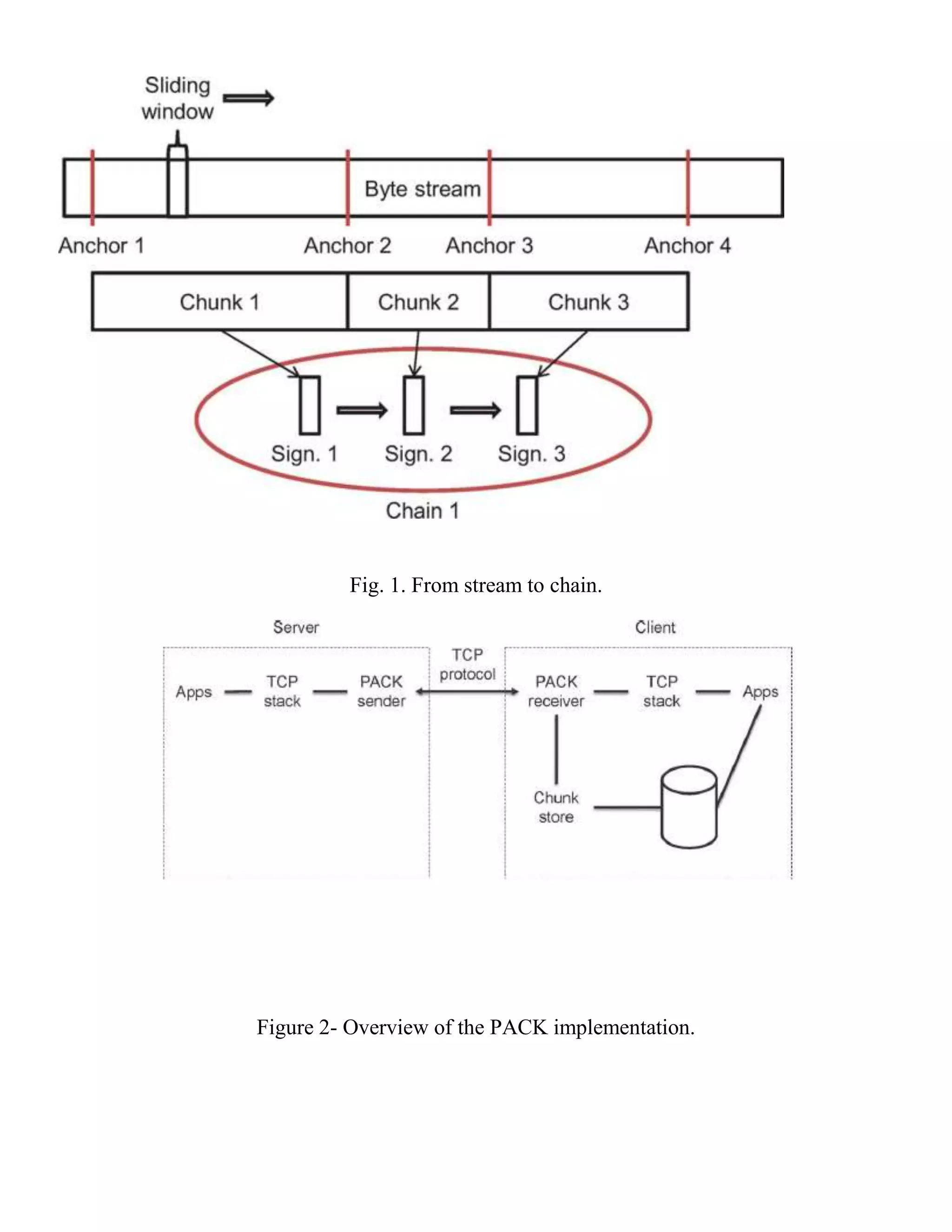
The document introduces 'PACK', a predictive traffic redundancy elimination (TRE) system aimed at optimizing cloud bandwidth and cost for end-users by minimizing server-side processing. It leverages client-side processing to predict and eliminate redundant data transmissions, overcoming the limitations of existing TRE solutions that require synchronization between client and server. Experimental results demonstrate that PACK achieves a 30% reduction in redundancy and 20% in overall costs without significantly increasing computational effort on the sender's side.