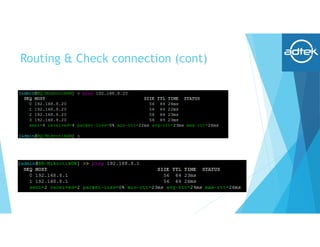
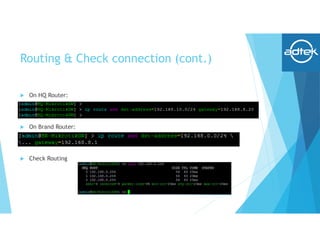
This document summarizes how to set up an OpenVPN connection between a headquarters Mikrotik router and a branch office Mikrotik router to allow secure connectivity between their networks. It describes generating certificates on the HQ router, setting up the HQ router as an OpenVPN server, configuring the branch router as an OpenVPN client, and verifying the routing and connection between the two sites.