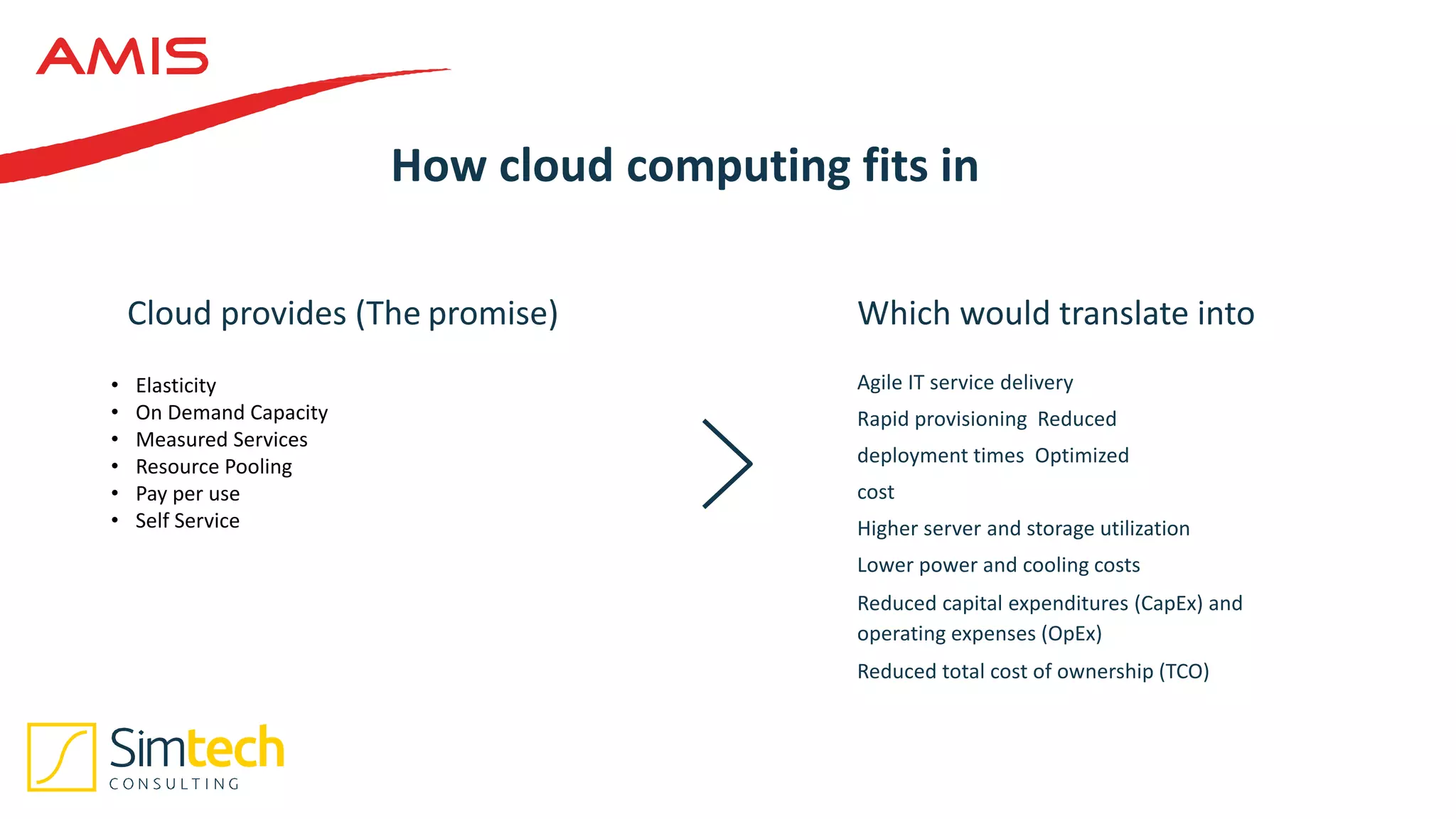
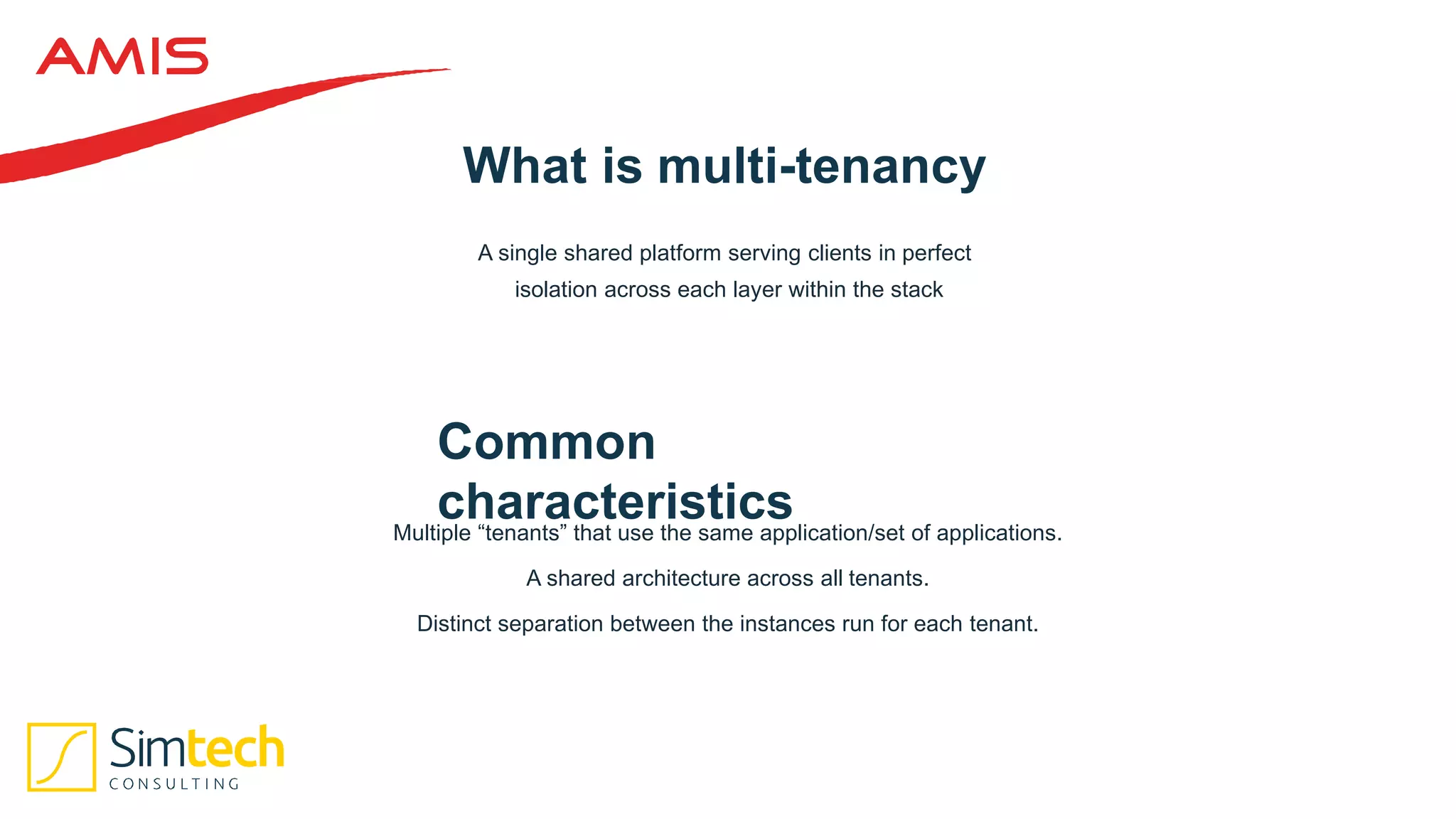
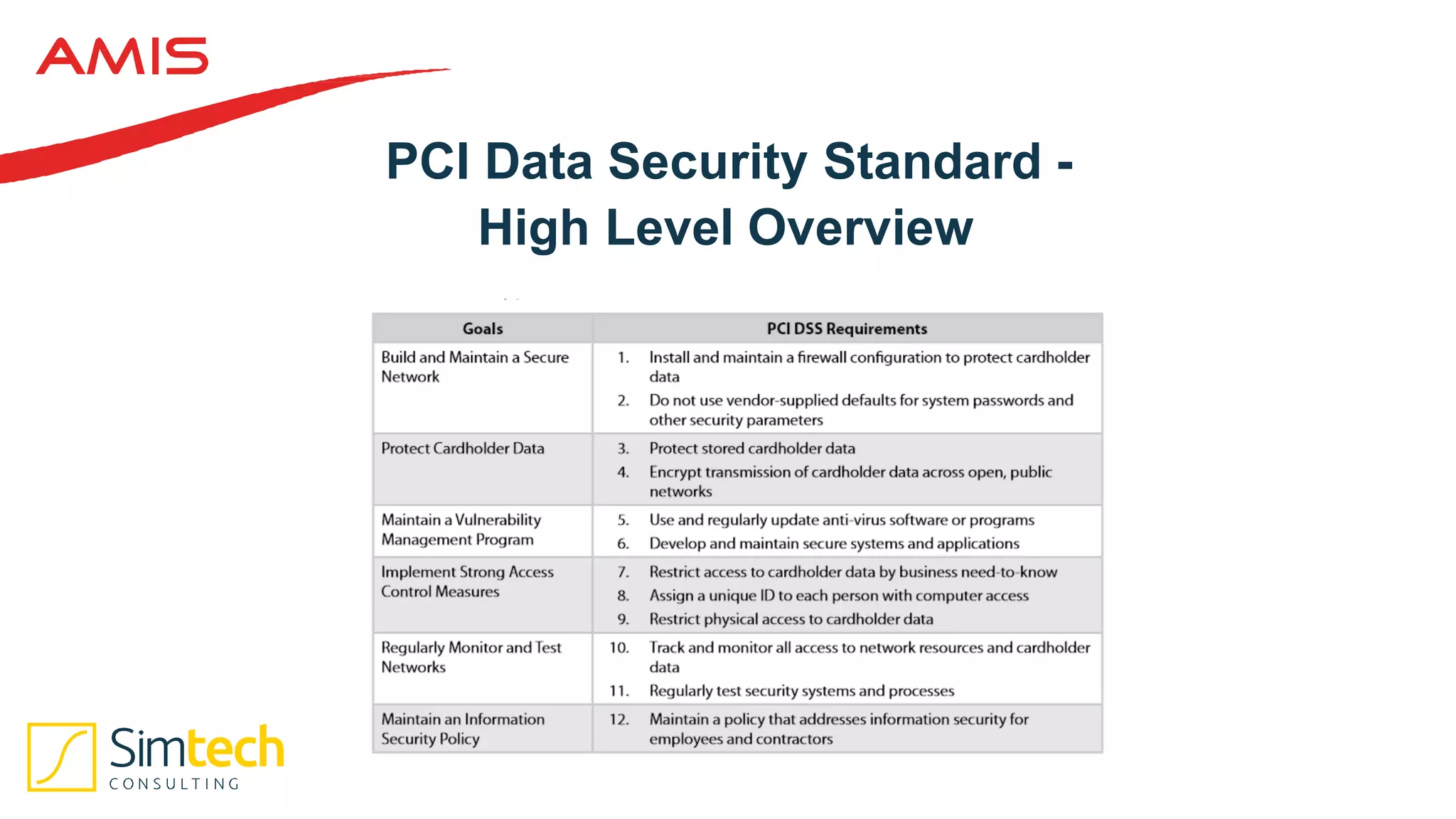
