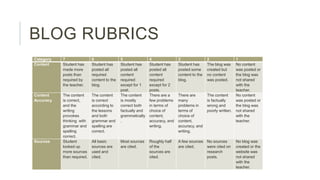
This document outlines an agenda for a class on phishing and internet security. It includes rubrics for grading blog posts and productivity. The agenda has sections on discussing phishing, protecting from phishing, and an assignment where students will create an internet security handbook for different groups. Students will then present and work on the assignment in pairs or trios.