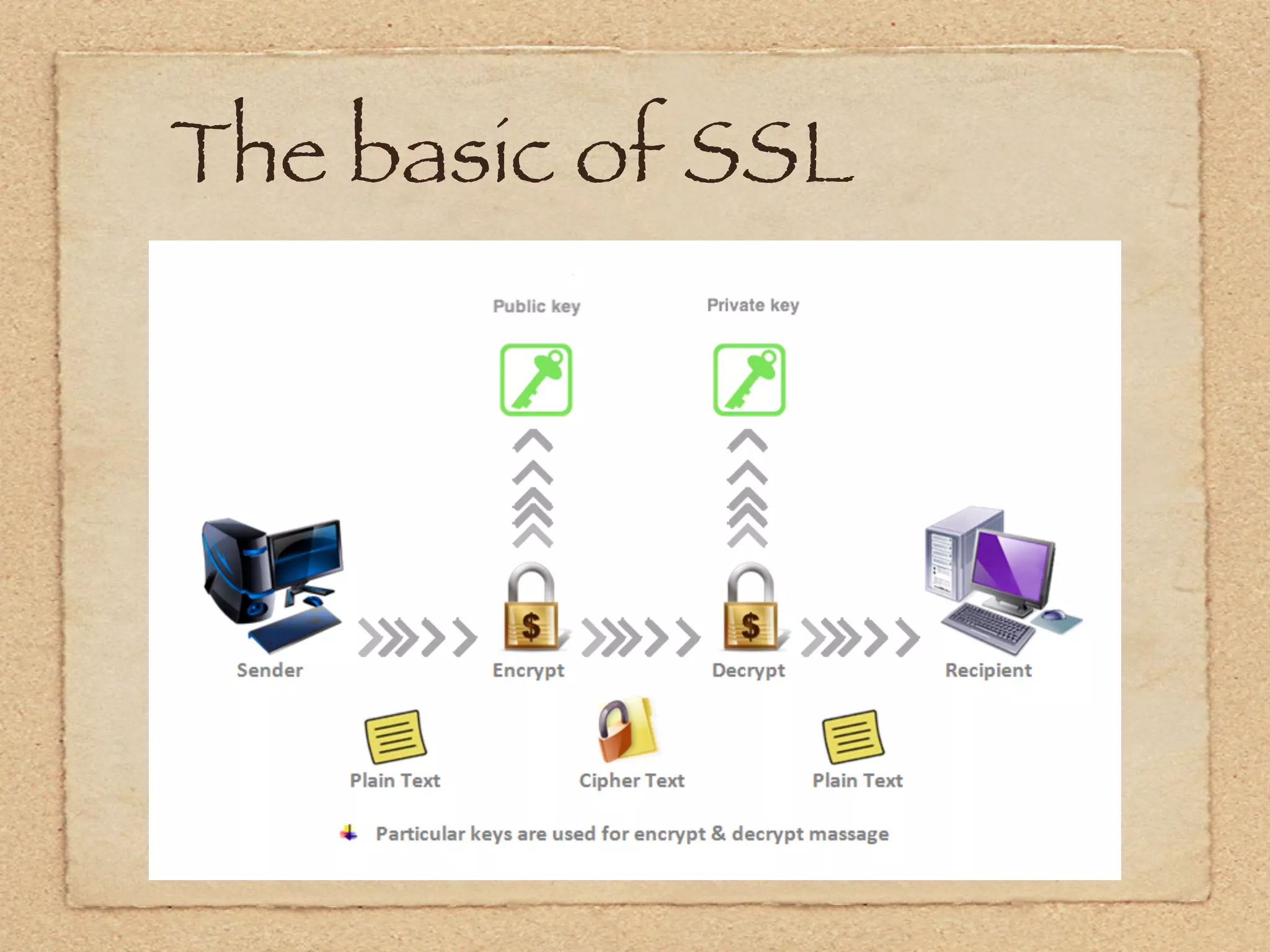
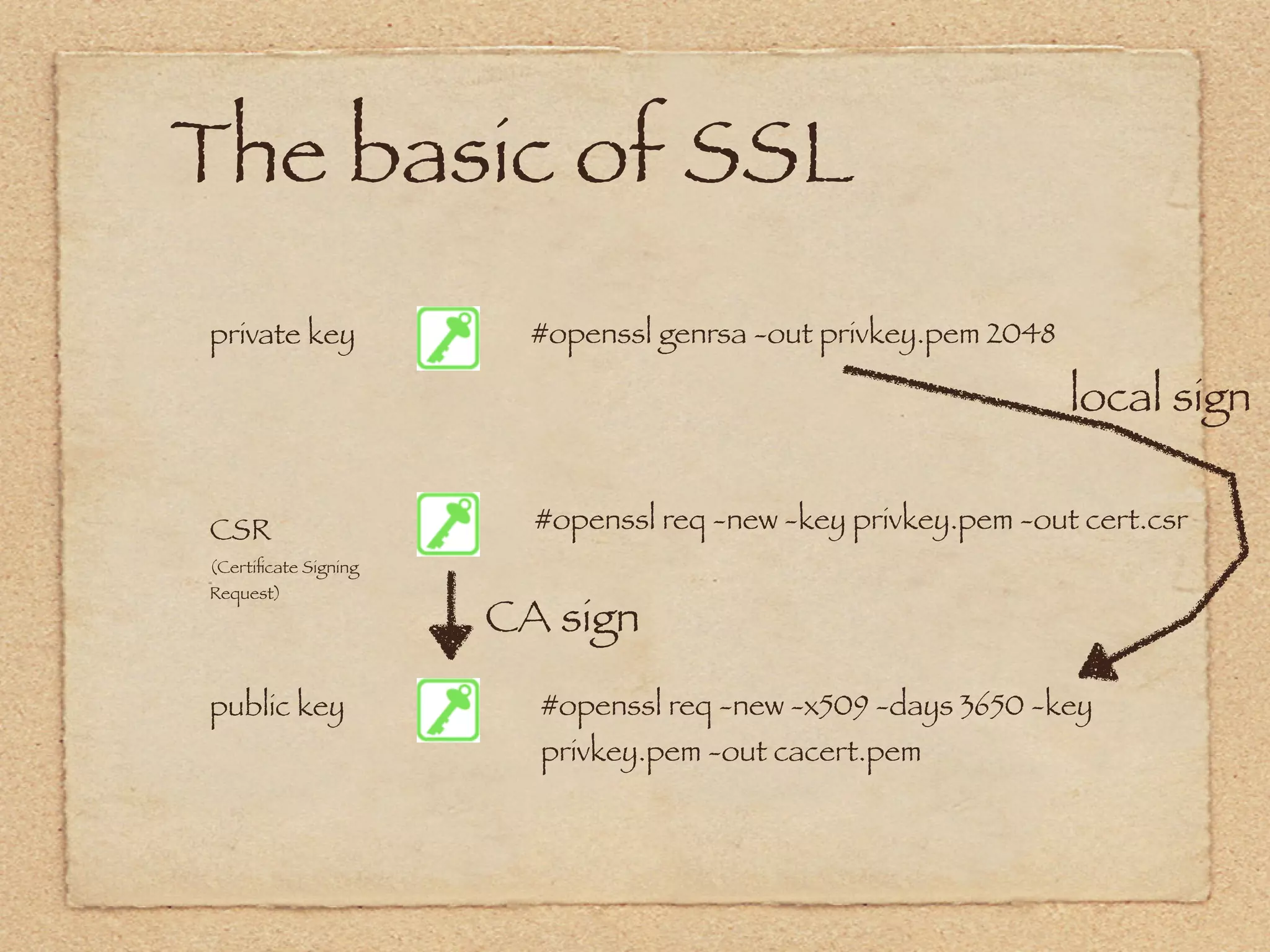
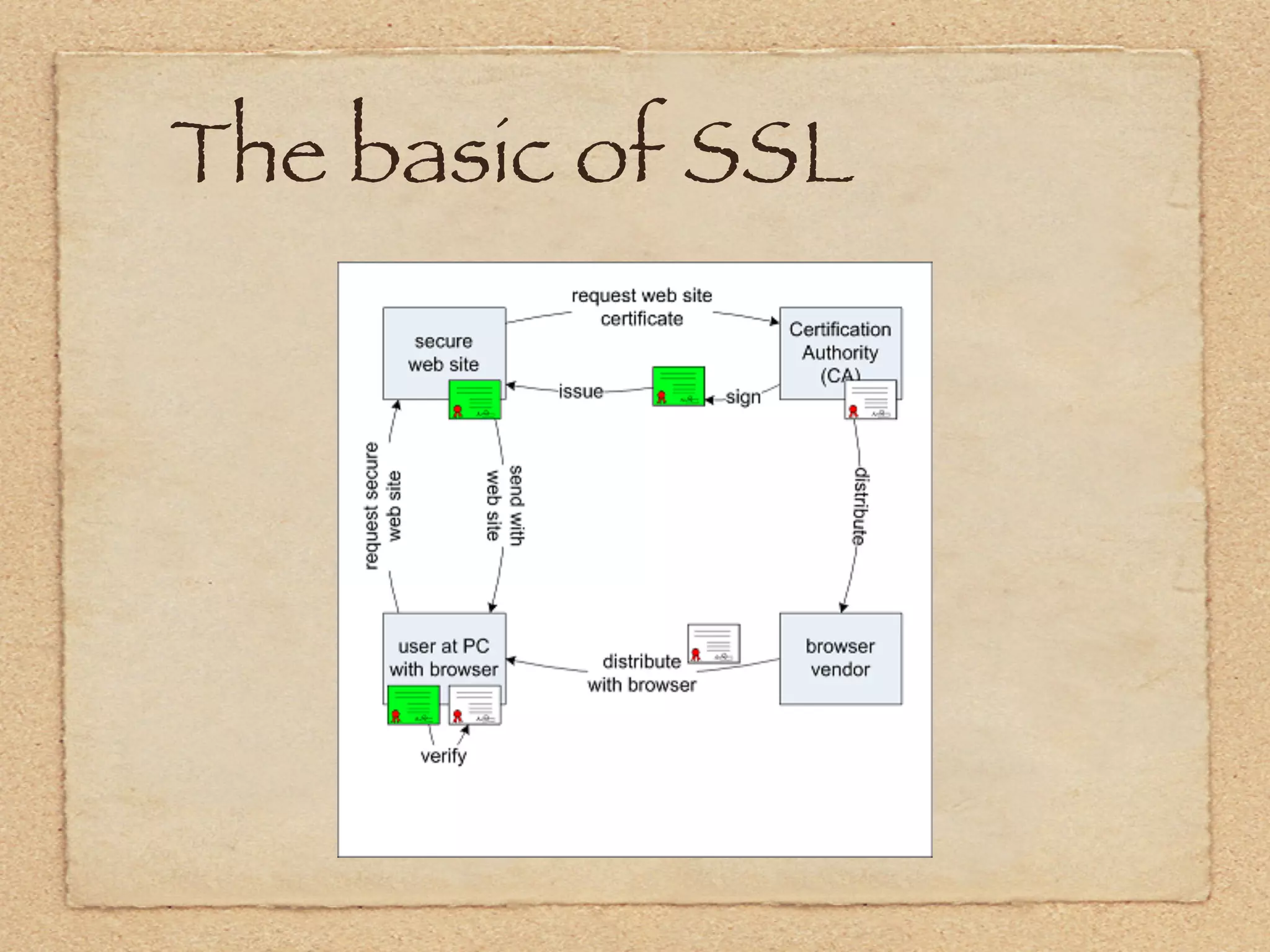
