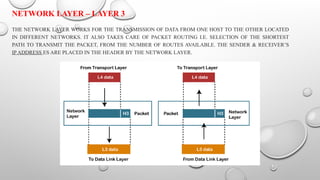
The document details the functions and responsibilities of the network, transport, session, and presentation layers of the OSI model. It explains how the network layer focuses on routing and logical addressing, the transport layer manages data delivery and error control, the session layer establishes and maintains sessions, and the presentation layer translates data formats and handles encryption. Various protocols are mentioned for each layer, highlighting their respective roles in enabling effective communication across networks.