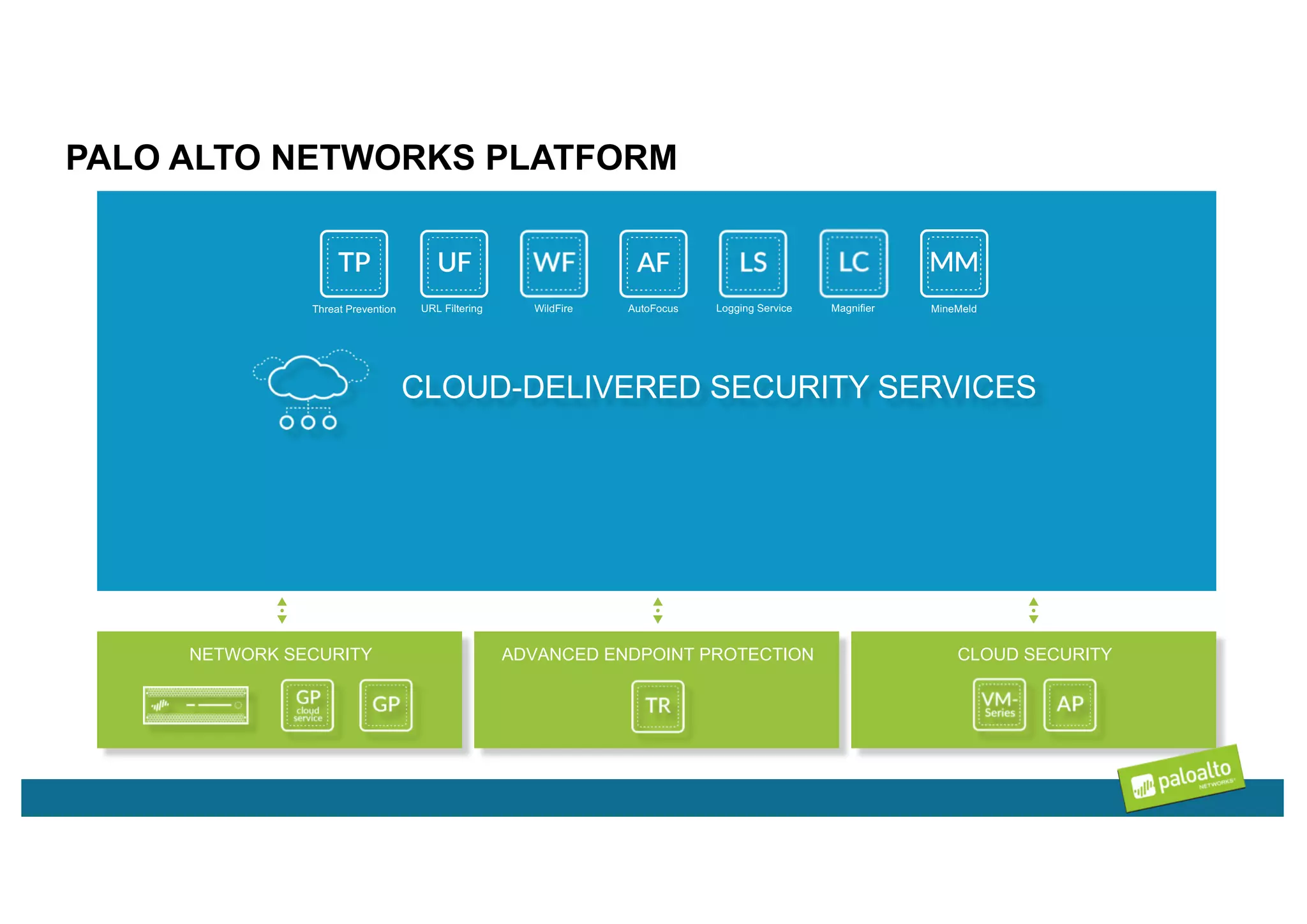
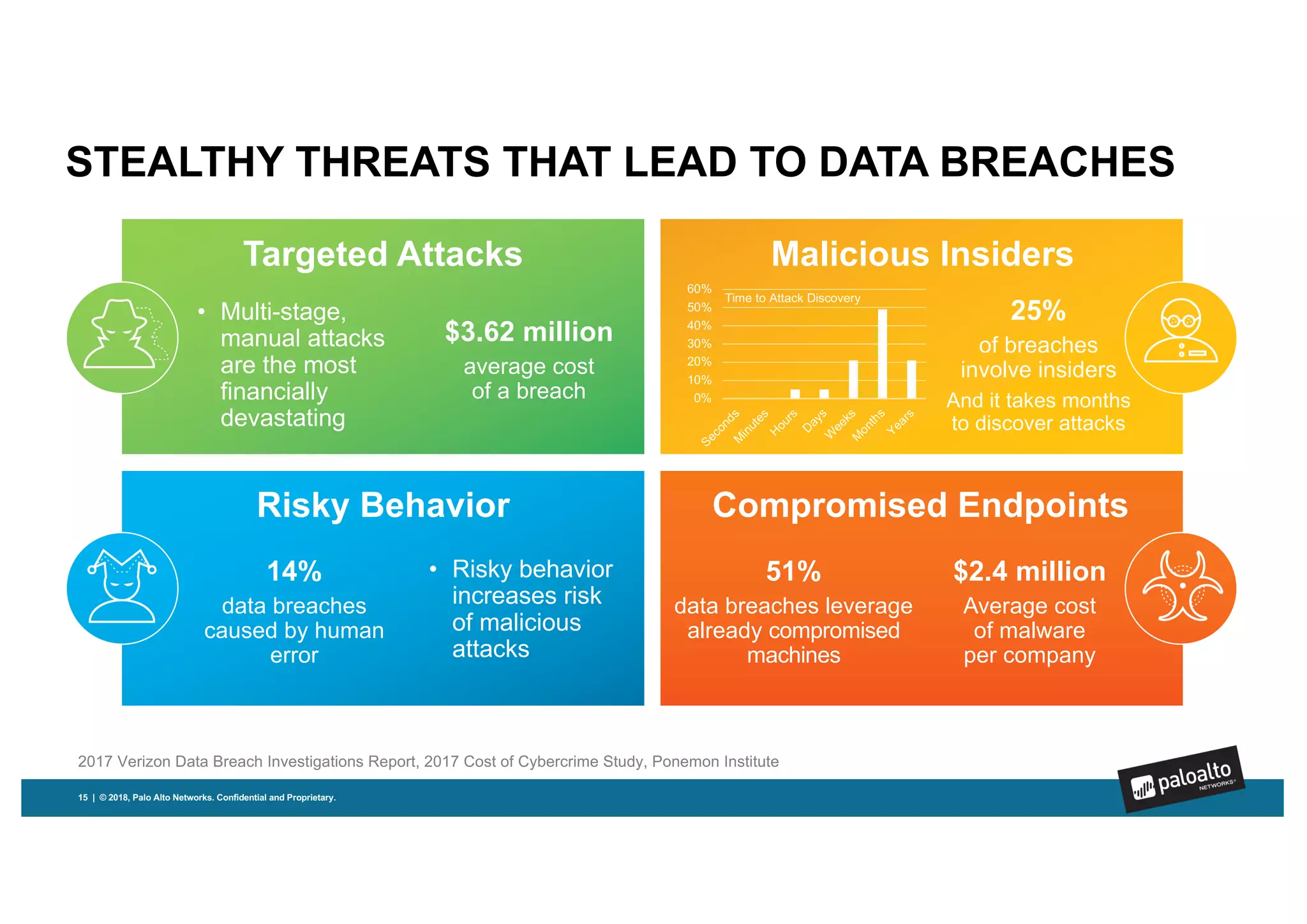
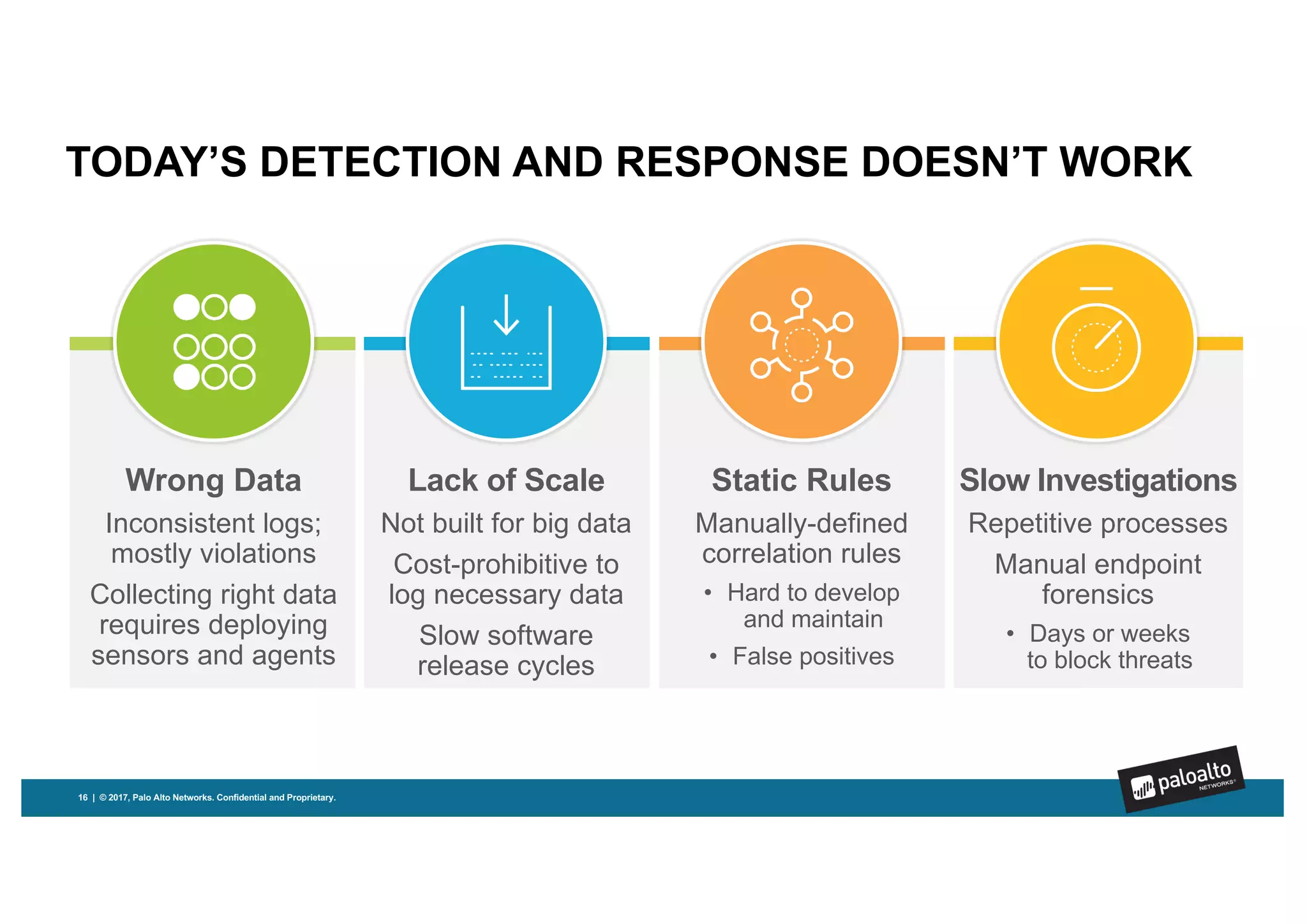