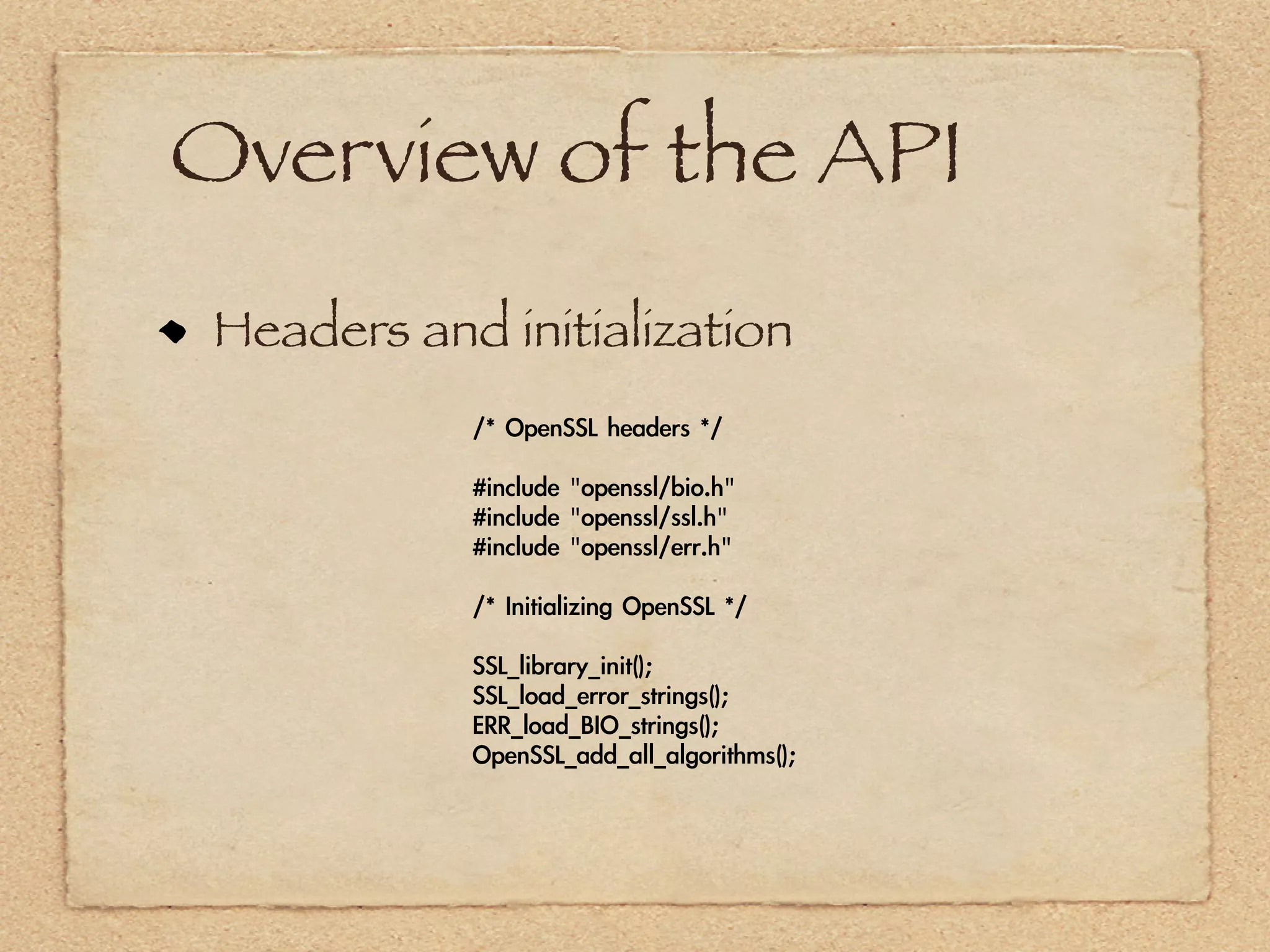
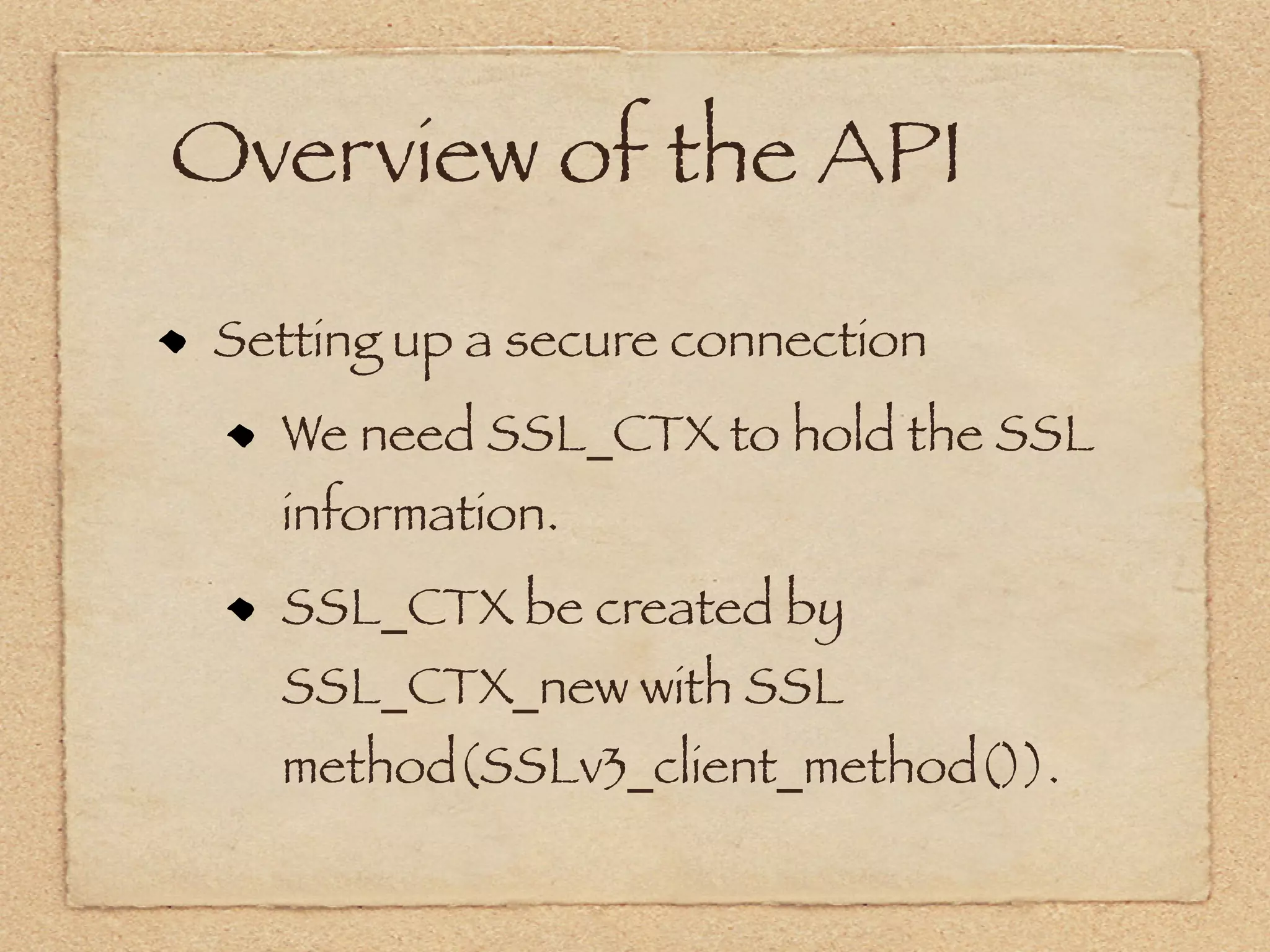
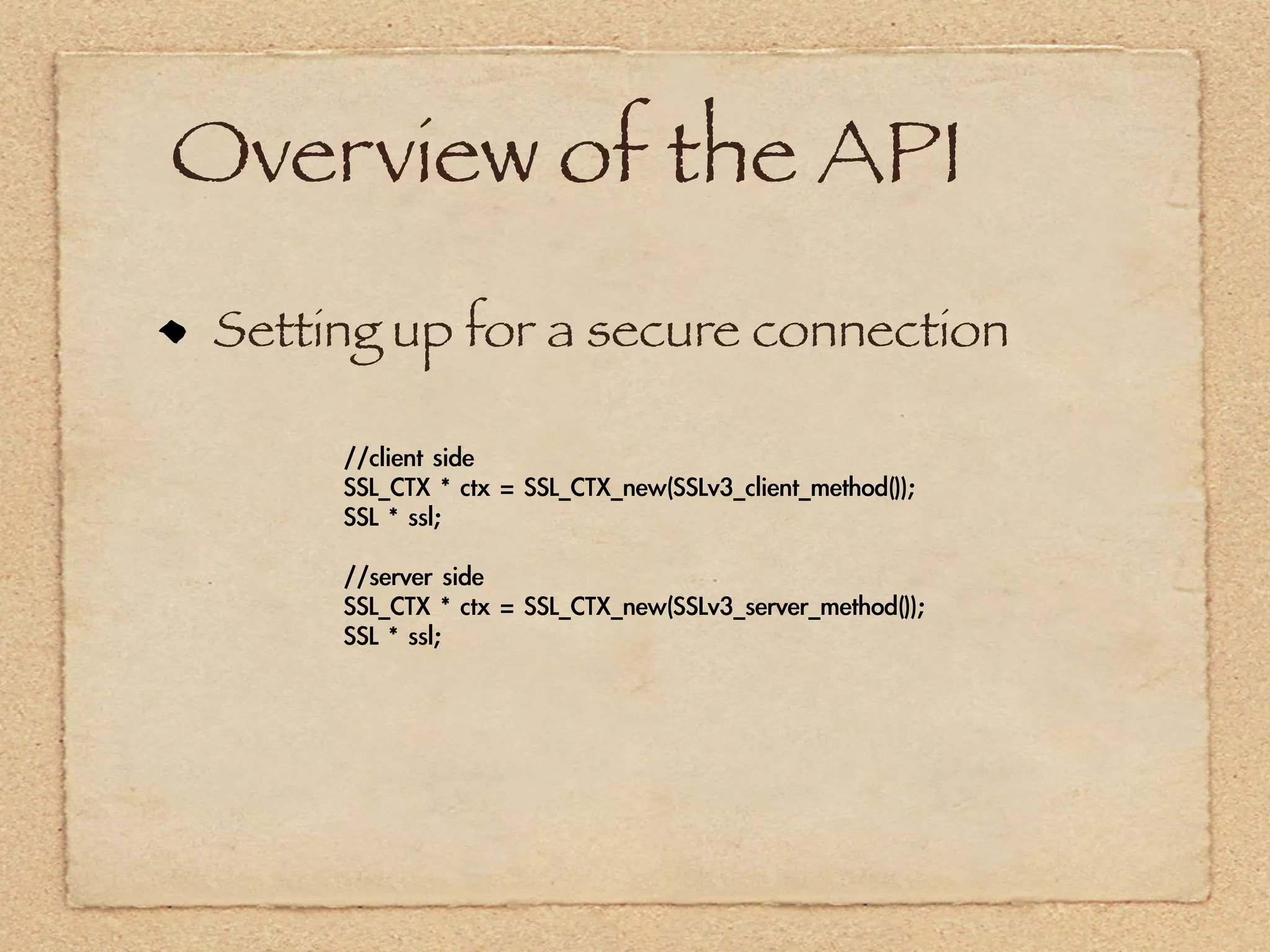
