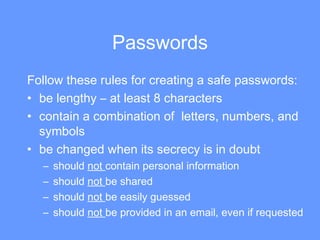
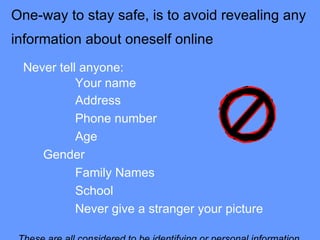
This document provides a summary of a personal safety unit that teaches students about safe online practices. The unit contains four mini lessons: 1) choosing secure screen names and passwords, 2) protecting personal information, 3) dealing with online strangers and predators, and 4) reviewing online safety. The lessons emphasize not including personal details that could reveal one's identity in screen names or passwords. Students are warned about sharing private information or meeting strangers from the internet. Reporting any uncomfortable interactions to parents or authorities is strongly encouraged.






![Screen Names Screen names should never contain or refer to: first and/or last name address phone number date of birth (complete or partial) or age social security number email address combinations of personal information such as listed above combinations of personal information such as listed above plus descriptions such as (but not limited to ) gender, school name, favorite sport, favorite celebrity, family member names [email_address] marcy14inSanFran tiger1234](https://image.slidesharecdn.com/personalsafetygr5unitppt-110526112117-phpapp01/85/Personal-safety-gr5-unit-ppt-7-320.jpg)