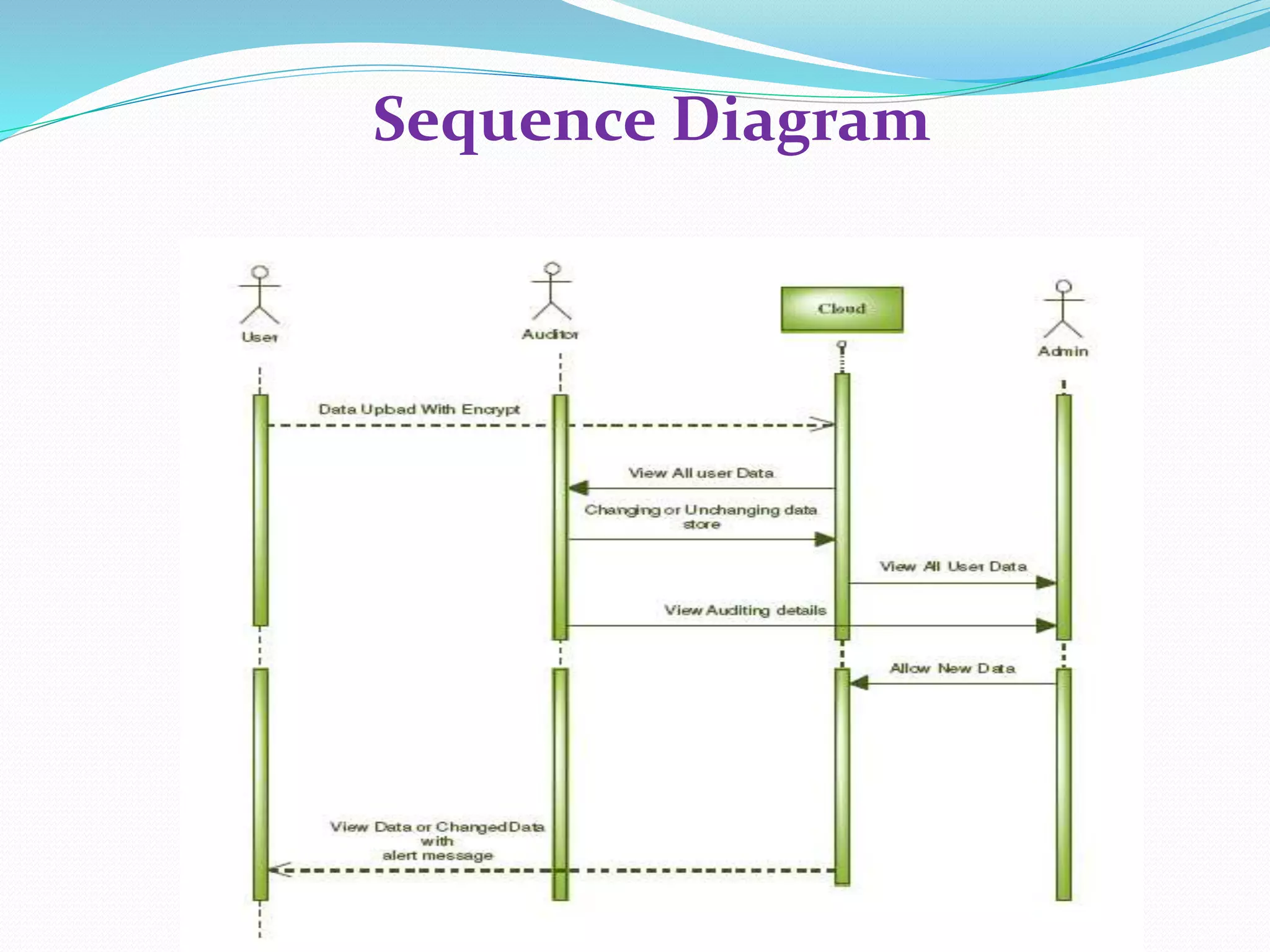


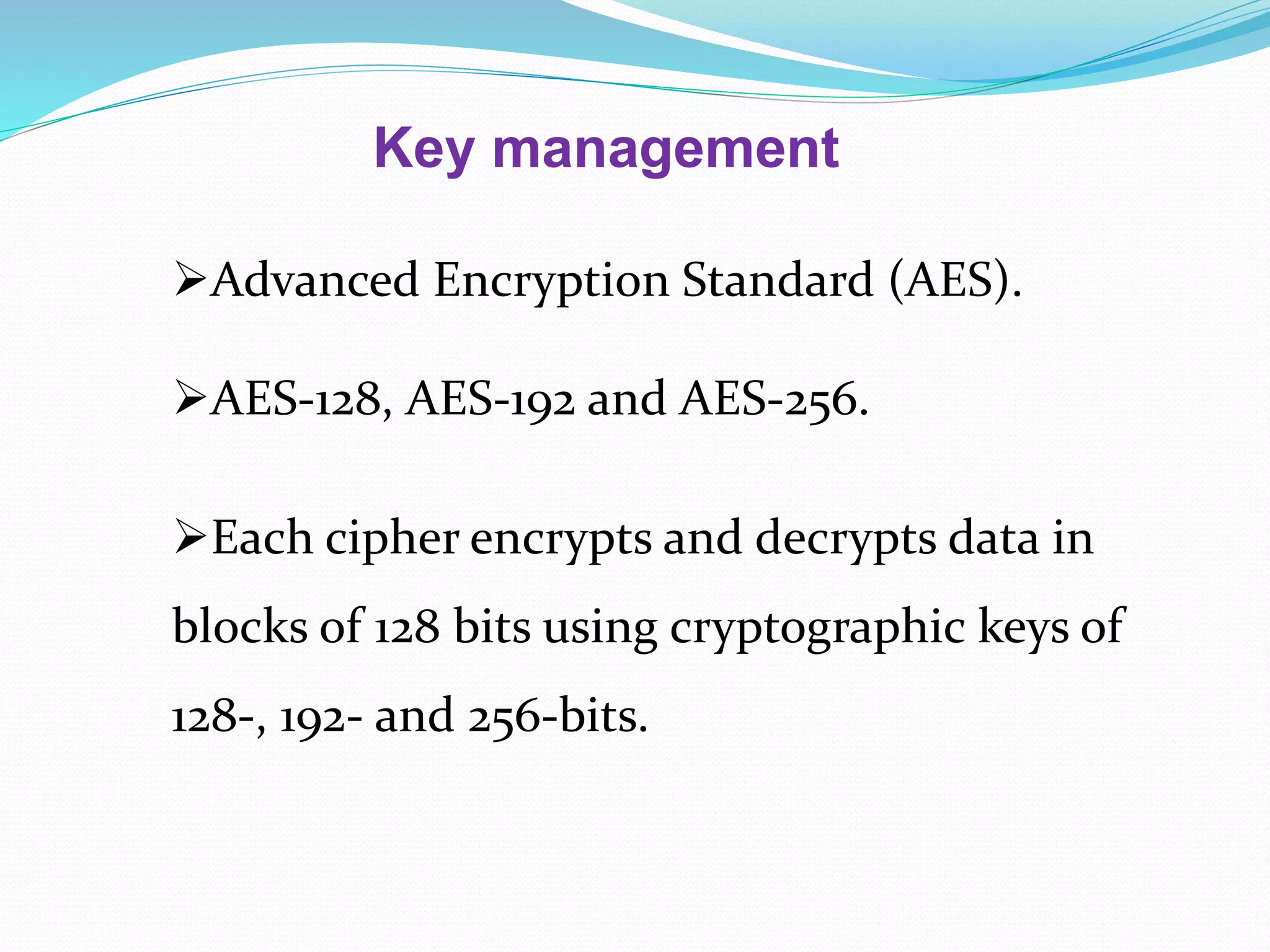


The document discusses cloud computing, highlighting its benefits such as lower costs and accessibility, but also notes concerns about security and privacy among users. It proposes a new system called Data Protection as a Service (DPaaS) that aims to enhance data security through access control, logging, and auditing. The conclusion emphasizes the importance of protecting cloud users' data and ensuring secure execution environments.