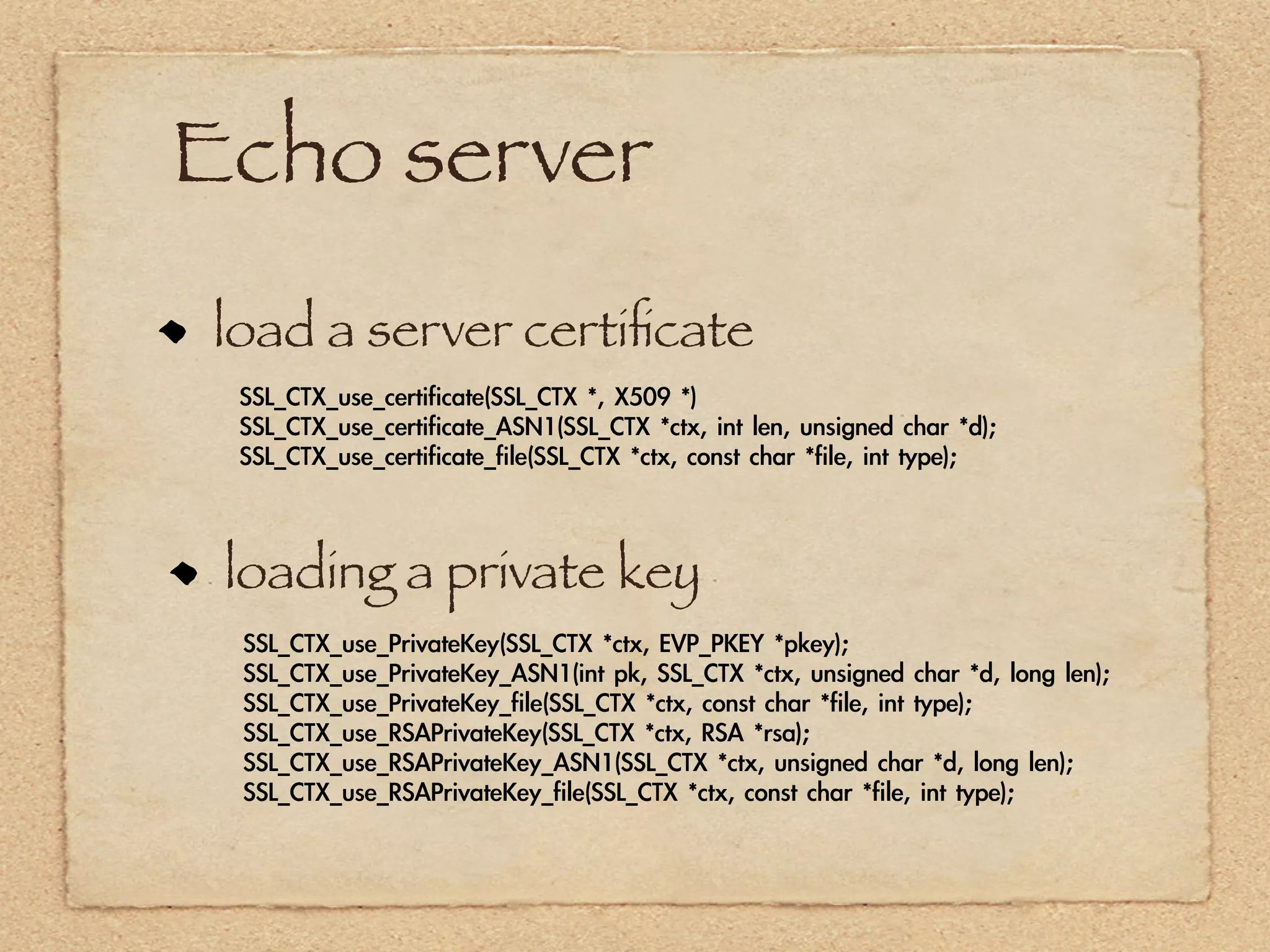
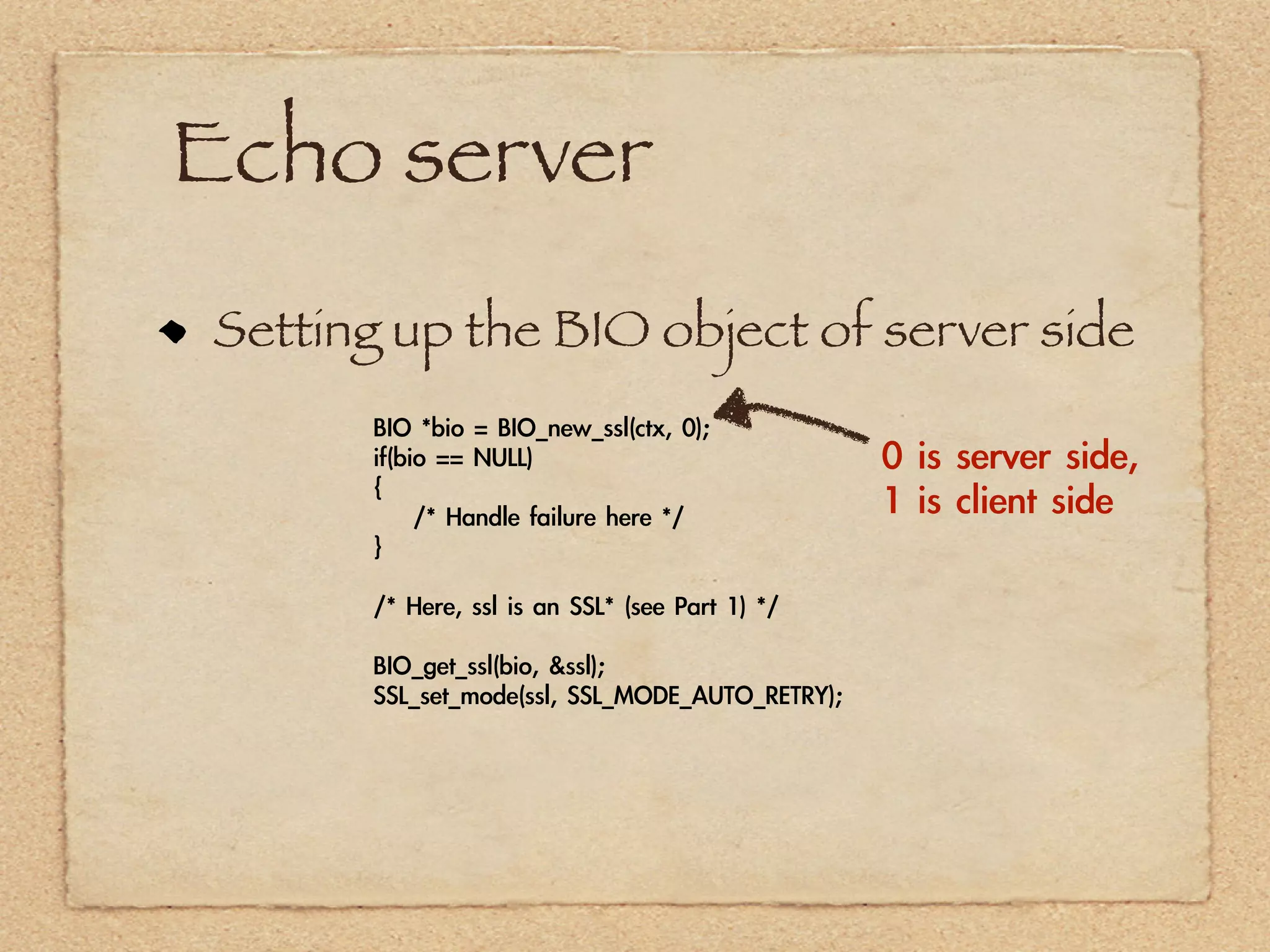
