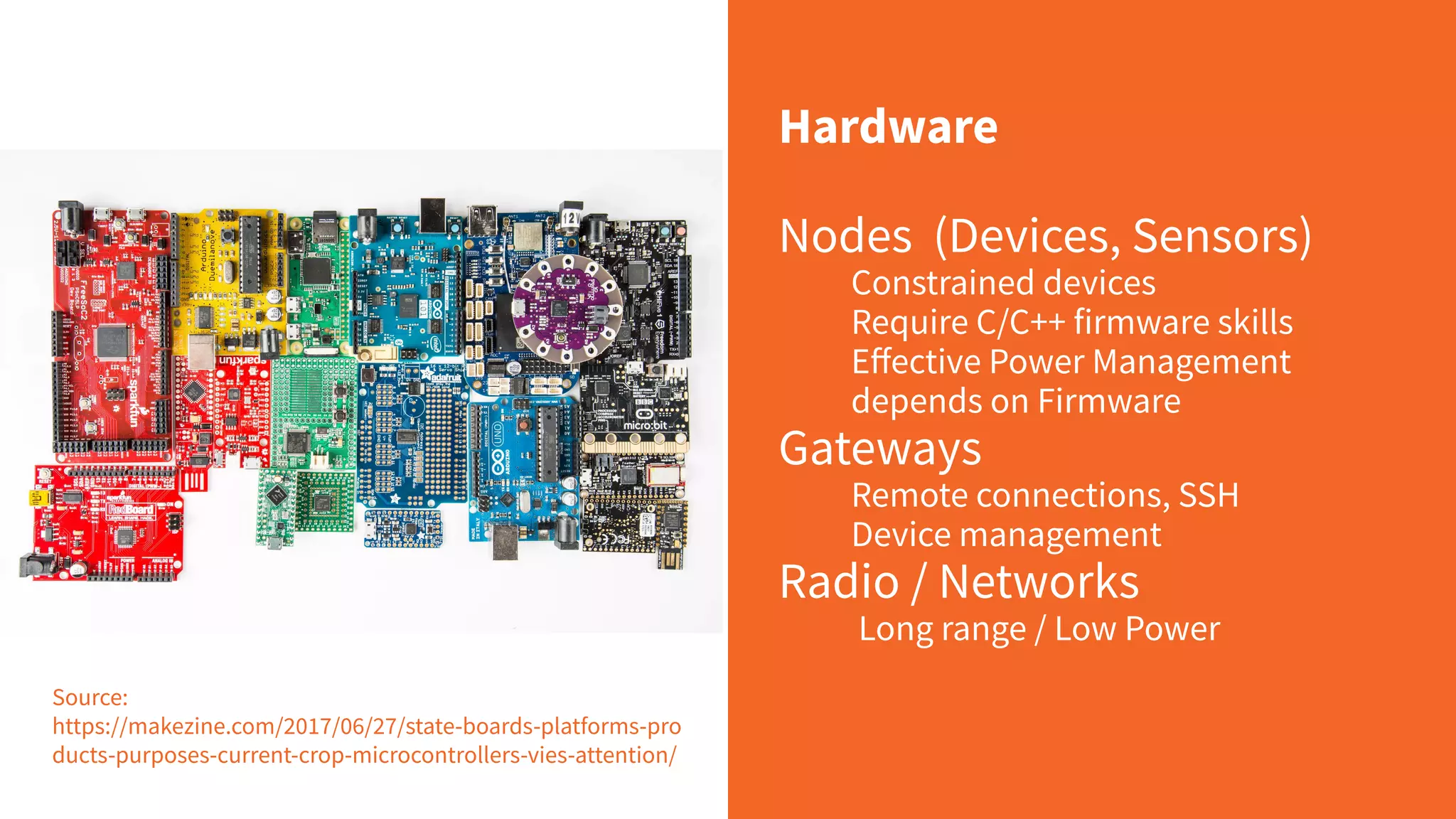
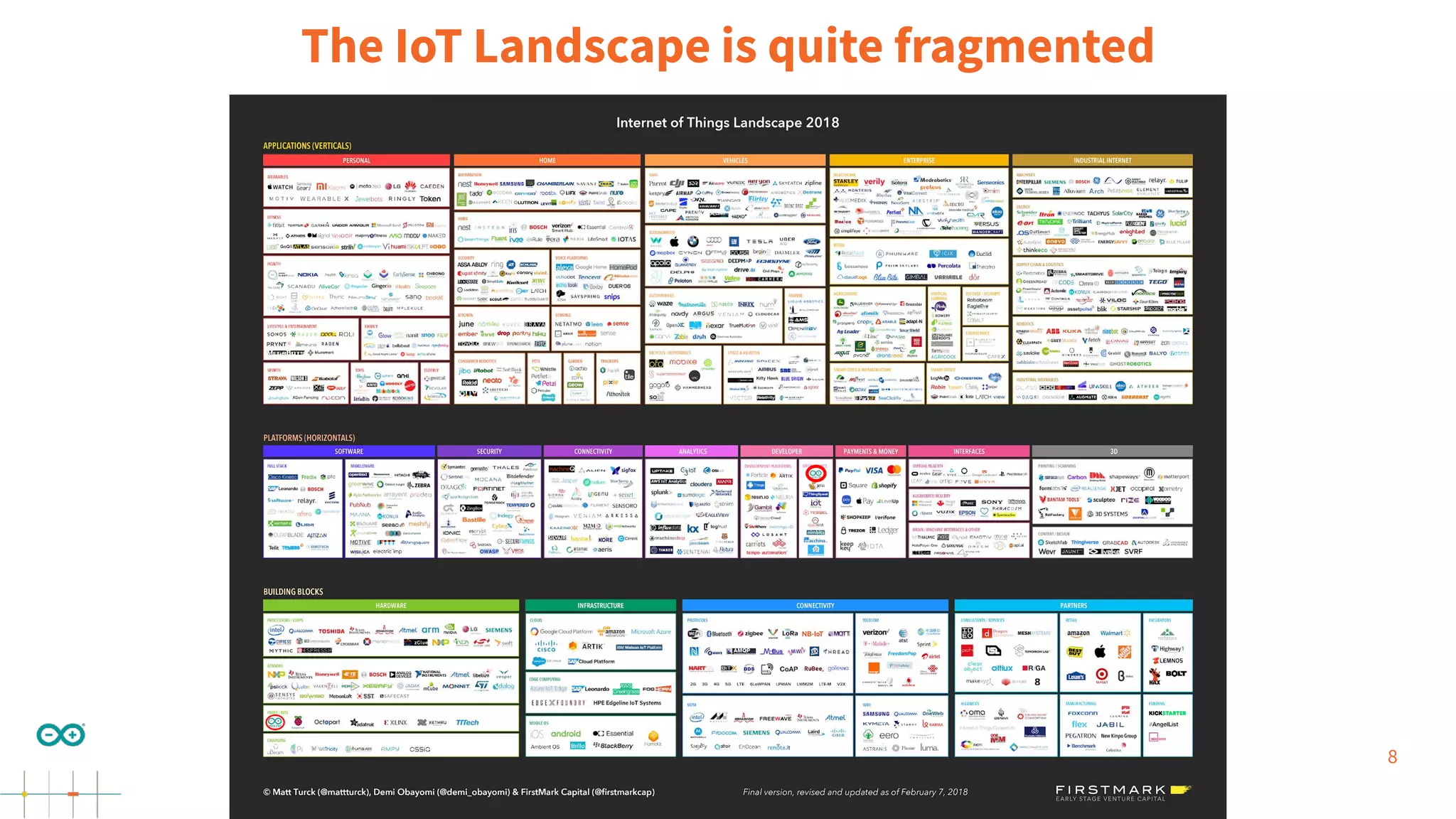
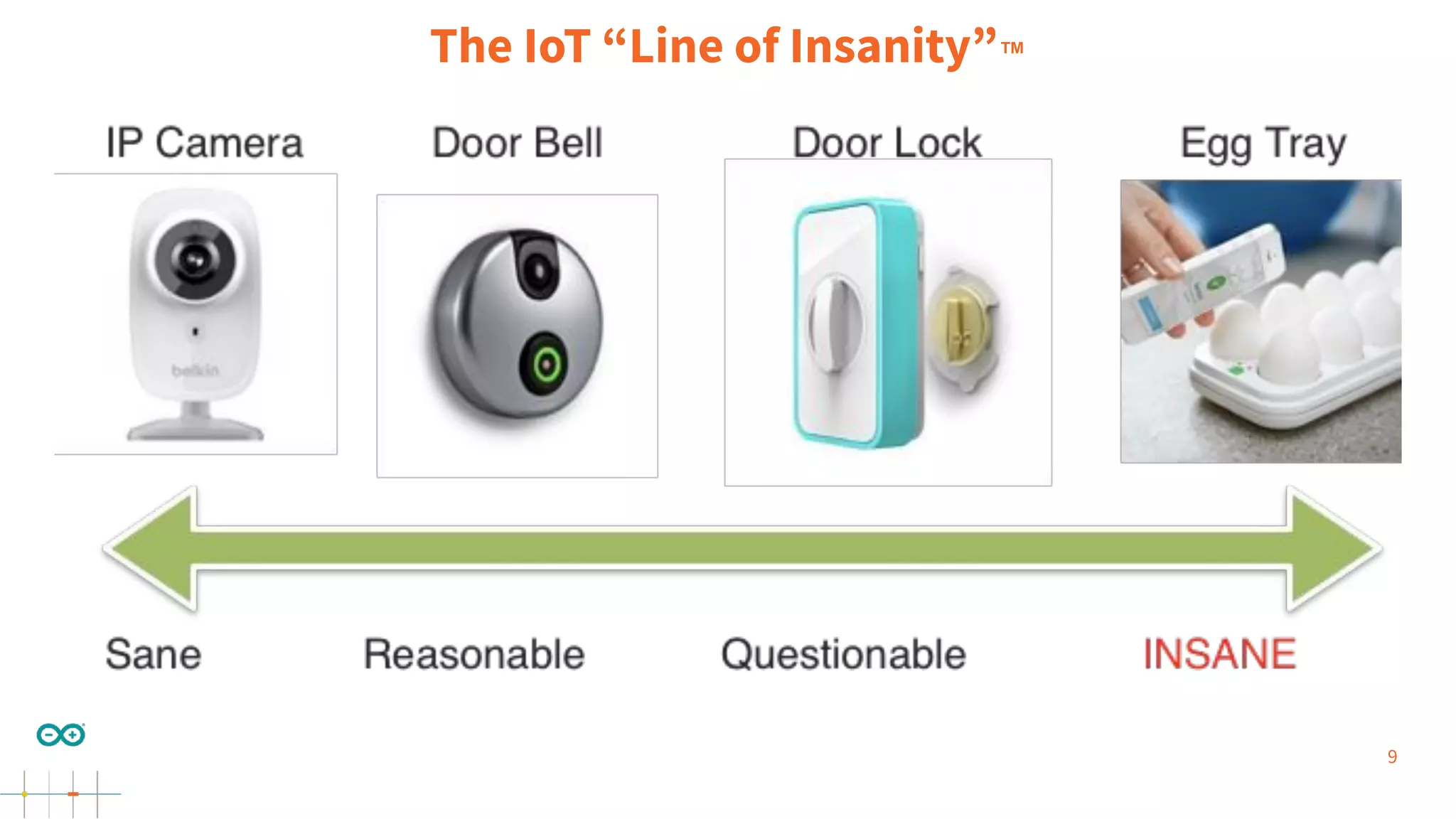
