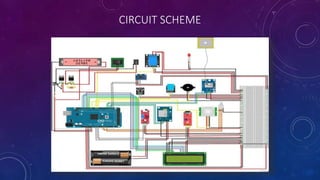
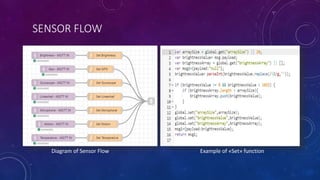
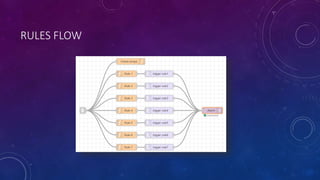
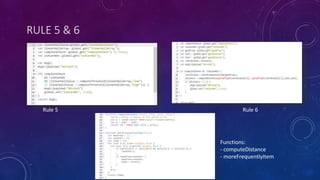
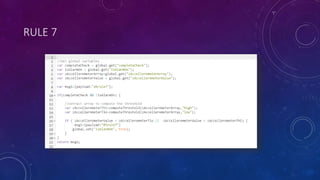
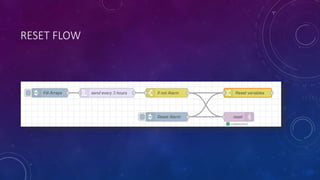
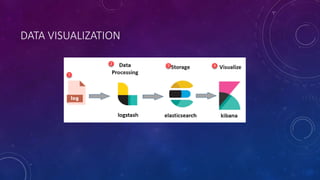
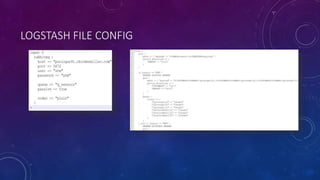
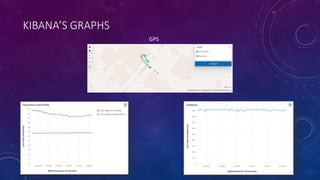
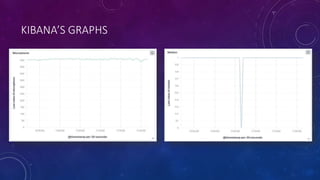
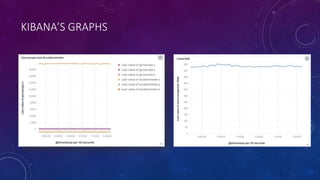
The document describes a project to simulate a secure ATM using an Arduino board and sensors to detect two potential attack scenarios: 1) physical access of the ATM's internal components, and 2) removing the entire ATM from its location. The system uses an Arduino board connected to various sensors to monitor for threats. If sensor readings match rules indicating a threat, an alarm is triggered. RabbitMQ and Node-RED are used to process sensor data in real-time and evaluate the rules. Kibana visualizes the sensor data for analysis. The goal is to prototype an IoT-based security system to protect ATMs from physical attacks.