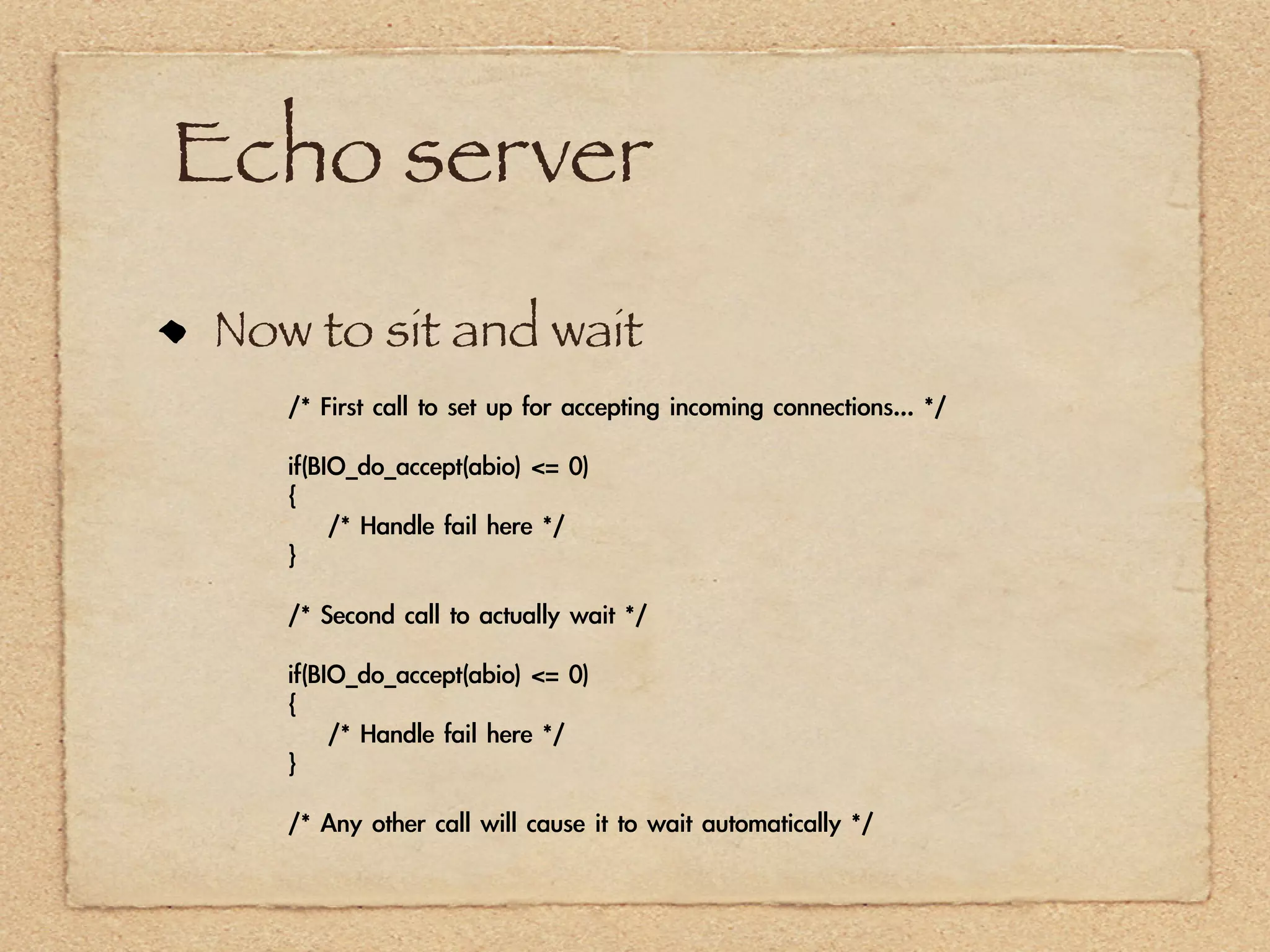
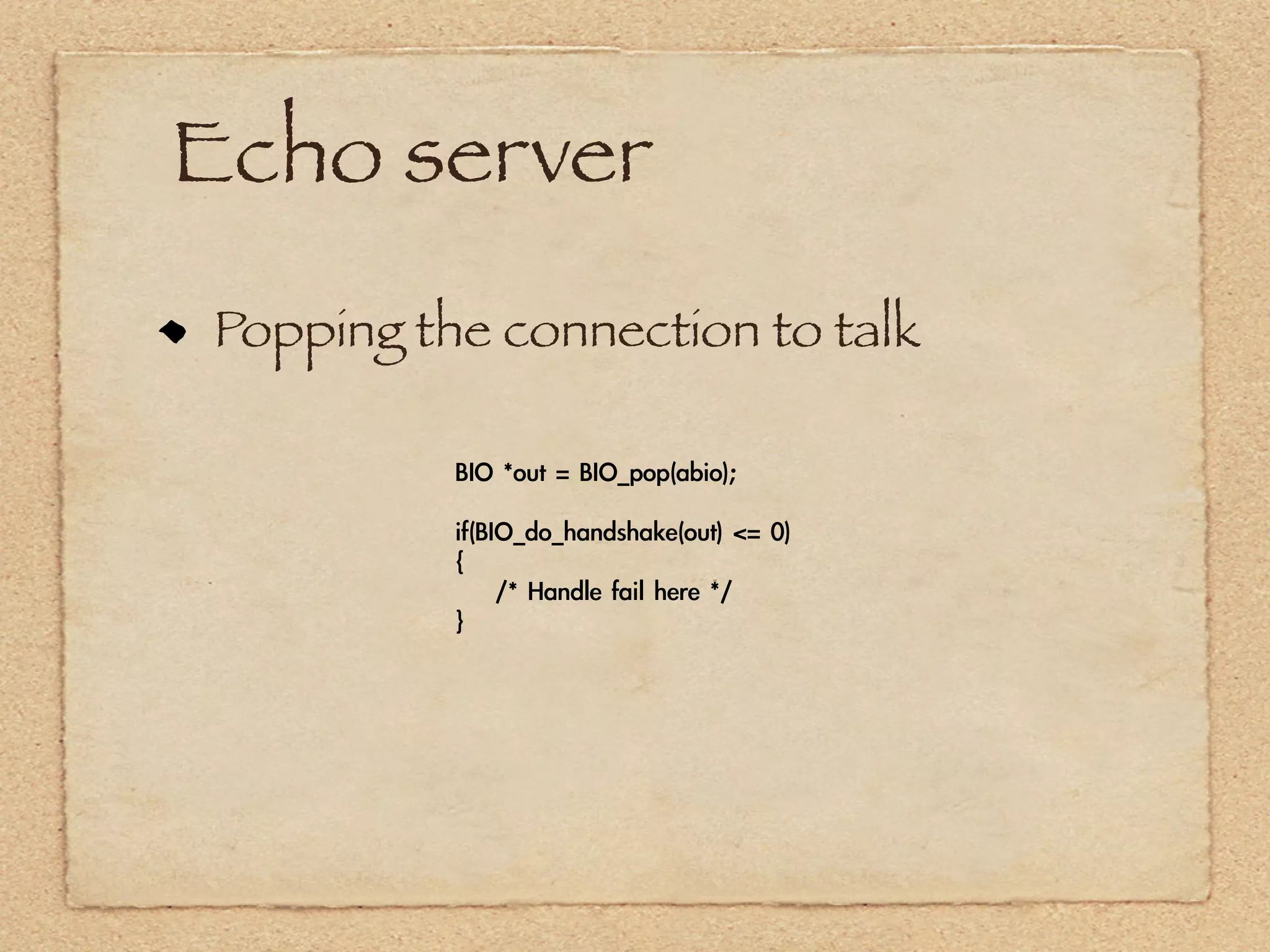
The document provides an overview of SSL and OpenSSL. It discusses generating keys and certificates, setting up SSL contexts, creating secure connections, reading/writing data, and handling errors. It also provides code snippets for an echo client and server. The echo server loads a certificate, sets up a listening BIO, accepts connections, and performs handshakes. The handshake process involves a client sending a "hello" message and the server responding with its own parameters to establish encryption.