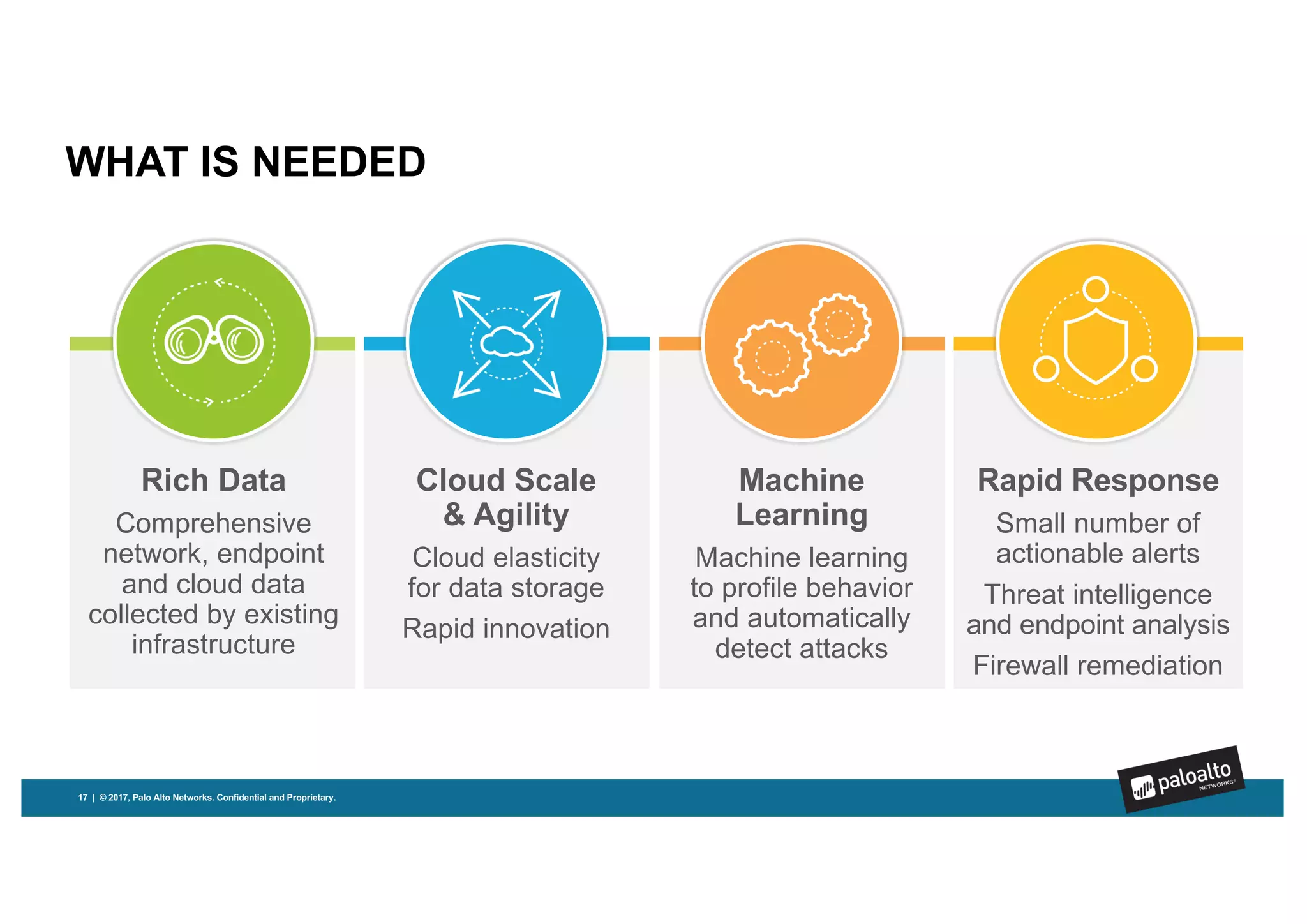
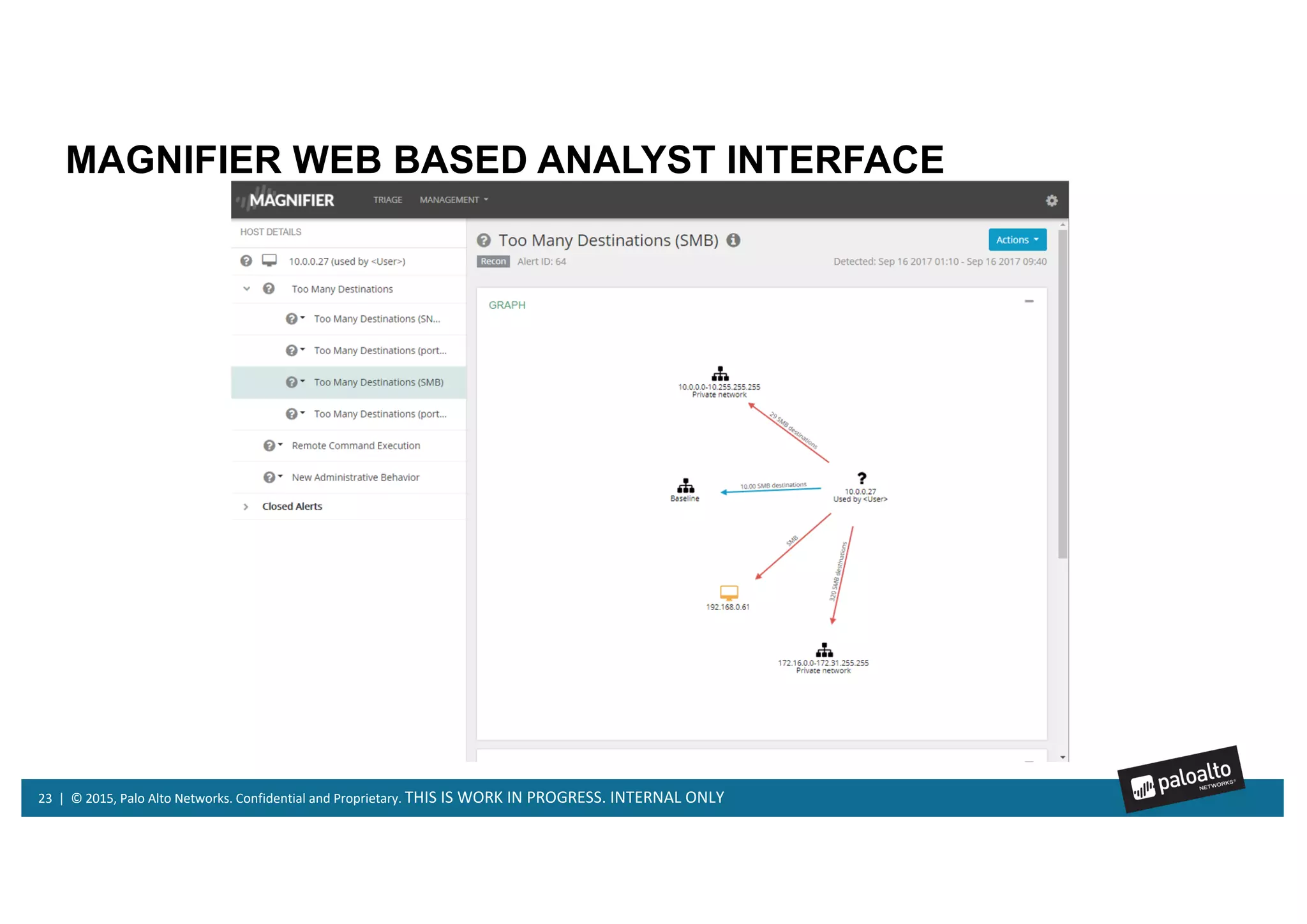
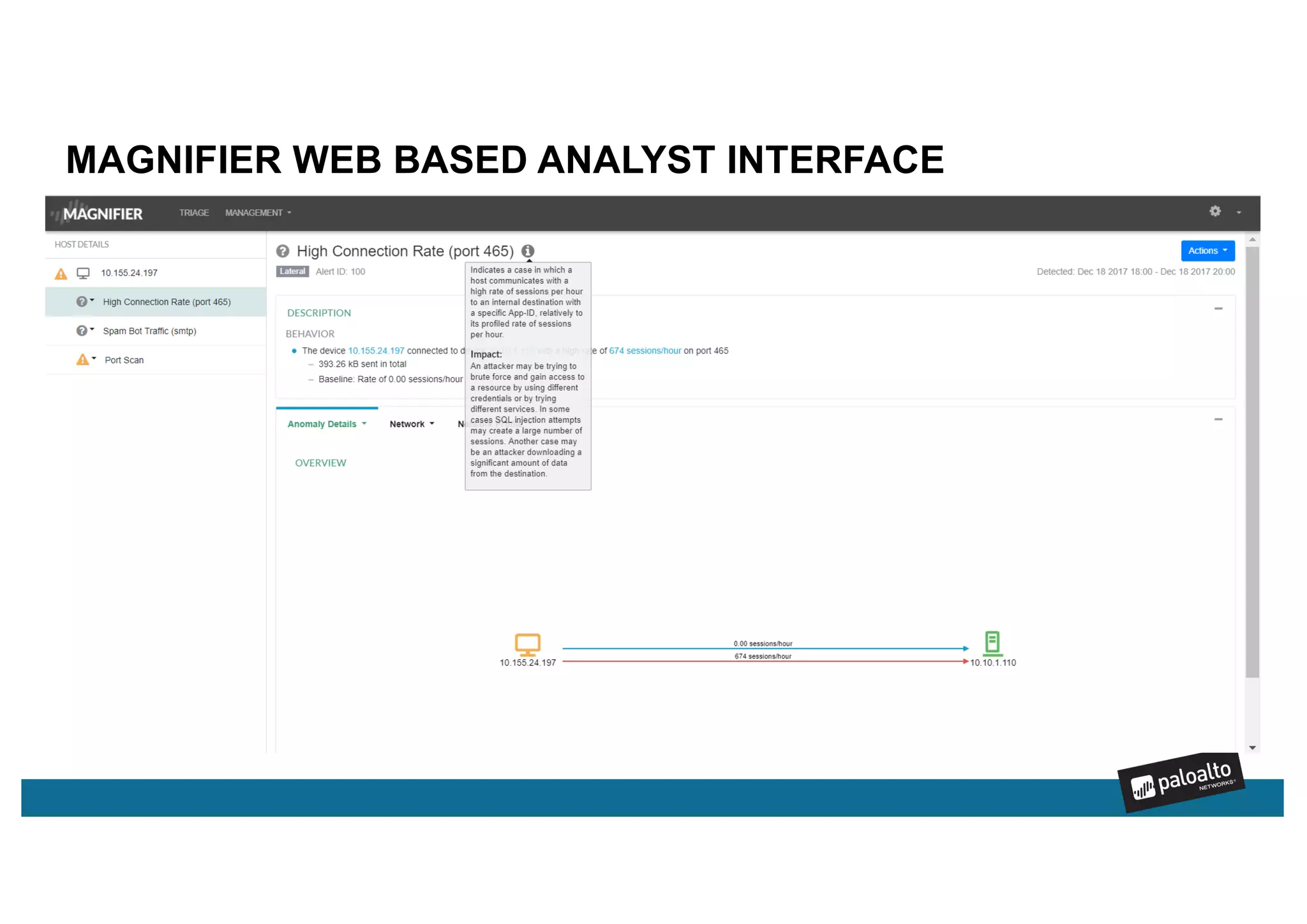
