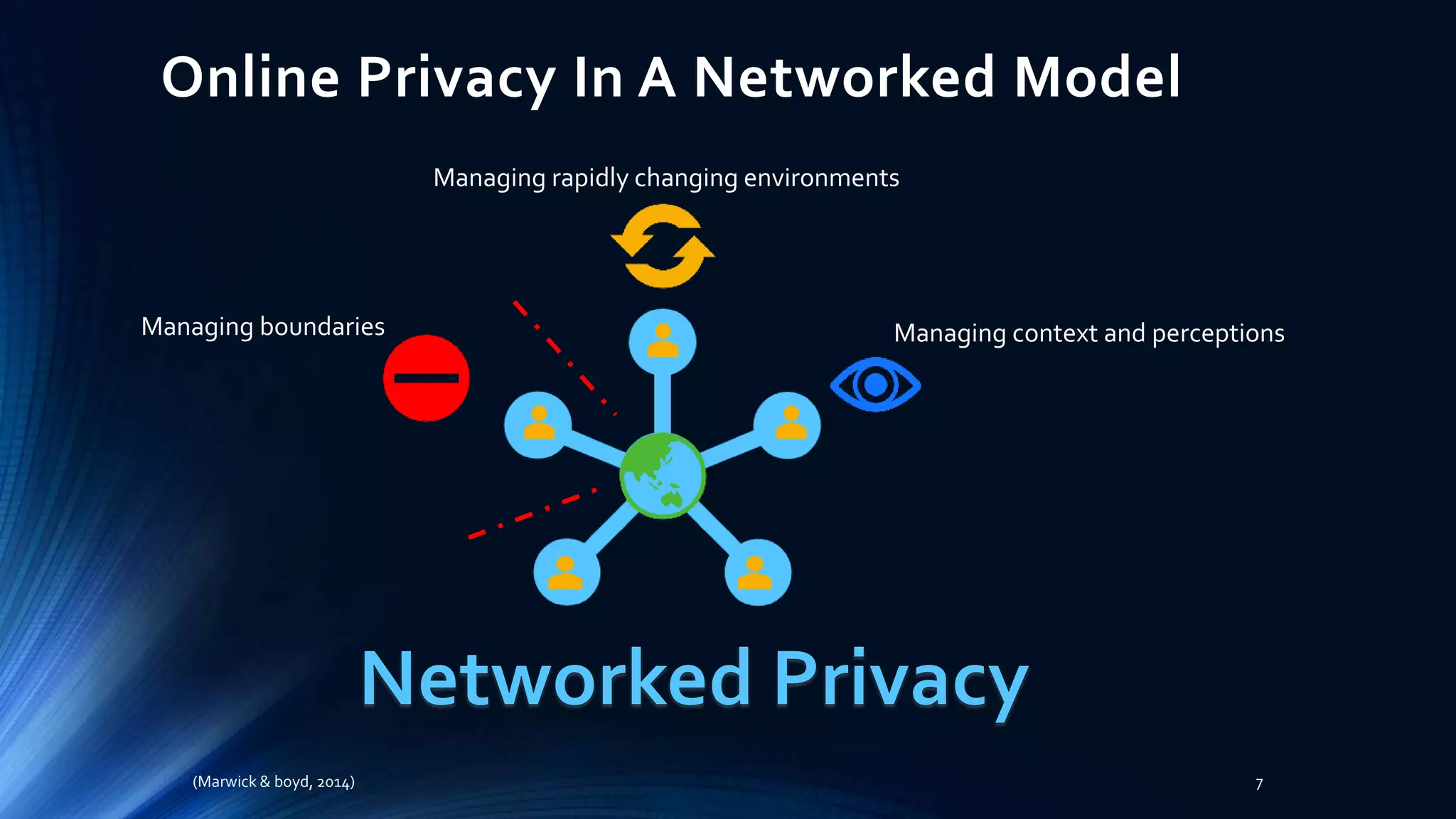
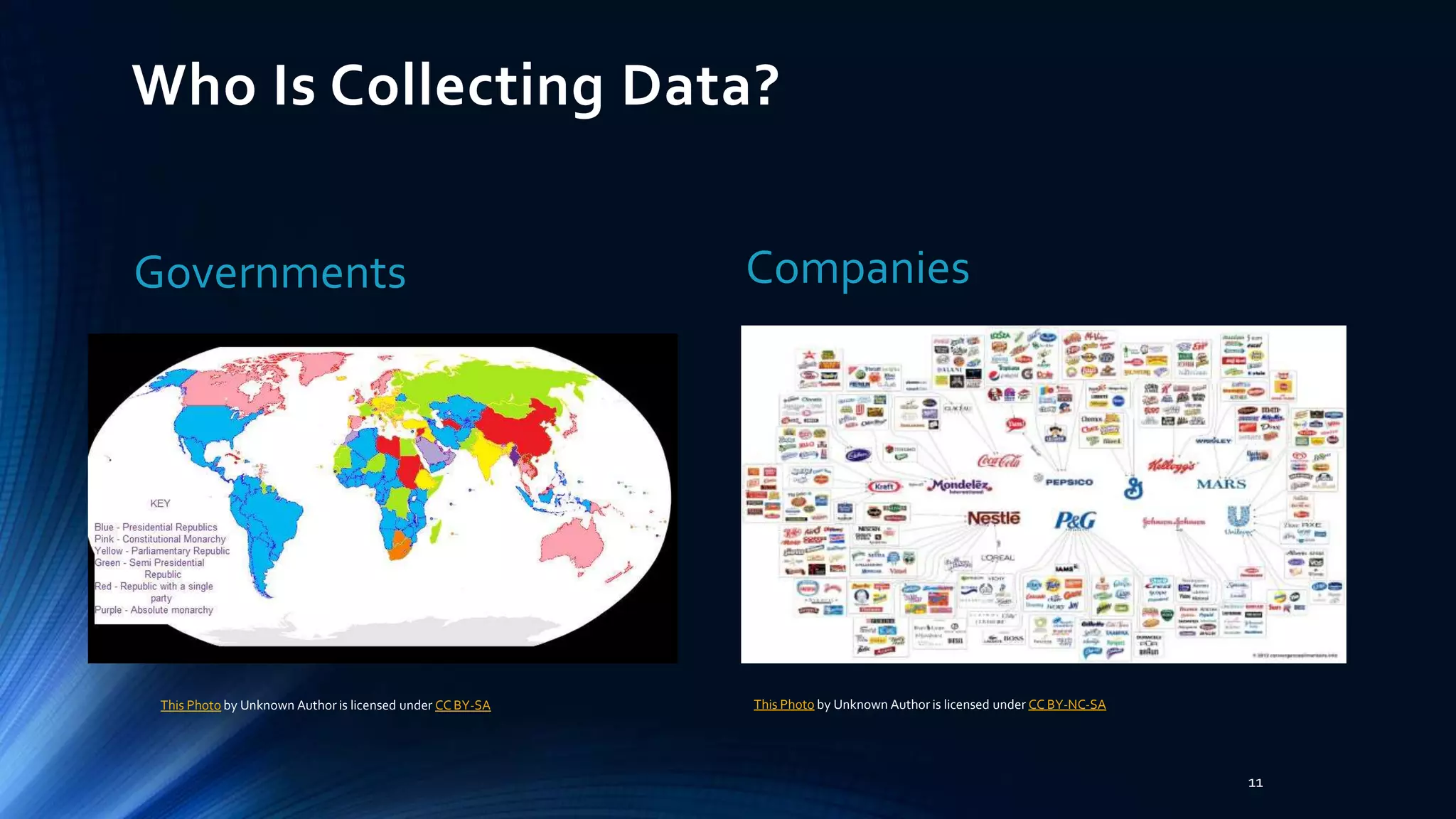
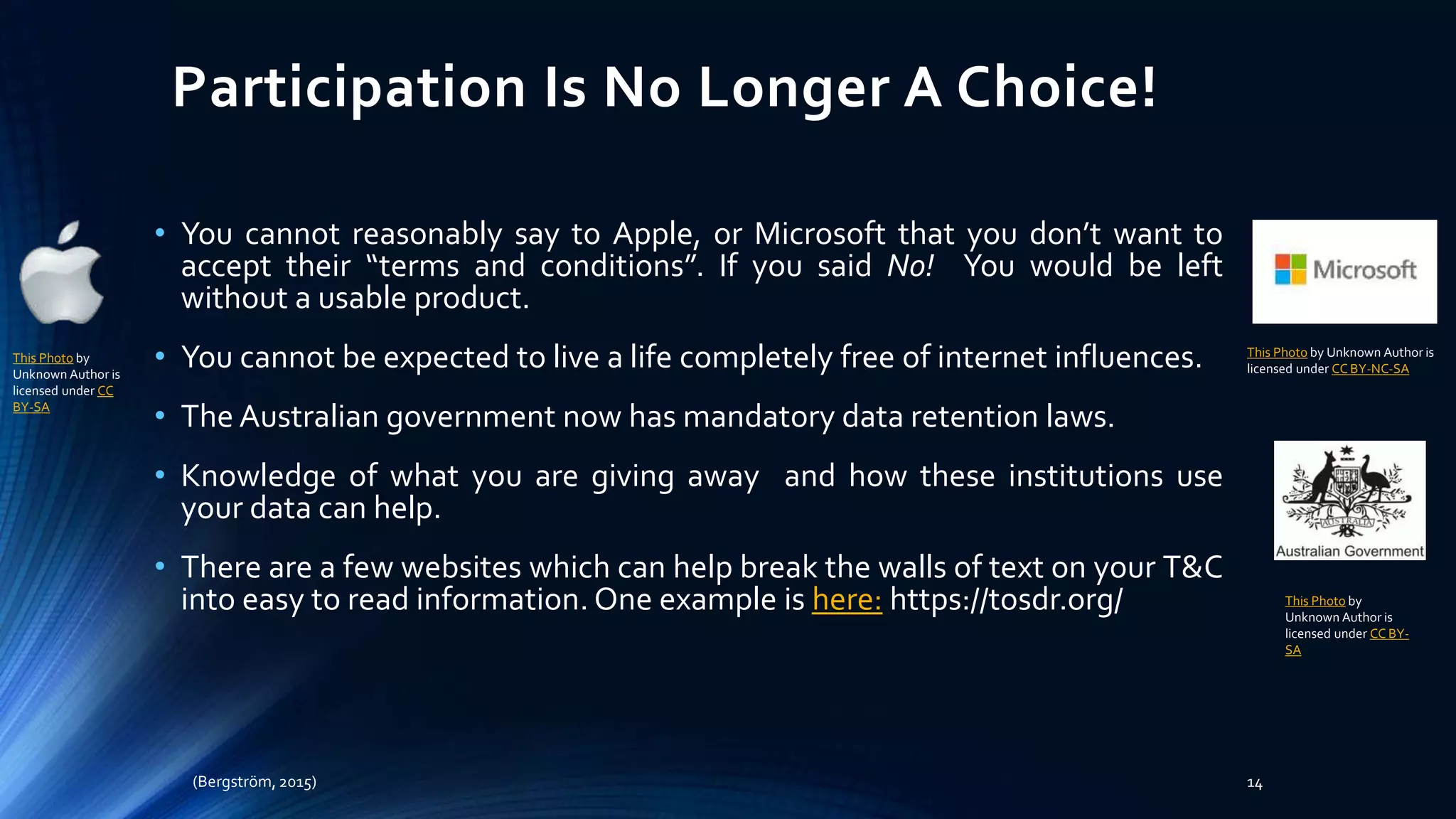
The document discusses the implications of online privacy, emphasizing that it affects everyone due to changes in how data is monitored and accessed. It highlights the complexities of privacy in a networked world, where personal information is often collected without consent and shared through 'terms of use.' Experts predict that while connectivity will continue to deepen, concerns about privacy and data misuse remain significant.












![Some Further Reading On The Topic Of This Policy Primer.
