Embed presentation
Download to read offline

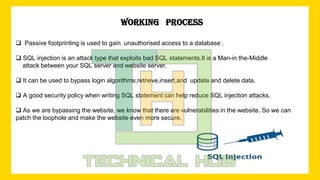
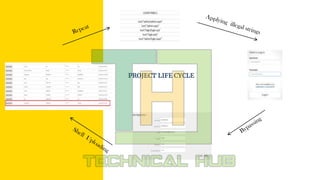
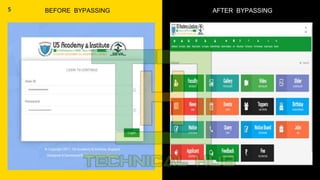


The document details a project on passive footprinting, which involves unauthorized access to targeted websites using techniques like SQL injection. It outlines the risks associated with vulnerabilities in website security, emphasizing the need for better security policies to prevent such attacks. Team members include Vaishnavi, Supriya Eswari, and Namratha.





