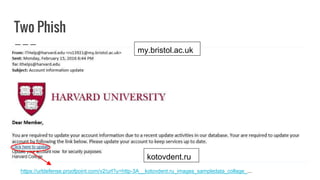
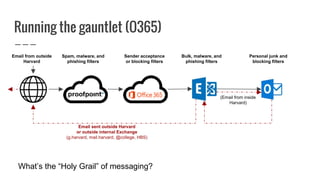
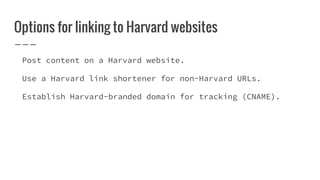
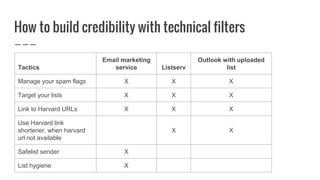
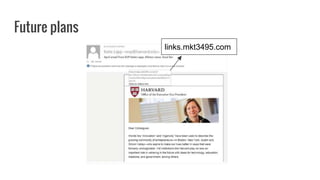
This document discusses best practices for crafting effective email communications while avoiding phishing risks. It provides tips for increasing email credibility and engagement, including: safely linking to external URLs, maintaining clean mailing lists, using a consistent branded template, and educating recipients to recognize phishing attempts. The document also describes Harvard's technical filters for blocking spam and phishing, and case studies how the Executive Vice President's newsletter incorporated these practices into its successful email marketing.