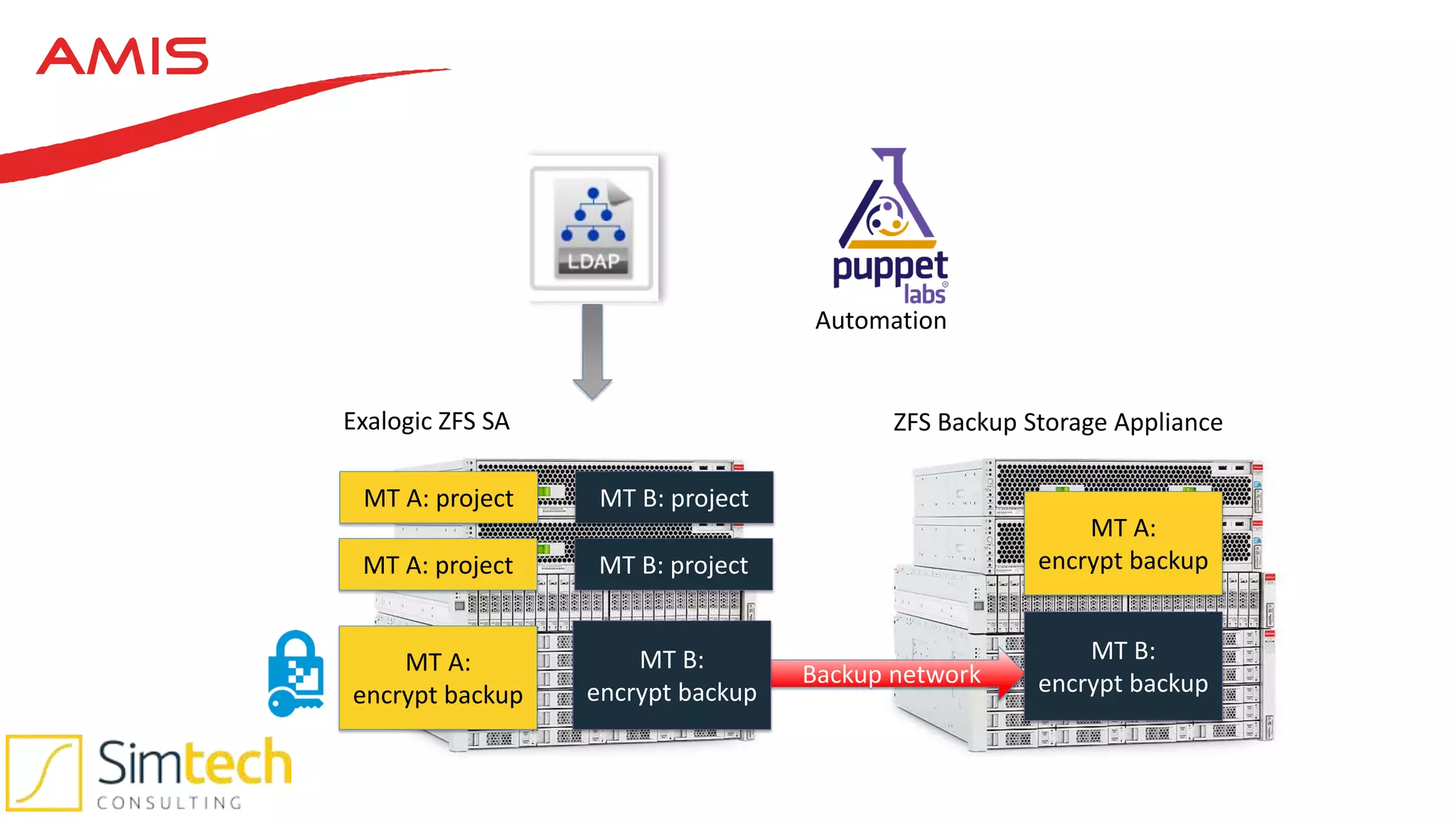
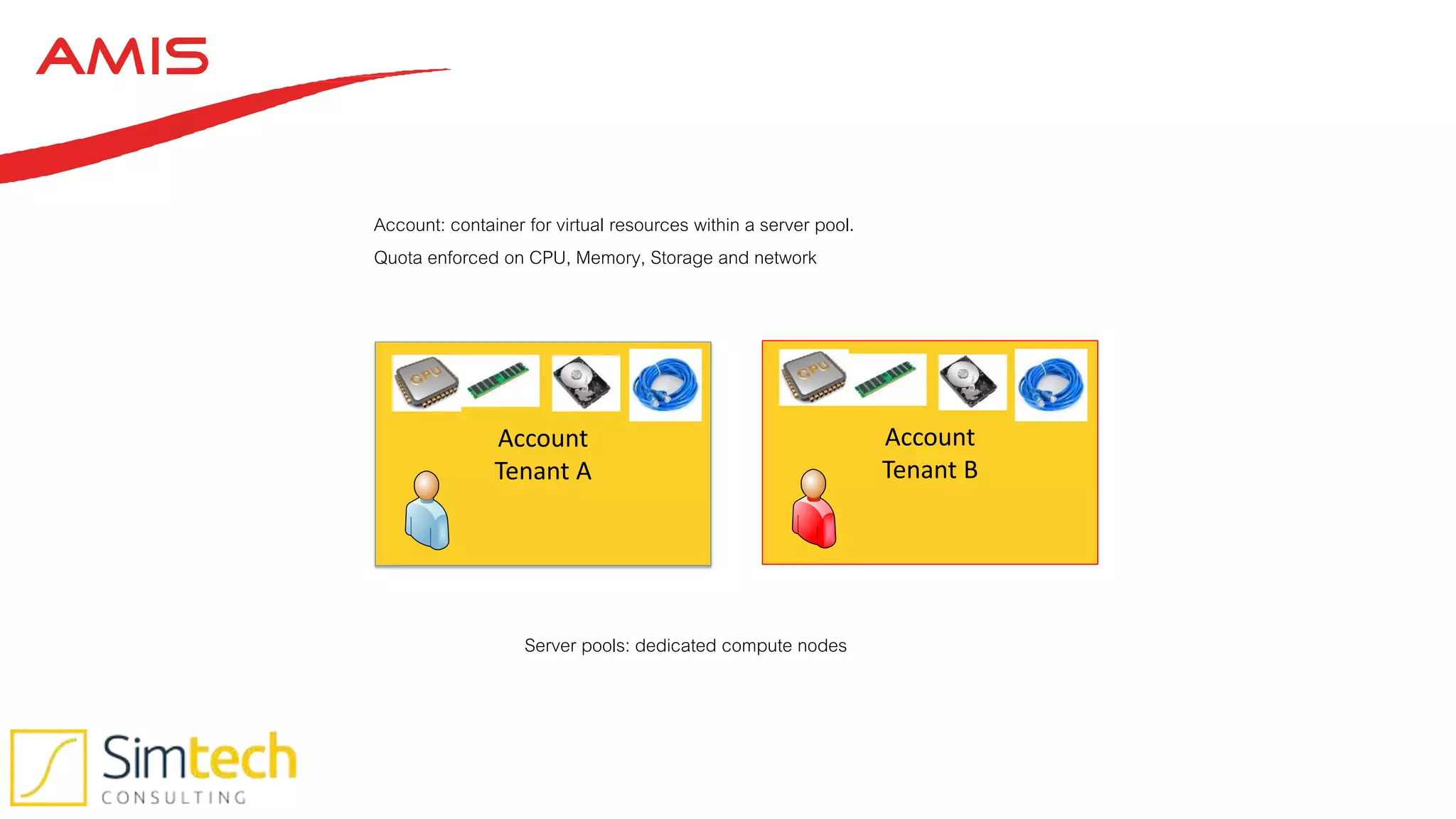
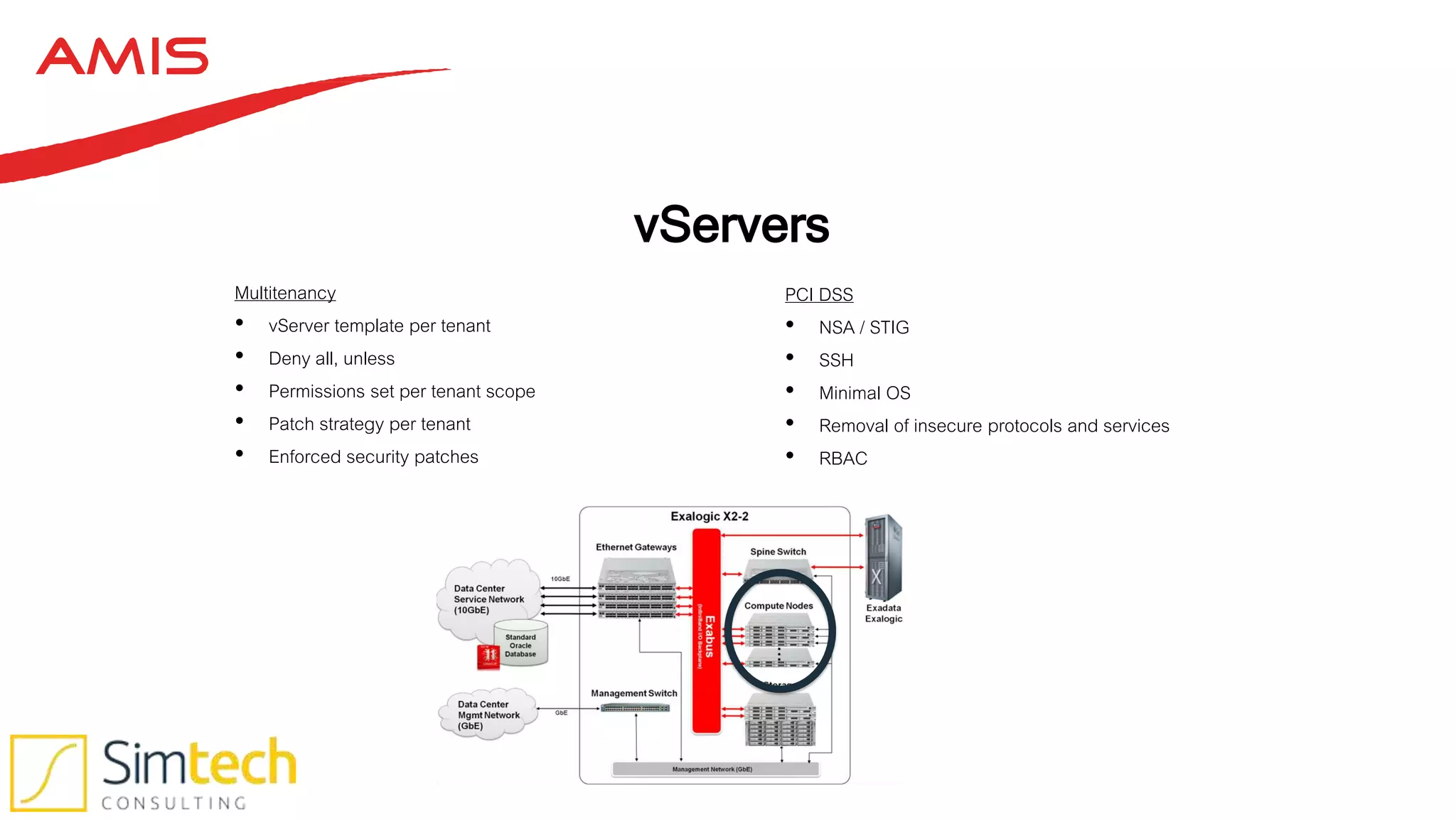
