This document summarizes a research paper on the architecture of a distributed virtual worlds system developed by researchers at Microsoft. The system was designed to allow multiple users to interact in shared 3D virtual environments. It was built on top of COM and OLE Automation to facilitate access from scripting languages. The system was influenced by MUDs and aimed to support the social and structural aspects of virtual worlds while adding a graphical interface. Key challenges included supporting a distributed architecture, persistent objects, and enabling end users to extend and modify the system securely.

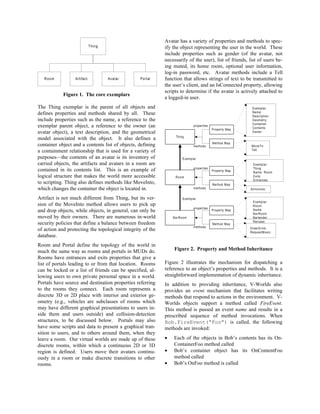
![The Architecture of a Distributed Virtual Worlds System
Manny Vellon, Kirk Marple, Don Mitchell, Steven Drucker
Virtual Worlds Group
Microsoft Research
Microsoft Corporation
Abstract
We have developed an object model that facilitates the
development of shared virtual environments. We have
implemented our object model on top of COM and
OLE Automation and facilitated access from Active
Scripting enabled languages. This paper provides a
brief description of the work we have done on the V-
Worlds project.
1. Introduction
Virtual reality is a user-interface paradigm in which the
user feels immersed in a computer-generated space.
Two aspects of this feeling of immersion have been
discussed: simulating the sensory experience of being
in a space, and the non-sensory aspect of presenting the
user with consistent structure and action [Mitchell94].
The sensory aspect has been pursued by research and
development in 3D computer graphics and display
technology [Sutherland65, Sutherland68, Brooks86,
Brooks88]. Some currently popular computer games
have demonstrated immersive 3D graphical interfaces
on personal computers available to the general public
[DOOM93, QUAKE97].
We use the term virtual world for virtual reality sys-
tems that allow multiple users to interact in the same
space. Adding multiple users to VR creates a number
of interesting new problems. Networking with multiple
clients is obviously necessary, and in some cases the
technology of distributed databases may be required to
support a multi-user VR system. The interface now
requires social functionality for talking and gesturing.
The graphical presentation of the space must allow a
group of people to interact socially and see one an-
other’s actions and responses. Security is an issue, es-
pecially if the system allows users to build and program
within the world.
Current work on multi-user VR systems can be divided
into graphical chat systems, characterized by static
spaces and transient user identity and persistent worlds
with dynamic spaces, movable objects and permanent
user identities. Two very different kinds of systems
have pioneered the development of large-scale virtual
worlds: military simulation networks [Thorpe87,
Zyda92], and text-based multi-user worlds known as
MUDs [Reid94]. SIMNET is based on vehicle and
flight simulators that generate real-time 3D images of a
virtual world. A peer-to-peer network protocol allows
these simulators to display other users’ vehicles and
projectiles during virtual battle simulations.
MUDs maintain long-term persistent worlds in a central
object server; these worlds are accessed via clients
similar in appearance to the old text adventure com-
puter games. Having existed for almost twenty years,
MUDs are a rich source of experience about the struc-
tural aspects of virtual worlds. Some MUDs have been
in continuous operation for ten years and have on the
order of 10,000 subscribed users [FurryMUCK, Lamb-
daMOO], so there is also considerable experience about
the sociology of on-line worlds. We’ve drawn more
extensively from the technology of MUDs than from
graphical VR systems and standards, because we are
explicitly interested in supporting the structural and
social mechanisms found in MUDs.
Elizabeth Reid’s thesis gives a well-researched history
and analysis of MUDs [Reid94]. Early multi-user
combat/adventure games appeared in the late 1970s,
and by the mid 1980s, some of them had abandoned
actual game play and enhanced user communication
and self-expression, becoming what are now called
social MUDs. Jim Aspnes’ TinyMUD and the Habitat
system by Farmer and Morningstar [Morningstar91]
were good examples of purely social MUDs. Habitat
was distinguished by a 2D graphical interface, and
TinyMUD was the first system to give users extensive
abilities to build new places and objects in the world.
Stephen White developed the TinyMUCK and the
MOO systems, extensions to TinyMUD that allowed
users to write scripts controlling objects. The MOO
was developed further by researchers at Xerox PARC
[Curtis92]. In the meantime, combat/adventure MUDs
have also evolved, and servers like the LPMUD have
essentially the same technical capabilities as the most
advanced social MUDs.
