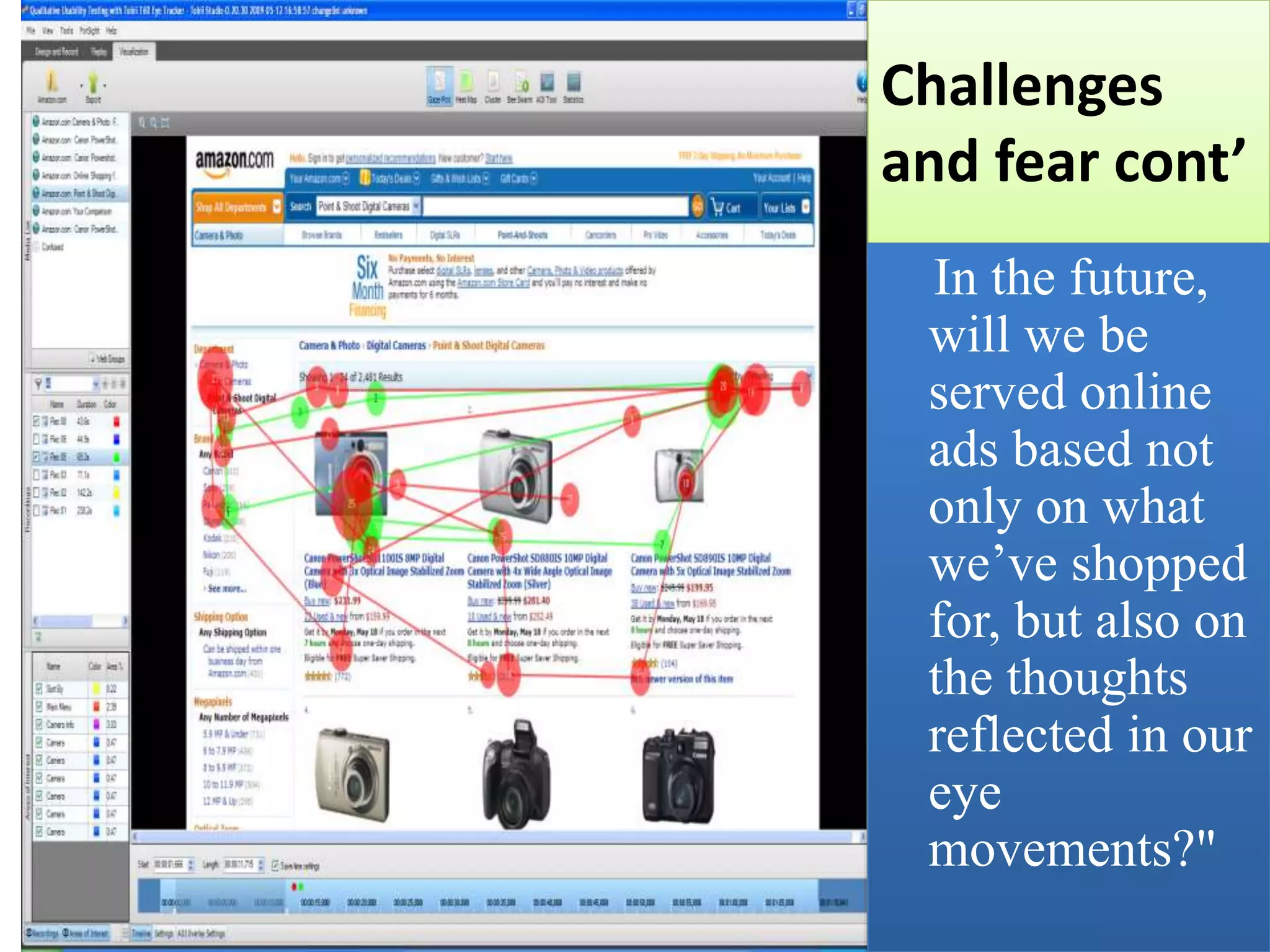
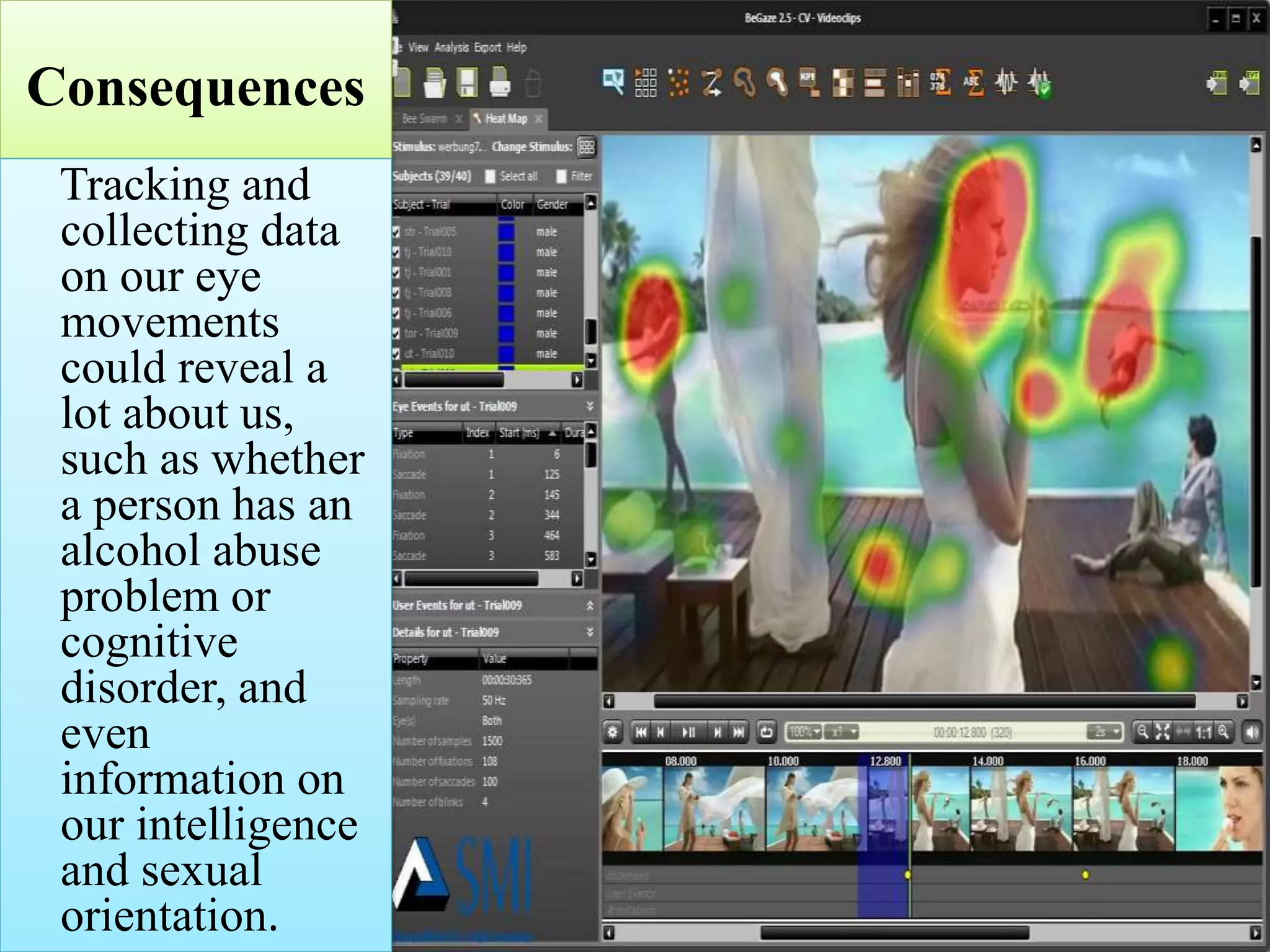
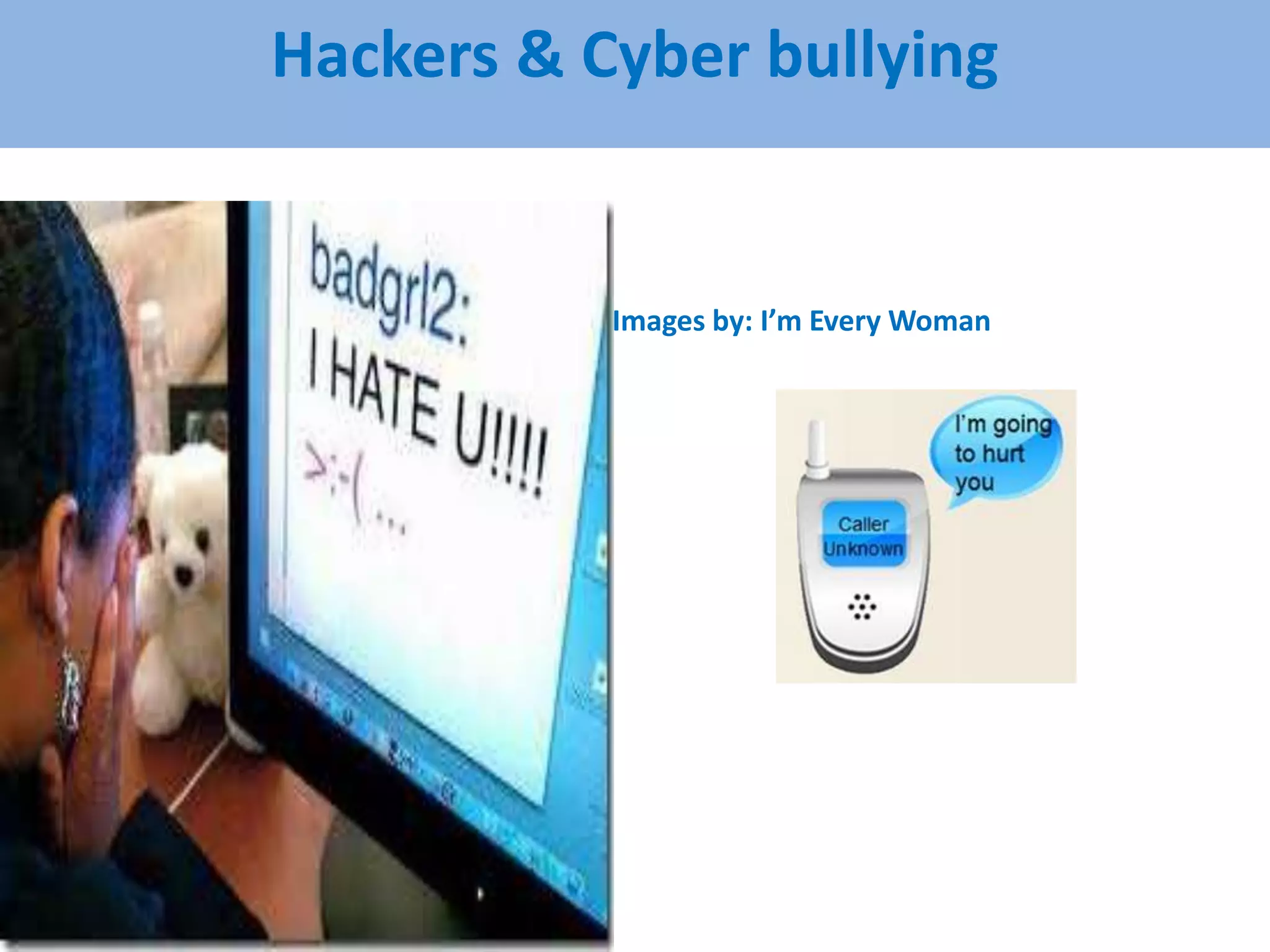
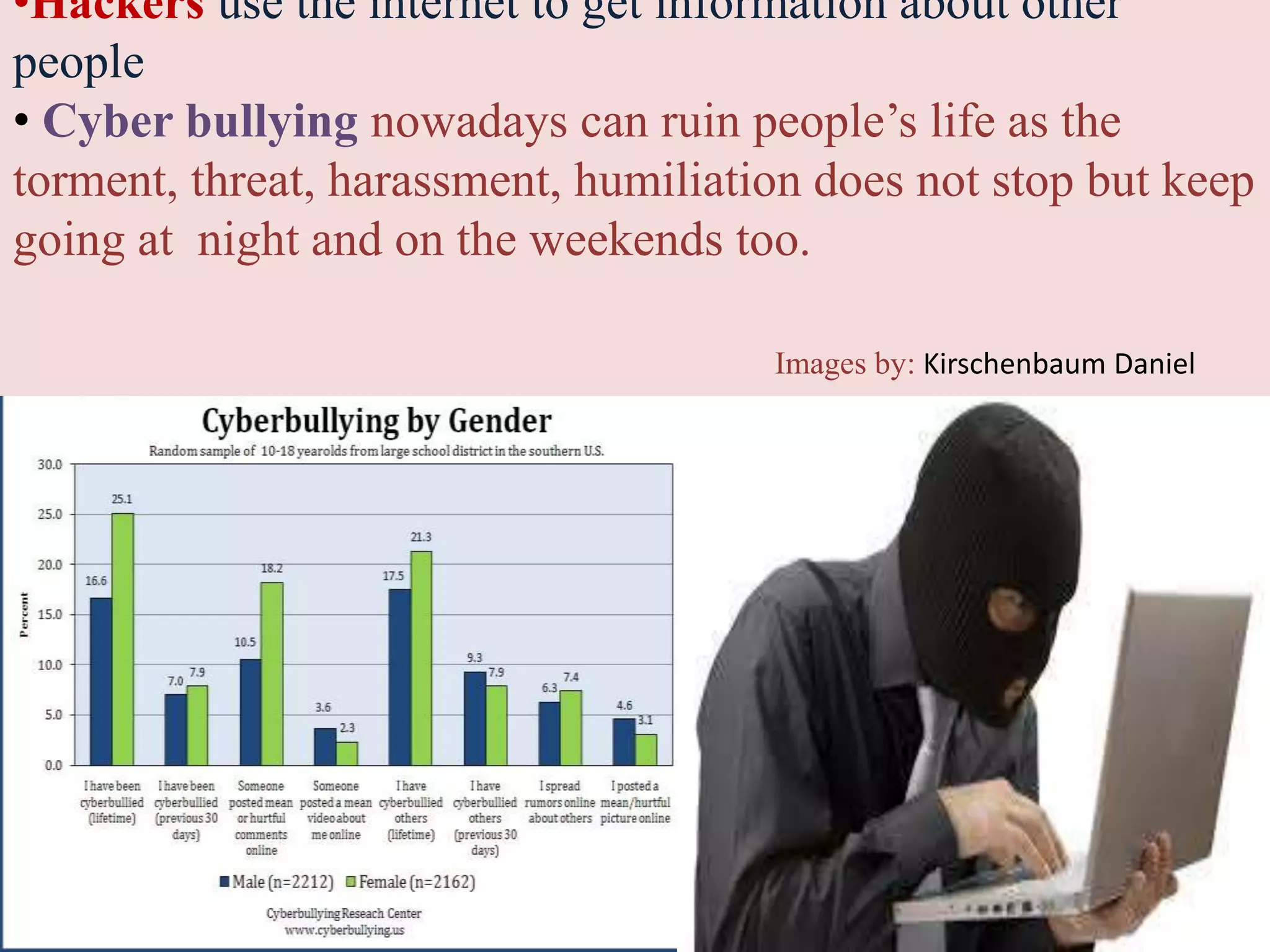
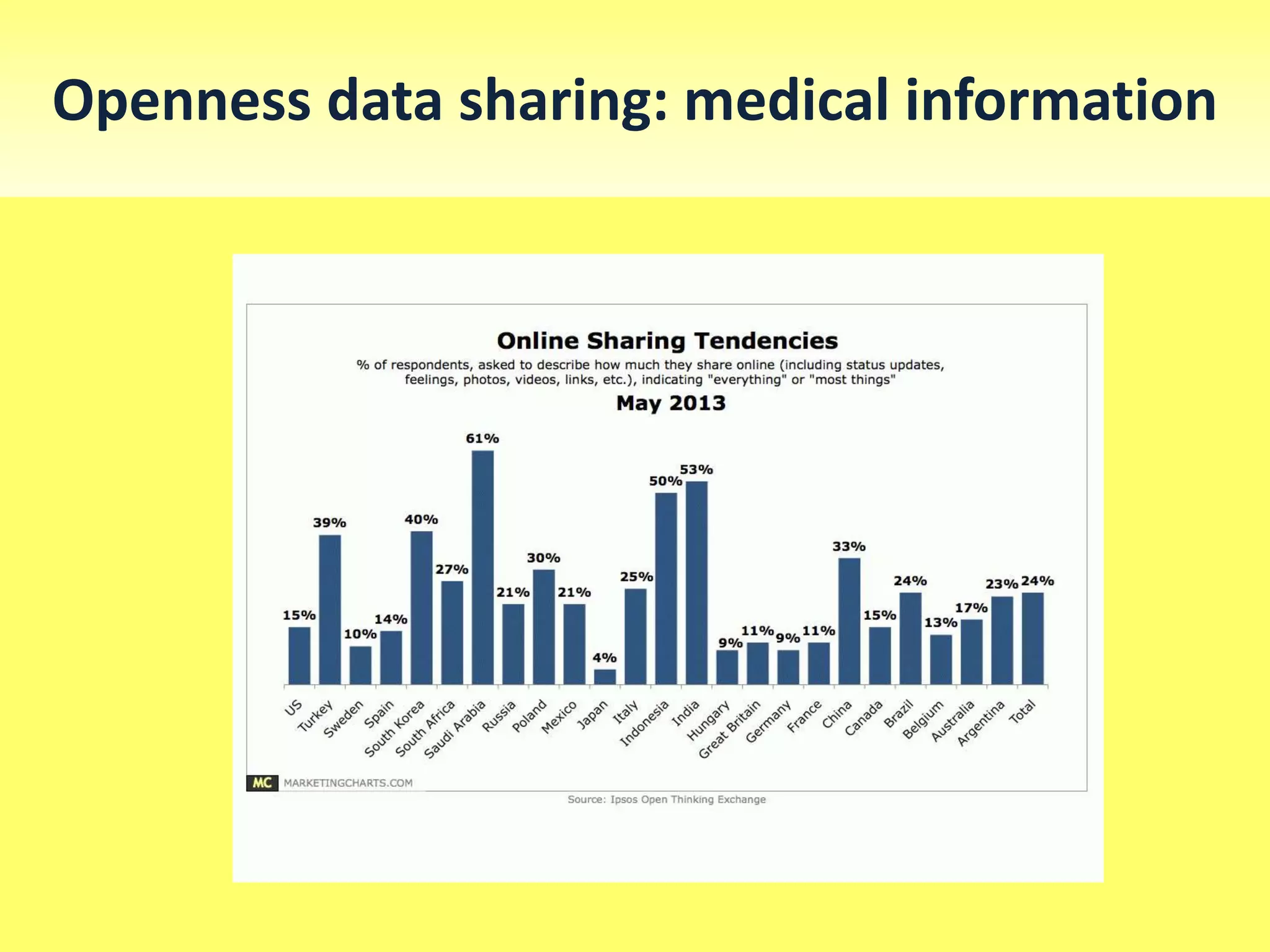
This document discusses privacy and security concerns regarding social media and the internet. It explores how personal information shared online can be tracked and used in ways that people may not expect. This includes information gathered through social media profiles, public records, and emerging technologies like eye tracking. The document warns that whatever is posted online can potentially follow people for many years. It also examines issues like cyberbullying, online harassment, and how future employers may judge people based on their digital profiles and online activities. Overall, the document analyzes challenges to privacy as internet use grows and more personal data is collected, shared and available publicly.