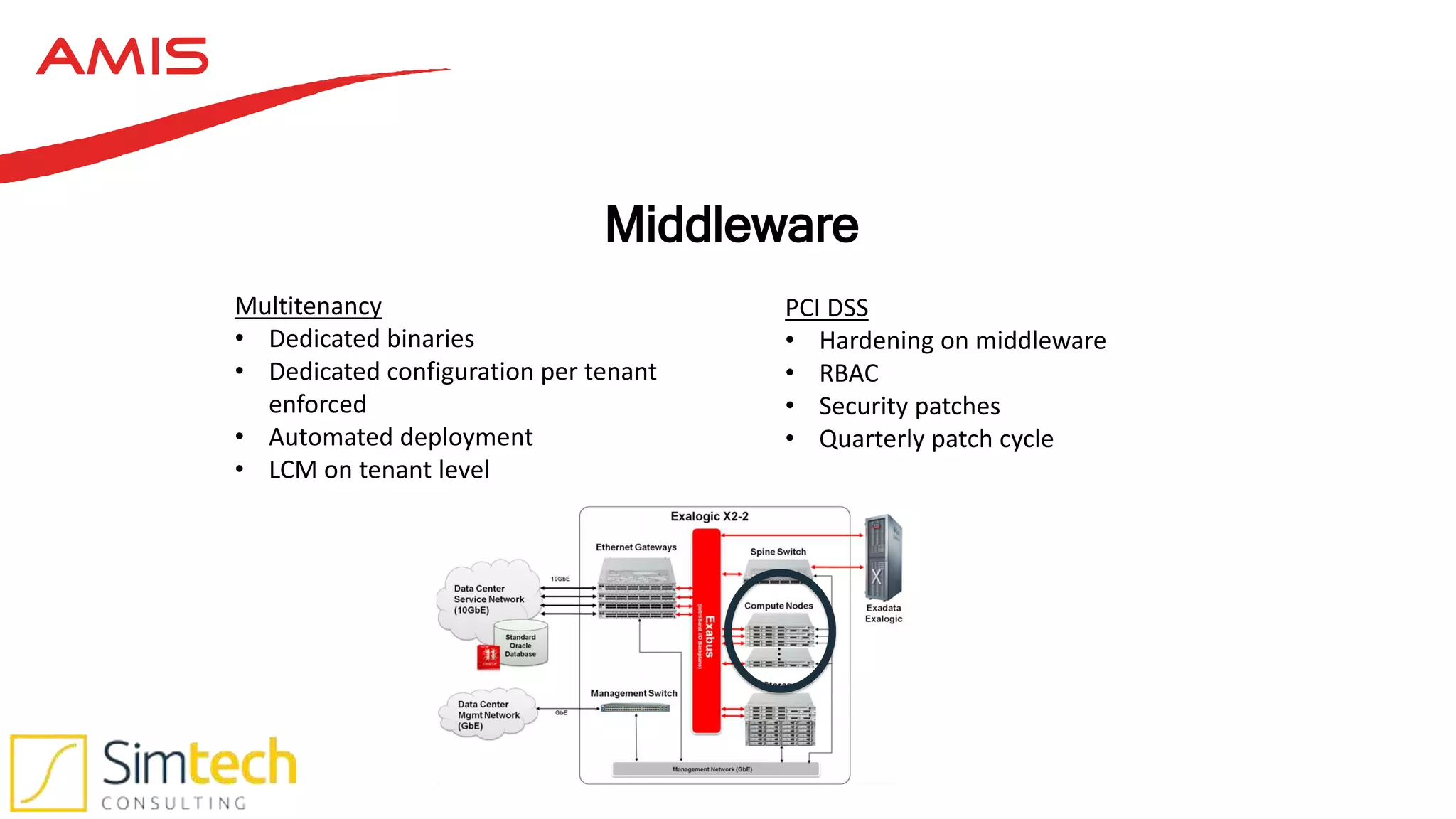
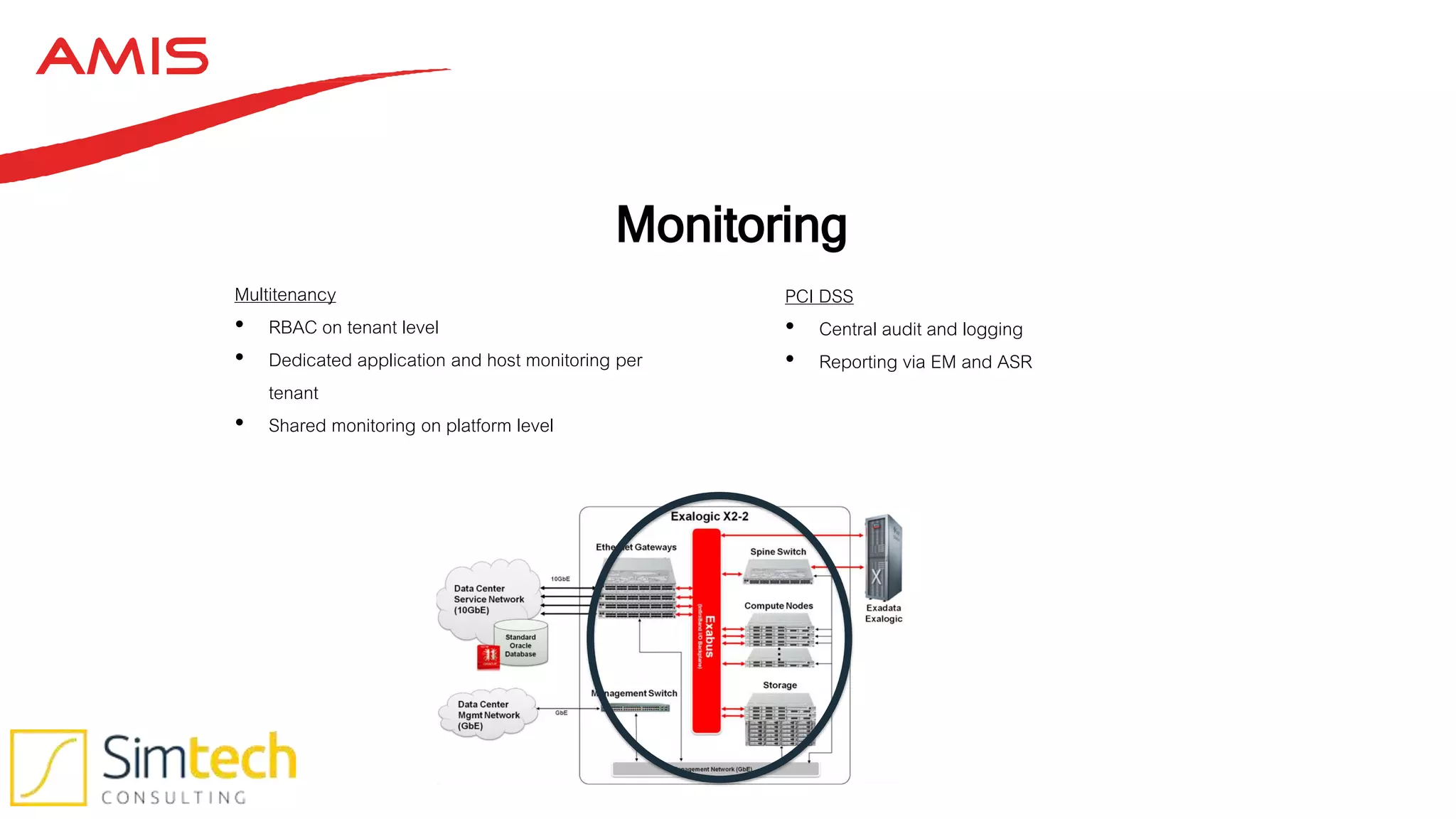