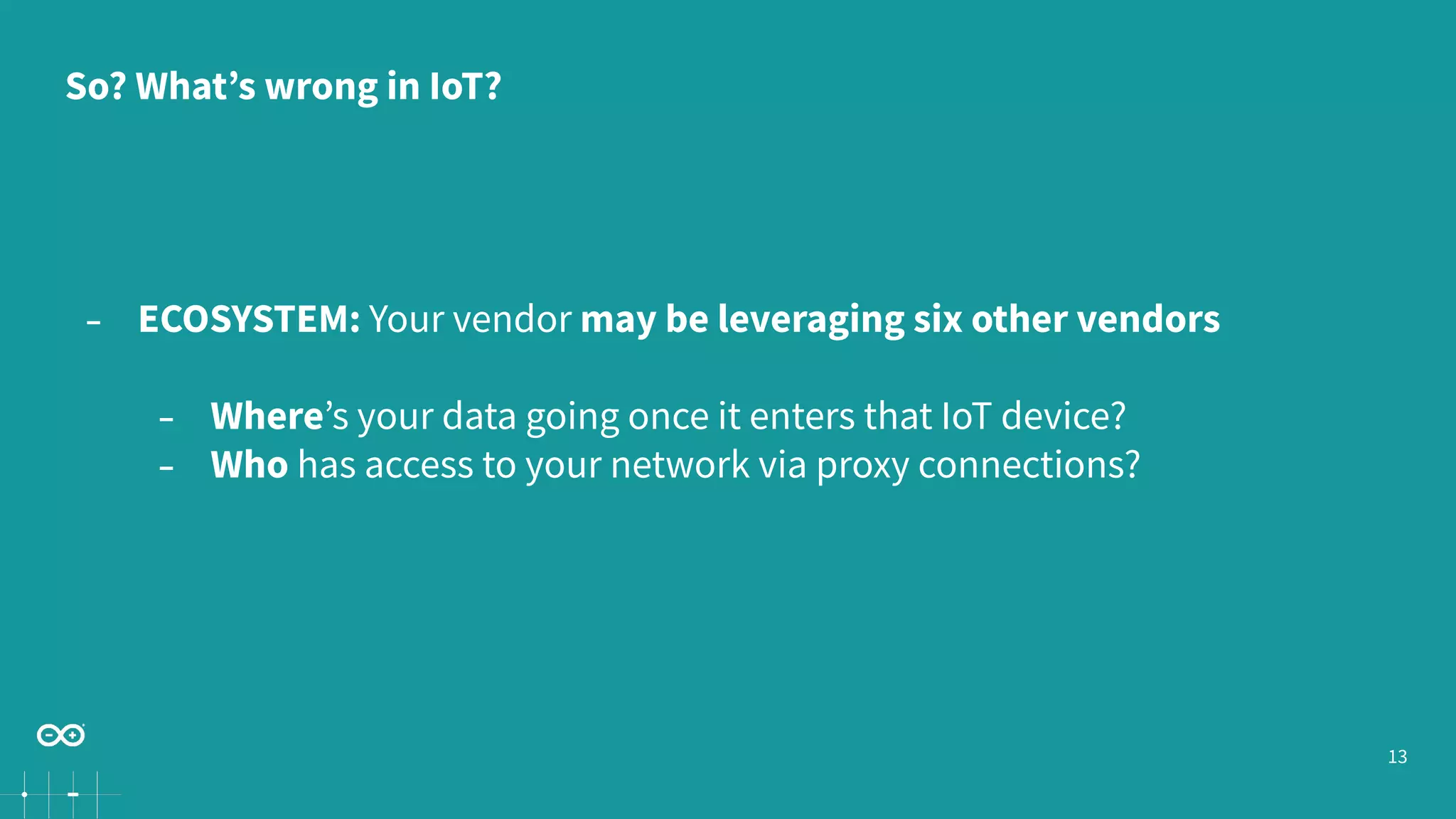
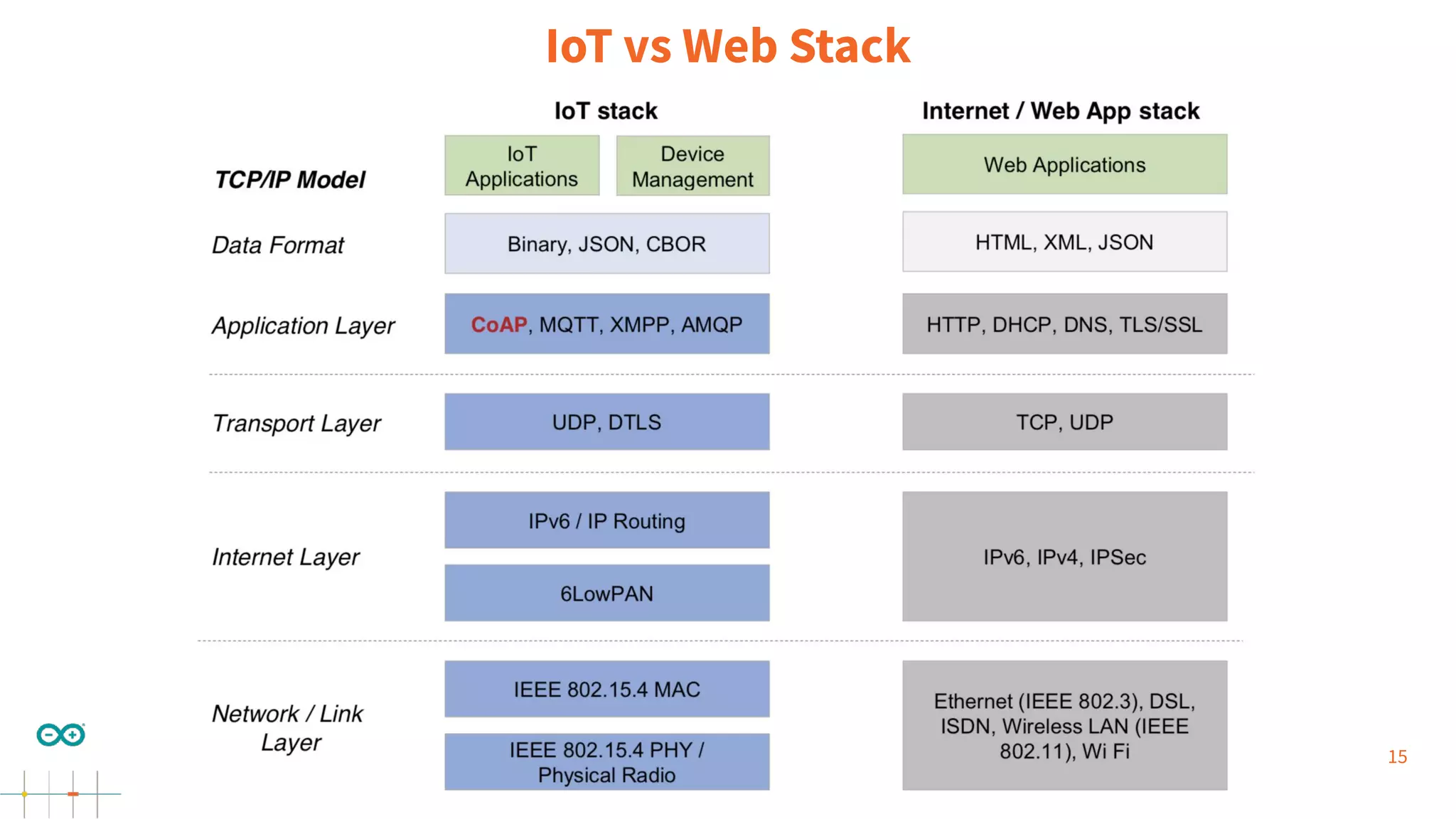
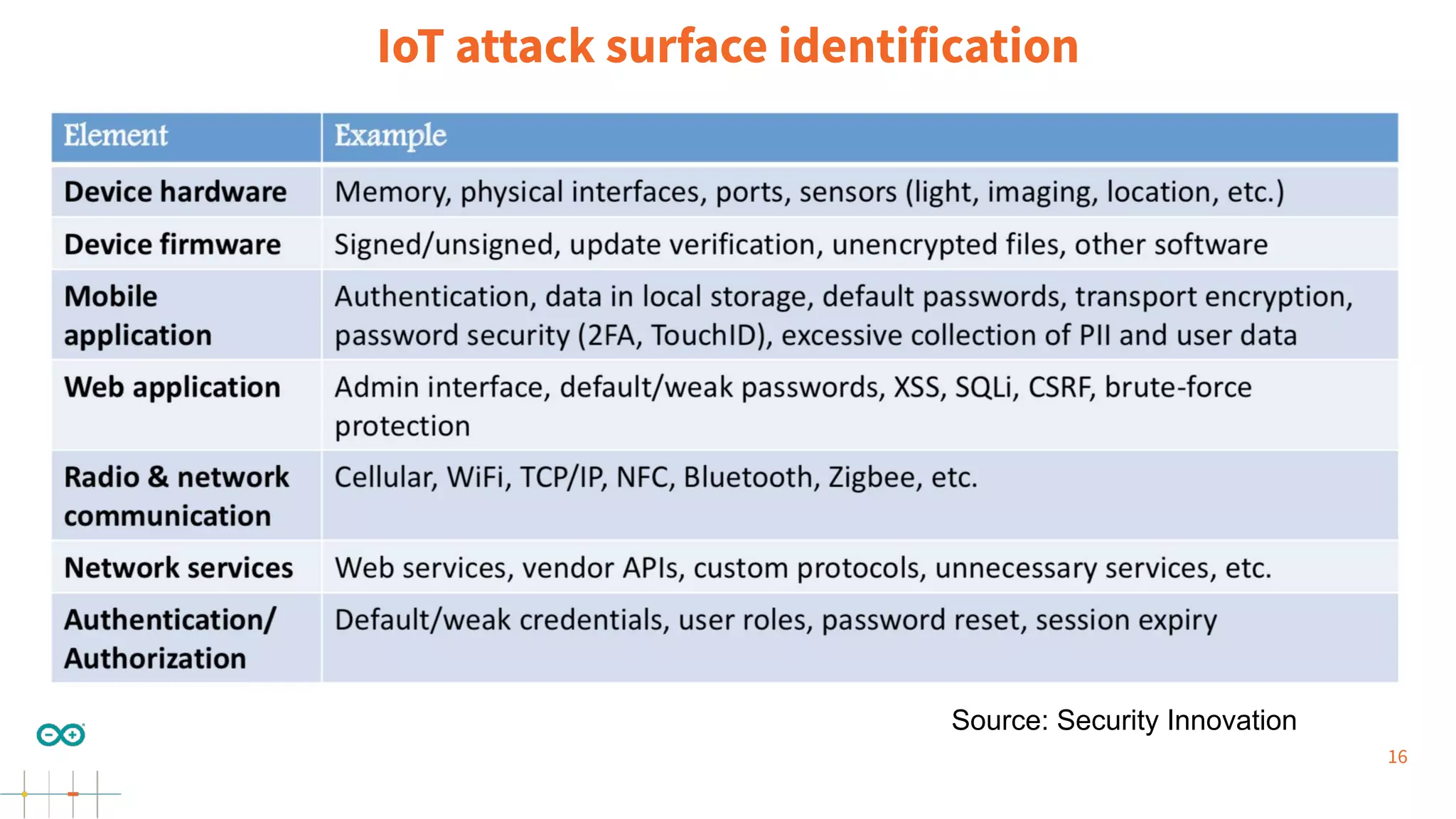
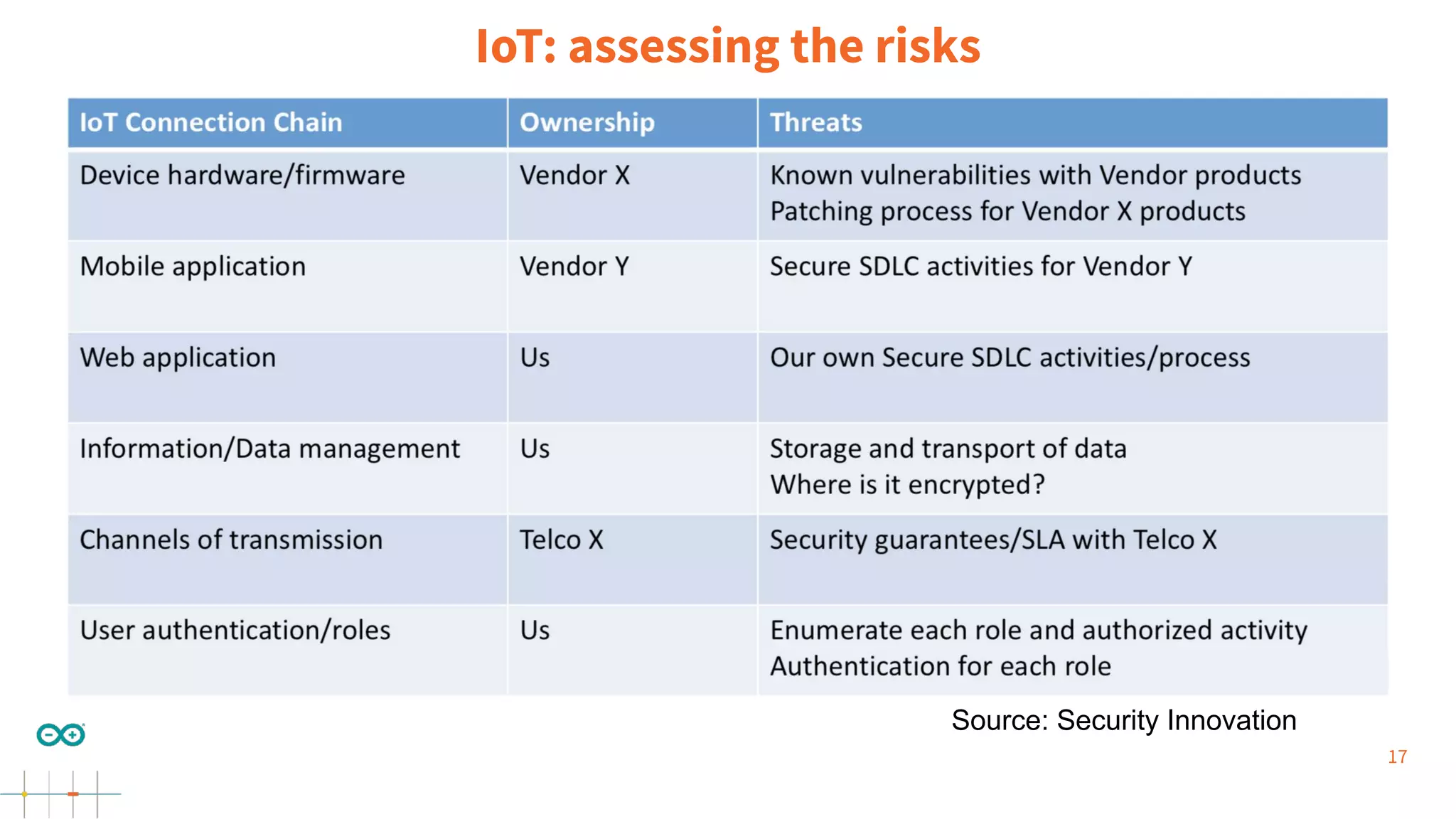