• Bergström, A. (2015). Online privacy concerns: A broad approach to understanding the concerns of different
groups for different uses. Computers in Human Behavior, 53, 419-426. doi:10.1016/j.chb.2015.07.025
• Duggan, M. (2017). Online Harassment 2017. Retrieved 16 Sep 17, from @pewinternet
http://www.pewinternet.org/2017/07/11/online-harassment-2017/
• Lessig, L. (1988). The Architecture of privacy. Paper presented at theTaiwan Net 1998,Taipei.
https://cyber.harvard.edu/works/lessig/architecture_priv.pdf
• Marwick, A. E., & boyd, d. (2014). Networked privacy: How teenagers negotiate context in social media. New
Media & Society, 16(7), 1051-1067. doi:10.1177/1461444814543995
• Prothman, B. (2000). Meta data. Potentials, IEEE, 19(1), 20-23. doi:10.1109/45.825636
• Rainie, L. A., Janna. (2017).The Internet ofThings Connectivity Binge: What Are the Implications? Retrieved
2017-06-06, from @pewinternet http://www.pewinternet.org/2017/06/06/the-internet-of-things-connectivity-
binge-what-are-the-implications/
• Westerman, H. a. J., Emil (Producer). (2014, 15 Oct 17). Metadata and data retention: what information is at
risk? . [Online Media presentation] Retrieved from
https://www.sbs.com.au/news/article/2014/08/08/infographic-metadata-and-data-retention-explained
16](https://image.slidesharecdn.com/policyprimernet303studyperiod32017-171016090600/75/Policy-primer-net303-study-period-3-2017-16-2048.jpg)
