Embed presentation
Downloaded 14 times



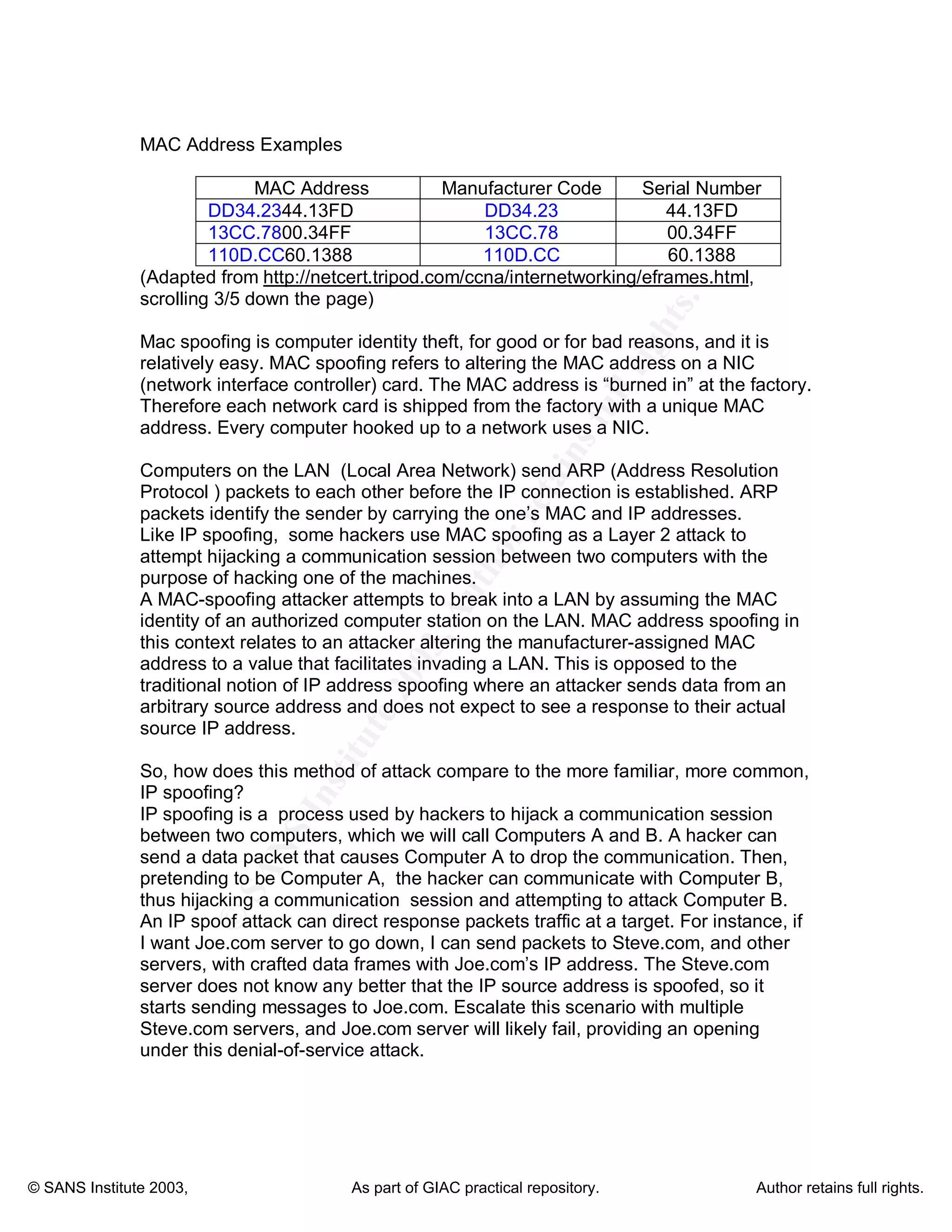


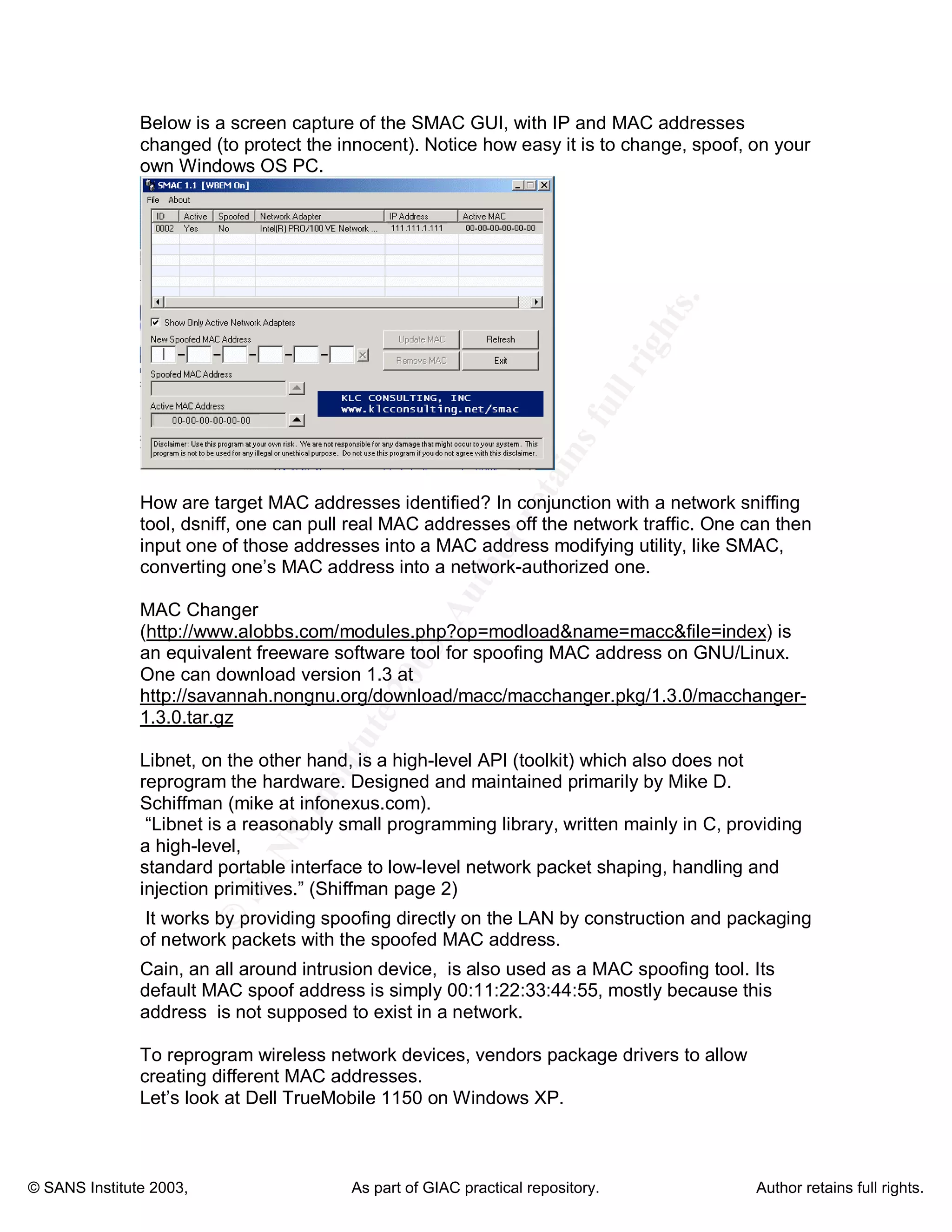

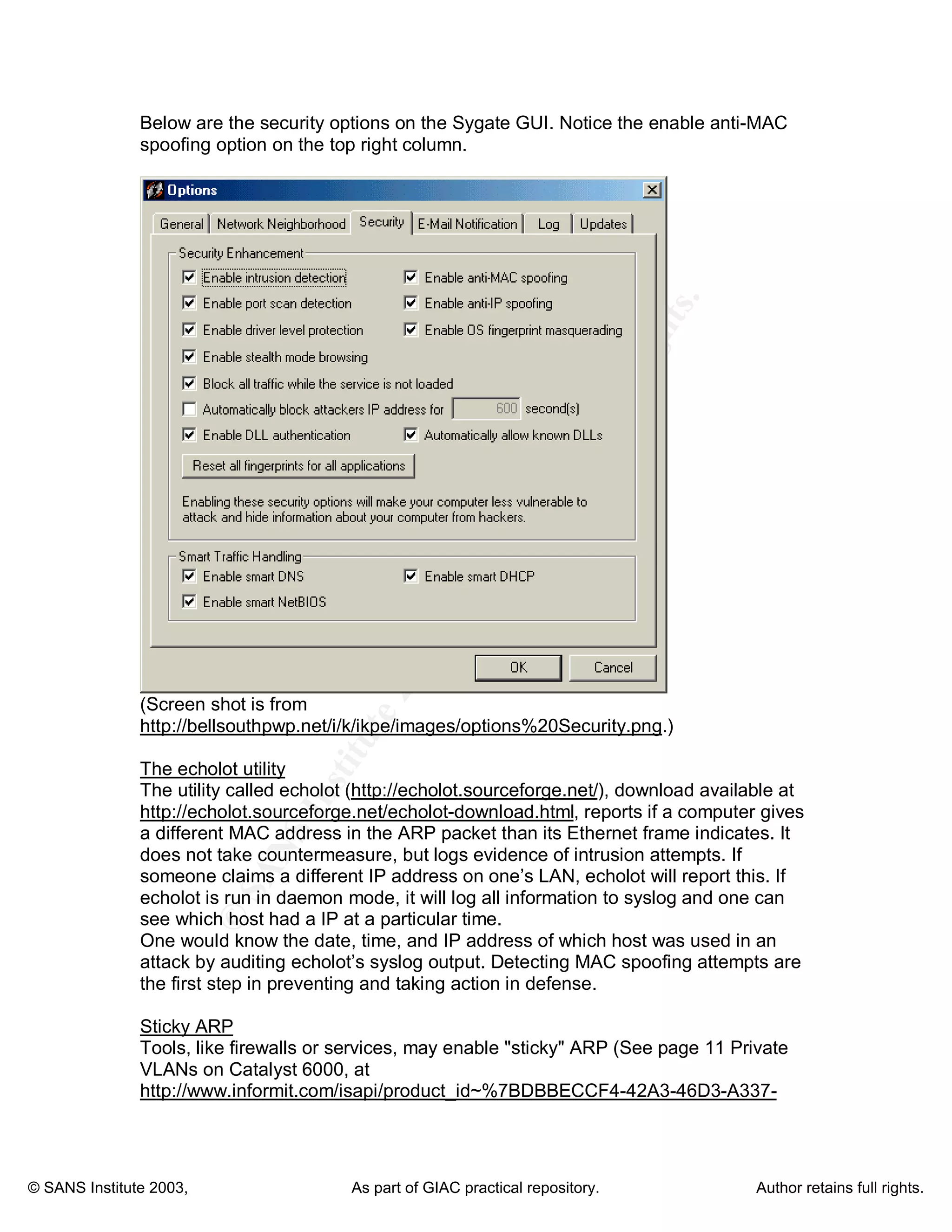





MAC spoofing is the act of altering the media access control (MAC) address of a network interface to disguise a machine's identity. The document discusses how MAC spoofing works, why people use it, how to prevent it, and its advantages for penetration testing. It notes that while less publicized than IP spoofing, MAC spoofing provides a powerful and versatile tool for breaking into networks or penetration testing due to the ability to bypass MAC address filtering and impersonate other devices.