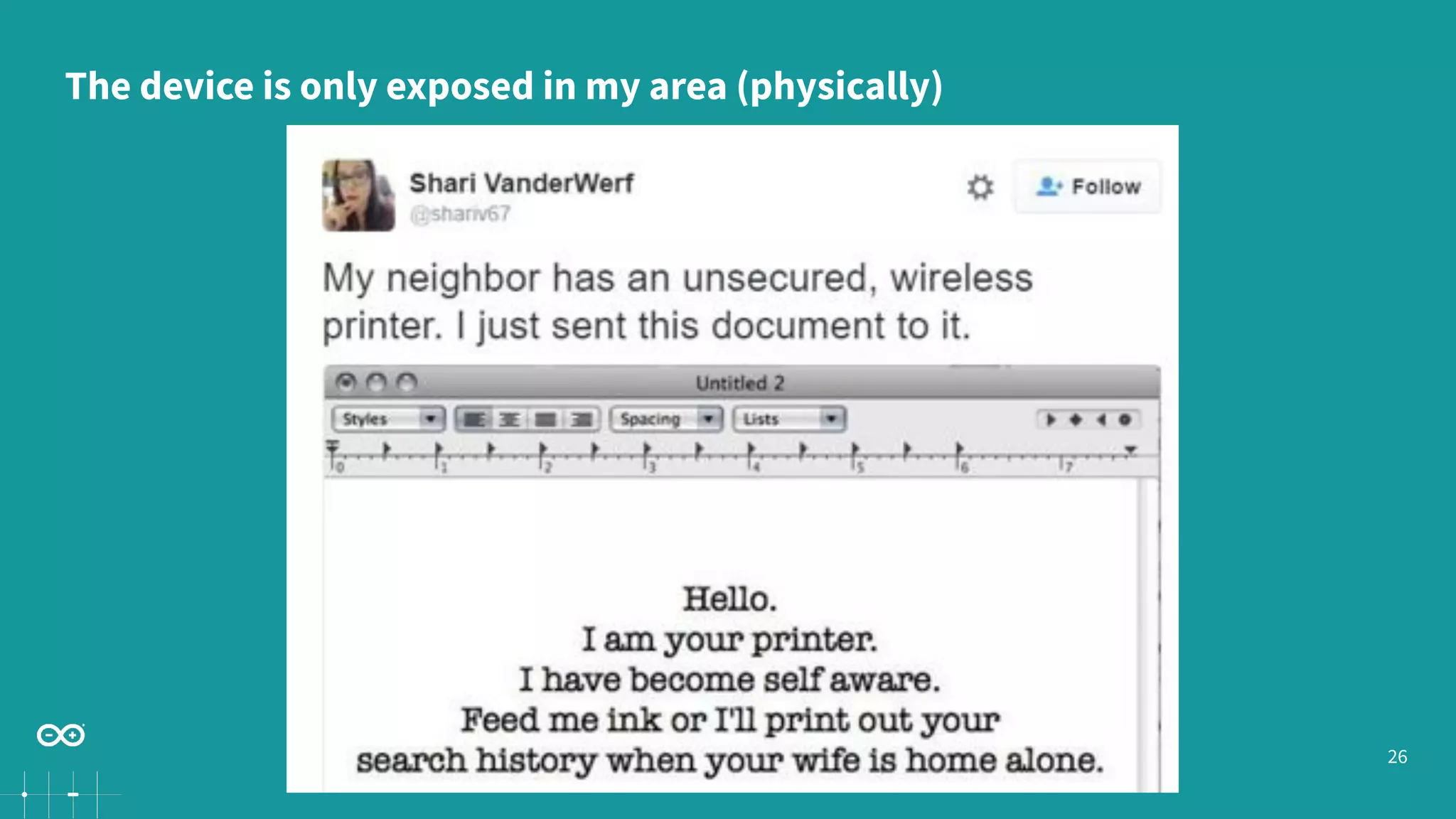
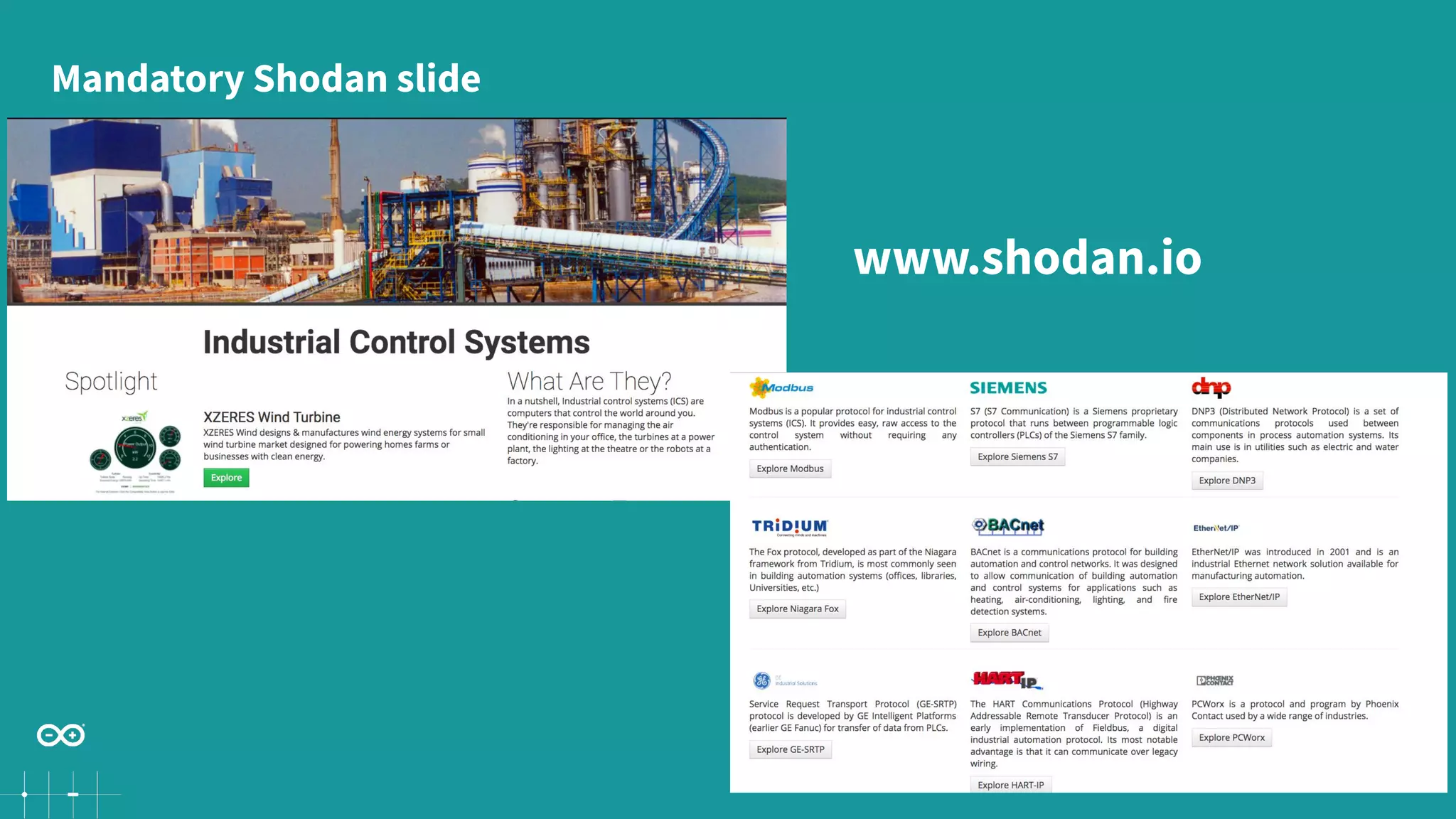
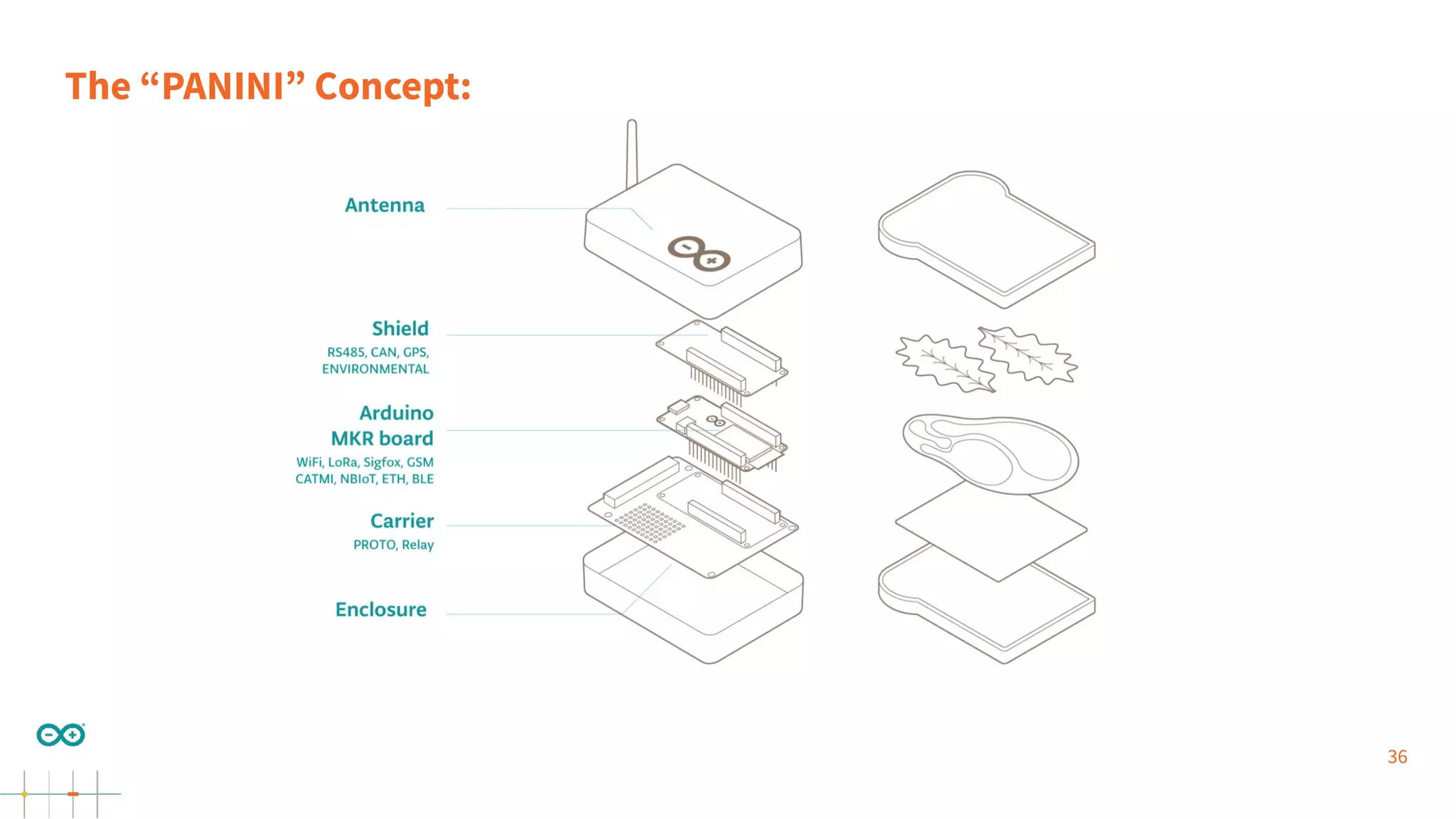