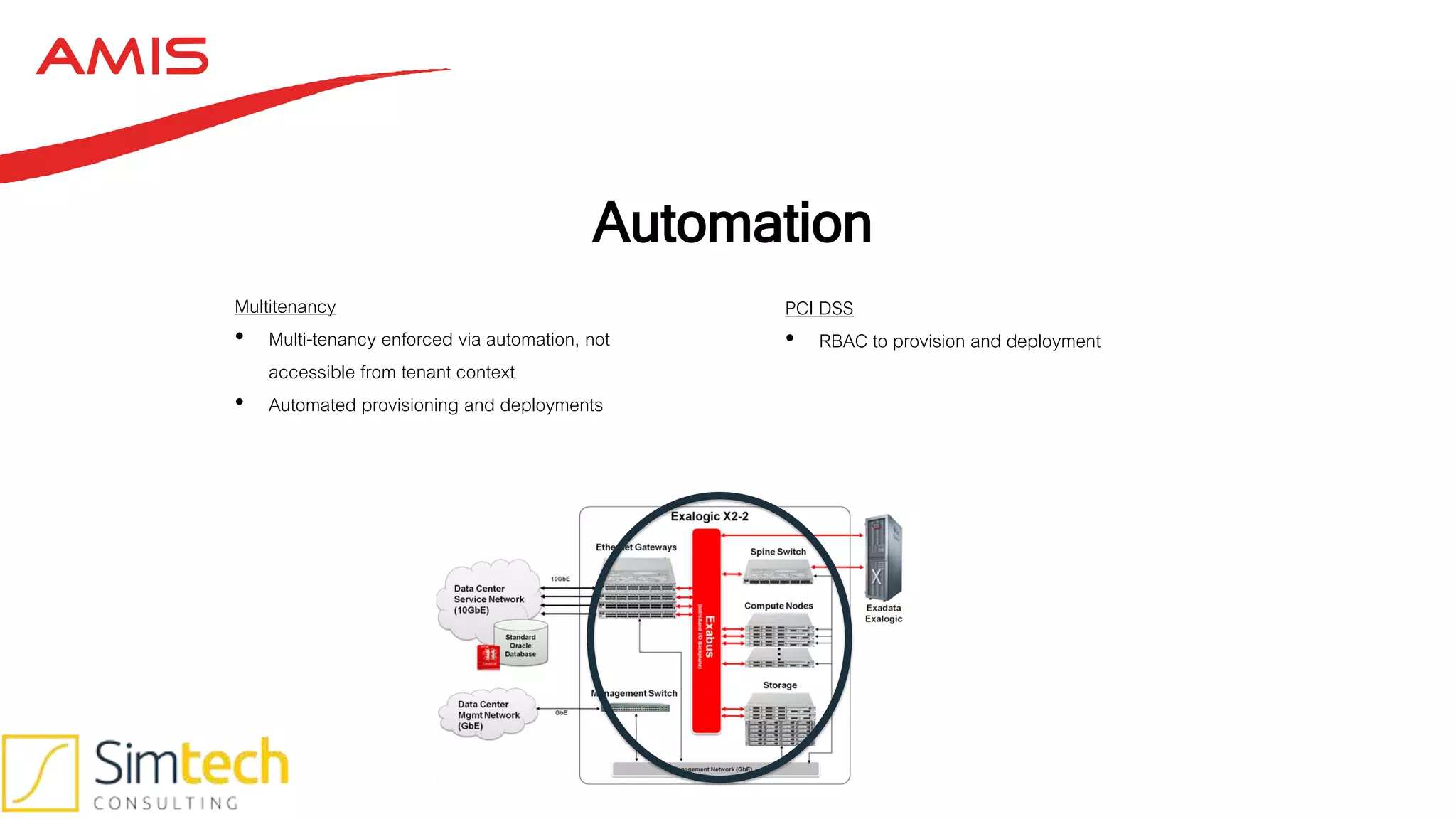
This document discusses how to deliver a multi-tenant and PCI compliant Exalogic platform. It outlines the challenges of a shared platform including compliance with regulations like PCI-DSS. It then explains how Exalogic addresses these challenges through automation, isolation across storage, network and virtualization layers, and other security controls. Key aspects covered include per-tenant provisioning, encryption, firewalling, patching, and auditing to ensure isolation and compliance for different tenants including those processing credit card data.