An object-oriented MUD, like White and Curtis’ MOO,
is a network database server which stores objects hav-
ing properties and methods. The topology of the space
is defined by “room” objects, representing discrete lo-
cations, interconnected by portal objects. Each room
has descriptive text which users read to situate them-](https://image.slidesharecdn.com/25ae3c39-7c55-4606-85af-84c14c50f8f6-161230205909/85/Papers_usenix98-2-320.jpg)





![Worlds to perform late binding. The helper functions
also enforce V-Worlds security policies and automati-
cally perform any remoting (e.g. replicating property
changes or invoking remote methods). On the server,
the put_Property helper function is responsible for log-
ging property changes.
From scripting languages (and anything else that uses
OLE Automation), access to V-Worlds objects is much
more straightforward. V-Worlds IThing objects im-
plement IDispatch by consulting the dynamically added
properties and methods in addition to the static OLE
TypeLib information. Essentially, the implementation
of IDispatch turns an x.y reference into an
x.get_Property(“y”),x.put_Property(“y
”)or x.InvokeMethod(“y”) helper function
call. Thus, the content developer can more naturally
access added methods and properties:
‘ In VBScript
‘ add a new property and initial-
ize it
foo.AddProperty “Age”, 12
‘ access the property
DogYears = foo.Age * 7
foo.Age = DogYears
‘ add a new method
bServerSide = True
set method = world.CreateMethod(…,
bServerSide, …)
foo.AddMethod “newmethod”, method
‘ call it
foo.newmethod 7, “Bob”
10. Status
The V-Worlds system has been implemented and will
be released to a limited developer beta-test in the sec-
ond quarter of 1998. We’re currently working with
about a half dozen third party developers and universi-
ties to build different worlds on top of the basic plat-
form described in this paper. Performance improve-
ments and optimizations are still in progress. To date,
we have built 4 test worlds on top of the V-Worlds plat-
form and the system has been tested with 20 simultane-
ous users, and 150 simulated users.
11. Summary
The Virtual Worlds Group has implemented a platform
that facilitates the development of shared virtual envi-
ronments. The platform provides features that handle
client/server computing, persistent state management,
security and ease of development. These features are
built on top of standard COM functionality.
12. References
[Brooks86] Brooks, F.P. Walkthrough – A Dynamic
Graphics System for Simulating Virtual Buildings –
Proceedings of 1986 Workshop on Interactive 3D
Computer Graphics (Chapel Hill, North Carolina).
Computer Graphics. pp. 9-21. 1986.
[Brooks88] Brooks, F.P. Grasping Reality Through
Illusion: Interactive Graphics Serving Science. Pro-
ceedings of SIGCHI - 1988. pp 1-11. 1988.
[Curtis92] Curtis, P. Mudding: Social Phenomena in
Text-Based Virtual Realities, Intertek Vol 3.3 1992
[DOOM93, QUAKE97] The DOOM and Quake PC
computer games, produced by Id Software, Mesquite
TX, 1993, 1997.
[FurryMUCK] http://www.furry.com/
[LambdaMOO] lambda.parc.xerox.com:8888
[Mitchell94] Mitchell, A.R., S. Rosen, W. Bricken, R.
Martinez, B. Laurel, Panel on Determinants of Immer-
sivity in Virtual Reality: Graphics vs. Action. Computer
Graphics, p. 496. 1994.
[Morningstar91] Morningstar, C., Farmer, R., “The
Lessons of Lucasfilm’s Habitat” in Cyberspace: First
Steps, Michael Benedikt (ed), pp 273-302, MIT Press,
1991.
[Reid94] Reid, E. Cultural Formations in Text-Based
Virtual Realities. Masters Thesis. English Department.
University of Melbourne. 1994.
[Sutherland65]. Sutherland. I.E. The Ultimate Display.
Information Processing. Proc. IFIP Congress 65. 506-
508. 1965.
[Sutherland68] Sutherland I.E. A Head Mounted Three
Dimensional Display. In Fall Joint Computer Confer-
ence, AFIPS Conference Proceedings 33. 757-764.
1968.
[Thorpe87] Thorpe, Jack. The New Technology of
Large Scale Simulator Networking: Implications for
Mastering the Art of Warfighting. Proceedings of the
Ninth Interservice Industry Training Systems Confer-
ence. 1987.
[Zyda92]. Zyda, Michael J. D.R. Pratt, JG Monahan,
K.P. Wilson, NPSNET: Constructing a 3D Virtual
World. Proceedings of 1992 Symposium on Interactive
3D Graphics. Computer Graphics. 1992.](https://image.slidesharecdn.com/25ae3c39-7c55-4606-85af-84c14c50f8f6-161230205909/85/Papers_usenix98-9-320.jpg)