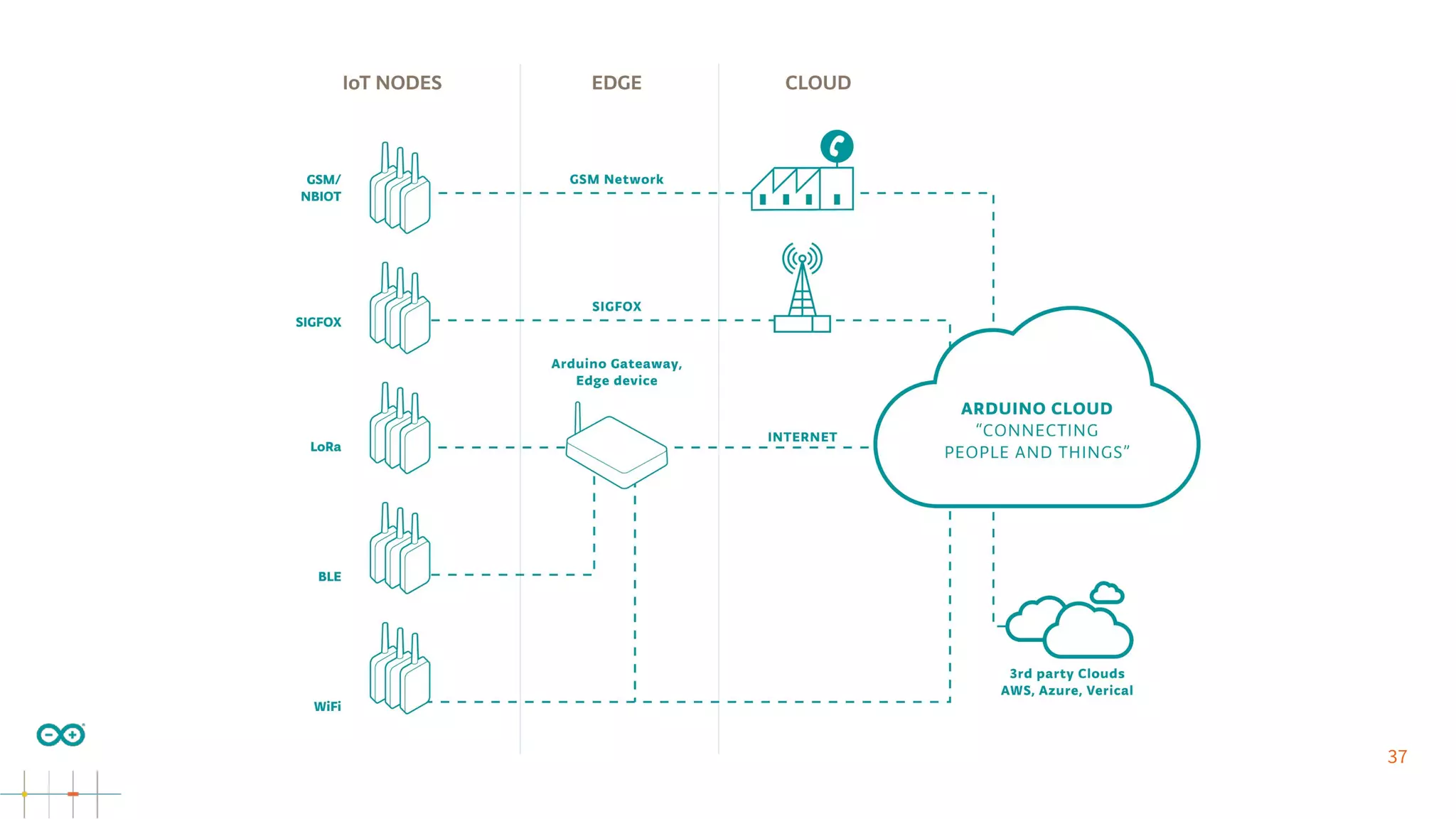
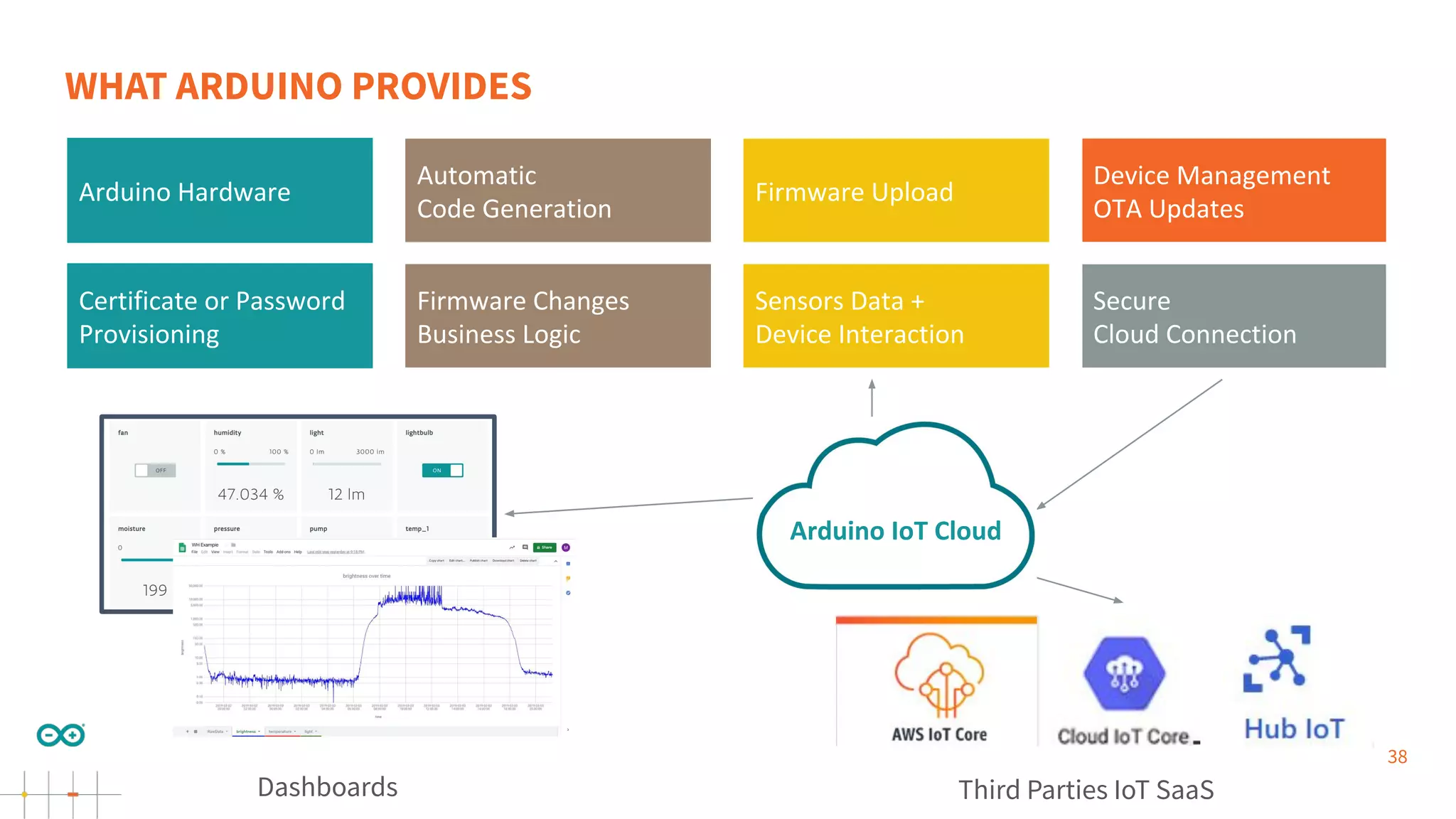
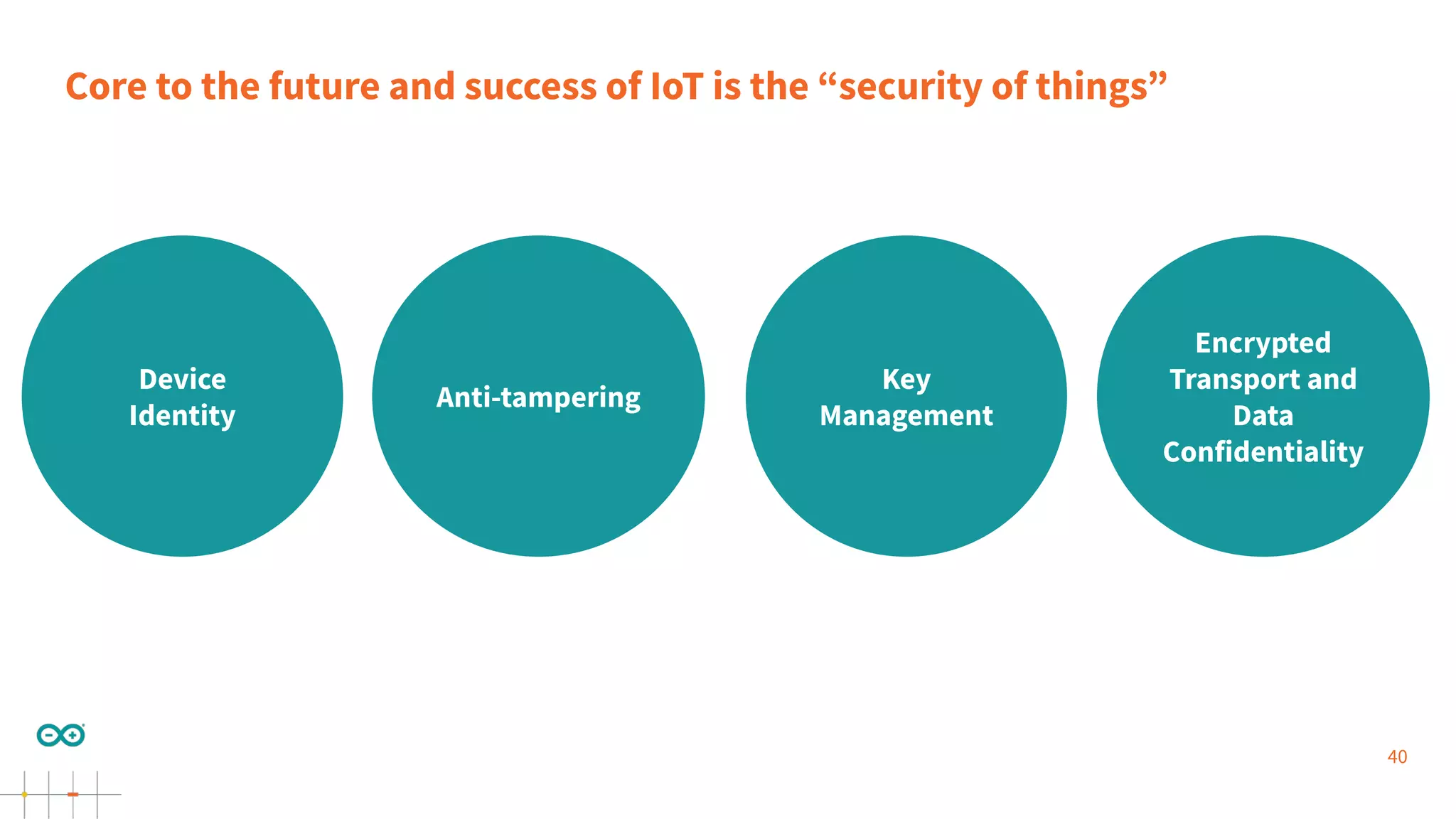
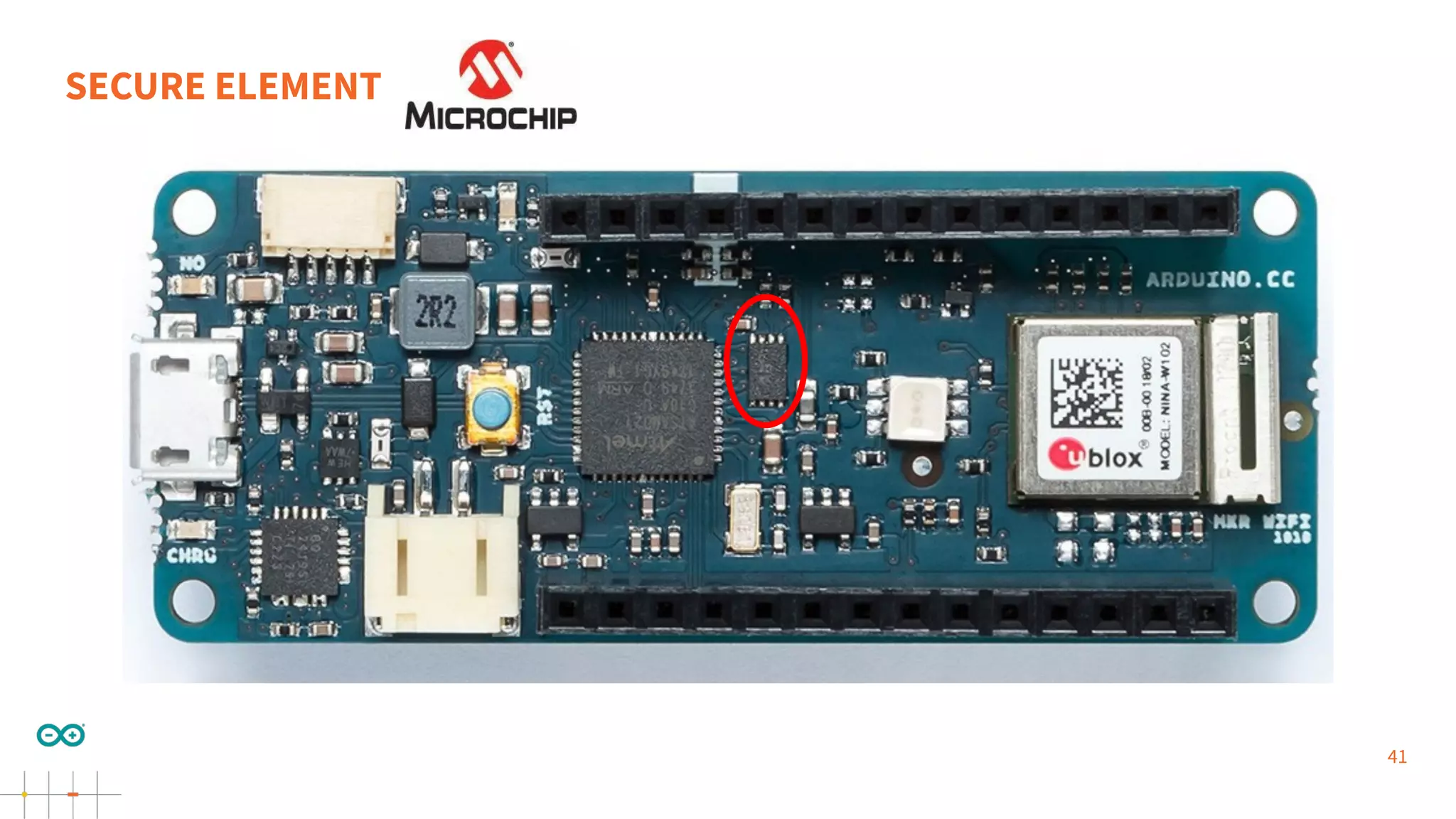
