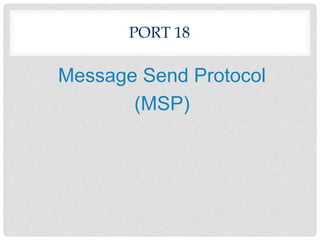
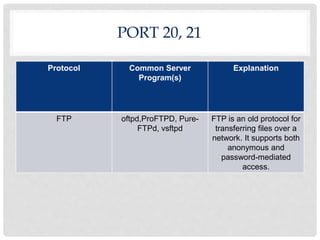
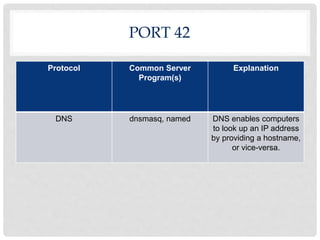
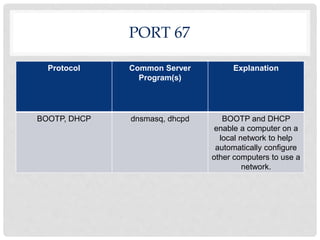
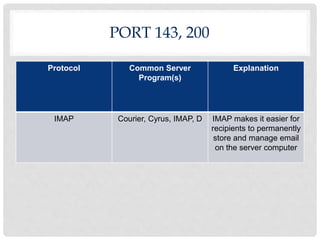
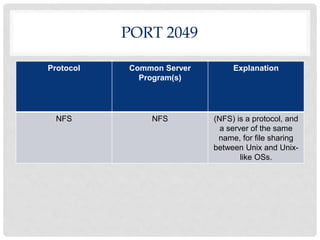
Ports are numbered resources that identify the protocol being used to transfer data over a network. Some common ports and their purposes include:
Port 80 for HTTP, which is the basis of the World Wide Web. Port 22 for SSH, which allows for encrypted remote access and file transfers. Port 25 for SMTP, which is the main protocol for moving email on the Internet.