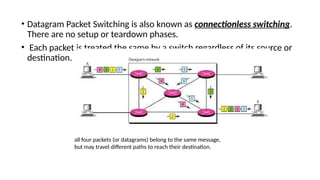
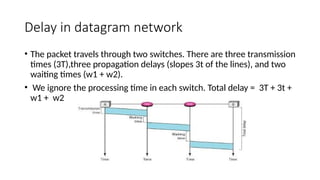
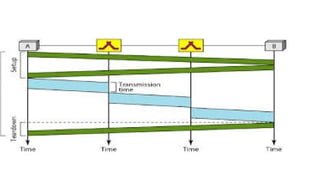
The network layer in the TCP/IP protocol suite is responsible for host-to-host delivery of datagrams, translating logical addresses to physical addresses, and managing routing, congestion, and flow control. It uses packet switching techniques to send data in smaller packets, and can operate in two modes: datagram packet switching (connectionless) and virtual circuit switching (connection-oriented). Security concerns at this layer can be addressed using IPsec, which protects against attacks such as packet sniffing, modification, and IP spoofing.