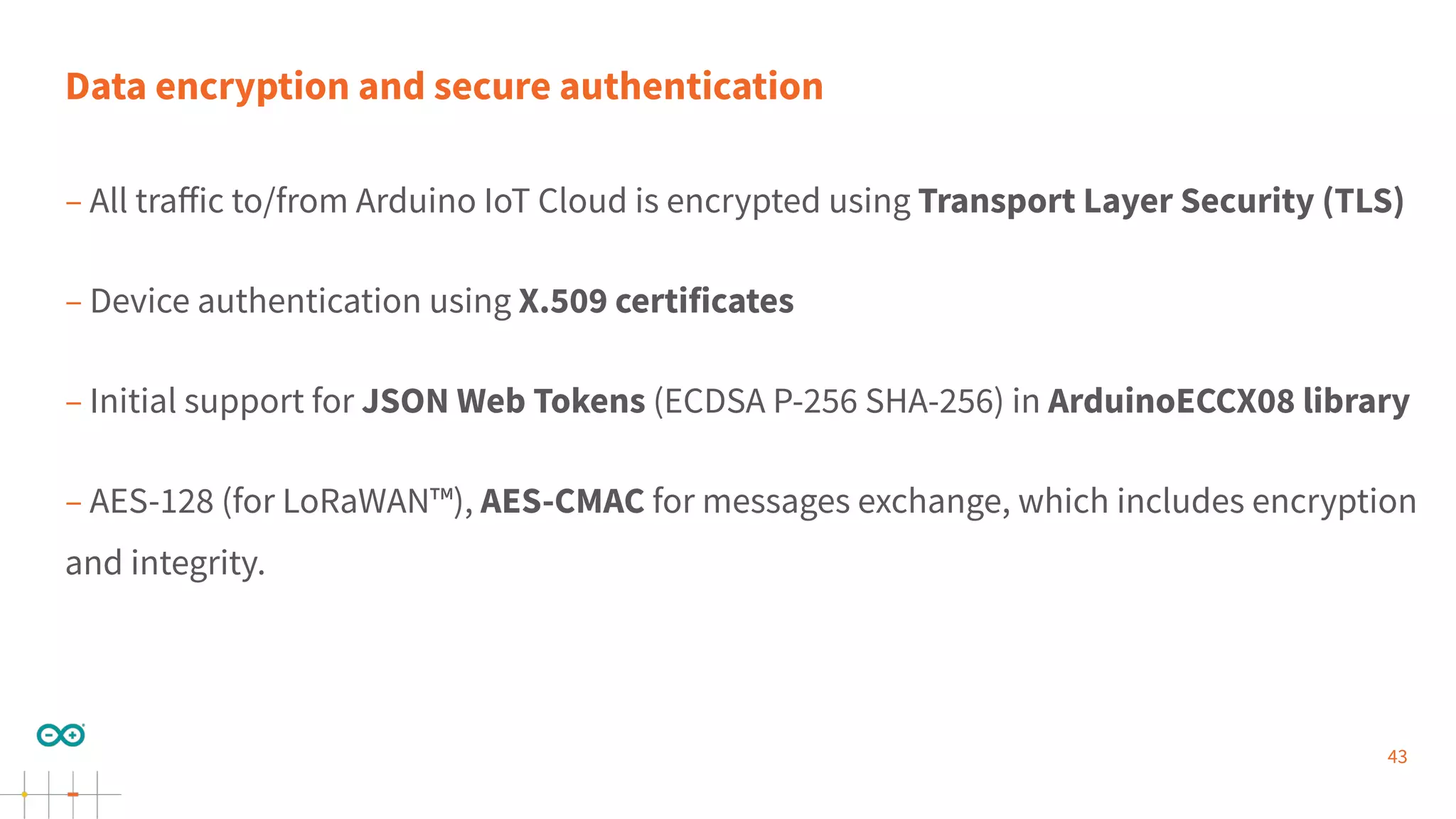
Gianluca Varisco discusses the challenges of securing IoT applications at the Arduino Paris Open Source Summit, highlighting the fragmented landscape and various security risks faced by devices. Key issues include weak data protection, insufficient security training, and the lack of firmware updates, leading to vulnerabilities and potential breaches. Varisco emphasizes the importance of a robust cybersecurity strategy and the need for manufacturers to ensure secure device management and communication protocols.