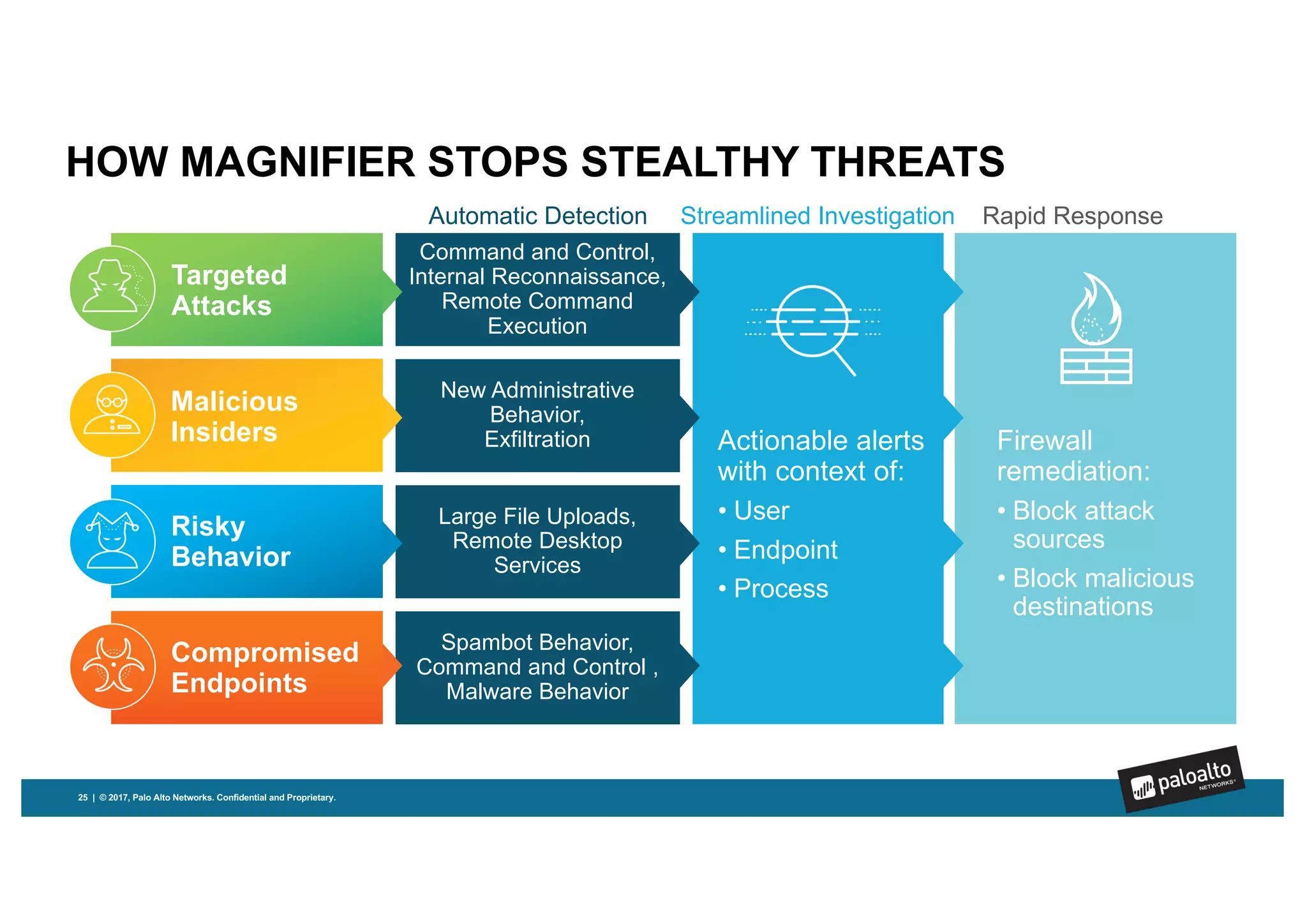
Magnifier is Palo Alto Networks' behavioral analytics solution that uses machine learning to analyze network, endpoint, and cloud data to detect stealthy threats across the attack lifecycle. It detects anomalies in device behaviors and generates actionable alerts with relevant context. Magnifier then facilitates rapid investigations through automated endpoint interrogation. It can also respond quickly by blocking malicious devices or destinations at the firewall. As a cloud-delivered application, Magnifier provides scalability, agility, and ease of deployment compared to on-premise solutions.