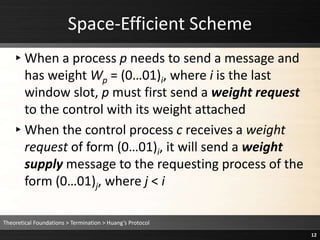
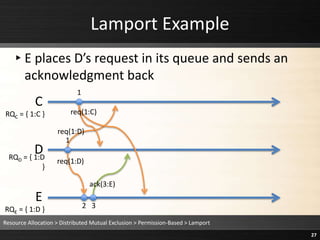
The document describes Lamport's permission-based distributed mutual exclusion algorithm. The algorithm works as follows:
1) To request a resource, a process sends a timestamped request message to all other processes and stores a copy in its local request queue.
2) When a process receives a request, it adds the request to its own queue and sends an acknowledgment back.
3) A process is granted the resource when its highest-priority request in its local queue has received an acknowledgment from every other process with a later timestamp.











































![Ricart & Agrawala Algorithm
▸Rule 1: Mutual Exclusion Invocation
requesting_critical_section = true;
sequence_no = highest_sequence_no + 1;
outstanding_replies = N – 1;
for(i = 0; i < N; i++) {
if(i != me) send(REQUEST(sequence_no, me), i);
}
while(outstanding_replies > 0) { }
critical_section();
requesting_critical_section = false;
for(i = 0; i < N; i++) {
if(reply_deferred[i]) {
reply_deferred[i] = false;
send(REPLY, i);
}
}
Resource Allocation > Distributed Mutual Exclusion > Permission-Based > Ricart & Agrawala
48](https://image.slidesharecdn.com/08-240229050203-dab2578e/85/os-distributed-system-theoretical-foundation-48-320.jpg)





![Ricart & Agrawala Algorithm
▸Rule 2: Receiving Requests(j, k)
highest_sequence_no = max(highest_sequence_no, j);
defer = requesting_critical_section &&
((j > sequence_no) ||(j == sequence_no && k >
me));
if(defer) {
reply_deferred[k] = true;
}
else {
send(REPLY, k);
}
Resource Allocation > Distributed Mutual Exclusion > Permission-Based > Ricart & Agrawala
54](https://image.slidesharecdn.com/08-240229050203-dab2578e/85/os-distributed-system-theoretical-foundation-54-320.jpg)



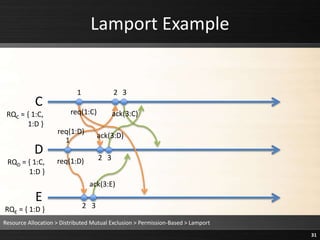
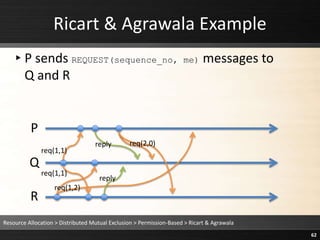
![Ricart & Agrawala Example
▸ defer = requesting_critical_section &&
((j > sequence_no) ||(j == sequence_no && k > me))
= true && ((1 > 1) || (1 == 1 && 2 > 1)) = true
▸Q defers R’s request (reply_deferred[k] = true)
Resource Allocation > Distributed Mutual Exclusion > Permission-Based > Ricart & Agrawala
58
P
Q
R
reply
req(1,1)
req(1,1)
req(1,2)](https://image.slidesharecdn.com/08-240229050203-dab2578e/85/os-distributed-system-theoretical-foundation-58-320.jpg)






![Ricart & Agrawala Algorithm
▸Rule 1: Mutual Exclusion Invocation
requesting_critical_section = true;
sequence_no = highest_sequence_no + 1;
outstanding_replies = N – 1;
for(i = 0; i < N; i++) {
if(i != me) send(REQUEST(sequence_no, me), i);
}
while(outstanding_replies > 0) { }
critical_section();
requesting_critical_section = false;
for(i = 0; i < N; i++) {
if(reply_deferred[i]) {
reply_deferred[i] = false;
send(REPLY, i);
}
}
Resource Allocation > Distributed Mutual Exclusion > Permission-Based > Ricart & Agrawala
66](https://image.slidesharecdn.com/08-240229050203-dab2578e/85/os-distributed-system-theoretical-foundation-66-320.jpg)


![Ricart & Agrawala Example
▸ defer = requesting_critical_section &&
((j > sequence_no) ||(j == sequence_no && k > me))
= true && ((2 > 1) || (2 == 1 && 0 > 1)) = true
▸Q defers P’s request (reply_deferred[k] = true)
Resource Allocation > Distributed Mutual Exclusion > Permission-Based > Ricart & Agrawala
69
P
Q
R
reply
reply
req(1,1)
req(1,1)
req(2,0)
req(1,2)](https://image.slidesharecdn.com/08-240229050203-dab2578e/85/os-distributed-system-theoretical-foundation-69-320.jpg)

![Ricart & Agrawala Example
▸ defer = requesting_critical_section &&
((j > sequence_no) ||(j == sequence_no && k > me))
= true && ((2 > 1) || (2 == 1 && 0 > 2)) = true
▸R defers P’s request (reply_deferred[k] = true)
Resource Allocation > Distributed Mutual Exclusion > Permission-Based > Ricart & Agrawala
71
P
Q
R
reply
reply
req(1,1)
req(1,1)
req(2,0)
req(1,2)](https://image.slidesharecdn.com/08-240229050203-dab2578e/85/os-distributed-system-theoretical-foundation-71-320.jpg)
![Ricart & Agrawala Algorithm
▸Rule 1: Mutual Exclusion Invocation
requesting_critical_section = true;
sequence_no = highest_sequence_no + 1;
outstanding_replies = N – 1;
for(i = 0; i < N; i++) {
if(i != me) send(REQUEST(sequence_no, me), i);
}
while(outstanding_replies > 0) { }
critical_section();
requesting_critical_section = false;
for(i = 0; i < N; i++) {
if(reply_deferred[i]) {
reply_deferred[i] = false;
send(REPLY, i);
}
}
Resource Allocation > Distributed Mutual Exclusion > Permission-Based > Ricart & Agrawala
72](https://image.slidesharecdn.com/08-240229050203-dab2578e/85/os-distributed-system-theoretical-foundation-72-320.jpg)
![Ricart & Agrawala Example
▸Q exits critical section
▸Since reply_deferred[0], Q sends REPLY message to P
▸Since reply_deferred[2], Q sends REPLY message to R
Resource Allocation > Distributed Mutual Exclusion > Permission-Based > Ricart & Agrawala
73
P
Q
R
reply
reply
req(1,1)
req(1,1)
req(2,0) reply
reply
req(1,2)](https://image.slidesharecdn.com/08-240229050203-dab2578e/85/os-distributed-system-theoretical-foundation-73-320.jpg)




![Ricart & Agrawala Example
▸R exits critical section
▸Since reply_deferred[0], R sends REPLY message to P
Resource Allocation > Distributed Mutual Exclusion > Permission-Based > Ricart & Agrawala
78
P
Q
R
reply
reply
req(1,1)
req(1,1)
req(2,0) reply
reply
reply
reply
req(1,2)](https://image.slidesharecdn.com/08-240229050203-dab2578e/85/os-distributed-system-theoretical-foundation-78-320.jpg)



